S5500-24P 与 S5500-24P 点对点如何组网
- 0关注
- 1收藏,2431浏览
问题描述:
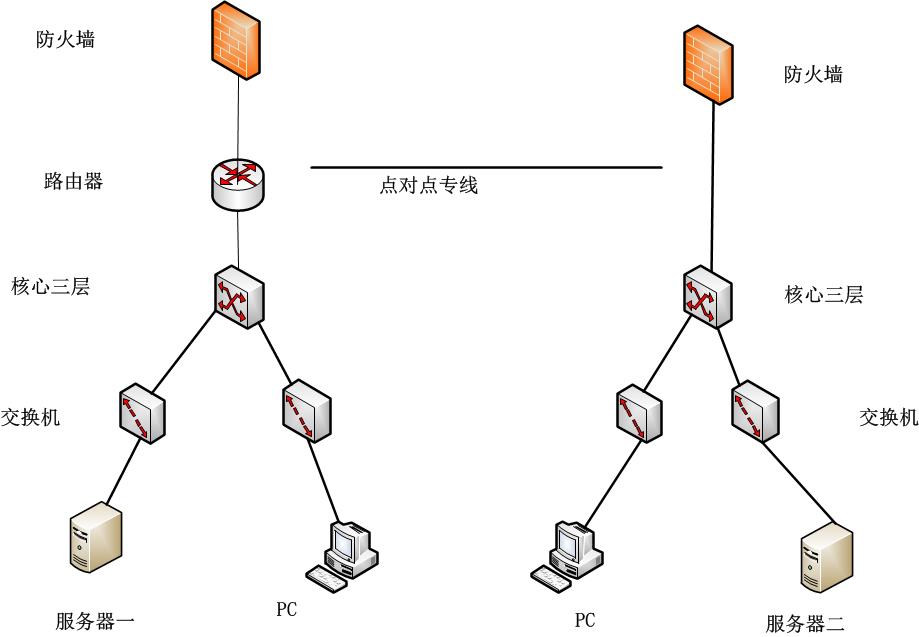
大家好,我这边和子公司有一个局域网内部访问需求。各自靠电信200M专线上网,因为一些原因,现在又额外办了一条点对点专线,这条点对点专线可以理解为一条网线从这边机房拉到对方机房。
需求:我这边的办公网要访问对方服务二的资源,对方办公网PC可以访问我这边的服务器一的资源,可以把我这边和对方设定为一个内网,资源共享。但是上外网就各自走外网专线。
请问这条点对点专线分别接入哪个设备上( 防火墙 还是 核心三层 ),然后由哪一边分配IP。谢谢指教
组网及组网描述:
- 2018-02-05提问
- 举报
-
(0)
最佳答案

可以连在防火墙上,也可以直接接在三层交换机上。 如果需要通过防火墙进行访问控制,可以连接在防火墙上,如果没有访问能控制需求,也不需要通过防火墙对访问的数据进行过滤,直接连接在三层交换机上组网更简单。
如果连接在三层交换机上,需要提前做好规划
1、规划好互联接口IP
2、两边网络中,不可以有相同网段,如果有相同网段需要提前修改成整个网络唯一的网段。
实现方法也比较建单,两台交换机配置互联IP, 分别配置静态路由,目的地址时对端内网网段,吓一跳时对端设备的互联IP即可。
- 2018-02-05回答
- 评论(1)
- 举报
-
(0)
第一次这样操作,不过都思路都比较清晰了,谢谢你

你好,我按照你的说法设置了几遍,好像还是没效果,我现在把需求和相关信息再详细说一遍吧,麻烦你帮指导一下,谢谢。
一、需求:
1、我这边要访问对方的服务器为 172.18.3.159
2、对方需要访问我这边的服务器 172.18.5.249
二、配置:
1、我这边三层的配置:
#
version 5.20.99, Release 2220P10
#
sysname ds_5500
#
domain default enable system
#
ipv6
#
telnet server enable
#
password-recovery enable
#
vlan 1
#
vlan 3
#
vlan 50
#
vlan 60
#
vlan 70
#
vlan 80
#
vlan 120
#
vlan 130
#
domain system
access-limit disable
state active
idle-cut disable
self-service-url disable
#
user-group system
group-attribute allow-guest
#
local-user admin
password cipher *********
authorization-attribute level 3
service-type ssh telnet terminal
service-type web
#
interface NULL0
#
interface Vlan-interface1
ip address ******************
#
interface Vlan-interface50
ipv6 address auto link-local
#
interface Vlan-interface60
ipv6 address auto link-local
#
interface Vlan-interface70
ipv6 address auto link-local
#
interface Vlan-interface80
ipv6 address auto link-local
#
interface Vlan-interface120
ipv6 address auto link-local
#
interface Vlan-interface130
ipv6 address auto link-local
#
interface GigabitEthernet1/0/1
port access vlan 60
#
interface GigabitEthernet1/0/2
port access vlan 60
#
interface GigabitEthernet1/0/3
port link-type trunk
port trunk permit vlan 1 70
#
interface GigabitEthernet1/0/4
port link-type trunk
port trunk permit vlan 1 70 130
#
interface GigabitEthernet1/0/5
port access vlan 70
#
interface GigabitEthernet1/0/6
port access vlan 70
#
interface GigabitEthernet1/0/7
port access vlan 70
#
interface GigabitEthernet1/0/8
port access vlan 70
#
interface GigabitEthernet1/0/9
port access vlan 80
#
interface GigabitEthernet1/0/10
port access vlan 80
#
interface GigabitEthernet1/0/11
port access vlan 80
#
interface GigabitEthernet1/0/12
port access vlan 80
#
interface GigabitEthernet1/0/13
port access vlan 120
#
interface GigabitEthernet1/0/14
port access vlan 120
#
interface GigabitEthernet1/0/15
port access vlan 120
#
interface GigabitEthernet1/0/16
port access vlan 50
#
interface GigabitEthernet1/0/17
port access vlan 130
#
interface GigabitEthernet1/0/18
port access vlan 130
#
interface GigabitEthernet1/0/19
port access vlan 3
#
interface GigabitEthernet1/0/20
port access vlan 130
#
interface GigabitEthernet1/0/21
port link-type trunk
port trunk permit vlan 1 to 2 4 to 4094
#
interface GigabitEthernet1/0/22
port link-type trunk
port trunk permit vlan 1 to 2 4 to 4094
#
interface GigabitEthernet1/0/23
port access vlan 3
#
interface GigabitEthernet1/0/24
port link-type trunk
port trunk permit vlan 1 to 2 4 to 4094
#
interface GigabitEthernet1/0/25
port link-type trunk
port trunk permit vlan 1
speed 1000
duplex full
shutdown
#
interface GigabitEthernet1/0/26
shutdown
#
interface GigabitEthernet1/0/27
shutdown
#
interface GigabitEthernet1/0/28
port access vlan 50
duplex full
shutdown
#
ip route-static 0.0.0.0 0.0.0.0 172.18.5.1
#
load xml-configuration
#
user-interface aux 0
authentication-mode scheme
user-interface vty 0 15
authentication-mode scheme
#
return
2、对方三层的配置:
#
version 5.20, Release 2221P27
#
sysname H3C
#
domain default enable system
#
ipv6
#
telnet server enable
#
password-recovery enable
#
vlan 1
#
vlan 2
name CableArea1
#
vlan 3
#
vlan 4
name FinancialDepartment
#
vlan 5
name Wifi
#
vlan 11
name CableArea2
#
vlan 12
name CCTV
#
vlan 50
#
domain system
access-limit disable
state active
idle-cut disable
self-service-url disable
#
dhcp server ip-pool cablearea1
network 172.18.1.0 mask 255.255.255.0
gateway-list 172.18.1.1
dns-list 202.96.134.133 202.96.128.86
#
dhcp server ip-pool cablearea2
network 172.18.11.0 mask 255.255.255.0
gateway-list 172.18.11.1
dns-list 202.96.134.133 202.96.128.86
#
dhcp server ip-pool devices
network 172.18.0.0 mask 255.255.255.0
gateway-list 172.18.0.254
dns-list 202.96.134.133 202.96.128.86
#
dhcp server ip-pool financialdepartment
network 172.18.3.0 mask 255.255.255.0
gateway-list 172.18.3.1
dns-list 202.96.134.133 202.96.128.86
#
dhcp server ip-pool vlan3
network 172.18.2.0 mask 255.255.255.0
gateway-list 172.18.2.1
dns-list 202.96.134.133 202.96.128.86
#
dhcp server ip-pool wifi
network 172.18.14.0 mask 255.255.254.0
gateway-list 172.18.14.1
dns-list 202.96.134.133 202.96.128.86
expired day 0 hour 2
#
user-group system
group-attribute allow-guest
#
local-user admin
password cipher *********
authorization-attribute level 3
service-type ssh telnet terminal
service-type web
#
interface NULL0
#
interface Vlan-interface1
ip address 172.18.0.1 255.255.255.0
#
interface Vlan-interface2
ip address 172.18.1.1 255.255.255.0
#
interface Vlan-interface3
ip address 172.18.2.1 255.255.255.0
#
interface Vlan-interface4
ip address 172.18.3.1 255.255.255.0
#
interface Vlan-interface5
ip address 172.18.14.1 255.255.254.0
#
interface Vlan-interface11
ip address 172.18.11.1 255.255.255.0
#
interface Vlan-interface12
ip address 172.18.12.1 255.255.255.0
#
interface GigabitEthernet1/0/1
port access vlan 12
#
interface GigabitEthernet1/0/2
port access vlan 12
#
interface GigabitEthernet1/0/3
port access vlan 2
#
interface GigabitEthernet1/0/4
port access vlan 2
#
interface GigabitEthernet1/0/5
port access vlan 2
#
interface GigabitEthernet1/0/6
port access vlan 2
#
interface GigabitEthernet1/0/7
port access vlan 2
#
interface GigabitEthernet1/0/8
port access vlan 2
#
interface GigabitEthernet1/0/9
port access vlan 2
#
interface GigabitEthernet1/0/10
port access vlan 2
#
interface GigabitEthernet1/0/11
port access vlan 11
#
interface GigabitEthernet1/0/12
port access vlan 11
#
interface GigabitEthernet1/0/13
port access vlan 11
#
interface GigabitEthernet1/0/14
port access vlan 11
#
interface GigabitEthernet1/0/15
port access vlan 11
#
interface GigabitEthernet1/0/16
port access vlan 11
#
interface GigabitEthernet1/0/17
port access vlan 4
#
interface GigabitEthernet1/0/18
port access vlan 4
#
interface GigabitEthernet1/0/19
port access vlan 5
#
interface GigabitEthernet1/0/20
port access vlan 5
#
interface GigabitEthernet1/0/21
port access vlan 5
#
interface GigabitEthernet1/0/22
port access vlan 5
#
interface GigabitEthernet1/0/23
port access vlan 3
#
interface GigabitEthernet1/0/24
#
interface GigabitEthernet1/0/25
shutdown
#
interface GigabitEthernet1/0/26
shutdown
#
interface GigabitEthernet1/0/27
shutdown
#
interface GigabitEthernet1/0/28
shutdown
#
ip route-static 0.0.0.0 0.0.0.0 172.18.0.254
#
dhcp server forbidden-ip 172.18.3.200 172.18.3.254
dhcp server forbidden-ip 172.18.0.200 172.18.0.254
dhcp server forbidden-ip 172.18.11.200 172.18.11.254
dhcp server forbidden-ip 172.18.11.1 172.18.11.99
dhcp server forbidden-ip 172.18.14.1 172.18.14.10
#
dhcp enable
#
ssh server enable
#
load xml-configuration
#
user-interface aux 0
authentication-mode scheme
user-interface vty 0 15
authentication-mode scheme
#
return
三: 路由设置:
我这边是用防火墙做DHCP。他是直接用三层做DHCP的
那么,我这边要访问对方的 172.18.3.159,我这边三层的网关是172.18.8.246,路由表不是应该如下设置吗:
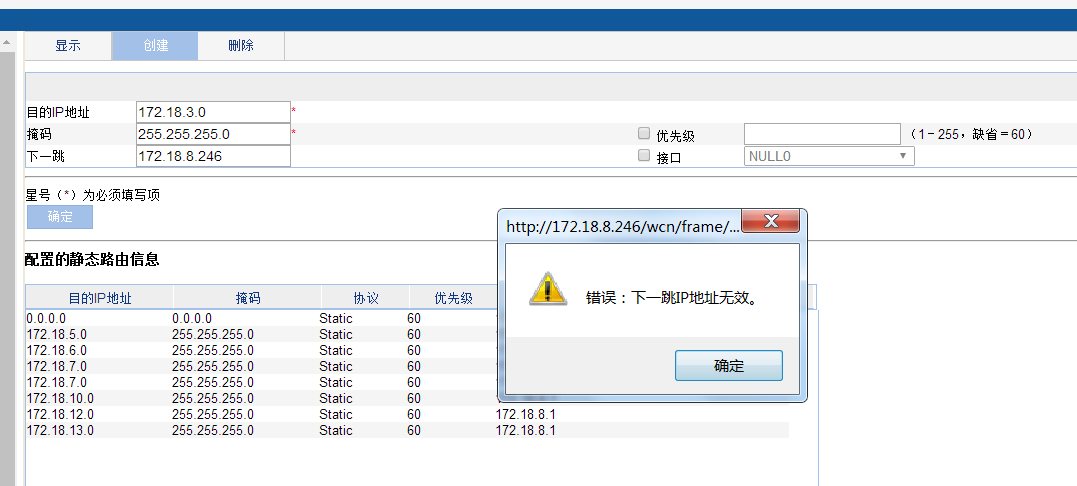
要是我设置错误,请耐心指导,只要说明一方访问对方的。那我就会在对方设置访问我这边服务器的了,尽量用web界面设置,命令行暂时还不会,非常感谢你了啦。
- 2018-02-12回答
- 评论(0)
- 举报
-
(0)
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明


第一次这样操作,不过都思路都比较清晰了,谢谢你