组网及说明
要求路由器之间之间路由可达,PC使用loopback口代替,并且有如下要求:
1、ipsec 采用主模式
2、认证方式为证书认证
3、证书需要离线导入到路由器
一、 组网图:
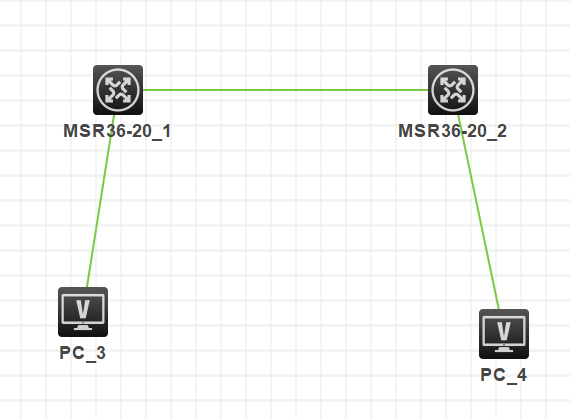
IP地址规划:
|
设备 |
外网口IP |
内网口(loopback)IP |
|
MSR3620-1 |
10.88.142.136/24 |
192.168.10.1 |
|
MSR3620-2 |
10.88.142.214/24 |
192.168.2.1 |
配置步骤
各设备上IP地址和路由的配置省略
1.1
察看路由器上时钟,是否与CA服务器时钟一致
以北京时间为准,不要相差太大,时钟不一致可能导致CA证书失效或未启用
察看修改正确时钟命令如下:
<MSR G2>display clock
23:05:18 beijing Tue 12/14/2021
Time Zone : beijing add 08:00:00
< MSR G2>clock datetime 11:15:00 12/14/2021
1.2
配置pki实体:
#
pki entity 123
common-name 123
#
1.3
配置pki域:
#
pki domain 123
certificate request from ca
certificate request entity 123
public-key rsa general name 123
undo crl check enable
#
1.4
手工申请证书
手工申请证书,打印证书申请字符串,提供证书申请字符串给证书颁发机构:
[MSR G2]pki request-certificate domain 123 pkcs10
.
*** Request for encryption certificate ***
-----BEGIN CERTIFICATE REQUEST-----
MIIBazCB1QIBADAOMQwwCgYDVQQDEwMxMjMwgZ8wDQYJKoZIhvcNAQEBBQADgY0A
MIGJAoGBAMm3ffyxMjv3s1gvkL9Ofca4R8a3wZqQFLb2sVp71aUZCShtG5eTEgGk
oQZjlh9TI/w7FdI7sBmS3kkp80mVmGZGO/wNZaU4IuYidFbwuaX6coeXqhuB7igb
rqSMNI0tCIq3s6Xz3gr5+xwr3vt7t3shdnkBw6z0EQvzBAVPiiSBAgMBAAGgHjAc
BgkqhkiG9w0BCQ4xDzANMAsGA1UdDwQEAwIEMDANBgkqhkiG9w0BAQUFAAOBgQCo
URHLeH74Kb6GXxW3JS7PJLeYmBrcxjesseuJxwhLS9dNI6bjGxQxV4pOV0V8snkE
Xee33lwaOKpATQElsGENsltAao930AgEYyjMpS8dAks5pBXPdKyRi0ggGzkYB/CW
5zDFMermKxvnJOCfg+x4i27GfqLJaAiYaYxjgKsAVw==
-----END CERTIFICATE REQUEST-----
[MSR G2]
1.5
把根证书和本地证书传输到路由器上:
<MSR G2>ftp 172.33.26.100
Trying 172.33.26.100 ...
Press CTRL+K to abort
Connected to 172.33.26.100.
220 Serv-U FTP-Server v2.4 for WinSock ready...
User(172.33.26.100:(none)):f
331 User name okay, need password.
Password:
230 User logged in, proceed.
[ftp]bin
200 Type set to I.
[ftp]get CA.cer
227 Entering Passive Mode (172,33,26,100,13,48)
150 Opening BINARY mode data connection for CA.cer (816 bytes).
226 Transfer complete.
FTP: 816 byte(s) received in 0.093 second(s), 8.00K byte(s)/sec.
[ftp]get 123456.pfx
227 Entering Passive Mode (172,33,26,100,13,49)
150 Opening BINARY mode data connection for 123456.pfx (1118 bytes).
226 Transfer complete.
FTP: 1118 byte(s) received in 0.121 second(s), 9.00K byte(s)/sec.
[ftp]bye
221 Goodbye!
1.6
导入根证书:
[MSR G2]pki import domain 123 der ca filename CA.cer
The trusted CA's finger print is:
MD5 fingerprint:39F8 33BC C02D 84E2 F3F6 15B4 7454 32A8
SHA1 fingerprint:1651 A12B 79A8 1ECF 8093 EB67 65D2 C372 88D2 D4BA
Is the finger print correct?(Y/N):y
[MSR G2]
1.7
导入路由器证书:
[MSR G2]pki import domain 123 p12 local filename 123456.pfx
Please input the password:
The device already has a key pair. If you choose to continue, the existing key pair will be overwritten if it is used for the same purpose. The local certificates, if any, will also be overwritten.
Continue? [Y/N]:y
[MSR G2]
1.8
察看导入的根证书:
[MSR G2]dis pki certificate domain 123 ca
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
37:9e:70:4f:24:51:fb:91:4b:3c:18:50:ee:16:16:0c
Signature Algorithm: sha1WithRSAEncryption
Issuer: DC=com, DC=h3c, CN=www
Validity
Not Before: Apr 20 01:51:11 2015 GMT
Not After : Apr 20 02:01:10 2025 GMT
Subject: DC=com, DC=h3c, CN=www
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:c4:28:c4:ed:4f:58:57:37:28:dc:69:b7:9e:3d:
4d:8b:2a:82:16:25:1c:8f:d7:98:31:35:7e:31:ae:
52:81:c4:5b:91:99:10:c4:19:75:fc:e7:e7:9c:9c:
2b:07:7b:68:96:27:96:5e:31:4e:75:53:5c:87:86:
74:7d:23:33:80:5a:a3:bf:4a:b8:55:76:bd:1f:b4:
7e:2e:84:4a:51:80:74:ed:b7:90:df:76:1d:56:ed:
40:a1:ba:60:a4:b1:5a:77:39:20:e6:04:58:72:f9:
bf:c5:ad:19:ec:b2:2f:01:9d:f2:47:ac:d8:e0:7c:
1a:7a:f0:94:ad:dc:67:e4:f7:94:83:be:df:56:0d:
82:39:68:75:12:ca:b0:e2:c0:71:5e:1a:c2:7c:50:
96:1a:68:58:6f:c9:f5:ab:85:a2:1e:a8:e4:fd:40:
78:0b:4a:3a:6c:ea:ef:27:dd:ea:ff:94:50:aa:c8:
fd:e7:1b:4b:6f:50:17:99:b5:13:f0:35:7c:46:86:
bd:9a:6e:58:25:3f:db:06:0b:cd:35:08:a3:02:9b:
a8:45:72:b9:a4:b2:22:99:4d:48:7b:cf:6f:2b:b2:
e5:69:eb:6e:78:f3:6c:5e:bf:a6:5b:b6:1a:f4:4b:
15:45:c6:d8:24:a2:90:e3:bb:c6:af:d8:c8:c2:b4:
9e:e5
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Key Usage:
Digital Signature, Certificate Sign, CRL Sign
X509v3 Basic Constraints: critical
CA:TRUE
X509v3 Subject Key Identifier:
FE:CB:E5:95:AD:B0:F5:86:91:23:16:02:C3:E2:53:08:C4:4A:BA:11
1.3.6.1.4.1.311.21.1:
...
Signature Algorithm: sha1WithRSAEncryption
78:45:b7:ea:f8:81:38:d9:ec:bd:5d:c6:a0:f0:9c:13:9a:18:
01:2c:33:f2:e8:8a:68:e1:35:51:bb:96:02:1b:3c:73:bb:70:
c0:db:16:3e:7a:ca:78:24:29:22:3f:b2:2f:18:e9:30:70:98:
fa:3d:22:14:c7:bc:d5:21:eb:aa:71:12:1c:73:b3:ff:24:3c:
e2:62:94:5a:aa:c5:92:e6:99:82:27:4f:54:c9:42:80:d6:06:
be:e0:9a:c7:9c:de:59:8a:2f:ed:ac:f0:08:06:9c:76:be:3d:
85:ab:a1:d4:fe:65:60:87:2d:ee:e0:64:38:f2:8d:84:4b:1d:
2a:a6:48:91:e9:e5:0b:d1:52:0d:83:ce:25:e1:aa:6a:06:ac:
8c:5b:5e:93:92:ca:72:52:75:74:d3:5c:70:72:8f:5e:dd:bf:
a2:d1:63:4f:7f:ea:bc:71:fd:4c:a2:3c:43:b7:ab:93:eb:43:
7c:4f:96:e0:5f:36:76:93:1a:91:15:00:af:a2:eb:84:c3:54:
d3:ee:33:dc:b6:50:b4:56:44:ff:e6:58:00:b0:ef:2f:2e:4a:
fd:1f:a6:be:d0:1e:43:5a:c5:77:1b:ce:e5:2f:5a:65:84:1a:
4b:8a:0c:17:f8:e5:08:39:6b:71:af:af:e5:1a:fb:e3:bd:df:
99:43:cc:e5
[MSR G2]display pki certificate domain 123 local
Data:
Version: 3 (0x2)
Serial Number:
1e:f8:00:33:00:00:00:00:1d:1f
Signature Algorithm: sha1WithRSAEncryption
Issuer: DC=com, DC=h3c, CN=www
Validity
Not Before: Dec 13 07:03:46 2021 GMT
Not After : Dec 13 07:13:46 2022 GMT
Subject: CN=123
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (1024 bit)
Modulus:
00:bb:59:aa:93:ad:bf:55:a3:2b:c4:76:2d:70:2d:
23:a4:3c:17:34:d3:0d:12:84:31:f6:b4:66:7a:f0:
7d:66:0b:83:78:c7:7d:af:92:f0:a2:2b:46:75:5a:
90:1a:75:84:d0:c8:44:af:f5:1b:6c:23:ae:13:74:
cf:e2:9c:7a:be:e2:8a:57:e2:4b:59:eb:42:f4:7d:
89:a7:29:12:7f:2f:40:f0:89:82:22:9d:e1:33:23:
c1:c3:64:af:4c:7b:2d:95:57:16:7a:21:e8:ee:30:
59:5b:bd:1e:a8:68:de:43:eb:7a:9b:9a:e6:b7:16:
99:00:86:16:5c:8a:b3:00:3f
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Key Usage:
Digital Signature, Non Repudiation, Key Encipherment, Data Encipherment
X509v3 Subject Key Identifier:
1B:70:46:06:53:43:24:6A:B5:21:6F:F0:C5:BF:85:DA:FF:83:90:77
X509v3 Authority Key Identifier:
keyid:FE:CB:E5:95:AD:B0:F5:86:91:23:16:02:C3:E2:53:08:C4:4A:BA:11
X509v3 CRL Distribution Points:
Full Name:
URI:file://VPNZSBF003/CertEnroll/h3c.crl
Authority Information Access:
CA Issuers - URI:file://VPNZSBF003/CertEnroll/VPNZSBF003_h3c.crt
Signature Algorithm: sha1WithRSAEncryption
2b:aa:f3:70:22:62:99:23:eb:ad:23:3c:08:52:75:bb:eb:e8:
31:7c:b8:b5:b7:4b:41:e3:87:72:f4:9c:66:07:6e:c5:b4:e7:
2f:67:f1:69:bf:08:9c:14:8d:e7:ca:83:ef:3a:a8:e9:f7:62:
2b:81:51:41:48:c7:d8:98:a3:0d:67:78:f6:6b:a9:ed:dc:0d:
69:c4:80:a8:66:a4:b7:71:01:db:fa:2c:ae:61:32:3f:1c:a9:
d0:41:67:3f:85:04:28:a1:99:0c:6a:0c:ce:6b:41:63:af:35:
86:9e:ef:c9:16:24:af:ba:5f:80:5b:6d:98:d1:29:b0:c7:4b:
01:79:44:d5:02:48:45:5d:2a:bc:0d:5b:66:57:34:3d:32:b0:
99:cc:4b:f9:69:0f:e3:37:f3:b7:05:db:9b:7e:9f:50:23:dc:
b8:4e:1f:e5:9e:8a:67:a8:b7:e7:6f:01:e3:d8:71:4c:7f:48:
94:be:0b:6b:63:b9:f1:41:c2:68:9f:90:60:05:5c:f5:0e:4d:
16:d6:16:b9:91:05:11:91:cd:e6:cb:78:21:c4:c0:f2:12:8e:
1a:8f:66:be:45:01:3c:4e:7d:68:92:f6:a9:5f:bd:28:93:be:
25:32:d8:00:41:82:68:ad:8c:d4:3e:8a:22:d6:ca:b6:5b:15:
e4:c3:32:ae
MSR配置IPSec隧道,使用证书认证
1.9
配置证书访问策略
#
pki certificate access-control-policy policy1
rule 1 permit group1
#
pki certificate attribute-group group1
attribute 1 subject-name dn ctn 123 //创建证书属性规则。对端证书subject-name DN中包必需包含(ctn)规则中定义的字符串才被认为是有效的证书。本例使用的证书subject-name DN中包含字符“123”,因此在这里使用参数ctn 123
1.10
配置IKE安全提议,使用证书验证:
#
ike proposal 10
authentication-method rsa-signature
encryption-algorithm 3des-cbc
dh group2
authentication-algorithm md5
#
1.11
配置IKE对端,配置证书认证的PKI域:
#
ike profile 10
certificate domain 123
match remote certificate policy1
match remote identity address 10.88.142.214 255.255.255.255
proposal 10
#
1.12
配置IPSec安全提议:
ipsec transform-set 10
esp encryption-algorithm aes-cbc-128
esp authentication-algorithm sha1
#
1.13
配置要使用IPSec保护的流量:
#
acl advanced 3333
rule 0 permit ip source 192.168.10.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
#
1.14
配置IPSec安全策略:
#
ipsec policy ipsec 10 isakmp
transform-set 10
security acl 3333
remote-address 10.88.142.214
ike-profile 10
#
1.15
在接口下应用IPSec安全策略:
interface ge0/0
ipsec apply policy ipsec
配置关键点
1
2
3
4
✖
案例意见反馈


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
