问题描述:
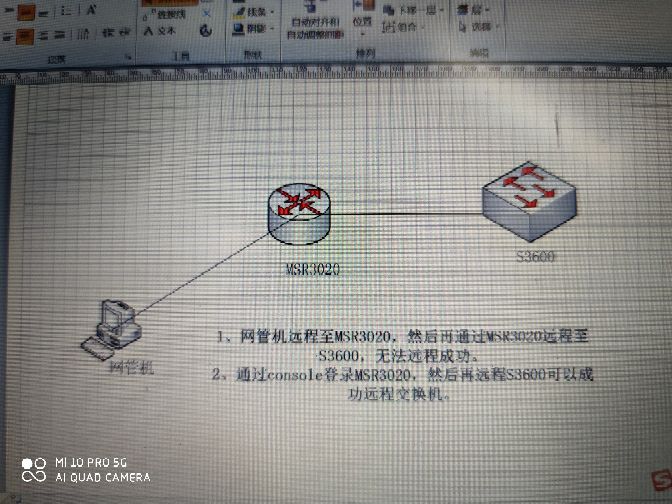
通过网管机远程至现场MSR3020(V5.20 Release 1809p04),然后再通关msr3020ssh远程跳转至一台交换机,出现可以输入用户名,但是还是无法远程至交换机。
但是,通过console口登陆msr3020路由器,可以ssh远程交换机。
有人可以帮忙解答一下吗?
组网及组网描述:
- 2020-12-03提问
- 举报
-
(0)
最佳答案

建议开debug查一下,如果需要停掉debug,按ctrl+O;
<H3C>terminal debugging
The current terminal is enabled to display debugging logs.
<H3C>terminal monitor
The current terminal is enabled to display logs.
# 打开SSH服务器端的事件调试信息开关。远端用户从192.168.0.58上通过putty客户端登录本设备,用户名为abc、密码为abc。
<Sysname> debugging ssh server event
*Dec 31 17:58:29:819 2009 Sysname SSHS/7/EVENT: Start new child 135.
*Dec 31 17:58:29:841 2009 Sysname SSHS/6/EVENT: Connection from 192.168.0.58 port 1476
// 用户从192.168.0.58的1476端口发起连接请求,用户进程ID为135
// 客户端SSH协议版本号2.0,客户端软件版本信息为PuTTY_Release_0.60
*Dec 31 17:58:29:888 2009 Sysname SSHS/7/EVENT: Enabling compatibility mode for protocol 2.0
*Dec 31 17:58:29:897 2009 Sysname SSHS/7/EVENT: Local version string SSH-2.0-Comware-7
// 发给客户端的服务器端版本串信息(版本中的Comware-7与产品型号有关,请以设备的实际情况为准)
*Dec 31 17:58:29:947 2009 Sysname SSHS/7/EVENT: Hostkey string is : ssh-dss,ssh-rsa
// 主机公钥串为ssh-dss、ssh-rsa,即支持DSA和RSA公钥算法
*Dec 31 17:58:29:988 2009 Sysname SSHS/7/EVENT: Received SSH2_MSG_KEXINIT.
// 收到SSH2_MSG_KEXINIT消息
*Dec 31 17:58:29:993 2009 Sysname SSHS/7/EVENT: My proposal kex:
// 服务器端的版本协商算法串信息如下
// 密钥交换算法串
*Dec 31 17:58:30:35 2009 Sysname SSHS/7/EVENT: Kex strings(1): ssh-dss,ssh-rsa
// 服务器端支持的主机公钥算法串
*Dec 31 17:58:30:43 2009 Sysname SSHS/7/EVENT: Kex strings(2): aes128-cbc,3des-cbc,des-cbc
// 客户端到服务器端的加密算法串
*Dec 31 17:58:30:48 2009 Sysname SSHS/7/EVENT: Kex strings(3): aes128-cbc,3des-cbc,des-cbc
// 服务器端到客户端的加密算法串
// 客户端到服务器端的HMAC算法串
// 服务器端到客户端的HMAC算法串
*Dec 31 17:58:30:76 2009 Sysname SSHS/7/EVENT: Kex strings(6): none,zlib,zlib@openssh.com
// 客户端到服务器端的压缩算法串
*Dec 31 17:58:30:82 2009 Sysname SSHS/7/EVENT: Kex strings(7): none,zlib,zlib@openssh.com
// 服务器端到客户端的压缩算法串
*Dec 31 17:58:30:91 2009 Sysname SSHS/7/EVENT: Kex strings(8):
*Dec 31 17:58:30:96 2009 Sysname SSHS/7/EVENT: Kex strings(9):
*Dec 31 17:58:30:104 2009 Sysname SSHS/7/EVENT: Peer proposal kex:
// 客户端的版本协商算法串信息如下
// 密钥交换算法串
*Dec 31 17:58:30:147 2009 Sysname SSHS/7/EVENT: Kex strings(1): ssh-rsa,ssh-dss
// 服务器端支持的主机公钥算法串
// 服务器端支持的加密算法串
// 服务器端到客户端的加密算法串
*Dec 31 17:58:30:170 2009 Sysname SSHS/7/EVENT: Kex strings(4): hmac-sha1,hmac-sha1-96,hmac-md5
// 客户端到服务器端的HMAC算法串
*Dec 31 17:58:30:171 2009 Sysname SSHS/7/EVENT: Kex strings(5): hmac-sha1,hmac-sha1-96,hmac-md5
// 服务器端到客户端的HMAC算法串
*Dec 31 17:58:30:172 2009 Sysname SSHS/7/EVENT: Kex strings(6): none,zlib
// 客户端到服务器端的压缩算法
*Dec 31 17:58:30:173 2009 Sysname SSHS/7/EVENT: Kex strings(7): none,zlib
// 客户端到服务器端的压缩算法
*Dec 31 17:58:30:174 2009 Sysname SSHS/7/EVENT: Kex strings(8):
*Dec 31 17:58:30:243 2009 Sysname SSHS/7/EVENT: Kex strings(9):
*Dec 31 17:58:30:248 2009 Sysname SSHS/7/EVENT: Kex: client->server, Encrypt: aes128-cbc, HMAC: hmac-sha1, Compress: none
// 协商出来的客户端到服务器端的加密算法、HMAC算法和压缩算法
// 协商出来的服务器端到客户端的加密算法、HMAC算法和压缩算法
*Dec 31 17:58:30:287 2009 Sysname SSHS/7/EVENT: Received SSH2_MSG_KEX_DH_GEX_REQUEST_OLD.
// 接收到SSH2_MSG_KEX_DH_GEX_REQUEST_OLD消息
*Dec 31 17:58:31:142 2009 Sysname SSHS/7/EVENT: Expecting packet type 32.
*Dec 31 17:58:33:45 2009 Sysname SSHS/7/EVENT: Set new keys: mode=1
// 设置协商出来的新的算法(mode=1表示输出方向)
*Dec 31 17:58:33:62 2009 Sysname SSHS/7/EVENT: Expecting packet type 21.
*Dec 31 17:58:33:466 2009 Sysname SSHS/7/EVENT: Set new keys: mode=0
// 设置协商出来的新的算法(mode=0标识输入方向)
*Dec 31 17:58:33:471 2009 Sysname SSHS/7/EVENT: KEX done.
// 密钥交换结束
*Dec 31 17:58:33:479 2009 Sysname SSHS/7/EVENT: Received SSH2_MSG_SERVICE_REQUEST.
*Dec 31 17:58:34:459 2009 Sysname SSHS/7/EVENT: Received SSH2_MSG_USERAUTH_REQUEST.
*Dec 31 17:58:34:464 2009 Sysname SSHS/7/EVENT: Username: abc, service: ssh-connection, method: none
// 接收到用户认证请求消息,消息中的用户名为abc,服务请求串为ssh-connection,认证方法为none(向对方请求对方支持的认证方法列表串)
// PAM初始化,PAM服务类型为login,纯用户名为abc,域名为空
*Dec 31 17:58:34:509 2009 Sysname SSHS/7/EVENT: Try authentication method none.
// 尝试none认证类型
*Dec 31 17:58:34:520 2009 Sysname SSHS/6/EVENT: Failed none for abc from 192.168.0.58 port 1476 ssh2
// none认证尝试失败
*Dec 31 17:58:34:525 2009 Sysname SSHS/7/EVENT: Get authentication methods: password
// 用户还可挑战的认证方法为password认证方法
*Dec 31 17:58:35:673 2009 Sysname SSHS/7/EVENT: Received SSH2_MSG_USERAUTH_REQUEST.
*Dec 31 17:58:35:679 2009 Sysname SSHS/7/EVENT: Username: abc, service: ssh-connection, method: password
*Dec 31 17:58:35:687 2009 Sysname SSHS/7/EVENT: Try authentication method password.
*Dec 31 17:58:36:86 2009 Sysname SSHS/7/EVENT: PAM: password authentication accepted for abc, level: 15, workdir:flash:.
// 用户password认证挑战成功,授权用户角色level-15,授权工作路径为flash:
// 用户abc从192.168.0.58端口1467发起连接请求,password认证通过
*Dec 31 17:58:36:139 2009 Sysname SSHS/7/EVENT: Entering interactive session for SSH2.
*Dec 31 17:58:36:147 2009 Sysname SSHS/7/EVENT: Initiate server message dispatch, compatibility:1/0
// 初始化消息分发处理,兼容2.0版本,不兼容1.3版本
*Dec 31 17:58:36:173 2009 Sysname SSHS/7/EVENT: Received session request.
*Dec 31 17:58:36:185 2009 Sysname SSHS/7/EVENT: Channel 0: new [server-session]
*Dec 31 17:58:36:191 2009 Sysname SSHS/7/EVENT: Session id 0 unused.
*Dec 31 17:58:36:199 2009 Sysname SSHS/7/EVENT: Session opened: session 0, link with channel 0
// 接收到SSH2_MSG_CHANNEL_OPEN消息,分配通道号为0,会话ID为0
*Dec 31 17:58:36:225 2009 Sysname SSHS/7/EVENT: Channel request: user abc, service type 1
// 用户abc的配置支持服务类型为1(1表示同时支持Stelnet和SFTP服务;2表示支持Stelnet服务,3表示支持SFTP服务)
// 接收到类型为shell的通道请求消息
*Dec 31 17:58:36:298 2009 Sysname SSHS/7/EVENT: Channel request: user abc, service type 1
*Dec 31 17:58:36:327 2009 Sysname SSHS/7/EVENT: Channel 0: read_fd 33 is a TTY.
*Dec 31 17:58:36:337 2009 Sysname SSHS/7/EVENT: Setup environment: user=abc, work directory=flash:, level=15
// 设置用户abc的环境变量:工作路径为flash:,授权等级为15
*Dec 31 17:58:36:349 2009 Sysname SSHS/7/EVENT: Get default work dir: /mnt/flash:, return:0
*Dec 31 17:58:40:87 2009 Sysname SSHS/7/EVENT: Received SIGCHLD.
*Dec 31 17:58:40:93 2009 Sysname SSHS/7/EVENT: Channel 0: request exit-status confirm 0
*Dec 31 17:58:40:102 2009 Sysname SSHS/7/EVENT: Release channel 0
*Dec 31 17:58:40:107 2009 Sysname SSHS/7/EVENT: Channel 0: write failed
*Dec 31 17:58:40:111 2009 Sysname SSHS/7/EVENT: Channel 0: send EOW
*Dec 31 17:58:40:115 2009 Sysname SSHS/7/EVENT: Channel 0: output state changed (open -> closed)
*Dec 31 17:58:40:125 2009 Sysname SSHS/7/EVENT: Channel 0: read failed
*Dec 31 17:58:40:129 2009 Sysname SSHS/7/EVENT: Channel 0: input state changed (open -> drain)
*Dec 31 17:58:40:134 2009 Sysname SSHS/7/EVENT: Channel 0: send EOF
*Dec 31 17:58:40:138 2009 Sysname SSHS/7/EVENT: Channel 0: input state changed (drain -> closed)
*Dec 31 17:58:40:143 2009 Sysname SSHS/7/EVENT: Channel 0: send SSH2_MSG_CHANNEL_CLOSE
*Dec 31 17:58:40:173 2009 Sysname SSHS/7/EVENT: Channel 0: received SSH2_MSG_CHANNEL_CLOSE
*Dec 31 17:58:40:180 2009 Sysname SSHS/7/EVENT: Close session: session 0, pid 0
*Dec 31 17:58:40:185 2009 Sysname SSHS/7/EVENT: Session id 0 unused.
*Dec 31 17:58:40:187 2009 Sysname SSHS/7/EVENT: Channel 0: garbage collecting
*Dec 31 17:58:40:198 2009 Sysname SSHS/7/EVENT: Connection closed by 192.168.0.58
// 从IP地址192.168.0.58发起的连接被主动关闭
*Dec 31 17:58:40:203 2009 Sysname SSHS/7/EVENT: PAM: cleanup
*Dec 31 17:58:40:205 2009 Sysname SSHS/6/EVENT: Transferred: sent 1928 bytes, received 1624 bytes
// 传输完成,发送1928字节,接收1624字节
*Dec 31 17:58:40:207 2009 Sysname SSHS/6/EVENT: Closing connection to 192.168.0.58 port 1476
// 关闭与IP地址192.168.0.58、端口1476之间的连接
# 打开SSH服务器端的消息调试信息开关。用户从IP地址为192.168.0.59的客户端上登录本设备。登录成功后,用户首先执行了dir命令,然后执行quit命令退出。
<Sysname> debugging ssh server message
*Dec 31 16:07:05:723 2009 Sysname SSHS/7/MESSAGE: Prepare packet[20].
// 准备消息,消息类型为20(以下各消息涵义类似,解释略)
*Dec 31 16:07:05:779 2009 Sysname SSHS/7/MESSAGE: Received packet type 20.
// 接收到消息,消息类型为20(以下各消息涵义类似,解释略)
*Dec 31 16:07:05:886 2009 Sysname SSHS/7/MESSAGE: Received packet type 34.
*Dec 31 16:07:05:887 2009 Sysname SSHS/7/MESSAGE: Prepare packet[31].
*Dec 31 16:07:07:444 2009 Sysname SSHS/7/MESSAGE: Received packet type 32.
*Dec 31 16:07:09:294 2009 Sysname SSHS/7/MESSAGE: Prepare packet[33].
*Dec 31 16:07:09:301 2009 Sysname SSHS/7/MESSAGE: Prepare packet[21].
*Dec 31 16:07:11:627 2009 Sysname SSHS/7/MESSAGE: Received packet type 21.
*Dec 31 16:07:11:738 2009 Sysname SSHS/7/MESSAGE: Received packet type 5.
*Dec 31 16:07:11:741 2009 Sysname SSHS/7/MESSAGE: Prepare packet[6].
*Dec 31 16:07:11:840 2009 Sysname SSHS/7/MESSAGE: Received packet type 50.
*Dec 31 16:07:11:846 2009 Sysname SSHS/7/MESSAGE: Prepare packet[51].
*Dec 31 16:07:12:673 2009 Sysname SSHS/7/MESSAGE: Received packet type 50.
*Dec 31 16:07:12:803 2009 Sysname SSHS/7/MESSAGE: Prepare packet[52].
*Dec 31 16:07:12:885 2009 Sysname SSHS/7/MESSAGE: Received packet type 90.
*Dec 31 16:07:12:887 2009 Sysname SSHS/7/MESSAGE: Prepare packet[91].
*Dec 31 16:07:12:986 2009 Sysname SSHS/7/MESSAGE: Received packet type 98.
*Dec 31 16:07:12:996 2009 Sysname SSHS/7/MESSAGE:P repare packet[99].
*Dec 31 16:07:13:86 2009 Sysname SSHS/7/MESSAGE: Received packet type 98.
*Dec 31 16:07:13:97 2009 Sysname SSHS/7/MESSAGE: Prepare packet[93].
*Dec 31 16:07:13:99 2009 Sysname SSHS/7/MESSAGE: Prepare packet[99].
*Dec 31 16:07:14:62 2009 Sysname SSHS/7/MESSAGE: Received packet type 94.
*Dec 31 16:07:14:268 2009 Sysname SSHS/7/MESSAGE: Received packet type 94.
*Dec 31 16:07:14:695 2009 Sysname SSHS/7/MESSAGE: Received packet type 94.
*Dec 31 16:07:14:902 2009 Sysname SSHS/7/MESSAGE: Received packet type 94.
*Dec 31 16:07:17:99 2009 Sysname SSHS/7/MESSAGE: Received packet type 94.
*Dec 31 16:07:17:205 2009 Sysname SSHS/7/MESSAGE: Received packet type 94.
*Dec 31 16:07:17:306 2009 Sysname SSHS/7/MESSAGE: Received packet type 94.
*Dec 31 16:07:17:508 2009 Sysname SSHS/7/MESSAGE: Received packet type 94.
*Dec 31 16:07:17:520 2009 Sysname SSHS/7/MESSAGE: Prepare packet[98].
*Dec 31 16:07:17:523 2009 Sysname SSHS/7/MESSAGE: Prepare packet[96].
*Dec 31 16:07:17:525 2009 Sysname SSHS/7/MESSAGE: Prepare packet[97].
*Dec 31 16:07:17:719 2009 Sysname SSHS/7/MESSAGE: Received packet type 24.
*Dec 31 16:07:17:722 2009 Sysname SSHS/7/MESSAGE: Prepare packet[3].
- 2020-12-03回答
- 评论(2)
- 举报
-
(0)
交换机上没有 debug ssh server event 这个命令
尖括号视图找下,打问号看看


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明




尖括号视图找下,打问号看看