L1090双机做出口负载案例
- 0关注
- 0收藏,1298浏览

防火墙设备上的关键配置(防火墙需要放通对应的安全策略,不再赘述):
#
interface Dialer1
ppp pap local-user test password cipher $c$3$HKrN4hJRbFiItP6JBbSKn6sjYufU8w==
dialer bundle enable
dialer-group 1
dialer timer idle 0
ip address ppp-negotiate
nat outbound
//先做拨号口的配置,在测试当中拨号口获取的地址是20.0.0.1
#
nqa template icmp nqa1
destination ip 20.0.0.254
out interface Dialer1
//创建PPPOE链路所用的ICMP健康性检测模板,指定探测的出接口和目的地址,这个目的地址根据现场实际情况来定
#
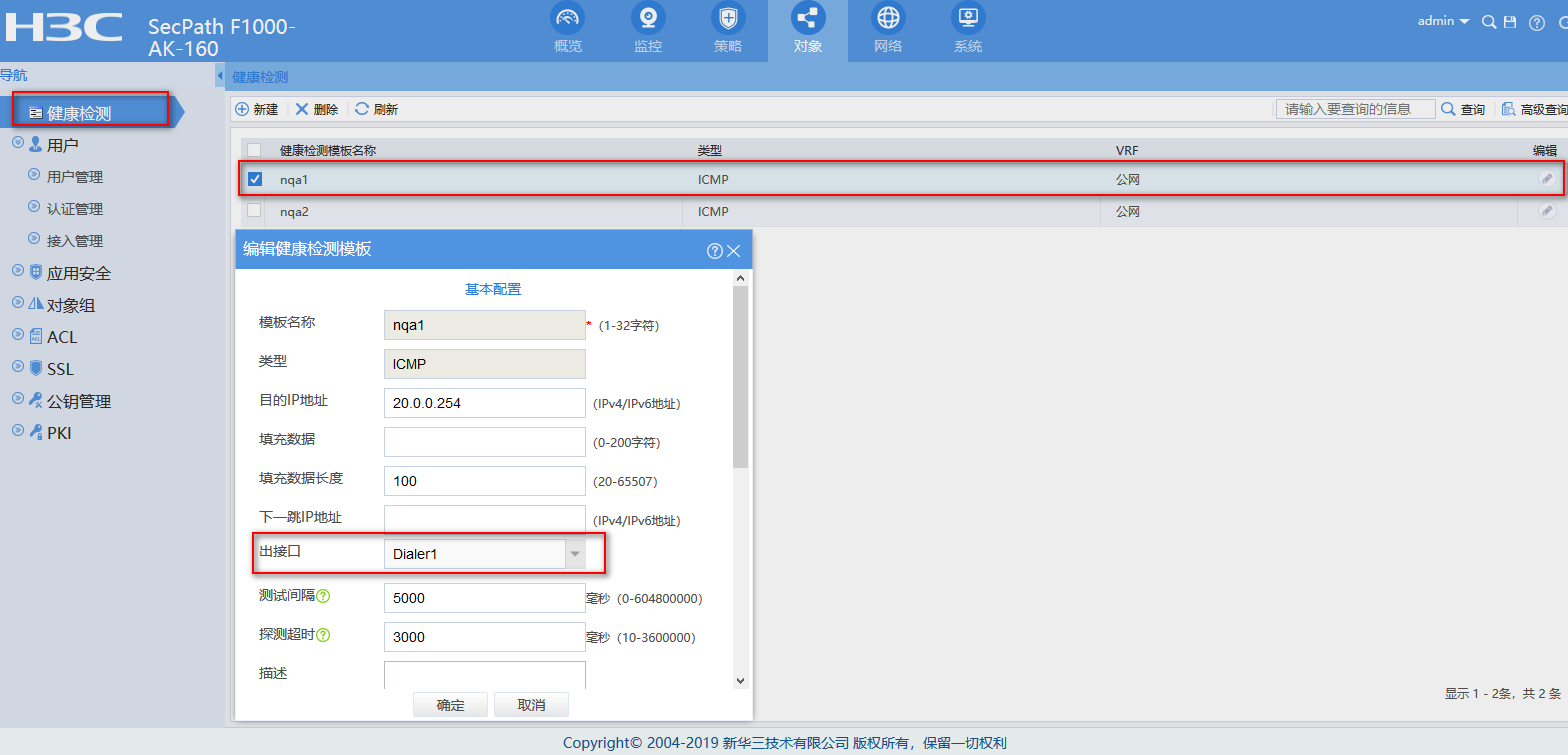
nqa template icmp nqa2
//创建固定IP链路所用的ICMP健康性检测模板,无须指定目的,会自动探测链路的router ip
#
interface GigabitEthernet2/0/1
port link-mode route
ip address A.A.A.A 255.255.255.0
//内网网关的配置,测试当中内网用户网关地址为10.0.0.1,到时请根据实际情况配置
#
interface GigabitEthernet2/0/2
port link-mode route
pppoe-client dial-bundle-number 1 //拨号口绑定
#
interface GigabitEthernet2/0/3
port link-mode route
ip address B.B.B.B 255.255.255.0
nat outbound
//固定IP的链路配置,测试当中配置的是30.0.0.2,现网中请按照实际情况配置
#
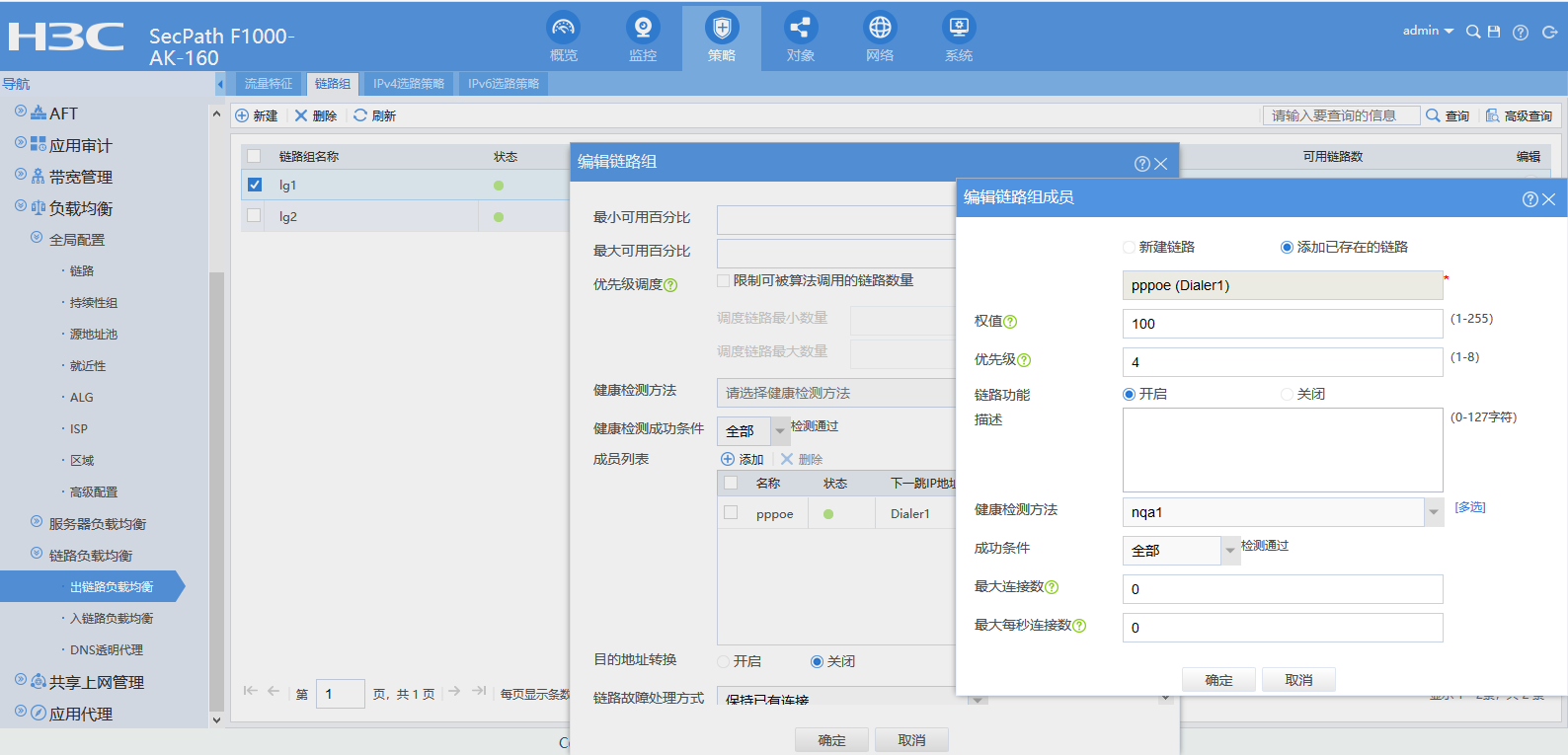
loadbalance link-group lg1
transparent enable
//创建链路组lg1,一定要记得关闭链路组当中的NAT转换,也就是说要配置transparent enable命令
#
loadbalance link-group lg2
transparent enable //创建链路组lg2
#
loadbalance class pppoe type link-generic match-any
match 1 acl 3001 //创建负载均衡类,acl 3001
#
acl advanced 3001
rule 0 permit ip source 10.0.0.2 0
// acl 3001当中放通地址10.0.0.2,负载均衡类的配置要结合现场实际需求来做,此处只是举例。
#
loadbalance class iplink type link-generic match-any
match 1 acl 3002 //创建负载均衡类,acl 3002
#
acl advanced 3002
rule 0 permit ip source 10.0.0.3 0
// acl 3002当中放通地址10.0.0.3,负载均衡类的配置要结合现场实际需求来做,此处只是举例。
#
loadbalance action pppoe type link-generic
link-group lg1 //创建负载均衡动作,让流量走链路组lg1
#
loadbalance action iplink type link-generic
link-group lg2 //创建负载均衡动作,让流量走链路组lg2
#
loadbalance policy test type link-generic
class pppoe action pppoe //让class为pppoe的流量执行action为pppoe的负载均衡动作
class iplink action iplink //让class为iplink的流量执行action为iplink的负载均衡动作
default-class action iplink //其他流量执行action为iplink的负载均衡动作
#
virtual-server test_pppoe type link-ip
virtual ip address 0.0.0.0 0
lb-policy test
service enable //创建虚服务,调用名为test的负载均衡策略
#
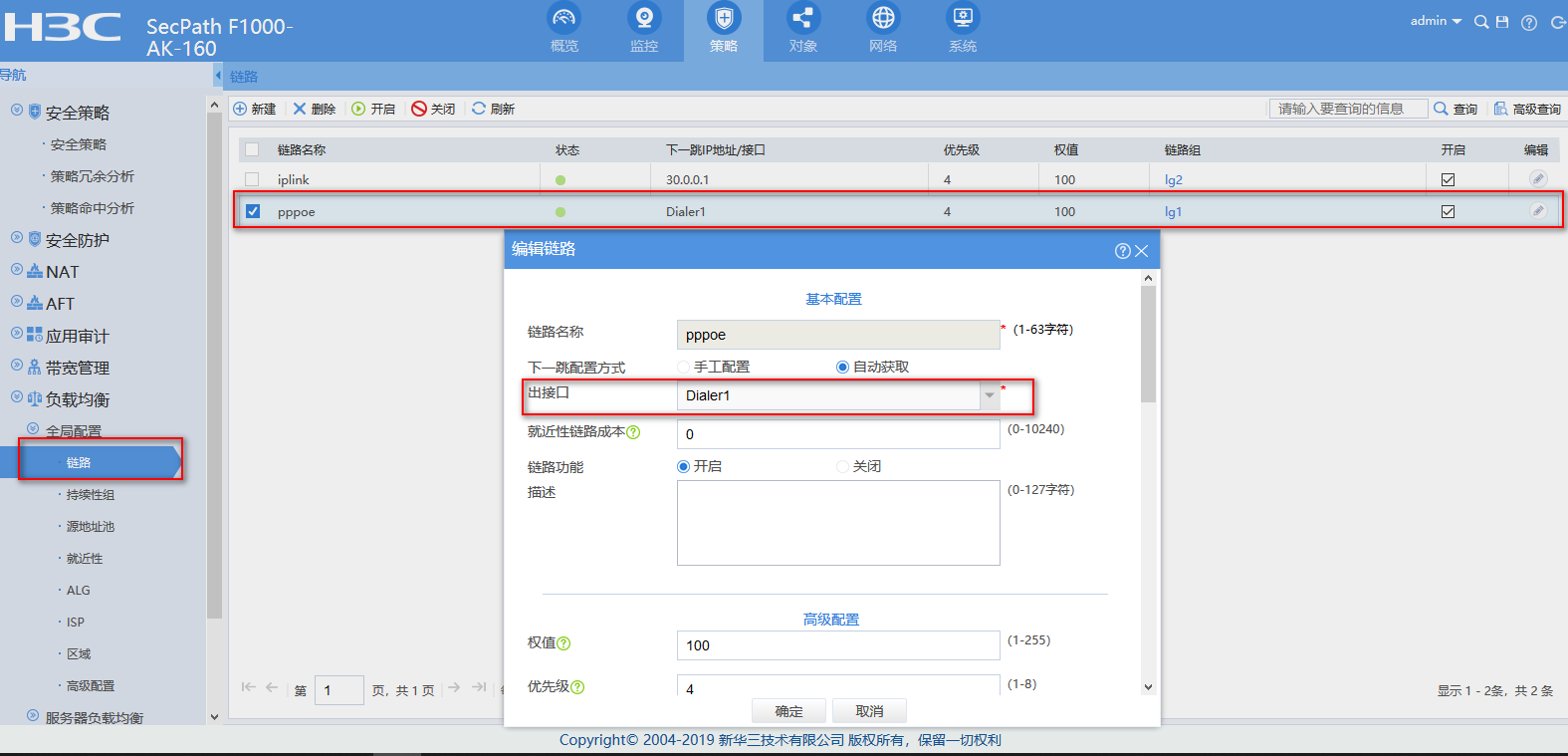
loadbalance link pppoe
router interface Dialer1
link-group lg1
probe nqa1
//创建链路pppoe属于链路组lg1,出接口为dialer口,健康性检测调用nqa1
#
loadbalance link iplink
router ip 30.0.0.1
link-group lg2
probe nqa2
//创建链路固定ip属于链路组lg2,下一跳30.0.0.1,健康性检测调用nqa2
#
关键配置的web界面配置:
创建负载均衡类:
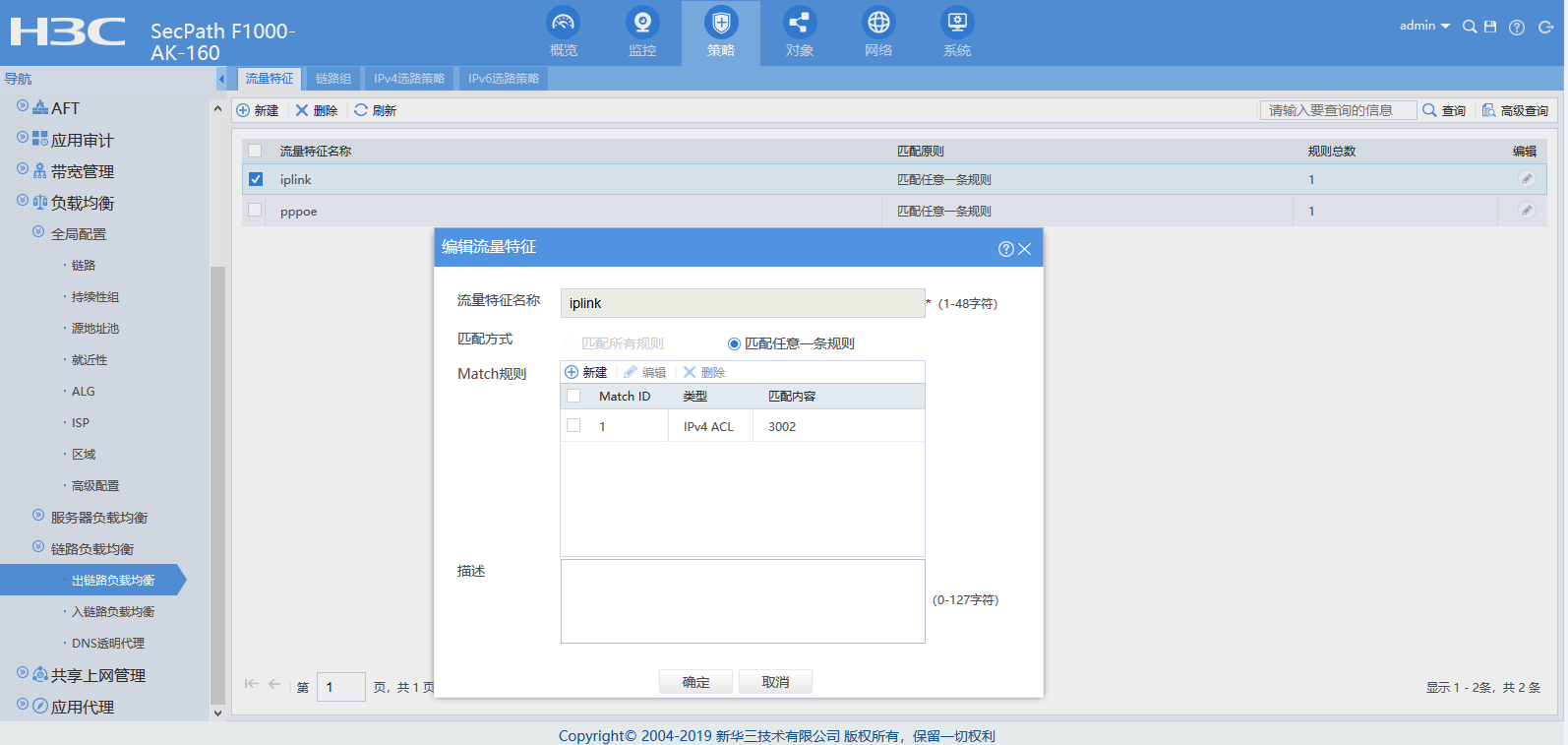

创建PPPOE链路健康性检测模板:
创建固定IP链路:

创建PPPOE链路:
创建链路组:

配置完成之后可以通过会话信息测试:
当PC1的地址为10.0.0.2时,匹配acl 3001,会话信息如下:
Slot 2:
Initiator:
Source IP/port: 10.0.0.2/1
Destination IP/port: 40.0.0.2/2048
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: ICMP(1)
Inbound interface: GigabitEthernet2/0/1
Source security zone: Trust
Responder:
Source IP/port: 40.0.0.2/2
Destination IP/port: 20.0.0.1/0 //nat outbound转换成了pppoe的接口地址
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: ICMP(1)
Inbound interface: Dialer1 //回包入接口是dialer口
Source security zone: dialer
State: ICMP_REPLY
Application: ICMP
Rule ID: 0
Rule name: pass
Start time: 2019-12-20 21:07:08 TTL: 25s
Initiator->Responder: 4 packets 240 bytes
Responder->Initiator: 4 packets 240 bytes //来回报文都有
当PC1的地址为10.0.0.2时,匹配acl 3001,会话信息如下:
Slot 2:
Initiator:
Source IP/port: 10.0.0.3/1
Destination IP/port: 40.0.0.2/2048
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: ICMP(1)
Inbound interface: GigabitEthernet2/0/1
Source security zone: Trust
Responder:
Source IP/port: 40.0.0.2/26
Destination IP/port: 30.0.0.2/0 //NAT 转换成了固定IP接口的地址
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: ICMP(1)
Inbound interface: GigabitEthernet2/0/3 //回包入接口是固定IP地址接口
Source security zone: Untrust
State: ICMP_REPLY
Application: ICMP
Rule ID: 0
Rule name: pass
Start time: 2019-12-20 21:06:15 TTL: 23s
Initiator->Responder: 4 packets 240 bytes
Responder->Initiator: 4 packets 240 bytes
- 2024-12-26回答
- 评论(0)
- 举报
-
(0)
暂无评论
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明



暂无评论