问题描述:
F1070防火墙结合IMC做Portal认证,终端无法自动弹出认证页面
防火墙版本为:Release 9360P46
IMCEIA版本为:E0632H07
防火墙上debugging portal all有如下报错:
是需要什么证书还是?下面客户端测试安卓苹果均不行
*Sep 12 22:56:55:925 2024 F1070 PORTAL/7/HTTP_REDIRECT-EVENT: -COntext=1; Receive the packet(flag:0x18,datalen:157,srcIP:10.66.66.4,dstIP:17.248.216.68,seq:0x429c8006,ack:0x7a,dataLen:157, sport:52538, dport:443)
*Sep 12 22:56:55:925 2024 F1070 PORTAL/7/HTTP_REDIRECT-EVENT: -COntext=1; Restructure success, Stream complete.
*Sep 12 22:56:55:925 2024 F1070 PORTAL/7/HTTP_REDIRECT-EVENT: -COntext=1; BIO wrote 157 bytes into SSL.
*Sep 12 22:56:55:925 2024 F1070 PORTAL/7/HTTP_REDIRECT-EVENT: -COntext=1; SSL negotiation message Recv Unknown TLS version [length 0005]unknown
*Sep 12 22:56:55:925 2024 F1070 PORTAL/7/HTTP_REDIRECT-EVENT: -COntext=1; SSL negotiation message Recv Unknown TLS version [length 0098]unknown
*Sep 12 22:56:55:925 2024 F1070 PORTAL/7/HTTP_REDIRECT-EVENT: -COntext=1; SSL negotiation message Send Unknown TLS version [length 0005]unknown
*Sep 12 22:56:55:925 2024 F1070 PORTAL/7/HTTP_REDIRECT-EVENT: -COntext=1; SSL negotiation message Send TLS 1.0 Alert [length 0002]unknown
*Sep 12 22:56:55:925 2024 F1070 PORTAL/7/HTTP_REDIRECT-ERROR: -COntext=1; Failed to accept SSL : error code=1, peek error=14209102.
*Sep 12 22:56:55:925 2024 F1070 PORTAL/7/HTTP_REDIRECT-EVENT: -COntext=1; Processed SSL handshake.
*Sep 12 22:56:55:925 2024 F1070 PORTAL/7/HTTP_REDIRECT-EVENT: -COntext=1; Compose RST reply packet.
*Sep 12 22:56:55:925 2024 F1070 PORTAL/7/HTTP_REDIRECT-EVENT: -COntext=1; Append tcp reply mbuf, mss=1024 len=20 seq=7a ack=429c80a3.
*Sep 12 22:56:55:925 2024 F1070 PORTAL/7/HTTP_REDIRECT-EVENT: -COntext=1; Send RST packet successfully.
*Sep 12 22:56:55:925 2024 F1070 PORTAL/7/HTTP_REDIRECT-EVENT: -COntext=1; Destroy RedirNode.
*Sep 12 22:57:00:114 2024 F1070 PORTAL/7/MAC-trigger Event: -COntext=1; Find MAC-trigger rule successfully.
*Sep 12 22:57:00:114 2024 F1070 PORTAL/7/MAC-trigger: -COntext=1;
组网及组网描述:
拓扑如下:
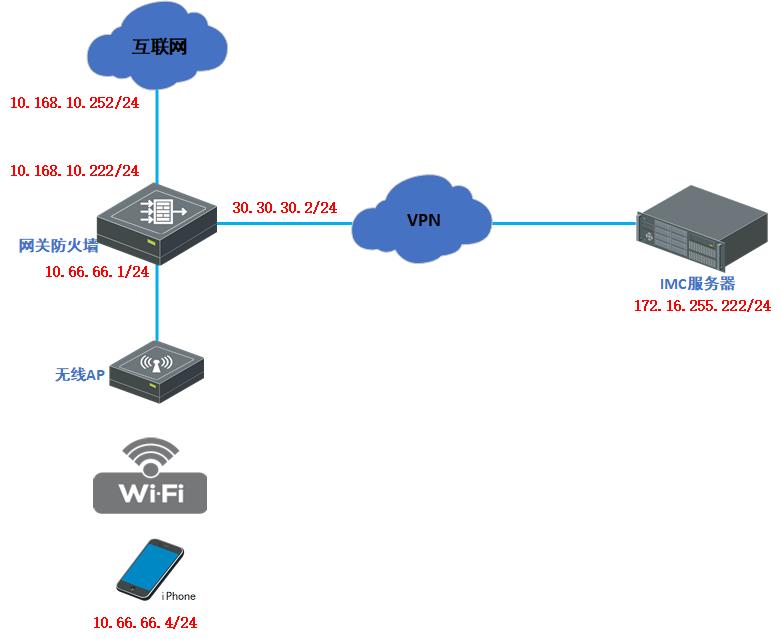
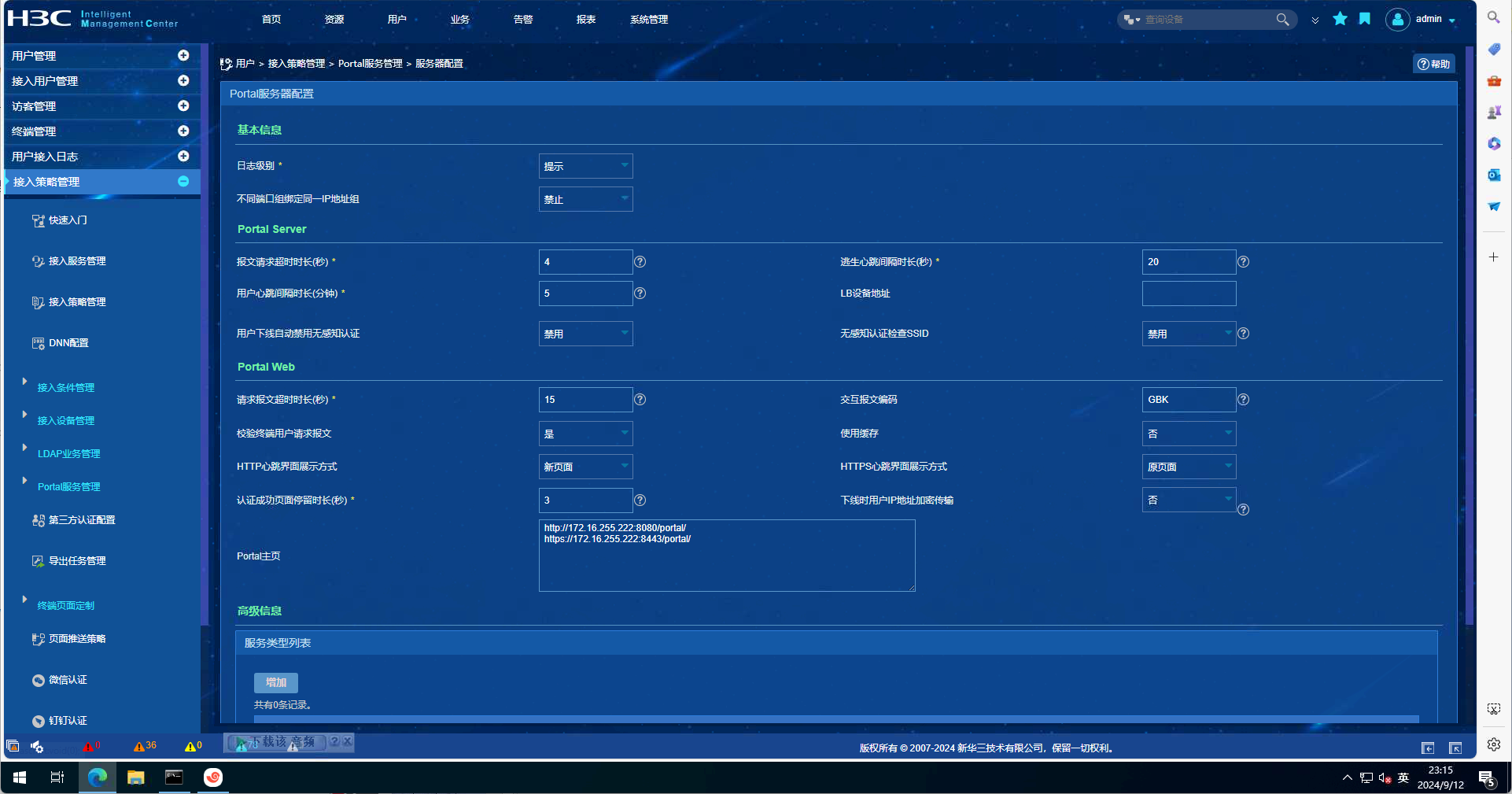
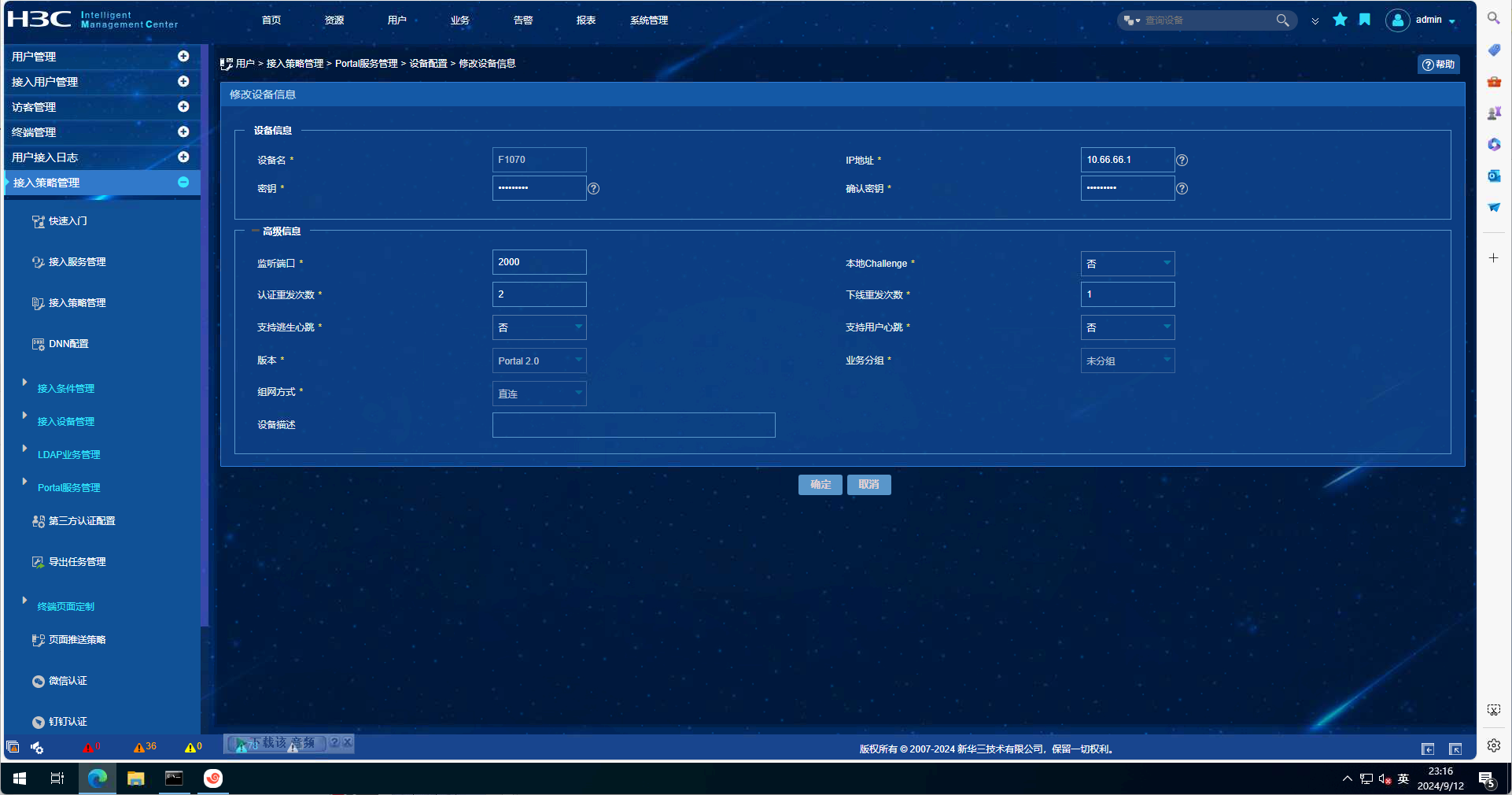
EIA配置截图如下:
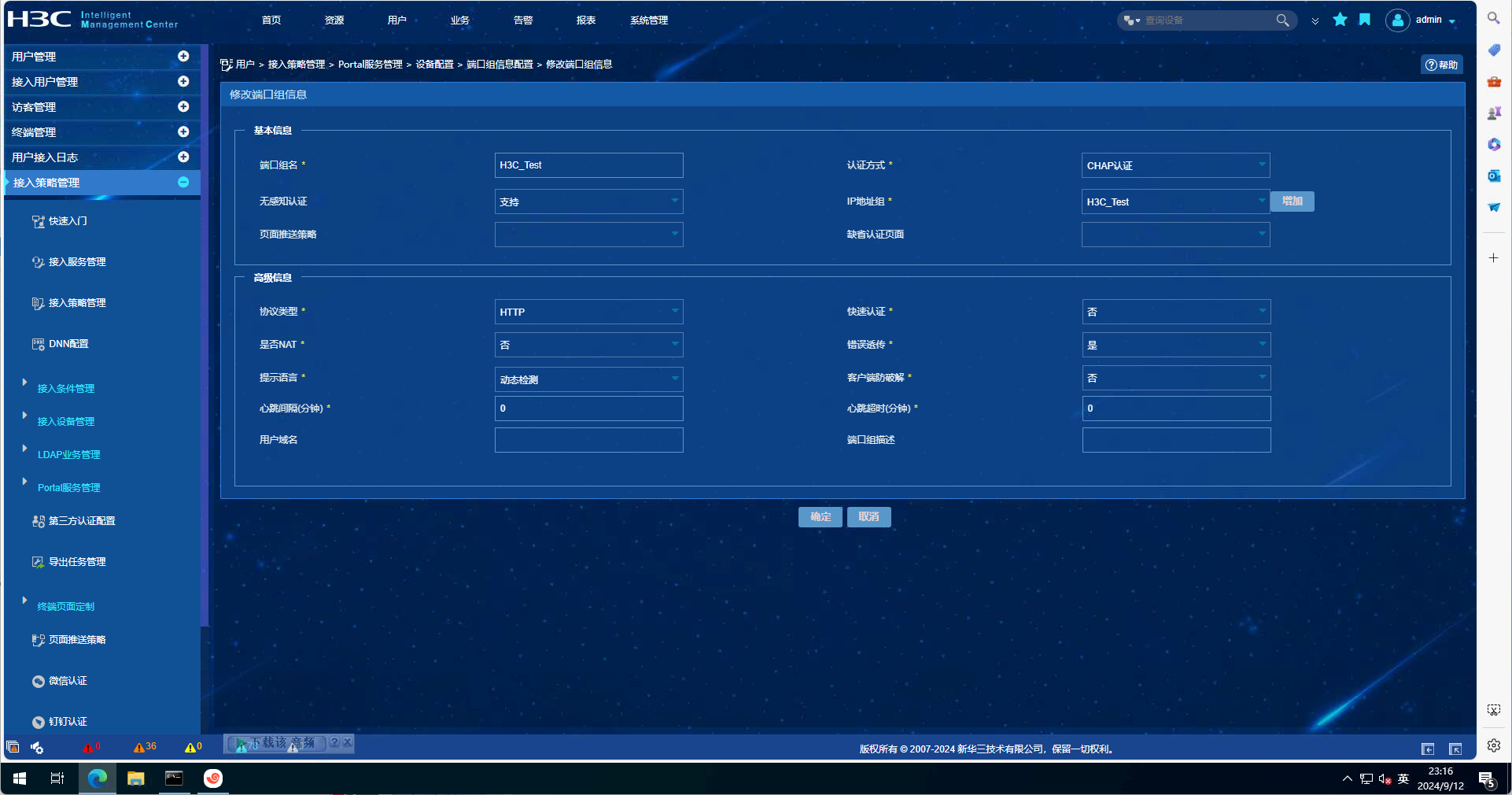
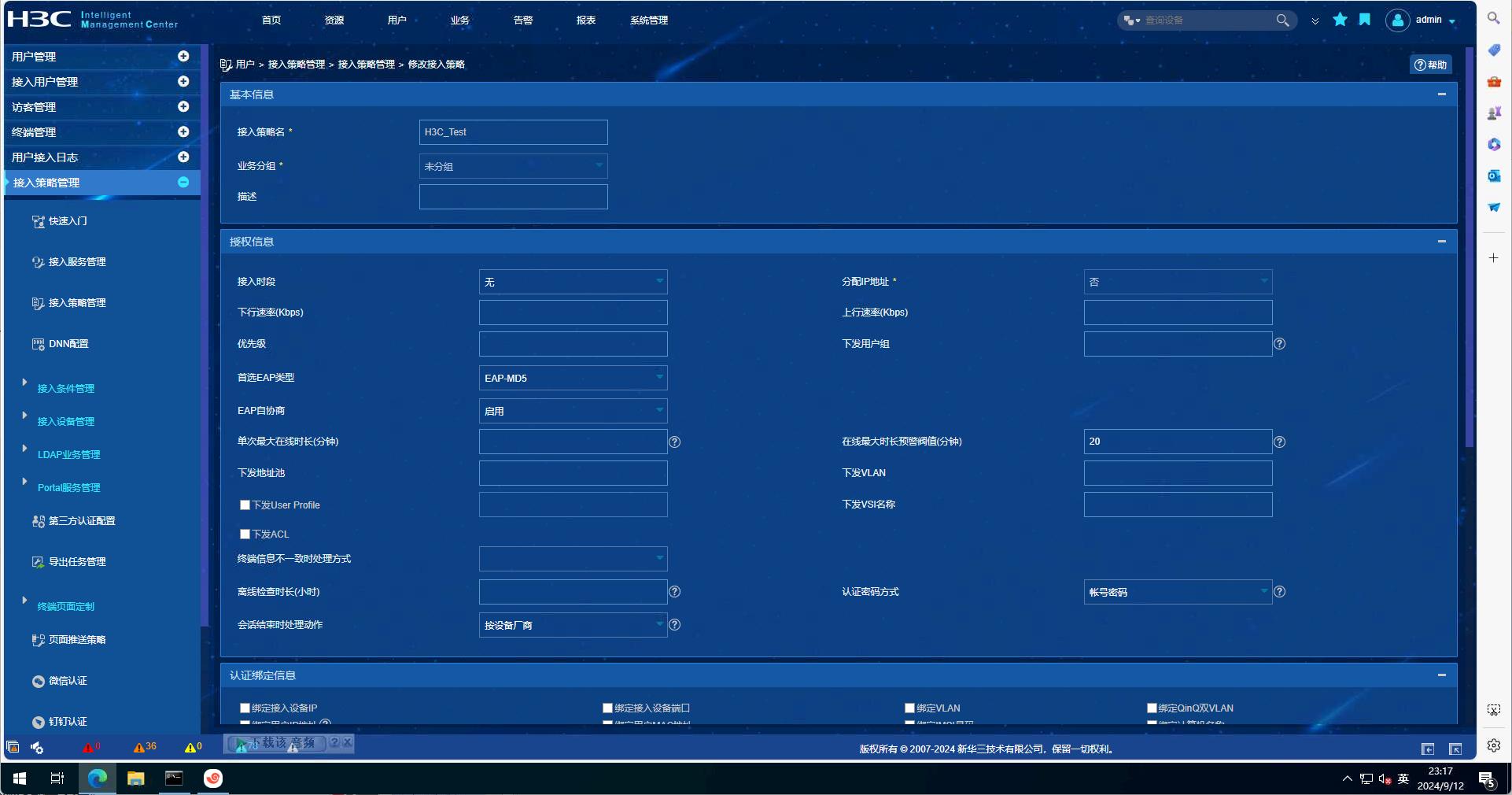
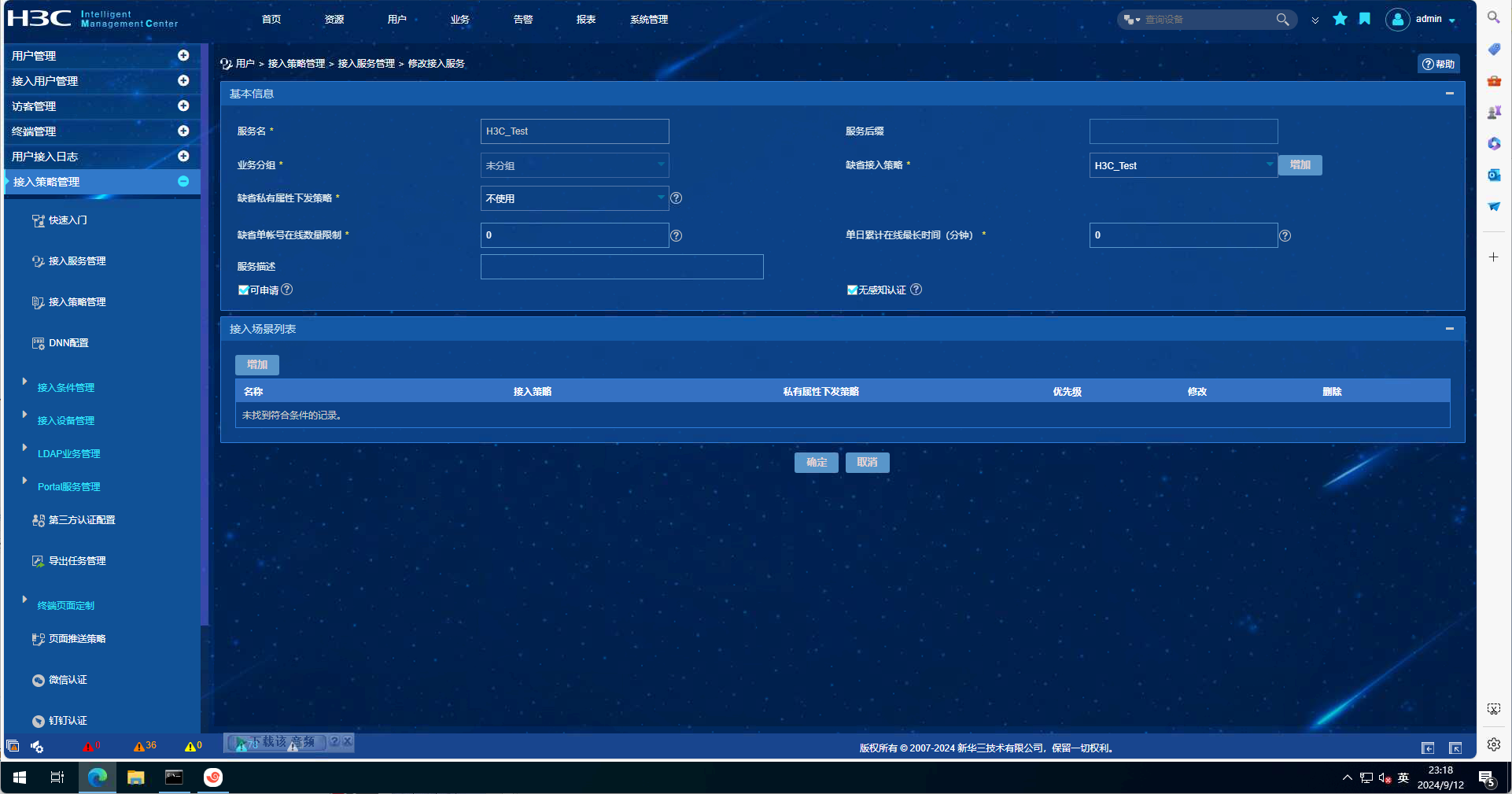
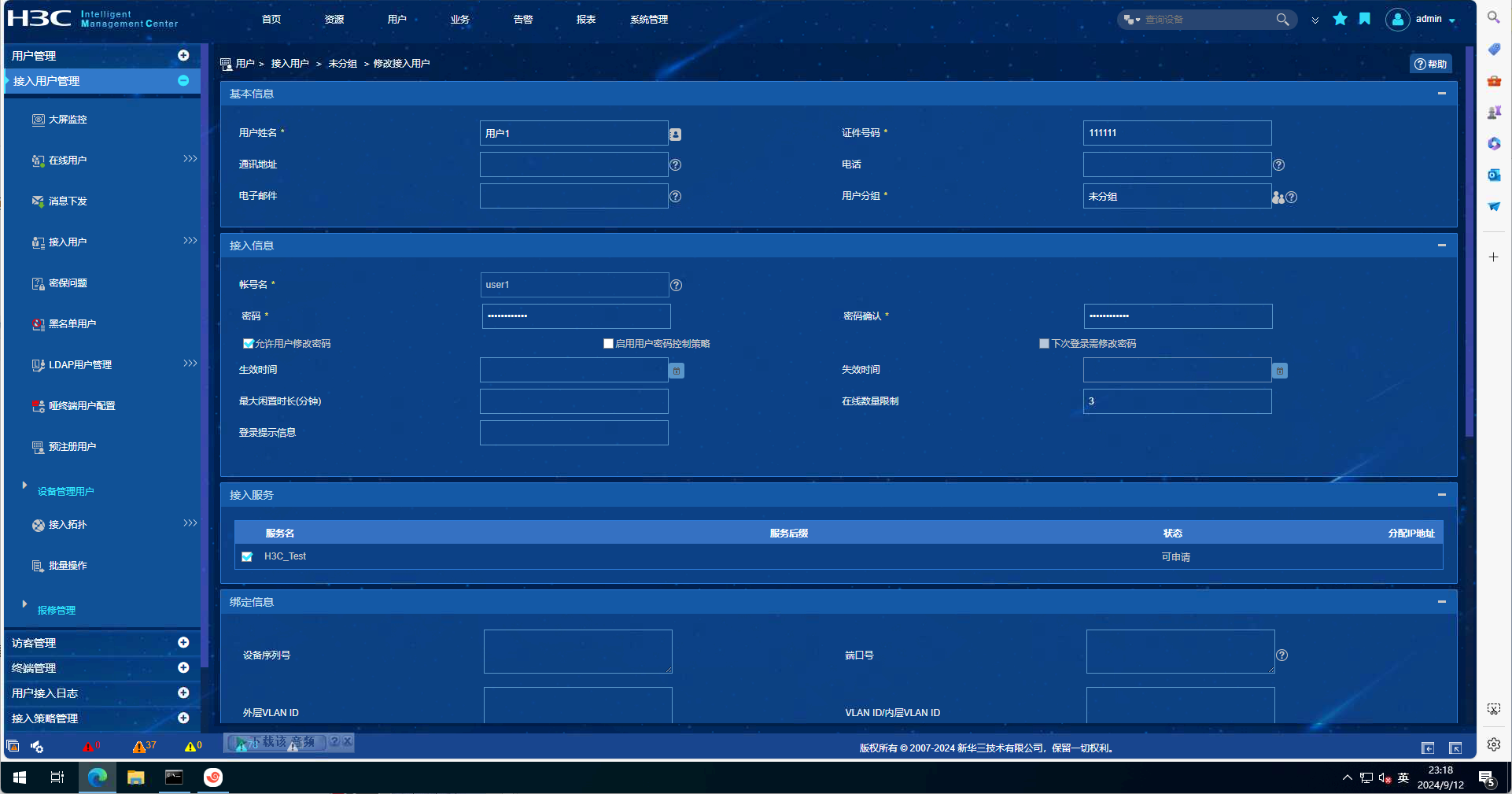
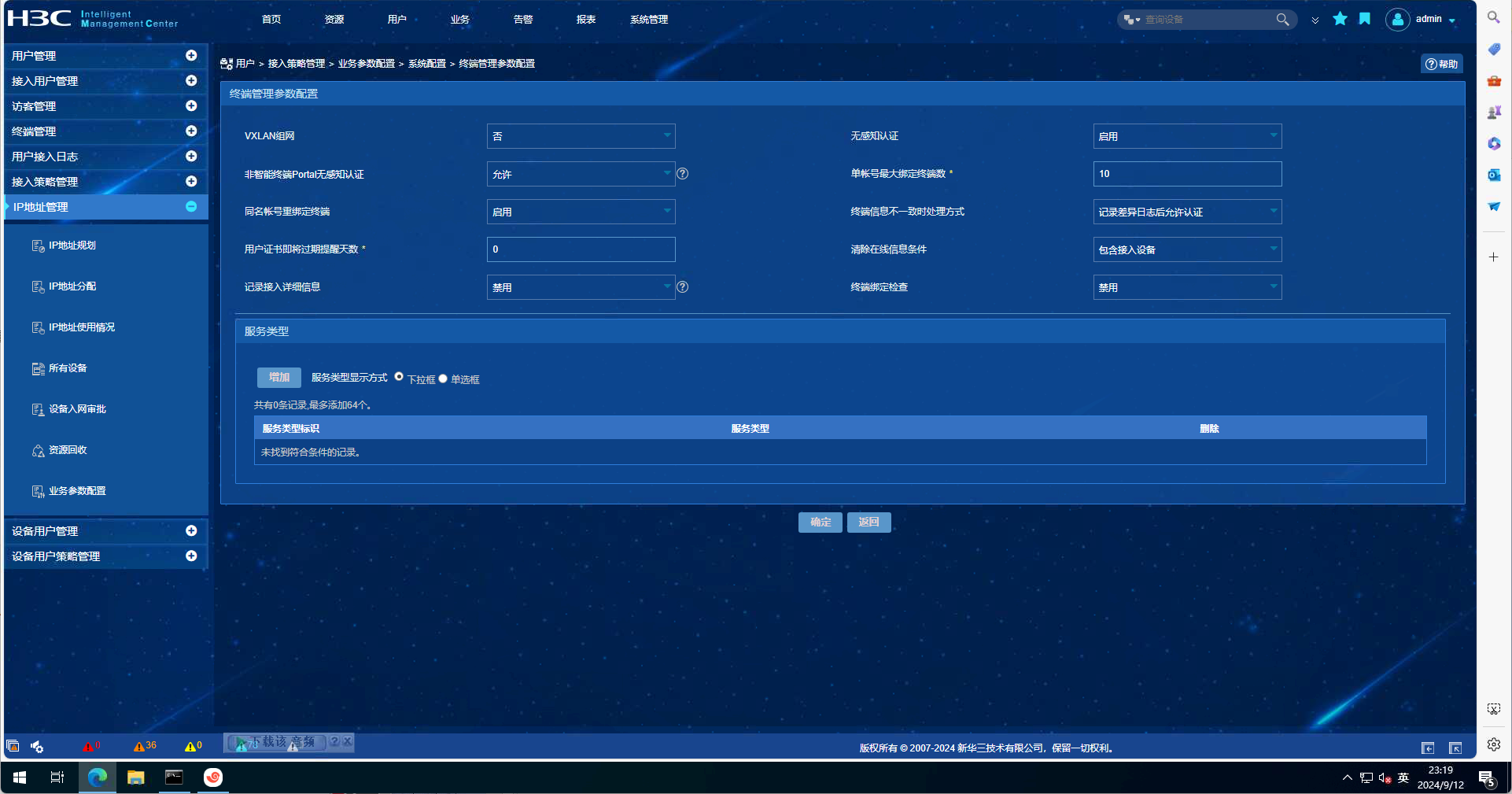
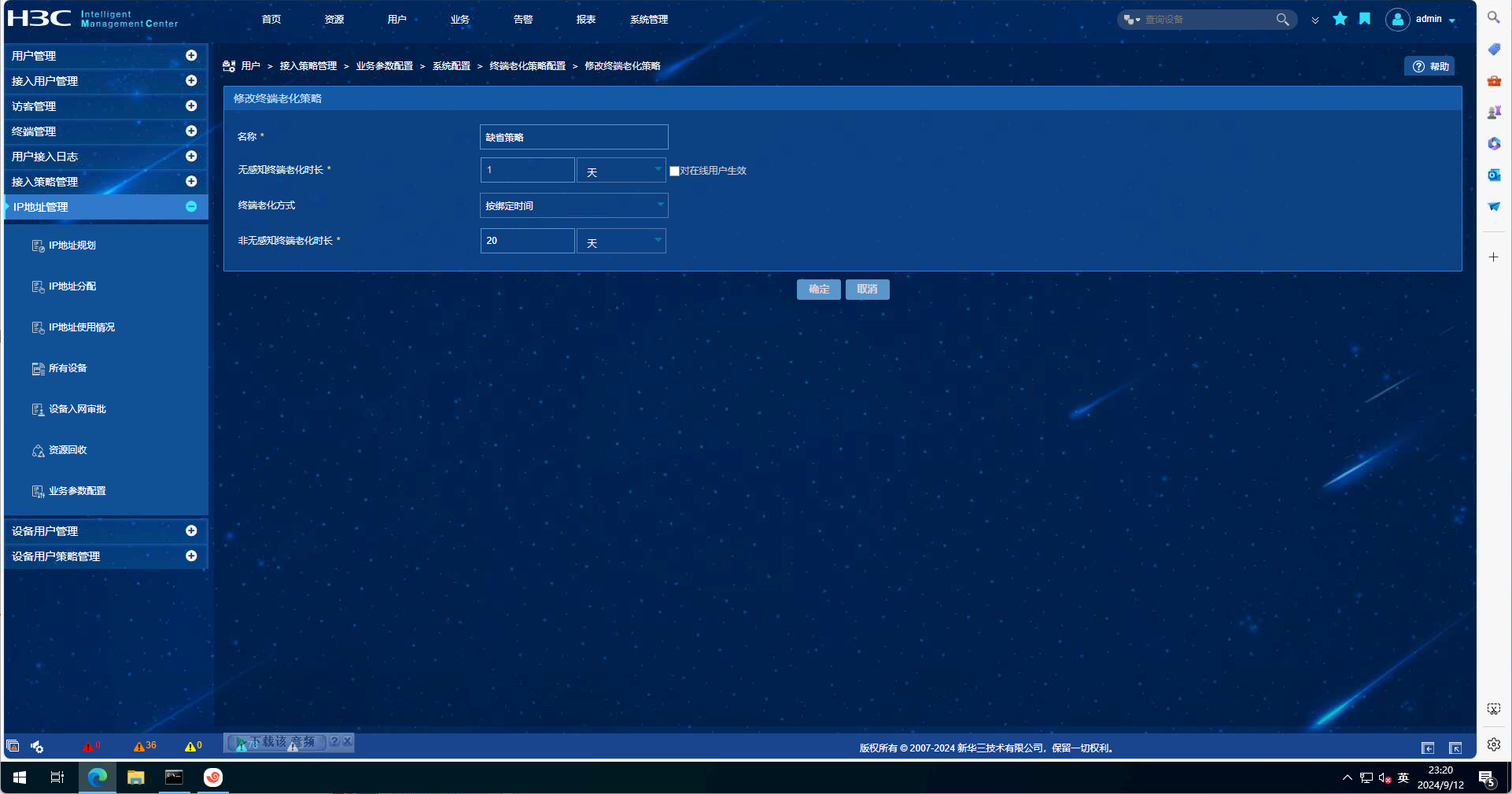
debugging信息如下:
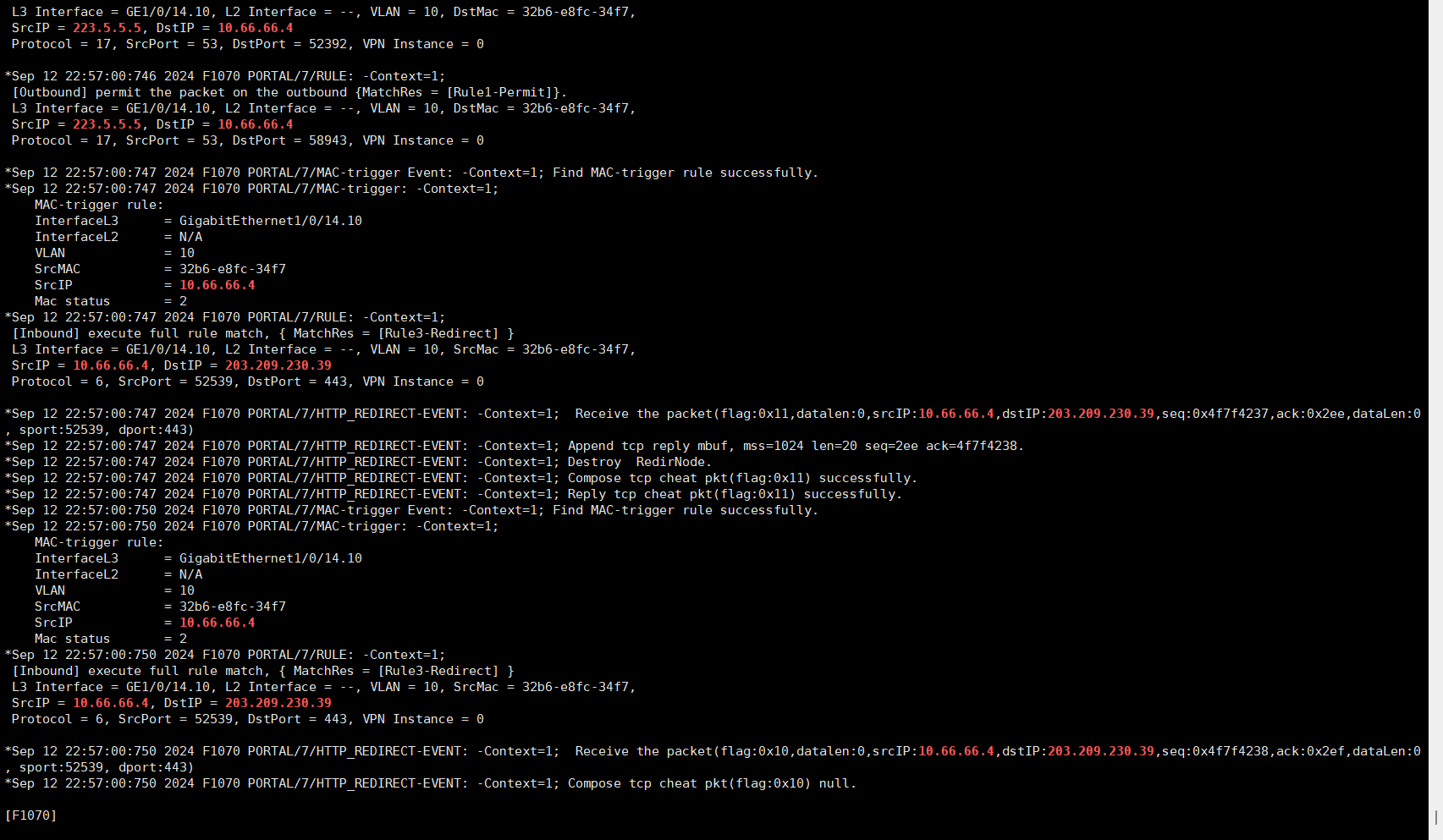
防火墙配置如下:
<F1070>DIS CU
#
version 7.1.064, Release 9360P46
#
sysname F1070
#
clock timezone Beijing add 08:00:00
clock protocol ntp context 1
#
context Admin id 1
#
telnet server enable
#
irf mac-address persistent timer
irf auto-update enable
irf auto-merge enable
undo irf link-delay
irf member 1 priority 1
#
ip unreachables enable
ip ttl-expires enable
#
dhcp enable
dhcp log enable
#
dns server 223.5.5.5
#
lldp global enable
#
password-recovery enable
#
vlan 1
#
dhcp server ip-pool 10
gateway-list 10.66.66.1
network 10.66.66.0 mask 255.255.255.0
dns-list 223.5.5.5 180.76.76.76
expired day 0 hour 8
#
controller Cellular1/0/0
#
controller Cellular1/0/1
#
interface Virtual-PPP0
ppp chap password cipher $c$3$hXR1PAI9dDANKY7iqwm1LJxlh1Bgf1E=
ppp chap user vpn
ip address ppp-negotiate
l2tp-auto-client l2tp-group 1
#
interface NULL0
#
interface GigabitEthernet1/0/0
port link-mode route
ip address 192.168.0.1 255.255.255.0
#
interface GigabitEthernet1/0/1
port link-mode route
#
interface GigabitEthernet1/0/2
port link-mode route
#
interface GigabitEthernet1/0/3
port link-mode route
#
interface GigabitEthernet1/0/4
port link-mode route
#
interface GigabitEthernet1/0/5
port link-mode route
#
interface GigabitEthernet1/0/6
port link-mode route
#
interface GigabitEthernet1/0/7
port link-mode route
#
interface GigabitEthernet1/0/8
port link-mode route
#
interface GigabitEthernet1/0/9
port link-mode route
#
interface GigabitEthernet1/0/10
port link-mode route
#
interface GigabitEthernet1/0/11
port link-mode route
#
interface GigabitEthernet1/0/12
port link-mode route
#
interface GigabitEthernet1/0/13
port link-mode route
#
interface GigabitEthernet1/0/14
port link-mode route
#
interface GigabitEthernet1/0/14.1
ip address 10.168.10.222 255.255.255.0
nat outbound 3000
vlan-type dot1q vid 1
#
interface GigabitEthernet1/0/14.10
ip address 10.66.66.1 255.255.255.0
vlan-type dot1q vid 10
portal enable method direct
portal bas-ip 10.66.66.1
portal apply web-server portal
portal apply mac-trigger-server imc
#
interface GigabitEthernet1/0/15
port link-mode route
ip address dhcp-alloc
#
interface GigabitEthernet1/0/16
port link-mode route
#
interface GigabitEthernet1/0/17
port link-mode route
#
interface GigabitEthernet1/0/18
port link-mode route
#
interface GigabitEthernet1/0/19
port link-mode route
#
interface GigabitEthernet1/0/20
port link-mode route
#
interface GigabitEthernet1/0/21
port link-mode route
#
interface GigabitEthernet1/0/22
port link-mode route
#
interface GigabitEthernet1/0/23
port link-mode route
#
interface Ten-GigabitEthernet1/0/24
port link-mode route
#
interface Ten-GigabitEthernet1/0/25
port link-mode route
#
security-zone name Local
#
security-zone name Trust
import interface GigabitEthernet1/0/14.10
#
security-zone name DMZ
#
security-zone name Untrust
import interface GigabitEthernet1/0/14.1
import interface GigabitEthernet1/0/15
import interface Virtual-PPP0
#
security-zone name Management
import interface GigabitEthernet1/0/0
#
scheduler logfile size 16
#
line class aux
user-role network-operator
#
line class console
user-role network-admin
#
line class vty
user-role network-operator
#
line aux 0
authentication-mode none
user-role 15
user-role network-admin
screen-length 512
history-command max-size 256
#
line con 0
user-role network-admin
#
line vty 0 3
authentication-mode scheme
user-role level-15
user-role network-admin
idle-timeout 3000 0
#
line vty 4
authentication-mode scheme
user-role level-15
user-role network-admin
#
line vty 5 63
authentication-mode scheme
user-role network-admin
#
ip route-static 0.0.0.0 0 10.168.10.252
ip route-static 172.16.255.222 32 30.30.30.1
#
performance-management
#
ssh server enable
sftp server enable
scp server enable
#
arp ip-conflict log prompt
#
acl advanced 3000
rule 1000 permit ip
#
radius session-control enable
#
radius scheme imc
primary authentication 172.16.255.222
primary accounting 172.16.255.222
key authentication cipher $c$3$o6yOrsyWwGd593dcVVQFJUnrLjJOFigrFKUnXQ==
key accounting cipher $c$3$uX9P6wXYRSaXSGrmJ7VaTOdXZjdfs9rq6/BH+Q==
user-name-format without-domain
#
domain portal
authentication portal radius-scheme imc
authorization portal radius-scheme imc
accounting portal radius-scheme imc
#
domain system
#
domain default enable portal
#
role name level-0
description Predefined level-0 role
#
role name level-1
description Predefined level-1 role
#
role name level-2
description Predefined level-2 role
#
role name level-3
description Predefined level-3 role
#
role name level-4
description Predefined level-4 role
#
role name level-5
description Predefined level-5 role
#
role name level-6
description Predefined level-6 role
#
role name level-7
description Predefined level-7 role
#
role name level-8
description Predefined level-8 role
#
role name level-9
description Predefined level-9 role
#
role name level-10
description Predefined level-10 role
#
role name level-11
description Predefined level-11 role
#
role name level-12
description Predefined level-12 role
#
role name level-13
description Predefined level-13 role
#
role name level-14
description Predefined level-14 role
#
user-group portal
authorization-attribute idle-cut 120
identity-member user user1
#
user-group system
#
ipsec logging negotiation enable
#
l2tp-group 1 mode lac
lns-ip 222.222.222.222
undo tunnel authentication
#
l2tp enable
#
ike logging negotiation enable
#
portal user log enable
portal free-rule 10 destination ip any udp 53
portal free-rule 20 destination ip 172.16.255.222 255.255.255.255
portal safe-redirect enable
portal safe-redirect user-agent Android
portal safe-redirect user-agent CaptiveNetworkSupport
portal safe-redirect user-agent MicroMessenger
portal safe-redirect user-agent Microsoft
portal safe-redirect user-agent Mozilla
portal safe-redirect user-agent WeChat
portal safe-redirect user-agent micromessenger
#
portal web-server portal
url http://172.16.255.222:8080/portal
#
portal server portal
ip 172.16.255.222 key cipher $c$3$MKND23gsQniXJE1QYi7fscMFUqw1cK+r18/IQg==
#
netconf soap http enable
netconf soap https enable
#
ip http enable
ip https enable
#
portal mac-trigger-server imc
ip 172.16.255.222
free-traffic threshold 102400
#
loadbalance isp file flash:/lbispinfo_v1.5.tp
#
user-identity enable
#
security-policy ip
rule 100 name Any-Any
action pass
logging enable
counting enable
#
return
- 2024-09-12提问
- 举报
-
(0)

您好:
终端连接网络后能否ping通认证页面的ip,手动输入是否能够跳转认证页面?
debug有提示到mac-trigger,是否配置的不正确?*Sep 12 22:57:00:114 2024 F1070 PORTAL/7/MAC-trigger Event: -COntext=1; Find MAC-trigger rule successfully.
- 2024-09-12回答
- 评论(1)
- 举报
-
(0)
手动在浏览器中输入网址可以打开portal认证页面

找到问题了,无感知的配置,配置了用户流量阈值
portal mac-trigger-server imc
ip 172.16.255.222
free-traffic threshold 102400
#
设备开启了基于MAC地址的快速认证功能时,可以配置用户在上线后有一定的免认证流量。设备会在MAC-trigger表项老化之前实时检测Portal用户收发的流量。当用户收发的流量还未达到设定的阈值时,允许用户访问外部网络资源
- 2024-09-12回答
- 评论(0)
- 举报
-
(0)
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明


手动在浏览器中输入网址可以打开portal认证页面