再来一个sslvpn问题
- 0关注
- 1收藏,1725浏览

您好,请知:
是要安装插件,可参考如下过程:
SW1:
[H3C]sysname SW1
[SW1]int LoopBack 0
[SW1-LoopBack0]ip address 1.1.1.1 32
[SW1-LoopBack0]quit
[SW1]router id 1.1.1.1
[SW1]int gi 1/0/1
[SW1-GigabitEthernet1/0/1]port link-mode route
[SW1-GigabitEthernet1/0/1]ip address 10.1.1.1 30
[SW1-GigabitEthernet1/0/1]description
[SW1-GigabitEthernet1/0/1]quit
[SW1]ip route-static 0.0.0.0 0.0.0.0 10.1.1.2
[SW1]telnet server enable
[SW1]local-user admin
New local user added.
[SW1-luser-manage-admin]password simple admin
[SW1-luser-manage-admin]service-type telnet
[SW1-luser-manage-admin]authorization-attribute user-role network-admin
[SW1]user-interface vty 0 4
[SW1-line-vty0-4]authentication-mode scheme
[SW1-line-vty0-4]protocol inbound all
[SW1-line-vty0-4]quit
F1060:
[H3C]sysname SSL_VPM-F1060
[SSL_VPM-F1060]int LoopBack 0
[SSL_VPM-F1060-LoopBack0]ip address 2.2.2.2 32
[SSL_VPM-F1060-LoopBack0]quit
[SSL_VPM-F1060]router id 2.2.2.2
[SSL_VPM-F1060]int gi 1/0/3
[SSL_VPM-F1060-GigabitEthernet1/0/3]ip address 10.1.1.2 30
[SSL_VPM-F1060-GigabitEthernet1/0/3]description
[SSL_VPM-F1060-GigabitEthernet1/0/3]quit
[SSL_VPM-F1060]int gi 1/0/2
[SSL_VPM-F1060-GigabitEthernet1/0/2]ip address 192.168.200.254 24
[SSL_VPM-F1060-GigabitEthernet1/0/2]description
[SSL_VPM-F1060-GigabitEthernet1/0/2]quit
[SSL_VPM-F1060]security-zone name Trust
[SSL_VPM-F1060-security-zone-Trust]import interface GigabitEthernet 1/0/3
[SSL_VPM-F1060-security-zone-Trust]import interface LoopBack 0
[SSL_VPM-F1060-security-zone-Trust]quit
[SSL_VPM-F1060]security-zone name Untrust
[SSL_VPM-F1060-security-zone-Untrust]import interface GigabitEthernet 1/0/2
[SSL_VPM-F1060-security-zone-Untrust]quit
[SSL_VPM-F1060]acl basic 2000
[SSL_VPM-F1060-acl-ipv4-basic-2000]rule 0 permit source any
[SSL_VPM-F1060-acl-ipv4-basic-2000]quit
[SSL_VPM-F1060]zone-pair security source trust destination untrust
[SSL_VPM-F1060-zone-pair-security-Trust-Untrust]packet-filter 2000
[SSL_VPM-F1060-zone-pair-security-Trust-Untrust]quit
[SSL_VPM-F1060]zone-pair security source untrust destination trust
[SSL_VPM-F1060-zone-pair-security-Untrust-Trust]packet-filter 2000
[SSL_VPM-F1060-zone-pair-security-Untrust-Trust]quit
[SSL_VPM-F1060]zone-pair security source local destination trust
[SSL_VPM-F1060-zone-pair-security-Local-Trust]packet-filter 2000
[SSL_VPM-F1060-zone-pair-security-Local-Trust]quit
[SSL_VPM-F1060]zone-pair security source local destination untrust
[SSL_VPM-F1060-zone-pair-security-Local-Untrust]packet-filter 2000
[SSL_VPM-F1060-zone-pair-security-Local-Untrust]quit
[SSL_VPM-F1060]zone-pair security source trust destination local
[SSL_VPM-F1060-zone-pair-security-Trust-Local]packet-filter 2000
[SSL_VPM-F1060-zone-pair-security-Trust-Local]quit
[SSL_VPM-F1060]zone-pair security source untrust destination local
[SSL_VPM-F1060-zone-pair-security-Untrust-Local]packet-filter 2000
[SSL_VPM-F1060-zone-pair-security-Untrust-Local]quit
[SSL_VPM-F1060]acl basic 2001
[SSL_VPM-F1060-acl-ipv4-basic-2001]rule 0 permit source any
[SSL_VPM-F1060-acl-ipv4-basic-2001]quit
[SSL_VPM-F1060]int gi 1/0/2
[SSL_VPM-F1060-GigabitEthernet1/0/2]nat outbound 2001
[SSL_VPM-F1060-GigabitEthernet1/0/2]quit
[H3C]acl advanced 3000
[H3C-acl-ipv4-adv-3000]rule 0 permit tcp source any destination any
[H3C-acl-ipv4-adv-3000]quit
创建SSL VPN网关,指定网关IP地址(注意:IP地址为外网接口的地址)
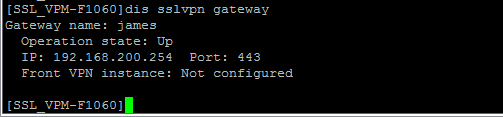
[SSL_VPM-F1060]sslvpn gateway james
[SSL_VPM-F1060-sslvpn-gateway-james]ip address 192.168.200.254
[SSL_VPM-F1060-sslvpn-gateway-james]service enable //开启SSL VPN网关
[SSL_VPM-F1060-sslvpn-gateway-james]quit
创建SSL VPN实例
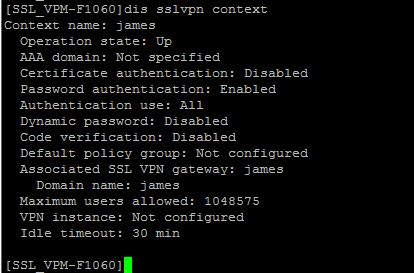
[SSL_VPM-F1060]sslvpn context james
[SSL_VPM-F1060-sslvpn-context-james]gateway james domain james //调用SSL VPN网关
[SSL_VPM-F1060-sslvpn-context-james-port-forward-item-james]local-port 2323 local-name 127.0.0.23 remote-server 10.1.1.1 remote-port 23 //发布资源
[SSL_VPM-F1060-sslvpn-context-james]port-forward list //创建资源列表
[SSL_VPM-F1060-sslvpn-context-james-port-forward-list]resources port-forward-item james //调用资源
[SSL_VPM-F1060-sslvpn-context-james-port-forward-list]quit
[SSL_VPM-F1060-sslvpn-context-james]policy-group james //创建策略组
[SSL_VPM-F1060-sslvpn-context-james-policy-group-james]resources port-forward list //调用资源列表
[SSL_VPN-F1060-sslvpn-context-james-policy-group-james]filter tcp-access acl 3000
[SSL_VPM-F1060-sslvpn-context-james-policy-group-james]quit
[SSL_VPM-F1060-sslvpn-context-james]service enable //启用SSL VPN实例
[SSL_VPM-F1060-sslvpn-context-james]quit
创建用户名、密码,赋予SSL VPN登陆方式及SSL VPN资源的访问权限
[SSL_VPM-F1060]local-user james class network
New local user added.
[SSL_VPM-F1060-luser-network-james]password simple james
[SSL_VPM-F1060-luser-network-james]service-type sslvpn
[SSL_VPM-F1060-luser-network-james]authorization-attribute user-role network-operator
[SSL_VPM-F1060-luser-network-james]authorization-attribute sslvpn-policy-group james
[SSL_VPM-F1060-luser-network-james]quit
测试:
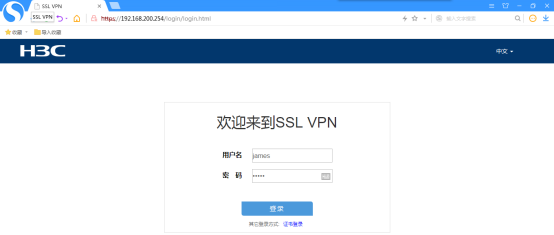
打开浏览器,输入192.168.200.254,回车:
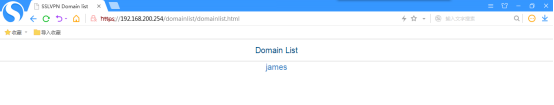
点击“james”:
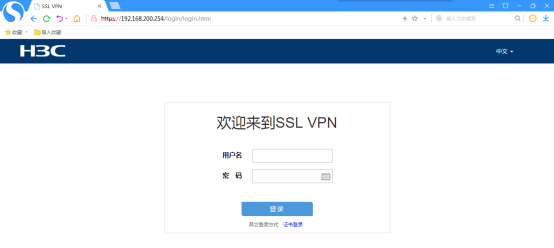
输入用户名,密码,点击“登陆”:
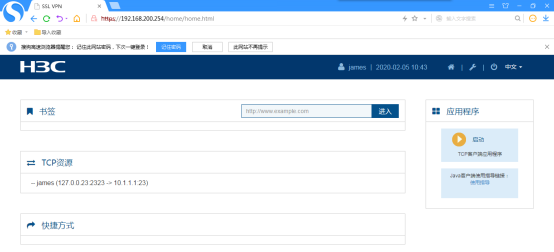
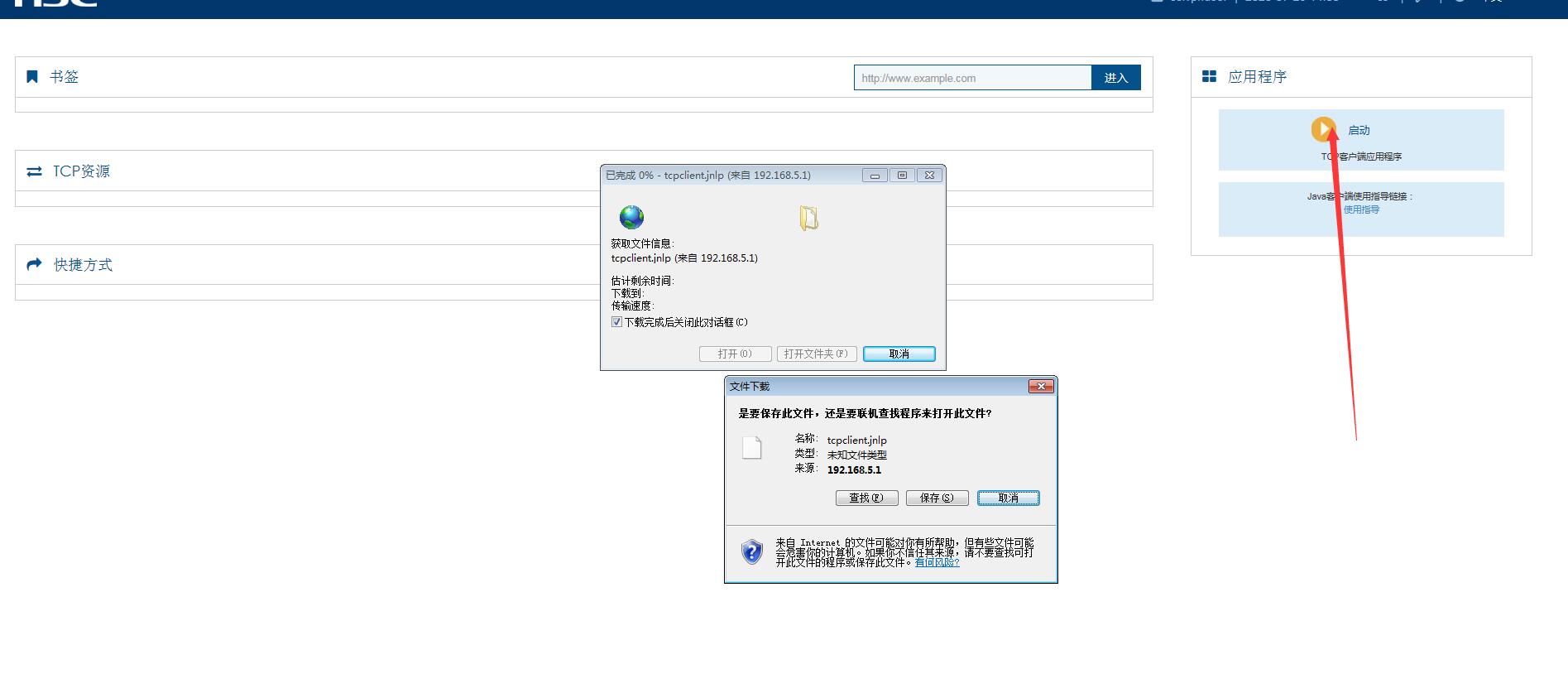
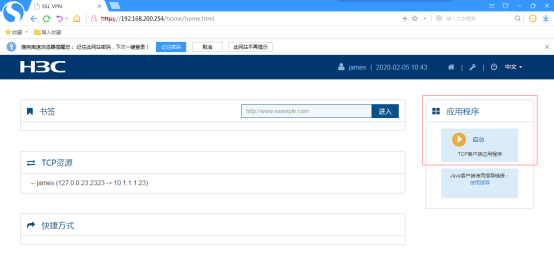
点击“启动 TCP客户端应用程序”:
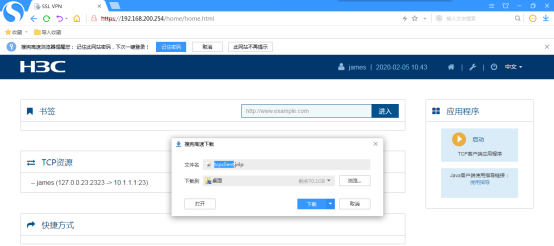
点击“下载”:
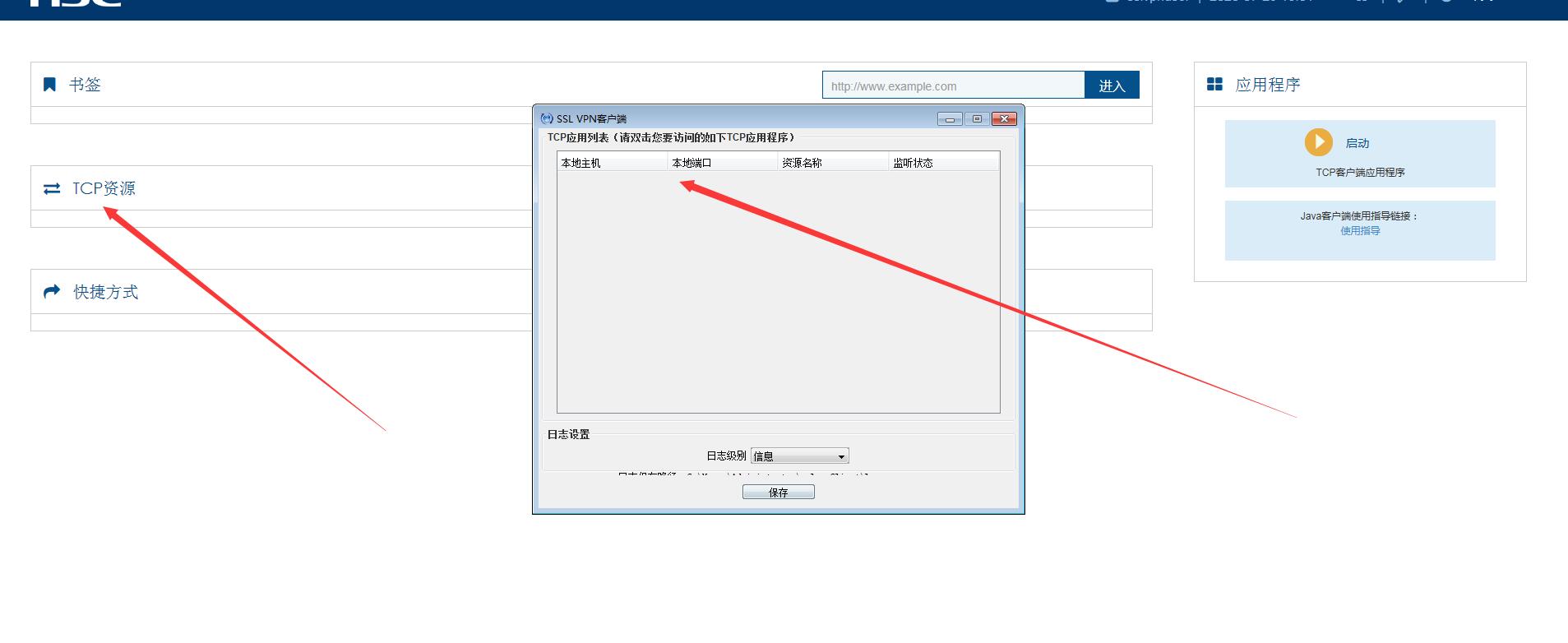
运行:
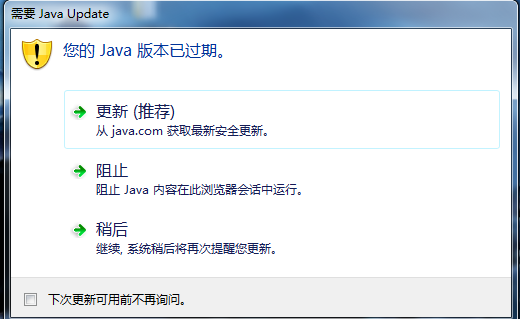
点击“更新”:
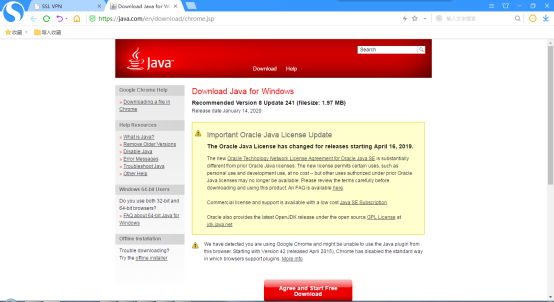
点击下载:
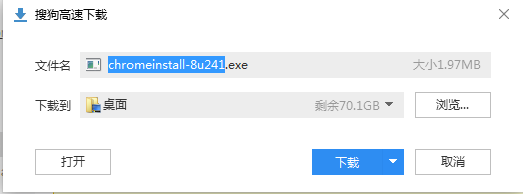
安装:

继续打开TCP客户端:
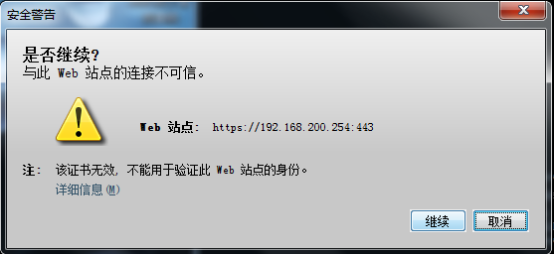
针对证书无效的问题,需要去到JAVA(32位)去添加信任站点。
打开控制面板,选择“JAVA(32位)”
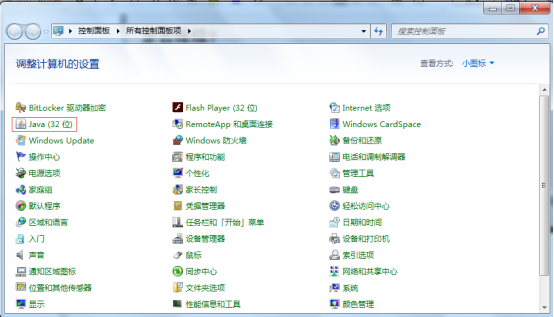
在打开的“JAVA控制面板”选择“安全”
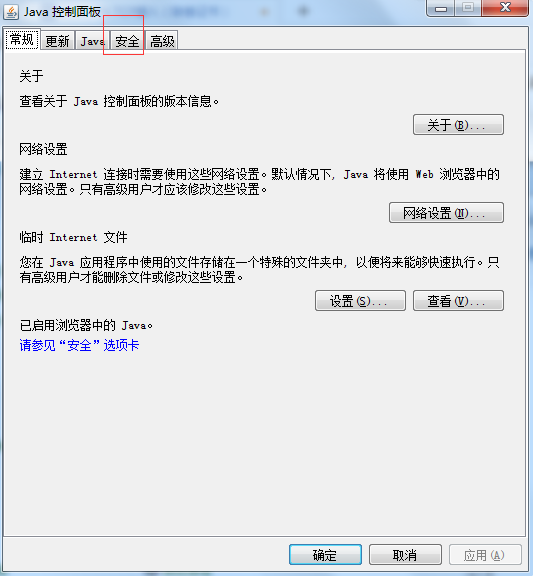
添加站点
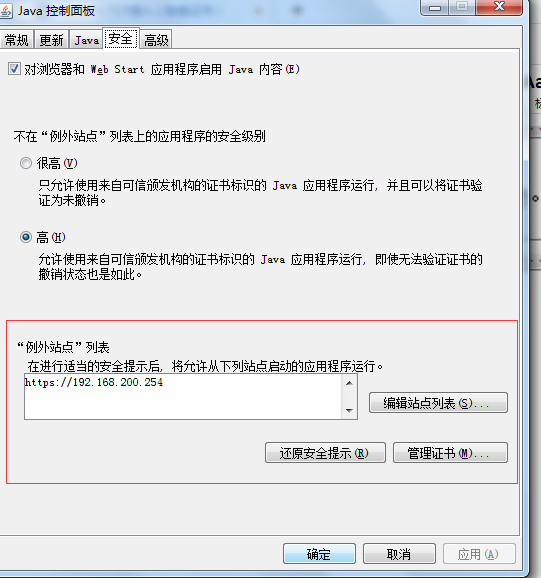
继续打开客户端:

选择“继续”

正在连接:

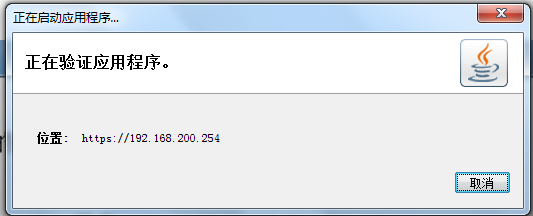
SSL VPN连接成功:
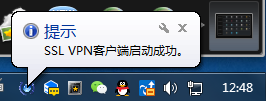
双击SSL VPN客户端:
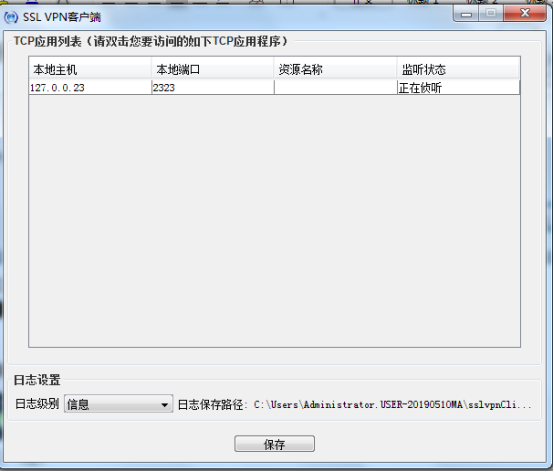
在CMD使用telnet 127.0.0.23 2323命令
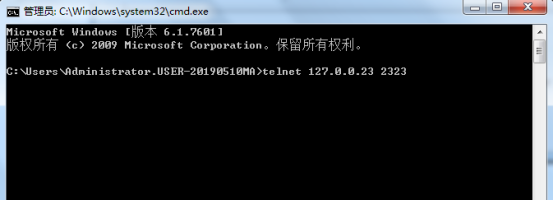

在SSL VPN查看信息:
至此SSL VPN TCP接入(缺省证书)典型组网配置案例已完成。
特别说明:由于模拟器及物理机的局限,本次实验的配置过程、测试效果仅供参考,实际以现场实施情况为准!
- 2020-07-29回答
- 评论(5)
- 举报
-
(1)
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明