问题描述:
核心交换机上vlan配置如下,
interface Vlan-interface350
ip address 192.168.16.1 255.255.255.252
#
interface Vlan-interface3501
ip address 192.168.18.1 255.255.255.252
两个IP地址都可以远程登录核心交换机,核心内置防火墙板卡,IP配置为
interface Vlan-interface3500
ip address 192.168.17.1 255.255.255.252
#
interface Vlan-interface3501
ip address 192.168.18.2 255.255.255.252
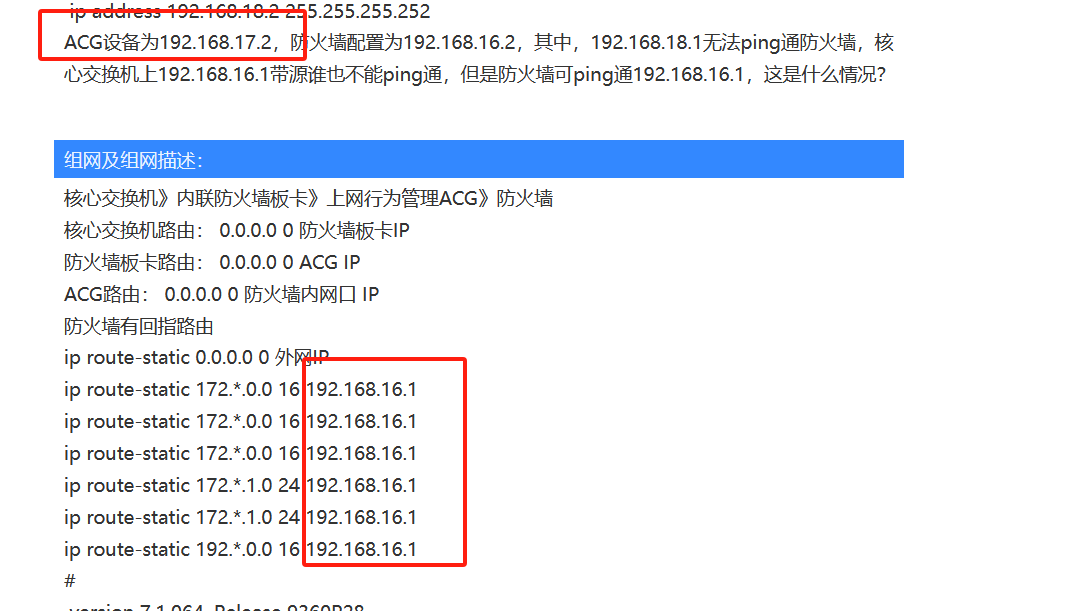
ACG设备为192.168.17.2,防火墙配置为192.168.16.2,其中,192.168.18.1无法ping通防火墙,核心交换机上192.168.16.1带源谁也不能ping通,但是防火墙可ping通192.168.16.1,这是什么情况?
组网及组网描述:
核心交换机》内联防火墙板卡》上网行为管理ACG》防火墙
核心交换机路由: 0.0.0.0 0 防火墙板卡IP
防火墙板卡路由: 0.0.0.0 0 ACG IP
ACG路由: 0.0.0.0 0 防火墙内网口 IP
防火墙有回指路由
ip route-static 0.0.0.0 0 外网IP
ip route-static 172.*.0.0 16 192.168.16.1
ip route-static 172.*.0.0 16 192.168.16.1
ip route-static 172.*.0.0 16 192.168.16.1
ip route-static 172.*.1.0 24 192.168.16.1
ip route-static 172.*.1.0 24 192.168.16.1
ip route-static 192.*.0.0 16 192.168.16.1
#
version 7.1.064, Release 9360P28
#
sysname BanGong-FIREWALL
#
clock timezone Beijing add 08:00:00
clock protocol ntp context 1
#
context Admin id 1
#
irf mac-address persistent timer
irf auto-update enable
irf auto-merge enable
undo irf link-delay
irf member 1 priority 1
#
nat log enable
nat log flow-begin
nat log flow-end
#
dns server 114.114.115.115
#
lldp global enable
#
ip subscriber access-user log enable successful-login failed-login logout normal abnormal
ipv6 subscriber access-user log enable successful-login failed-login logout normal abnormal
#
password-recovery enable
#
vlan 1
#
nqa template icmp nqa
reaction trigger per-probe
#
controller Cellular1/0/0
#
controller Cellular1/0/1
#
interface NULL0
#
interface GigabitEthernet1/0/0
port link-mode route
ip address 255.255.255.224
ip last-hop hold
nat outbound 2000
#
interface GigabitEthernet1/0/1
port link-mode route
ip address 192.168.16.2 255.255.255.252 \\内网口
nat hairpin enable
#
interface GigabitEthernet1/0/2
port link-mode route
ip address 255.255.255.128
ip last-hop hold
nat outbound 2000
nat hairpin enable
#
#
security-zone name Local
#
security-zone name Trust
import interface GigabitEthernet1/0/1
#
security-zone name DMZ
security-zone name Untrust
import interface GigabitEthernet1/0/0
import interface GigabitEthernet1/0/2
#
security-zone name Management
#
zone-pair security source Local destination Trust
packet-filter 2001
#
zone-pair security source Local destination Untrust
packet-filter 2001
#
zone-pair security source Trust destination Local
packet-filter 2001
#
zone-pair security source Trust destination Untrust
packet-filter 2001
#
zone-pair security source Untrust destination Local
packet-filter 2001
#
zone-pair security source Untrust destination Trust
packet-filter 2001
#
scheduler logfile size 16
#
line class aux
user-role network-operator
#
line class console
user-role network-admin
#
line class vty
user-role network-operator
#
line aux 0
user-role network-admin
#
line con 0
user-role network-admin
#
line vty 0 4
authentication-mode scheme
user-role level-15
#
line vty 5 63
authentication-mode scheme
user-role network-admin
#
ip route-static 0.0.0.0 0
#
customlog format nat unicom
customlog format security-policy sgcc
customlog host source GigabitEthernet1/0/2
#
snmp-agent
snmp-agent local-engineid 800063A2800440A9E7769B00000001
snmp-agent community read cipher $c$3$p7lUaGGoisMi7JCU/Rxz64pDYOYLjkFlY9Irbbw5EA==
snmp-agent community write cipher $c$3$2M0zL0LZ8mRV/c95y9NhjLsoKC5nXIEhPWNKxifcgw==
snmp-agent sys-info version all
snmp-agent target-host trap address udp-domain 172.20.1.100 params securityname Passw0rd@xt1
#
performance-management
#
ssh server enable
#
ntp-service enable
ntp-service source GigabitEthernet1/0/0
ntp-service unicast-peer version 1
#
acl basic 2000
rule 11 permit source 192.168.16.1 0 \\此配置属于核心交换机
rule 100 deny
#
acl basic 2001
rule 0 permit
rule 5 permit source 0.0.0.0 0
#
acl basic 2002
rule 0 permit source 0.0.0.0 255.255.0.0
rule 0 comment fw remote manage
#
acl advanced 3002
rule 0 permit ip destination 0
rule 5 permit ip destination 0
#
domain system
#
aaa session-limit ftp 16
aaa session-limit telnet 16
aaa session-limit ssh 16
domain default enable system
#
role name level-0
description Predefined level-0 role
#
role name level-1
description Predefined level-1 role
#
role name level-2
description Predefined level-2 role
#
role name level-3
description Predefined level-3 role
#
role name level-4
description Predefined level-4 role
#
role name level-5
description Predefined level-5 role
#
role name level-6
description Predefined level-6 role
#
role name level-7
description Predefined level-7 role
#
role name level-8
description Predefined level-8 role
#
role name level-9
description Predefined level-9 role
#
role name level-10
description Predefined level-10 role
#
role name level-11
description Predefined level-11 role
#
role name level-12
description Predefined level-12 role
#
role name level-13
description Predefined level-13 role
#
role name level-14
description Predefined level-14 role
#
user-group system
#
local-user adm class manage
password hash
service-type ssh telnet terminal http https
authorization-attribute user-role level-15
authorization-attribute user-role network-admin
#
public-key peer 127.0.0.1
public-key-code begin
public-key-code end
peer-public-key end
#
session statistics enable
session log flow-begin
session log flow-end
#
ip http port 103
ip https port 80
ip http enable
ip https enable
#
inspect logging parameter-profile av_logging_default_parameter
#
inspect logging parameter-profile ips_logging_default_parameter
#
inspect email parameter-profile mailsetting_default_parameter
undo authentication enable
#
loadbalance link-group china-isp
fail-action reschedule
transparent enable
probe nqa
#
loadbalance link-group cmcc
fail-action reschedule
transparent enable
probe nqa
#
loadbalance class chinanet type link-generic match-any
match 1 isp chinatel
#
loadbalance class cmcc type link-generic match-any
match 1 isp cmcc
#
loadbalance class server type link-generic
match 1 acl 3002
#
loadbalance action chinanet type link-generic
link-group china-isp
fallback-action continue
#
loadbalance action cmcc type link-generic
link-group cmcc
fallback-action continue
#
loadbalance action server type link-generic
forward all
fallback-action continue
#
loadbalance policy 1 type link-generic
class chinanet action chinanet
class cmcc action cmcc
class server action server
#
virtual-server outbound type link-ip
virtual ip address 0.0.0.0 0
lb-policy 1
default link-group cmcc
service enable
#
loadbalance link chinanet-link
router ip
link-group china-isp
probe nqa
#
loadbalance link cmcc-link
router ip
link-group cmcc
probe nqa
#
uapp-control
#
ips logging parameter-profile ips_logging_default_parameter
#
anti-virus logging parameter-profile av_logging_default_parameter
#
return
- 2024-06-19提问
- 举报
-
(0)

你画个图,在图上标出地址和路由,这样能方便看一写
你这个对劲么?
防火墙回指不是应该指向ACG么 你不是应该指向192.168.17.2 吗
- 2024-06-19回答
- 评论(9)
- 举报
-
(1)
好的,我试试
我试过了,不行,改完后连acg都ping不通了
不太确定是透明模式还是路由模式,acg的0口连接防火墙,IP地址是192.168.16.1,是 上联口,下联口是两个核心交换机的聚合端口,然后这个acg有一个0.0.0.0 0 192.168.16.2的路由,这是透明模式吗
那我描述就有问题了,这么看192.168.16.1是acg 的上联端口
,acg的0口连接防火墙,IP地址是192.168.16. 1 你不是说核心上Vlan-interface350 是这个地址么?不是地址冲突啊?
那我将核心的16.1的地址取消就能好了吗
这个去不了,好几个端口还继续用的这个vlan

interface GigabitEthernet1/0/1 该端口 需要允许ping
- 2024-06-19回答
- 评论(8)
- 举报
-
(0)
直接给远程码即可
已经试过了,不行,加了manage ping inbound\outbound,没啥用
那试一下 配置acl 然后在这个端口上调用一下acl number 3000 rule 0 permit icmp 将ACL应用到接口上:packet-filter 3000 inbound packet-filter 3000 outbound
防火墙ping路由 正常的话 就是icmp协议的问题了
方便的话 可以j直接远程给你看看
直接给远程码即可
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明


这个去不了,好几个端口还继续用的这个vlan