MSR36-60 vlan问题,接口问题
- 0关注
- 0收藏,2600浏览
问题描述:
MSR36-60 设备一台,没有增加板卡,用主机自带的三个网口,其中GE2配置interface GigabitEthernet0/2;port link-mode bridge; port access vlan 244;设置了一个VLAN244 ,并且在VLANif中设置ip地址 192.168.233.1 24 ,将笔记本接GE2下配置192.168.233.100 无法与VLANif (192.168.233.1)通信,这是怎么回事啊?
- 2025-05-21提问
- 举报
-
(0)
最佳答案

你的问题是:在 H3C MSR36-60 路由器上,将 GE2 设置为 access 模式并加入 VLAN 244,同时给 VLAN 244 的三层接口 Vlan-interface 244 配了 IP 地址 192.168.233.1/24,但笔记本接在 GE2(配置 IP 为 192.168.233.100)无法与网关通信。
🔍 快速问题定位逻辑
这类问题通常可以从以下几个方向入手排查:
✅ 1. VLAN 是否与物理接口绑定成功?
请确认是否 VLAN 244 已生效,并且绑定在了 GE2 接口上:
[MSR] display vlan 244
输出应该包含 GE2 接口:
VID Type Ports
244 static GE2
如果 Ports 一栏没有包含 GE2,说明 port access vlan 244 没有生效或 VLAN 没有创建成功。
如果 VLAN 244 没有创建,可以先执行:
[MSR] vlan 244
[MSR-vlan244] quit
✅ 2. VLAN 接口(Vlan-interface 244)是否 up?
执行:
[MSR] display interface Vlan-interface 244
你应该看到 Line protocol is UP。如果显示 down,说明三层接口没有“活”起来,常见原因是:
-
没有任何物理口属于 VLAN 244;
-
或者所有下属物理口都是
down状态;
👉 请检查 GE2 接口状态:
[MSR] display interface GigabitEthernet 0/2
确认它是 up 状态。
✅ 3. 笔记本物理链路是否 up?
简单办法:
-
看网卡灯是否亮;
-
在笔记本执行
ping 192.168.233.1是否返回 "Destination host unreachable"(说明链路断); -
再执行:
arp -a看看是否有路由器的 MAC 地址。
✅ 4. 是否配置了 port link-mode bridge
你写了如下配置:
interface GigabitEthernet 0/2
port link-mode bridge
port access vlan 244
这个配置是正确的。只要你使用 port link-mode bridge 并配置 access vlan,路由器就会按 L2 模式接入 VLAN 244。
如果你不使用 port link-mode bridge,MSR 默认是路由(L3)口,不能加入 VLAN。
✅ 5. 是否有防火墙/ACL 等阻挡?
-
MSR 有可能默认配置了 ACL、Zone、防火墙策略。
-
如果你用了安全域(security-zone),请检查是否存在禁止规则。
你可以暂时清除所有 ACL 做测试:
[MSR] undo packet-filter inbound
[MSR] undo packet-filter outbound
✅ 正确的最小可用配置示例
以下是一个最小可用配置,建议你对比一下:
vlan 244
interface GigabitEthernet 0/2
port link-mode bridge
port access vlan 244
interface Vlan-interface 244
ip address 192.168.233.1 255.255.255.0
🧪 补充测试建议
-
在笔记本上抓包(用 Wireshark)看是否能收到 ARP 请求或应答;
-
从路由器上
ping 192.168.233.100,看是否能双向; -
尝试从 MSR 上抓包:
[MSR] debugging packet vlan 244
✅ 总结可能原因及对应处理
| 问题 | 排查建议 |
|---|---|
| VLAN 未正确创建 | display vlan 244,是否有 GE2 接口 |
| 接口没 up | display interface 看 GE2 和 Vlan-interface 是否都 up |
| 接口未加入 VLAN | port access vlan 244 是否配置生效 |
| 物理线缆问题 | 换线缆或确认网卡灯是否亮 |
| 防火墙/安全域拦截 | 检查是否配置 zone、ACL、packet-filter |
- 2025-05-21回答
- 评论(0)
- 举报
-
(0)


正常来说不会不通的
你配置能发一下看一下吗?
- 2025-05-21回答
- 评论(16)
- 举报
-
(0)
你好,配置已经贴出,麻烦帮忙排查一下。
重新修改了,麻烦您看看,这个基础的错误还是不可能出现的


[MSR36-60]dis cu
#
version 7.1.064, Release 0707P21
#
sysname MSR36-60
#
telnet server enable
#
ip pool l2tp997 192.168.100.2 192.168.100.254
#
dhcp enable
dhcp server always-broadcast
#
dns proxy enable
dns server 221.7.1.20
#
password-recovery enable
#
vlan 1
#
vlan 233
#
vlan 244
#
controller Cellular0/0
#
controller Cellular0/1
#
interface Aux0
#
interface Virtual-Template0
#
interface Virtual-Template1
remote address pool l2tp997
ip address 192.168.100.1 255.255.255.0
#
interface NULL0
#
interface Vlan-interface233
#
interface Vlan-interface244
ip address 192.168.233.1 255.255.255.0
local-proxy-arp enable
tcp mss 1460
#
interface GigabitEthernet0/0
port link-mode route
combo enable copper
ip address 124.88.XX.XX 255.255.255.128
tcp mss 1280
nat outbound 3999
undo dhcp select server
ipsec apply policy XBBZ123
#
interface GigabitEthernet0/1
port link-mode route
combo enable copper
ip address 192.168.1.1 255.255.255.0
#
interface GigabitEthernet0/2
port link-mode bridge
port access vlan 244
#
object-policy ip Any-Any
rule 0 pass time-range any
#
security-zone name Local
#
security-zone name Trust
#
security-zone name DMZ
#
security-zone name Untrust
#
security-zone name Management
#
zone-pair security source Any destination Any
object-policy apply ip Any-Any
#
scheduler logfile size 16
#
line class aux
user-role network-admin
#
line class tty
user-role network-operator
#
line class vty
user-role network-operator
#
line aux 0
user-role network-admin
#
line vty 0 5
authentication-mode scheme
user-role network-operator
protocol inbound ssh
#
line vty 6 63
authentication-mode scheme
user-role network-operator
#
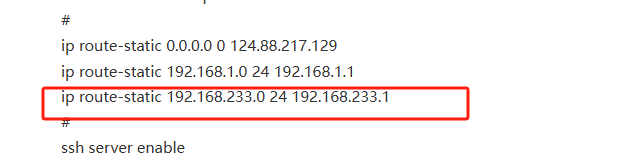
ip route-static 0.0.0.0 0 124.88.XX.XX
#
ssh server enable
ssh user admin service-type stelnet authentication-type password
ssh server port 65535
#
undo gratuitous-arp-learning enable
#
acl advanced 3999
rule 2 deny ip source 192.168.1.0 0.0.0.255 destination 192.168.200.0 0.0.0.255
rule 3 permit ip source 192.168.233.0 0.0.0.255
rule 100 permit ip
#
password-control enable
undo password-control aging enable
undo password-control history enable
password-control length 6
password-control login-attempt 3 exceed lock-time 10
password-control update-interval 0
password-control complexity user-name check
#
domain system
#
domain default enable system
#
role name level-0
description Predefined level-0 role
#
role name level-1
description Predefined level-1 role
#
role name level-2
description Predefined level-2 role
#
role name level-3
description Predefined level-3 role
#
role name level-4
description Predefined level-4 role
#
role name level-5
description Predefined level-5 role
#
role name level-6
description Predefined level-6 role
#
role name level-7
description Predefined level-7 role
#
role name level-8
description Predefined level-8 role
#
role name level-9
description Predefined level-9 role
#
role name level-10
description Predefined level-10 role
#
role name level-11
description Predefined level-11 role
#
role name level-12
description Predefined level-12 role
#
role name level-13
description Predefined level-13 role
#
role name level-14
description Predefined level-14 role
#
user-group system
#
local-user admin class manage
service-type ssh telnet terminal http https
authorization-attribute user-role network-admin
#
local-user guanli class manage
authorization-attribute user-role network-operator
#
local-user root class manage
service-type ftp
service-type ssh telnet terminal http https
authorization-attribute user-role network-admin
authorization-attribute user-role network-operator
#
ipsec transform-set XBBZ123
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
#
ipsec policy-template XBBZ123 65534
transform-set XBBZ123
ike-profile XBBZ123
sa duration time-based 3600
sa duration traffic-based 1843200
#
ipsec policy XBBZ123 65534 isakmp template XBBZ123
#
l2tp-group 997 mode lns
allow l2tp virtual-template 1 remote kpx4g
tunnel name kpx
tunnel password cipher $c$3$fCOm
#
l2tp enable
#
ike profile XBBZ123
keychain XBBZ123
dpd interval 60 on-demand
exchange-mode aggressive
local-identity address 124.88.XX.XX
match remote identity address 0.0.0.0 0.0.0.0
proposal 65534
#
ike proposal 65534
encryption-algorithm 3des-cbc
dh group2
authentication-algorithm md5
#
ike keychain XBBZ123
pre-shared-key address 0.0.0.0 0.0.0.0 key cipher $c$3$2riRn
#
ip http port 65534
ip https port 4433
ip http enable
ip https enable
#
wlan global-configuration
#
wlan ap-group default-group
vlan 1
#
return
[MSR36-60]
- 2025-05-21回答
- 评论(0)
- 举报
-
(0)
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明

