问题描述:
一端是PPPOE模式自动获取的地址,一端是固定IP,中间一台路由器模拟外网,现在做上IPSEC野蛮模式后,底下PC无法互通
组网及组网描述:
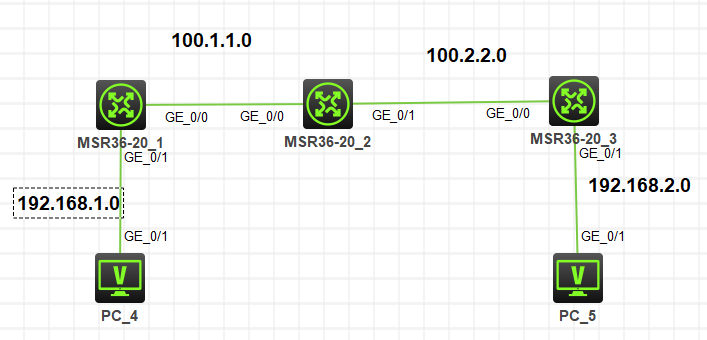
RT1
# interface GigabitEthernet0/0
port link-mode route
combo enable copper
ip address 100.1.1.2 255.255.255.0
nat outbound 3001
ipsec apply policy rta
# interface GigabitEthernet0/1
port link-mode route
combo enable copper
ip address 192.168.1.1 255.255.255.0
# ip route-static 0.0.0.0 0 100.1.1.1
ip route-static 192.168.2.0 24 100.1.1.1
# acl advanced 3000
rule 0 permit ip source 192.168.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
# acl advanced 3001
rule 0 deny ip source 192.168.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
rule 5 permit ip
ipsec transform-set rta
esp encryption-algorithm des-cbc
esp authentication-algorithm md5
# ipsec policy-template rta 1
transform-set rta
security acl 3000
ike-profile rta
# ipsec policy rta 1 isakmp template rta
# ike identity fqdn rta
# ike profile rta keychain rta
exchange-mode aggressive
match remote identity fqdn rtb
proposal 1
# ike proposal 1
# ike keychain rta
pre-shared-key hostname rtb key cipher $c$3$VMVSD5wr+5H/di47+qKz7hElVoqDUQEz1Q==
# return
RT2
# interface Virtual-Template1
ppp authentication-mode chap domain system
ppp chap user user1
remote address pool 1
ip address 100.2.2.1 255.255.255.0
interface GigabitEthernet0/0
port link-mode route
combo enable copper
ip address 100.1.1.1 255.255.255.0
interface GigabitEthernet0/1
port link-mode route
combo enable copper
pppoe-server bind virtual-template 1
# local-user user1 class network
password cipher $c$3$MuPd+IF4dmCJH0zQxEolYuyvTVE9Ks4=
service-type ppp
authorization-attribute user-role network-operator
RTC
# dialer-group 1 rule ip permit
interface Dialer1
mtu 1492
ppp chap password cipher $c$3$/29Pz8RGTf9hNRhCcdcZeEmO0VK25eQ=
ppp chap user user1
ppp ipcp dns admit-any
ppp ipcp dns request
dialer bundle enable
dialer-group 1
dialer timer idle 0
dialer timer autodial 1
ip address ppp-negotiate
tcp mss 1200
nat outbound 3001
# interface GigabitEthernet0/0
port link-mode route
combo enable copper
pppoe-client dial-bundle-number 1
ipsec apply policy rtb
# interface GigabitEthernet0/1
port link-mode route
combo enable copper
ip address 192.168.2.1 255.255.255.0
# ip route-static 0.0.0.0 0 Dialer1
ip route-static 192.168.1.0 24 Dialer1
# acl advanced 3000
rule 0 permit ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
# acl advanced 3001 rule 0 deny ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
rule 5 permit ip
# ipsec transform-set rtb
esp encryption-algorithm des-cbc
esp authentication-algorithm md5
# ipsec policy rtb 1 isakmp
transform-set rtb
security acl 3000
remote-address 100.1.1.2
ike-profile rtb
# ike identity fqdn rtb
# ike profile rtb keychain rtb
exchange-mode aggressive
match remote identity fqdn rta
proposal 1
# ike keychain rtb
pre-shared-key address 100.1.1.2 255.255.255.255 key cipher $c$3$oW4gmCObpuLn1/PJhebMcTaBTjU52m6+Pg==
- 2020-10-23提问
- 举报
-
(0)
最佳答案

dis ike sa
dis ipsec sa
都有输出吗
- 2020-10-23回答
- 评论(2)
- 举报
-
(0)
我也遇到这种情况了,不过有输出。但是还是ping不通对端内网地址,会不会是对端的acl没放通
没有
我也遇到这种情况了,不过有输出。但是还是ping不通对端内网地址,会不会是对端的acl没放通
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明


