防火墙怎么针对某个网段进行白名单式网址过滤
- 0关注
- 0收藏,1219浏览
问题描述:
在H3C防火墙上,要针对某个网段进行URL访问白名单,具体应该怎么操作了?在ds上问了很多次,都没法操作成功
防火墙的型号是SecPath F1000-AI-35,软件版本是version 7.1.064, Release 8860P12。
1. 创建 URL 分类和策略
url-filter category whitelist
rule 1 host text "***.***"
rule 2 host text "***.***"
rule 3 host text "h3c.com"
url-filter policy whitelist_policy
category whitelist action permit
default-action block
log enable
2. 创建 URL 过滤配置文件
url-filter profile whitelist_profile
policy whitelist_policy
3. 在接口上应用 URL 过滤
interface GigabitEthernet1/0/14 # 内网接口
url-filter apply profile whitelist_profile
4. 创建安全策略控制访问
security-policy ip
# 放行白名单网段的互联网访问
rule 10 name allow_whitelist_out
action pass
source-ip-group whitelist_group # 10.41.24.0/23
destination-zone untrust
logging enable
counting enable
# 阻止白名单网段的其他互联网访问
rule 11 name block_whitelist_out
action deny
source-ip-group whitelist_group
destination-zone untrust
logging enable
counting enable
组网及组网描述:
<xtlzx_OUT_f1000>dis cu
#
version 7.1.064, Release 8860P12
#
sysname xtlzx_OUT_f1000
#
clock protocol none
#
context Admin id 1
#
telnet server enable
#
irf mac-address persistent timer
irf auto-update enable
undo irf link-delay
irf member 1 priority 1
#
dns server 8.8.8.8
dns server 114.114.114.114
#
lldp global enable
#
password-recovery enable
#
vlan 1
#
object-group ip address school_wuxian
security-zone Trust
0 network subnet 10.32.0.0 255.255.0.0
#
object-group ip address teacher_wuxian
security-zone Trust
0 network subnet 10.31.0.0 255.255.0.0
#
object-group ip address youxian
security-zone Trust
0 network subnet 10.41.0.0 255.255.0.0
10 network subnet 172.16.100.0 255.255.255.0
#
interface NULL0
#
interface GigabitEthernet1/0/0
port link-mode route
#
interface GigabitEthernet1/0/1
port link-mode route
#
interface GigabitEthernet1/0/2
port link-mode route
#
interface GigabitEthernet1/0/3
port link-mode route
#
interface GigabitEthernet1/0/4
port link-mode route
#
interface GigabitEthernet1/0/5
port link-mode route
#
interface GigabitEthernet1/0/6
port link-mode route
#
interface GigabitEthernet1/0/7
port link-mode route
#
interface GigabitEthernet1/0/8
port link-mode route
#
interface GigabitEthernet1/0/9
port link-mode route
#
interface GigabitEthernet1/0/10
port link-mode route
#
interface GigabitEthernet1/0/11
port link-mode route
#
interface GigabitEthernet1/0/12
port link-mode route
#
interface GigabitEthernet1/0/13
port link-mode route
#
interface GigabitEthernet1/0/14
port link-mode route
description downto routeMSR5660
ip address 10.10.1.1 255.255.255.252
nat hairpin enable
manage https inbound
manage https outbound
#
interface GigabitEthernet1/0/15
port link-mode route
description upto lt_dianguanzhan2/2
ip address 124.165.196.45 255.255.255.0
packet-filter 3010 inbound
nat outbound 2000
#
interface GigabitEthernet1/0/16
port link-mode route
combo enable fiber
#
interface GigabitEthernet1/0/17
port link-mode route
combo enable fiber
#
interface GigabitEthernet1/0/18
port link-mode route
combo enable fiber
#
interface GigabitEthernet1/0/19
port link-mode route
combo enable fiber
#
interface GigabitEthernet1/0/20
port link-mode route
#
interface GigabitEthernet1/0/21
port link-mode route
#
interface GigabitEthernet1/0/22
port link-mode route
#
interface GigabitEthernet1/0/23
port link-mode route
#
interface GigabitEthernet1/0/24
port link-mode route
#
interface GigabitEthernet1/0/25
port link-mode route
#
interface M-GigabitEthernet1/0/0
ip address 192.168.0.1 255.255.255.0
#
interface Ten-GigabitEthernet1/0/26
port link-mode route
#
interface Ten-GigabitEthernet1/0/27
port link-mode route
#
interface SSLVPN-AC0
ip address 10.61.0.254 255.255.255.0
#
security-zone name Local
#
security-zone name Trust
import interface GigabitEthernet1/0/14
#
security-zone name DMZ
#
security-zone name Untrust
import interface GigabitEthernet1/0/15
import interface SSLVPN-AC0
#
security-zone name Management
import interface M-GigabitEthernet1/0/0
#
scheduler logfile size 16
#
line class console
authentication-mode scheme
user-role network-admin
#
line class vty
user-role network-operator
#
line con 0
user-role network-admin
#
line vty 0 63
authentication-mode scheme
user-role network-admin
#
ip route-static 0.0.0.0 0 124.165.196.1
ip route-static 10.10.1.4 30 10.10.1.2
ip route-static 10.20.0.0 16 10.10.1.2
ip route-static 10.31.0.0 16 10.10.1.2
ip route-static 10.32.0.0 16 10.10.1.2
ip route-static 10.33.0.0 16 10.10.1.2
ip route-static 10.41.0.0 16 10.10.1.2
ip route-static 10.51.0.0 16 10.10.1.2
ip route-static 172.16.100.0 24 10.10.1.2
#
info-center source CFGLOG loghost level informational
#
ssh server enable
#
acl basic 2000
rule 0 deny source 10.51.0.0 0.0.255.255
rule 5 permit
#
acl advanced 3000
rule 0 permit ip
#
acl advanced 3010
rule 0 deny tcp source-port eq 135 destination-port eq 135
rule 5 deny tcp source-port eq 137 destination-port eq 137
rule 10 deny tcp source-port eq 138 destination-port eq 138
rule 15 deny tcp source-port eq 139 destination-port eq 139
rule 20 deny tcp source-port eq 445 destination-port eq 445
rule 1000 permit ip
#
undo password-control composition enable
password-control length 8
password-control composition type-number 3 type-length 1
undo password-control complexity user-name check
#
domain system
#
domain xtl
authentication sslvpn local
authorization sslvpn local
#
domain default enable system
#
role name level-0
description Predefined level-0 role
#
role name level-1
description Predefined level-1 role
#
role name level-2
description Predefined level-2 role
#
role name level-3
description Predefined level-3 role
#
role name level-4
description Predefined level-4 role
#
role name level-5
description Predefined level-5 role
#
role name level-6
description Predefined level-6 role
#
role name level-7
description Predefined level-7 role
#
role name level-8
description Predefined level-8 role
#
role name level-9
description Predefined level-9 role
#
role name level-10
description Predefined level-10 role
#
role name level-11
description Predefined level-11 role
#
role name level-12
description Predefined level-12 role
#
role name level-13
description Predefined level-13 role
#
role name level-14
description Predefined level-14 role
#
user-group system
#
user-group usergroup1
authorization-attribute sslvpn-policy-group pgroup
#
local-user admin class manage
password hash $h$6$x1sfhGJcTTGDfsQY$YSknQ9Zu9tWQPW/Bj6W4pDK8LRhA5sRRgfGrrdrV12S/TRQBQjROybYZ2XKS42yno3Fdb++H0pCSLJxi7yx+rA==
service-type ssh telnet terminal http https
authorization-attribute user-role network-admin
authorization-attribute user-role network-operator
#
local-user baby class network
password cipher $c$3$JYlMpg6ncb5ebdj0HN46GtEhwetFKfY=
service-type sslvpn
group usergroup1
authorization-attribute user-role network-admin
authorization-attribute user-role network-operator
#
pki domain sslvpn
public-key rsa general name sslvpn
undo crl check enable
#
ftp server enable
#
session statistics enable
#
ike logging negotiation enable
#
ip https port 64400
ip http enable
ip https enable
#
loadbalance isp file flash:/lbispinfo_v1.5.tp
#
sslvpn ip address-pool ippool 10.61.0.1 10.61.0.100
#
sslvpn gateway gw
ip address 124.165.233.210 port 65500
service enable
#
sslvpn context ctx1
gateway gw
ip-tunnel interface SSLVPN-AC0
ip-tunnel address-pool ippool mask 255.255.255.0
ip-route-list iplist
include 10.20.0.15 255.255.255.255
include 10.20.3.254 255.255.255.255
policy-group pgroup
filter ip-tunnel acl 3000
ip-tunnel access-route ip-route-list iplist
default-policy-group pgroup
service enable
#
uapp-control
policy name 应用审计 audit
rule 1 any behavior any bhcontent any keyword include any action permit audit-logging
#
security-policy ip
rule 1 name trust-Local
action pass
counting enable
source-zone trust
destination-zone Local
service pingv6
service ping
service telnet
service ssh
service https
rule 4 name block-10.51-out
logging enable
counting enable
source-zone trust
destination-zone untrust
source-ip-subnet 10.51.0.0 255.255.0.0
rule 10 name 1111
action pass
logging enable
counting enable
source-zone Trust
destination-zone Trust
rule 9 name Local-untrust-2
action pass
counting enable
source-zone Local
destination-zone untrust
rule 8 name Local-trust-2
action pass
counting enable
source-zone Local
destination-zone trust
rule 7 name trust-untrust-2
action pass
counting enable
source-zone trust
destination-zone untrust
rule 2 name block-untrust-to-10.51
logging enable
counting enable
source-zone untrust
destination-zone trust
destination-ip-subnet 10.51.0.0 255.255.0.0
rule 3 name untrust-trust
logging enable
counting enable
source-zone untrust
destination-zone trust
#
dac log-collect service dpi traffic enable
dac traffic-statistic application enable
#
cloud-management server domain opstunnel-seccloud.h3c.com
#
return
<xtlzx_OUT_f1000>
- 2025-06-09提问
- 举报
-
(0)
最佳答案

不需要在url里做,安全策略里限制主机名就可以
I方式:基于域名的安全策略典型配置
使用版本
本举例是在F5000-AI-55-G的E9900版本上进行配置和验证的。
组网需求
如下图所示,某公司内的各部门之间通过Device实现互连,公司内网中部署了域名为***.***的Web服务器用于公司财务管理,该域名已在内网DNS服务器中注册。通过配置安全策略,实现如下需求:
允许财务部通过HTTP协议访问财务管理Web服务器。
禁止市场部在任何时间通过HTTP协议访问财务管理Web服务器。
图-1 基于域名的安全策略配置组网图
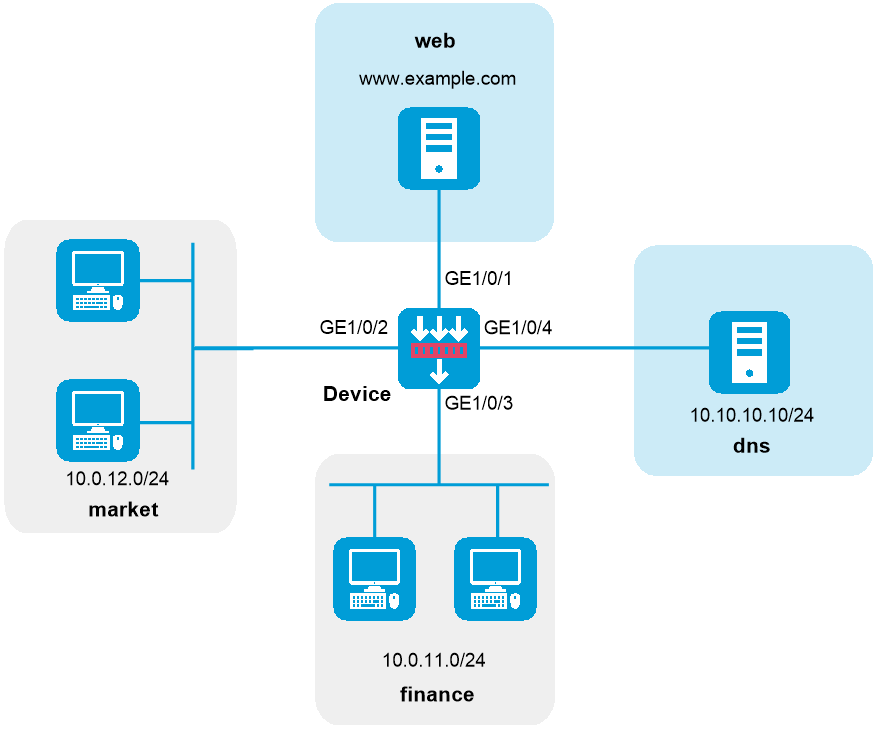
配置步骤
配置接口IP地址
# 根据组网图中规划的信息,配置各接口的IP地址,具体配置步骤如下。
<Device> system-view
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet1/0/1] ip address 10.0.13.1 255.255.255.0
[Device-GigabitEthernet1/0/1] quit
请参考以上步骤配置其他接口的IP地址,具体配置步骤略。
配置接口加入安全域
# 请根据组网图中规划的信息,创建安全域,并将接口加入对应的安全域,具体配置步骤如下。
[Device] security-zone name web
[Device-security-zone-web] import interface gigabitethernet 1/0/1
[Device-security-zone-web] quit
[Device] security-zone name market
[Device-security-zone-market] import interface gigabitethernet 1/0/2
[Device-security-zone-market] quit
[Device] security-zone name finance
[Device-security-zone-finance] import interface gigabitethernet 1/0/3
[Device-security-zone-finance] quit
[Device] security-zone name dns
[Device-security-zone-dns] import interface gigabitethernet 1/0/4
[Device-security-zone-dns] quit
配置对象
# 创建名为web的IP地址对象组,并定义其主机名称为***.***,具体配置步骤如下。
[Device] object-group ip address web
[Device-obj-grp-ip-web] network host name ***.***
[Device-obj-grp-ip-web] quit
配置DNS服务器地址
# 指定DNS服务器的IP地址为10.10.10.10,确保Device可以获取到主机名对应的IP地址,具体配置步骤如下。
[Device] dns server 10.10.10.10
配置安全策略
# 配置名称为dnslocalout的安全策略规则,允许Device访问DNS服务器,具体配置步骤如下。
[Device] security-policy ip
[Device-security-policy-ip] rule name dnslocalout
[Device-security-policy-ip-0-dnslocalout] source-zone local
[Device-security-policy-ip-0-dnslocalout] destination-zone dns
[Device-security-policy-ip-0-dnslocalout] destination-ip-host 10.10.10.10
[Device-security-policy-ip-0-dnslocalout] action pass
[Device-security-policy-ip-0-dnslocalout] quit
# 配置名称为host-dns的安全策略规则,允许内网主机访问DNS服务器,具体配置步骤如下。
[Device-security-policy-ip] rule name host-dns
[Device-security-policy-ip-1-host-dns] source-zone finance
[Device-security-policy-ip-1-host-dns] source-zone market
[Device-security-policy-ip-1-host-dns] destination-zone dns
[Device-security-policy-ip-1-host-dns] source-ip-subnet 10.0.11.0 24
[Device-security-policy-ip-1-host-dns] source-ip-subnet 10.0.12.0 24
[Device-security-policy-ip-1-host-dns] destination-ip-host 10.10.10.10
[Device-security-policy-ip-1-host-dns] service dns-udp
[Device-security-policy-ip-1-host-dns] action pass
[Device-security-policy-ip-1-host-dns] quit
# 配置名称为finance-web的安全策略规则,允许财务部通过HTTP协议访问财务管理Web服务器,具体配置步骤如下。
[Device-security-policy-ip] rule name finance-web
[Device-security-policy-ip-2-finance-web] source-zone finance
[Device-security-policy-ip-2-finance-web] destination-zone web
[Device-security-policy-ip-2-finance-web] source-ip-subnet 10.0.11.0 24
[Device-security-policy-ip-2-finance-web] destination-ip web
[Device-security-policy-ip-2-finance-web] service http
[Device-security-policy-ip-2-finance-web] action pass
[Device-security-policy-ip-2-finance-web] quit
# 配置名称为market-web的安全策略规则,禁止市场部在任何时间通过HTTP协议访问财务管理Web服务器,具体配置步骤如下。
[Device-security-policy-ip] rule name market-web
[Device-security-policy-ip-3-market-web] source-zone market
[Device-security-policy-ip-3-market-web] destination-zone web
[Device-security-policy-ip-3-market-web] source-ip-subnet 10.0.12.0 24
[Device-security-policy-ip-3-market-web] destination-ip web
[Device-security-policy-ip-3-market-web] service http
[Device-security-policy-ip-3-market-web] action drop
[Device-security-policy-ip-3-market-web] quit
# 激活安全策略规则的加速功能,具体配置步骤如下。
[Device-security-policy-ip] accelerate enhanced enable
[Device-security-policy-ip] quit
验证配置
配置完成后,财务部可以访问财务管理服务器的Web服务,市场部任何时间均不可以访问财务管理服务器的Web服务。
配置文件
- 2025-06-09回答
- 评论(0)
- 举报
-
(0)


防火墙通过安全策略实现过滤HTTPS网站配置方法(命令行)
1 目录
本案例适用于软件平台为Comware V7系列防火墙:F100-X-G2、F1000-X-G2、F100-WiNet、F1000-AK、F10X0等
注:本案例是在F100-C-G2的Version 7.1.064, Release 9510P08版本上进行配置和验证的。
防火墙部署在互联网出口,需要实现通过安全策略限制访问www.baidu.com的目的。

上网配置略,请参考《轻轻松松配安全》2.1章节防火墙连接互联网上网配置方法案例。
4.2 开启本地DNS代理
#开启设备本地DNS代理功能,用于解析域名。
<H3C>system-view //进入系统视图
System View: return to User View with Ctrl+Z.
[H3C]dns proxy enable //开启设备本地DNS代理功能
[H3C]dns server 114.114.114.114 //配置dns服务器
4.3 修改DHCP服务器DNS为设备接口地址
#如果防火墙作为DNS服务器则需要保证下发给终端地址时,客户端DNS为防火墙接口地址;
[H3C]dhcp server ip-pool 2 //创建dhcp服务器 地址池名称2
[H3C-dhcp-pool-2]gateway-list 192.168.2.1 //客户端网关
[H3C-dhcp-pool-2]network 192.168.2.0 mask 255.255.255.0 //配置客户端网段192.168.2.0 掩码 255.255.255.0
[H3C-dhcp-pool-2]dns-list 192.168.2.1 //客户端dns
[H3C-dhcp-pool-2]quit //退出当前视图
防火墙开启DNS代理后,如果终端将DNS请求发向防火墙则防火墙会替代向外网发起DNS解析请求,DNS回应报文返回防火墙后再由防火墙转发至终端,这样做的目的是保证终端和防火墙解析的地址相同。
#创建地址对象组,地址对象组名称为baidu.使用基于主机的形式关联域名:www.baidu.com.
[H3C]object-group ip address baidu //创建地址对象组,地址对象组名称为baidu
[H3C-obj-grp-ip-baidu]0 network host name www.baidu.com //使用基于主机的形式关联域名:www.baidu.com
[H3C-obj-grp-ip-baidu]quit //退出当前视图
#创建安全策略规则1名称为“baidu-deny”源安全域为“trust”、目的IP为名称为“baidu”的地址对象,安全策略默认策略为拒绝;创建安全策略规则2名称为“passany”源安全域为“trust”、目的安全域为“untrust”,动作配置为“pass”放通所有数据。
[H3C]security-policy ip //创建安全策略
[H3C-security-policy-ip]rule 1 name baidu-deny //创建规则1名称为“baidu-deny”
[H3C-security-policy-ip-1-denybaidu]source-zone trust //源安全域为“trust”
[H3C-security-policy-ip-1-denybaidu]destination-ip baidu //目的IP为名称为“baidu”的地址对象
[H3C-security-policy-ip-1-denybaidu]quit //退出当前视图
[H3C-security-policy-ip]rule 2 name passany //创建安全策略规则2名称为“passany”
[H3C-security-policy-ip-2-passany]action pass //动作配置为“pass”放通所有数据
[H3C-security-policy-ip-2-passany]source-zone trust //源安全域为“trust”
[H3C-security-policy-ip-2-passany]destination-zone untrust //目的安全域为“untrust”
[H3C-security-policy-ip-2-passany]quit //退出当前视图
[H3C]save force
使用浏览器打开www.baidu.com,不能正常访问:

使用浏览器打开***.***,可以正常访问:

查看pc针对百度解析的地址为39.156.66.18:

查看设备的安全策略日志,可以看到针对改目的ip已成功拒绝(第三条):
- 2025-06-09回答
- 评论(2)
- 举报
-
(0)
能根据我的配置提供步骤不?
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明

