H3C AC remote MAC+remote Portal+MAC senseless authentication typical configuration example (V7)
- 0关注
- 0收藏 3032浏览
Network Topology
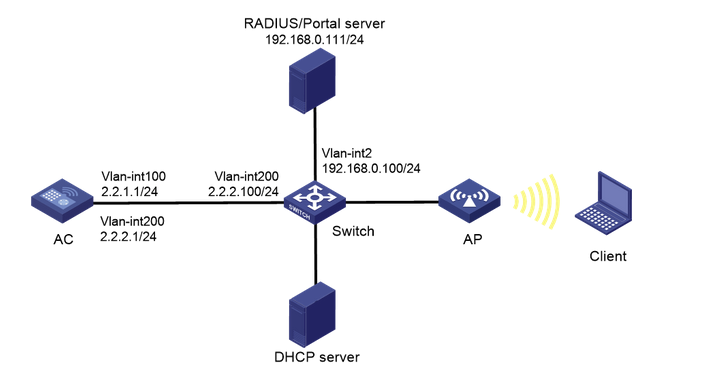
As shown in Figure, AP and Client obtain IP address through DHCP server. iMC acts as both Portal Authentication Server and Portal Web Server, RADIUS server, and requires.
- Remote MAC authentication for wireless users.
- AC uses Portal authentication in a direct way.
- The server needs to dynamically modify the user authorization information or force the user to go offline.
Configuration Steps
1. Configure the Server.
Omission
2. Configure the AC.
(1) Configure the interface of the AC
# Create VLAN 100 and its corresponding VLAN interface and configure an IP address for the interface. the AP will obtain this IP address to establish a CAPWAP tunnel with the AC.
<AC> system-view
[AC] vlan 100
[AC-vlan100] quit
[AC] interface vlan-interface 100
[AC-Vlan-interface100] ip address 2.2.1.1 24
[AC-Vlan-interface100] quit
# Create VLAN 200 and its corresponding VLAN interface, and configure the IP address for the interface. client will use this VLAN to access the wireless network.
[AC] vlan 200
[AC-vlan200] quit
[AC] interface vlan-interface 200
[AC-Vlan-interface200] ip address 2.2.2.1 24
[AC-Vlan-interface200] quit
# Configure the attribute of interface GigabitEthernet1/0/1, which is connected to the Switch, to be Trunk, allowing VLAN 1, VLAN 100, and VLAN 200 to pass.
[AC] interface gigabitethernet 1/0/1
[AC-GigabitEthernet1/0/1] port link-type trunk
[AC-GigabitEthernet1/0/1] port trunk permit vlan 1 100 200
[AC-GigabitEthernet1/0/1] quit
(2) Configure static routes
# Configure a static route to the iMC server.
[AC] ip route-static 192.168.0.0 255.255.0.0 2.2.2.100
(3) Configure the wireless service
# Create wireless service template st1 and enter wireless service template view.
[AC] wlan service-template st1
# Configure the SSID as service.
[AC-wlan-st-st1] ssid service
# Configure the wireless service template VLAN to be 200.
[AC-wlan-st-st1] vlan 200
[AC-wlan-st-st1] quit
# Create an AP, configure the AP name to office, select WA4320i-ACN for model name, and configure serial number 219801A0CNC138011454.
[AC] wlan ap office model WA4320i-ACN
[AC-wlan-ap-office] serial-id 219801A0CNC138011454
# Enter Radio 2 view.
[AC-wlan-ap-office] radio 2
# Bind the wireless service template st1 to radio 2 and turn on the RF.
[AC-wlan-ap-office-radio-2] service-template st1
[AC-wlan-ap-office-radio-2] radio enable
[AC-wlan-ap-office-radio-2] quit
[AC-wlan-ap-office] quit
(4) Configure the RADIUS scheme
# Create a RADIUS scheme with the name rs1 and enter this scheme view.
[AC] radius scheme rs1
# Configure the primary authentication and primary billing server of the RADIUS scheme and its communication key.
[AC-radius-rs1] primary authentication 192.168.0.111
[AC-radius-rs1] primary accounting 192.168.0.111
[AC-radius-rs1] key authentication simple radius
[AC-radius-rs1] key accounting simple radius
# Configure that the username sent to the RADIUS server does not carry the ISP domain name.
[AC-radius-rs1] user-name-format without-domain
# Configure the source IP address to be used for sending RADIUS messages to 2.2.2.1.
[AC-radius-rs1] nas-ip 2.2.2.1
[AC-radius-rs1] quit
# Enable the RADUIS session control function.
[AC] radius session-control enable
# Enable the RADIUS DAE service and enter RADIUS DAE server view.
[AC] radius dynamic-author server
# Set the IP address of the RADIUS DAE client to 192.168.0.111, and the shared key used to interact with the RADIUS DAE client for DAE messages is plaintext radius.
[AC-radius-da-server] client ip 192.168.0.111 key simple radius
[AC-radius-da-server] quit
(5) Configure the authentication domain dm2
# Create an ISP domain named dm2 and enter its view.
[AC] domain dm2
# Configure the authentication, authorization, and billing scheme for the lan-access user as RADIUS scheme rs1
[AC-isp-dm2] authentication lan-access radius-scheme rs1
[AC-isp-dm2] authorization lan-access radius-scheme rs1
[AC-isp-dm2] accounting lan-access radius-scheme rs1
[AC-isp-dm2] quit
(6) Configure the authentication domain dm1
# Create an ISP domain named dm1 and enter its view.
[AC] domain dm1
# Configure the AAA authentication method as RADIUS for the Portal user.
[AC-isp-dm1] authentication portal radius-scheme rs1
# Configure the AAA authorization method as RADIUS for the Portal user.
[AC-isp-dm1] authorization portal radius-scheme rs1
# Configure the AAA billing method to none for the Portal user, no billing.
[AC-isp-dm1] accounting portal none
# Specify that the idle cutoff time for users under ISP domain dm1 is 15 minutes, and the traffic generated during the idle cutoff time is 1024 bytes.
[AC-isp-dm1] authorization-attribute idle-cut 15 1024
[AC-isp-dm1] quit
(7) Configuring Portal Authentication
# Configure the Portal authentication server with the name newpt, IP address 192.168.0.111, and port 50100 for listening to Portal messages.
[AC] portal server newpt
[AC-portal-server-newpt] ip 192.168.0.111 key simple portal
[AC-portal-server-newpt] port 50100
# Configure the Portal authentication server type as CMCC.
[AC-portal-server-newpt] server-type cmcc
[AC-portal-server-newpt] quit
# Configure the URL of the Portal Web server as http://192.168.0.111:8080/portal.
[AC] portal web-server newpt
[AC-portal-websvr-newpt] url http://192.168.0.111:8080/portal
# Configure the URL of the Portal Web server that the device redirects to the user to carry the parameters ssid, wlanuserip and wlanacname, whose values are the SSID of the AP, the IP address of the user and the AC name respectively (these three parameters are mandatory when interfacing with China Mobile).
[AC-portal-websvr-newpt] url-parameter ssid ssid
[AC-portal-websvr-newpt] url-parameter wlanuserip source-address
[AC-portal-websvr-newpt] url-parameter wlanacname value AC
# Configure the Portal Web server type as CMCC.
[AC-portal-websvr-newpt] server-type cmcc
[AC-portal-websvr-newpt] quit
# Configure a Portal free authentication rule based on IPv4 address with number 0 and destination address 192.168.0.111 to release traffic accessing the Portal Web server so that users can access the Portal Web server normally.
[AC] portal free-rule 0 destination ip 192.168.0.111 24
# Configure a no-authentication rule from the aggregation port to any in order to release traffic coming from the aggregation port.
[AC] portal free-rule 1 source interface Bridge-Aggregation 1
# Enable the wireless Portal roaming feature.
[AC] portal roaming enable
# Disable the wireless Portal client ARP table entry solidification function.
[AC] undo portal refresh arp enable
# Enable the wireless Portal client legitimacy check function.
[AC] portal host-check enable
# Enable direct mode Portal authentication on wireless service template st1.
[AC] wlan service-template st1
[AC-wlan-st-st1] portal enable method direct
# Configure the incoming Portal user to use the authentication domain as dm1.
[AC-wlan-st-st1] portal domain dm1
# Reference Portal Web server newpt on wireless service template st1.
[AC-wlan-st-st1] portal apply web-server newpt
# Configure the source address for portal messages to be sent on wireless service template st1.
[AC-wlan-st-st1] portal bas-ip 2.2.2.1
[AC-wlan-st-st1] quit
(8) Configure MAC authentication
# Configure MAC authentication and configure to ignore MAC address authentication results.
[AC-wlan-st-st1] client-security authentication-mode mac
[AC-wlan-st-st1] client-security ignore-authentication
[AC-wlan-st-st1] mac-authentication domain dm2
# Enable the wireless service template.
[AC-wlan-st-st1] service-template enable
[AC-wlan-st-st1] quit
3. Configure Switch
# Create VLAN 100 for forwarding traffic within the CAPWAP tunnel between the AC and the AP.
<Switch> system-view
[Switch] vlan 100
[Switch-vlan100] quit
# Create VLAN 200 for forwarding Client wireless packets.
[Switch] vlan 200
[Switch-vlan200] quit
# Create VLAN 2.
[Switch] vlan 2
[Switch-vlan2] quit
# Configure the GigabitEthernet 1/0/1 interface that the Switch connects to the AC with the attribute Trunk to allow VLAN 100 and VLAN 200 to pass.
[Switch] interface gigabitethernet 1/0/1
[Switch-GigabitEthernet1/0/1] port link-type trunk
[Switch-GigabitEthernet1/0/1] port trunk permit vlan 100 200
[Switch-GigabitEthernet1/0/1] quit
# Configure the GigabitEthernet1/0/2 interface attribute of the Switch connected to the AP to be Access and allow VLAN 100 to pass.
[Switch] interface gigabitethernet 1/0/2
[Switch-GigabitEthernet1/0/2] port link-type access
[Switch-GigabitEthernet1/0/2] port access vlan 100
# Enable the PoE function.
[Switch-GigabitEthernet1/0/2] poe enable
[Switch-GigabitEthernet1/0/2] quit
# Configure the GigabitEthernet1/0/3 interface attribute of the Switch connected to the iMC server as Access and allow VLAN 2 to pass.
[Switch] interface gigabitethernet 1/0/3
[Switch-GigabitEthernet1/0/3] port link-type access
[Switch-GigabitEthernet1/0/3] port access vlan 2
[Switch-GigabitEthernet1/0/3] quit
# Configure the IP address of the VLAN 200 interface.
[Switch] interface vlan-interface 200
[Switch-Vlan-interface200] ip address 2.2.2.100 255.255.255.0
[Switch-Vlan-interface200] quit
# Configure the IP address of the VLAN 2 interface.
[Switch] interface vlan-interface 2
[Switch-Vlan-interface2] ip address 192.168.0.100 255.255.255.0
[Switch-Vlan-interface2] quit
Key Configuration
[AC-wlan-st-st1] client-security authentication-mode mac
[AC-wlan-st-st1] client-security ignore-authentication
No comments
Add Comments:
✖
案例意见反馈


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
