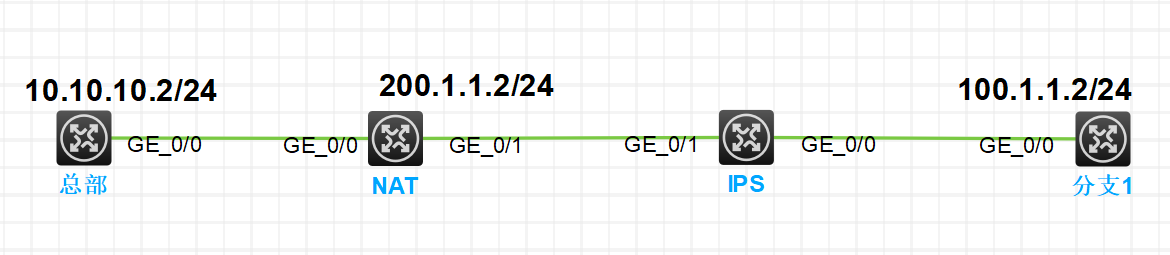
组网及说明
组网图如下:
配置步骤
总部配置如下:
ip vpn-instance vrf
interface LoopBack0 //loopback口模拟业务流量
ip binding vpn-instance vrf
ip address 2.2.2.2 255.255.255.255
interface GigabitEthernet0/0
ip binding vpn-instance vrf
ip address 10.10.10.2 255.255.255.0
interface Tunnel1000 mode ipsec //创建tunnel口模式是ipsec
ip binding vpn-instance vrf //绑定vpn实例vrf
ip address 192.168.213.22 255.255.255.248
source 10.10.10.2
destination 100.1.1.2
tunnel vpn-instance vrf //tunnel口属于vpn实例vrf
tunnel protection ipsec profile fenzhi1
ip route-static vpn-instance vrf 0.0.0.0 0 10.10.10.1
ip route-static vpn-instance vrf 1.1.1.1 32 Tunnel1000
ipsec transform-set fenzhi1
esp encryption-algorithm aes-cbc-256
esp authentication-algorithm sha256
pfs dh-group14
ipsec profile fenzhi1 isakmp
transform-set fenzhi1
ikev2-profile fenzhi1
#
ikev2 keychain fenzhi1
peer fenzhi1
address 100.1.1.2 255.255.255.255
identity address 100.1.1.2
pre-shared-key plaintext 123456
ikev2 profile fenzhi1
authentication-method local pre-share
authentication-method remote pre-share
keychain fenzhi1
identity local fqdn test
inside-vrf vrf
match vrf name vrf
match remote identity address 100.1.1.2 255.255.255.255
ikev2 proposal fenzhi1
encryption aes-cbc-256
integrity sha256
dh group14
ikev2 policy fenzhi1
match vrf name vrf //这个很关键需要绑定vrf,否则无法匹配上导致失败
proposal fenzhi1
分支配置:
interface GigabitEthernet0/0
ip address 100.1.1.2 255.255.255.0
interface Tunnel3 mode ipsec
ip address 192.168.213.17 255.255.255.248
source 100.1.1.2
destination 200.1.1.2
tunnel protection ipsec profile zongbu
ip route-static 0.0.0.0 0 100.1.1.1
ip route-static 2.2.2.2 32 Tunnel3
ipsec transform-set zongbu
esp encryption-algorithm aes-cbc-256
esp authentication-algorithm sha256
pfs dh-group14
ipsec profile zongbu isakmp
transform-set zongbu
ikev2-profile zongbu
ikev2 keychain zongbu
peer zongbu
address 200.1.1.2
identity address 200.1.1.2
pre-shared-key plaintext 123456
ikev2 profile zongbu
authentication-method local pre-share
authentication-method remote pre-share
keychain zongbu
match remote identity fqdn test
ikev2 proposal zongbu
encryption aes-cbc-256
integrity sha256
dh group14
ikev2 policy zongbu //创建ikev2 policy
proposal zongbu //调用proposal
NAT 设备配置
interface GigabitEthernet0/0
ip address 10.10.10.1 255.255.255.0
interface GigabitEthernet0/1
ip address 200.1.1.2 255.255.255.0
nat outbound
nat server protocol udp global current-interface 500 inside 172.25.23.5 500
nat server protocol udp global current-interface 4500 inside 172.25.23.5 4500
ip route-static 0.0.0.0 0 200.1.1.1
IPS配置:
interface GigabitEthernet0/0
ip address 100.1.1.1 255.255.255.0
interface GigabitEthernet0/1
ip address 200.1.1.1 255.255.255.0
配置关键点
注意事项:
因为总部这边是有vpn实例,所以在对应的ikev2的policy地方调用vrf否则会导致policy查询不到 tunnel口down
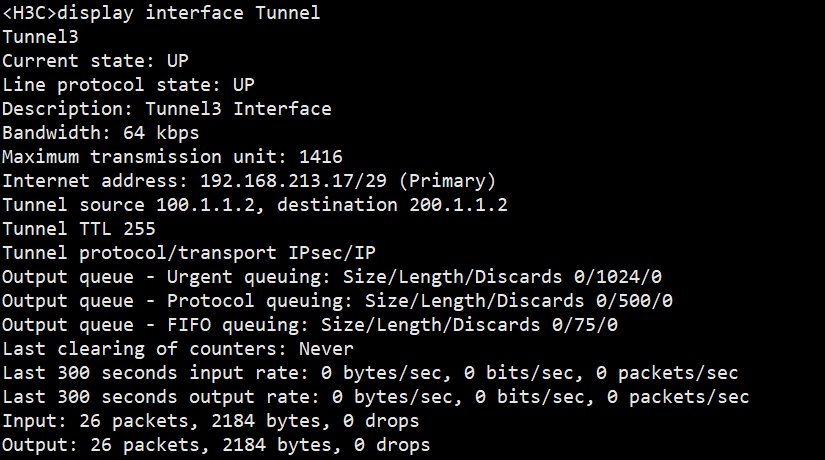
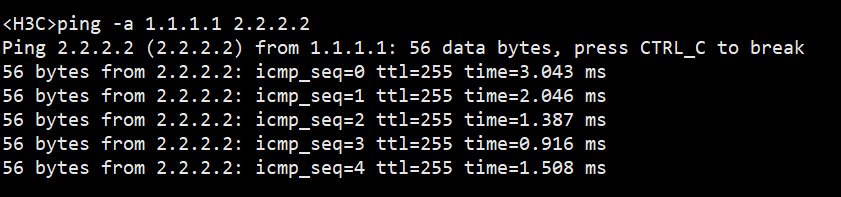
测试情况:
该案例暂时没有网友评论
编辑评论
✖
案例意见反馈


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
