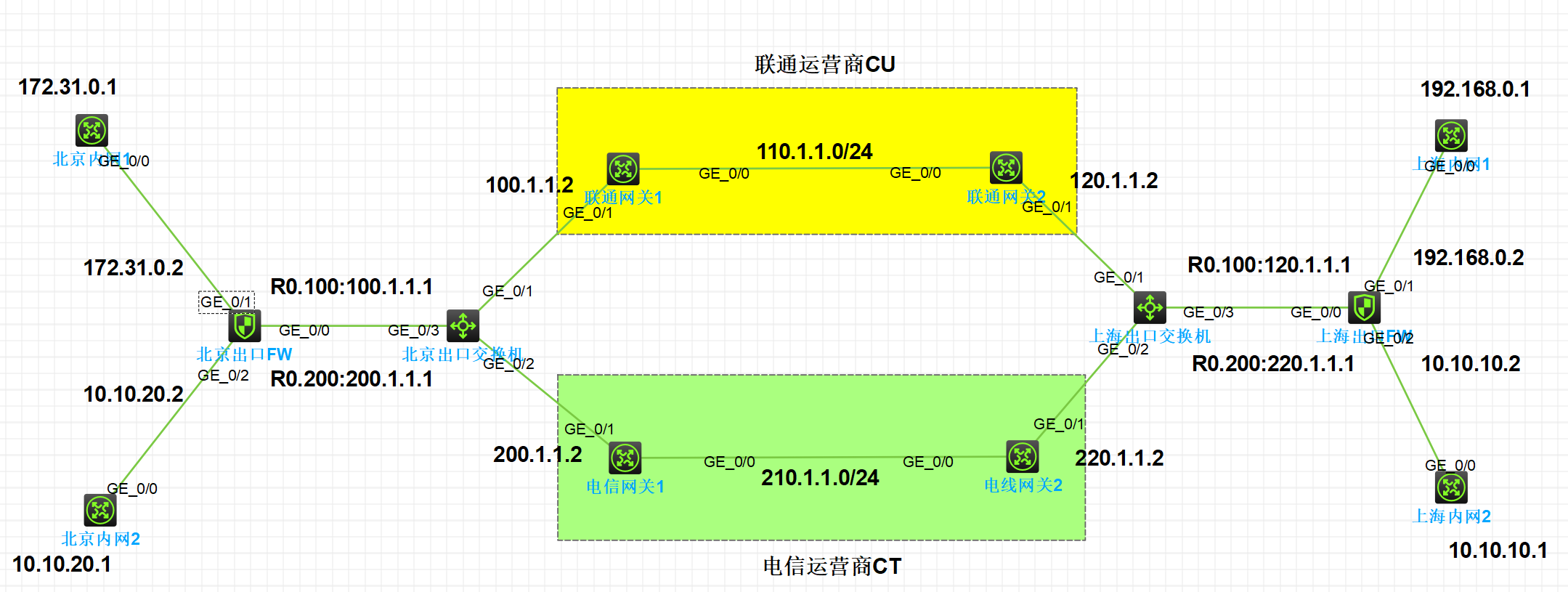
组网及说明
案例组网介绍:
(1)现场上海总部,北京分支;全部使用固定地址建立IPSEC
(2)总部使用模版的方式不校验分支的地址;
(3)总部和分支各有两个公网地址:CU联通 和 CT电信
配置步骤
============北京出口防火墙配置============
vlan 1
#
policy-based-route ipsec permit node 10
if-match acl 3333
apply next-hop 100.1.1.2
#
policy-based-route ipsec permit node 20
if-match acl 3334
apply next-hop 200.1.1.2
#
interface NULL0
#
interface GigabitEthernet1/0/0
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/0.100
description To-CU
ip address 100.1.1.1 255.255.255.0
vlan-type dot1q vid 100
ipsec apply policy IDCCU
#
interface GigabitEthernet1/0/0.200
description To-CT
ip address 200.1.1.1 255.255.255.0
vlan-type dot1q vid 200
ipsec apply policy IDCCT
#
interface GigabitEthernet1/0/1
port link-mode route
combo enable copper
ip address 172.31.0.2 255.255.255.0
#
interface GigabitEthernet1/0/2
port link-mode route
combo enable copper
ip address 10.10.20.2 255.255.255.0
#
security-zone name Management
#
security-zone name CT
import interface GigabitEthernet1/0/0.200
#
security-zone name CU
import interface GigabitEthernet1/0/0.100
#
security-zone name Trust1
import interface GigabitEthernet1/0/1
#
security-zone name Trust2
import interface GigabitEthernet1/0/2
#
ip route-static 0.0.0.0 0 100.1.1.2
ip route-static 0.0.0.0 0 200.1.1.2
ip route-static 192.168.0.1 32 100.1.1.2
ip route-static 192.168.0.1 32 200.1.1.2
#
ip local policy-based-route ipsec
#
acl advanced 3333
rule 0 permit ip source 100.1.1.1 0
#
acl advanced 3334
rule 0 permit ip source 200.1.1.1 0
#
acl advanced name CUCT
rule 0 permit ip source 172.31.0.1 0 destination 192.168.0.1 0
rule 5 permit ip source 10.10.20.1 0 destination 10.10.10.1 0
#
ipsec transform-set ipsectransCT
esp encryption-algorithm aes-cbc-256
esp authentication-algorithm sha256
#
ipsec transform-set ipsectransCU
esp encryption-algorithm aes-cbc-256
esp authentication-algorithm sha256
#
ipsec policy IDCCT 2 isakmp
transform-set ipsectransCT
security acl name CUCT
local-address 200.1.1.1
remote-address 220.1.1.1
ike-profile profileCT
sa trigger-mode auto
#
ipsec policy IDCCU 1 isakmp
transform-set ipsectransCU
security acl name CUCT
local-address 100.1.1.1
remote-address 120.1.1.1
ike-profile profileCU
sa trigger-mode auto
#
ike profile profileCT
keychain CT
exchange-mode aggressive
match remote identity address 220.1.1.1 255.255.255.255
match local address GigabitEthernet1/0/0.200
proposal 1
#
ike profile profileCU
keychain CU
exchange-mode aggressive
match remote identity address 120.1.1.1 255.255.255.255
match local address GigabitEthernet1/0/0.100
proposal 1
#
ike proposal 1
encryption-algorithm aes-cbc-256
dh group14
authentication-algorithm sha256
#
ike keychain CT
match local address GigabitEthernet1/0/0.200
pre-shared-key address 220.1.1.1 255.255.255.255 key cipher $c$3$jrfpxcGv4+l+aB48H+EHLOs6YP2saA==
#
ike keychain CU
match local address GigabitEthernet1/0/0.100
pre-shared-key address 120.1.1.1 255.255.255.255 key cipher $c$3$YhZQpl54n/KsmnsRr+2FiaMr+mL+rw==
#
security-policy ip
rule 0 name 00
action pass
======================上海出口防火墙配置==========================
<H3C>dis cu
#
vlan 1
#
policy-based-route ipsec permit node 10
if-match acl 3333
apply next-hop 120.1.1.2
#
policy-based-route ipsec permit node 20
if-match acl 3334
apply next-hop 220.1.1.2
#
interface NULL0
#
interface GigabitEthernet1/0/0
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/0.100
description To-CU
ip address 120.1.1.1 255.255.255.0
vlan-type dot1q vid 100
ipsec apply policy IDCCU
#
interface GigabitEthernet1/0/0.200
description To-CT
ip address 220.1.1.1 255.255.255.0
vlan-type dot1q vid 200
ipsec apply policy IDCCT
#
interface GigabitEthernet1/0/1
port link-mode route
combo enable copper
ip address 192.168.0.2 255.255.255.0
#
interface GigabitEthernet1/0/2
port link-mode route
combo enable copper
ip address 10.10.10.2 255.255.255.0
#
security-zone name CT
import interface GigabitEthernet1/0/0.200
#
security-zone name CU
import interface GigabitEthernet1/0/0.100
#
security-zone name Trust1
import interface GigabitEthernet1/0/1
#
security-zone name Trust2
import interface GigabitEthernet1/0/2
#
ip route-static 0.0.0.0 0 120.1.1.2
ip route-static 0.0.0.0 0 220.1.1.2
ip route-static 172.31.0.1 32 220.1.1.2
ip route-static 172.31.0.1 32 120.1.1.2
#
ip local policy-based-route ipsec
#
acl advanced 3333
rule 0 permit ip source 120.1.1.1 0
#
acl advanced 3334
rule 0 permit ip source 220.1.1.1 0
#
ipsec transform-set ipsectransCT
esp encryption-algorithm aes-cbc-256
esp authentication-algorithm sha256
#
ipsec transform-set ipsectransCU
esp encryption-algorithm aes-cbc-256
esp authentication-algorithm sha256
#
ipsec policy-template CT 2
transform-set ipsectransCT
local-address 220.1.1.1
ike-profile profileCT
#
ipsec policy-template CU 1
transform-set ipsectransCU
local-address 120.1.1.1
ike-profile profileCU
#
ipsec policy IDCCT 2 isakmp template CT
#
ipsec policy IDCCU 1 isakmp template CU
#
ike profile profileCT
keychain CT
exchange-mode aggressive
match remote identity address 0.0.0.0 0.0.0.0
match local address GigabitEthernet1/0/0.200
proposal 1
#
ike profile profileCU
keychain CU
exchange-mode aggressive
match remote identity address 0.0.0.0 0.0.0.0
match local address GigabitEthernet1/0/0.100
proposal 1
#
ike proposal 1
encryption-algorithm aes-cbc-256
dh group14
authentication-algorithm sha256
#
ike keychain CT
match local address GigabitEthernet1/0/0.200
pre-shared-key address 0.0.0.0 0.0.0.0 key cipher $c$3$wCaM6dCAG+jaVMFNHBlkAnHRKSD8YA==
#
ike keychain CU
match local address GigabitEthernet1/0/0.100
pre-shared-key address 0.0.0.0 0.0.0.0 key cipher $c$3$JzyGhiFbR6rVrL0onk2B2WesT6NsfQ==
#
security-policy ip
rule 0 name 00
action pass
#
配置关键点
案例中解释:
(1)使用acl CUCT包括所有的地址,是为了让所有的流量能在两个隧道走,不区分;
(2)开启ipsec自动触发是为了先把隧道建立起来,兴趣流能直接走隧道封装转发;
(3)!!!关键!!!使用本地PBR是为了让联通的流量一定从联通链路发出、电信的流量一定走电信链路;
(4)总部配置0.0.0.0不认证对端的地址,有可能分支是用的拨号上网;另外本地PBR也不写目的地址原因亦如此;
(5)相同的proposal建议直接调用,不要出现内容相同,proposal ID不同的情况;
本案例结果:
172和192互通
10.10.10.1和10.10.20.1互通;
✖
案例意见反馈


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作


thank you