F100-C80-WINET 的 L2TP能拨号,不能访问内网资源
- 0关注
- 1收藏,2005浏览
问题描述:
1、我的笔记本接入客户内网的时候,可以ping通 客户服务器、客户电脑,检查过 服务器、客户电脑防火墙都允许 ping;
2、我的笔记本实用手机热点,能 L2tp 拨号进客户防火墙,但是 ping不通 服务器、客户电脑。
3、防火墙可以正常与服务器、客户电脑 ping通的;
4、命令如下:
local-user vpnuser class network
password simple vpnuser
service-type ppp
quit
domain system
authentication ppp local
quit
l2tp enable
ip pool l2tp-1 172.16.100.10 172.16.100.200
ip pool l2tp-1 gateway 172.16.100.1
int virtual-template 1
ppp authentication-mode chap domain system
remote address pool l2tp-1
quit
security-zone name Untrust
import interface Virtual-Template 1
quit
acl basic 2000
rule permit source any
quit
zone-pair security source untrust destination local
packet-filter 2000
quit
l2tp-group 1 mode lns
tunnel name LNS
allow l2tp virtual-template 1
undo tunnel authentication
object-group service 1701
service udp destination eq 1701
quit
object-policy ip 1701
rule pass service 1701
quit
zone-pair security source Untrust destination Local
object-policy apply ip 1701
quit
zone-pair security source Local destination Untrust
object-policy apply ip 1701
quit
object-group ip address neiwang
network subnet 172.16.0.0 255.255.255.0
quit
object-policy ip neiwang
rule pass destination-ip neiwang
quit
zone-pair security source Untrust destination Trust
object-policy apply ip neiwang
quit
组网及组网描述:
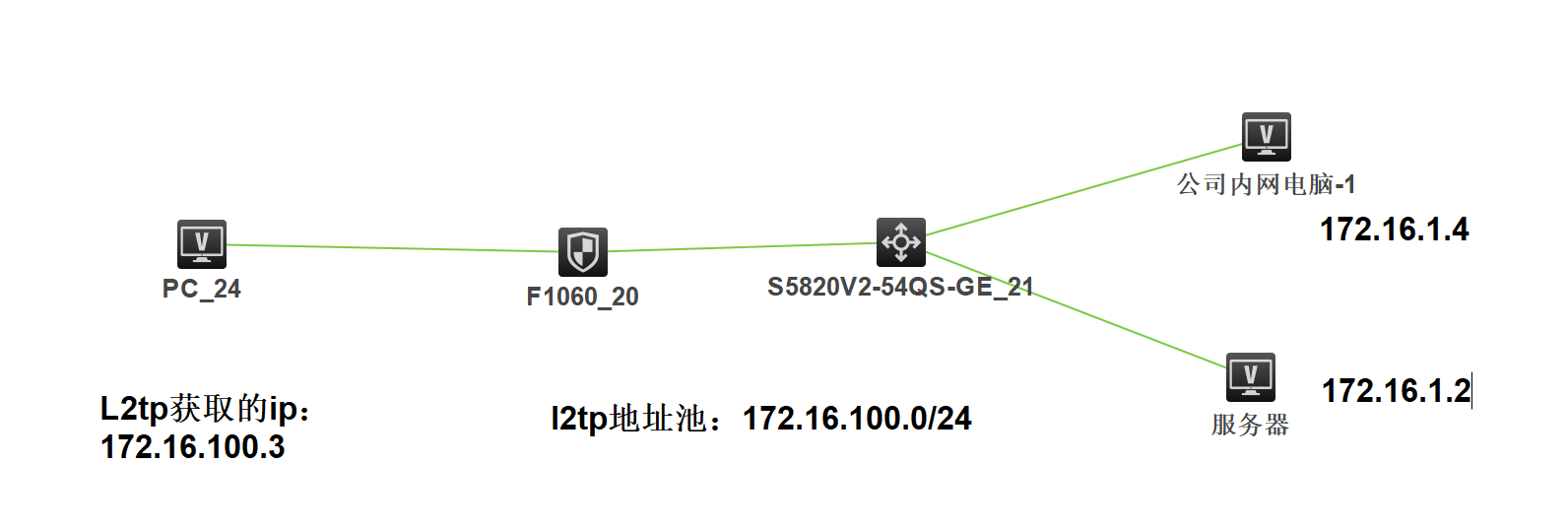
- 2020-11-10提问
- 举报
-
(0)
最佳答案

您好,请知:
检查下L2TP VPN的地址段是否有在路由内向内网发布。
检查内网的核心设备是否有VPN网段的路由。
VT配置下ip地址为172.16.100.1看下。
- 2020-11-10回答
- 评论(7)
- 举报
-
(0)
核心交换机看过,没有VPN到内网的路由。防火墙上设置的路由是: ip route-static 0.0.0.0 0 120.196.131.97 ip route-static 172.16.1.0 24 192.168.30.2; 核心的路由是: ip route-static 0.0.0.0 0 192.168.30.1 请问要怎么加路由呢
交换机和防火墙的互联地址是192.168.30.0的网段?
安全策略,比如对象组这里没有看到172.16.100.0的网段
防火墙、核心的管理网段是 192.168.30.0
完整的配置看下一条评论
您好,看了下策略object-group ip address neiwang这个对象组里面没有看到172.16.100.0这个VPN网段,然后放通的是untrust到trust的
我知道怎么回事了, l2tp 命令没错,只是早上先配置了 IPsec ,中午再配置 l2tp,所以导致 l2tp 能拨号,但是与内网不通。我把 IPsec 删了,l2tp 就可以正常使用了

#
version 7.1.064, Ess 9508
#
sysname fw-foshan
#
context Admin id 1
#
ip vpn-instance management
route-distinguisher 1000000000:1
vpn-target 1000000000:1 import-extcommunity
vpn-target 1000000000:1 export-extcommunity
#
telnet server enable
#
irf mac-address persistent timer
irf auto-update enable
undo irf link-delay
irf member 1 priority 1
#
ip pool l2tp-1 172.16.100.10 172.16.100.200
ip pool l2tp-1 gateway 172.16.100.1
#
dns proxy enable
dns server 211.136.192.6
#
password-recovery enable
#
vlan 1
#
object-group ip address 172.16.1.0
0 network subnet 172.16.1.0 255.255.255.0
#
object-group ip address neiwang
0 network subnet 172.16.1.0 255.255.255.0
10 network subnet 192.168.30.0 255.255.255.0
#
object-group service 1701
0 service udp destination eq 1701
#
interface Virtual-Template1
ppp authentication-mode chap domain system
remote address pool l2tp-1
ip address 172.16.100.1 255.255.255.0
#
interface NULL0
#
interface GigabitEthernet1/0/3
port link-mode route
ip address 120.XXXXXXXXX.100 255.255.255.248
nat outbound 3200
ipsec apply policy changchun
#
interface GigabitEthernet1/0/4
port link-mode route
ip address 192.168.30.1 255.255.255.0
#
object-policy ip 1701
rule 0 pass service 1701
#
object-policy ip Local-Untrust
rule 0 pass
#
object-policy ip Untrust-Local
rule 0 drop service ssh
rule 0 append service telnet
#
object-policy ip Untrust-Trust
rule 0 pass source-ip 192.168.5.0 destination-ip 172.16.1.0
#
object-policy ip neiwang
rule 0 drop service ssh
rule 0 append service telnet
#
object-policy ip pass
rule 0 pass
#
security-zone name Local
#
security-zone name Trust
import interface GigabitEthernet1/0/4
#
security-zone name DMZ
#
security-zone name Untrust
import interface GigabitEthernet1/0/3
import interface Virtual-Template1
#
security-zone name Management
import interface GigabitEthernet1/0/0
import interface GigabitEthernet1/0/2
#
zone-pair security source Local destination Trust
object-policy apply ip pass
#
zone-pair security source Local destination Untrust
object-policy apply ip Local-Untrust
#
zone-pair security source Trust destination Local
object-policy apply ip pass
packet-filter 3000
#
zone-pair security source Trust destination Untrust
object-policy apply ip pass
#
zone-pair security source Untrust destination Local
object-policy apply ip Untrust-Local
packet-filter 2000
#
zone-pair security source Untrust destination Trust
object-policy apply ip neiwang
#
ip route-static 0.0.0.0 0 120.196.131.97
ip route-static 172.16.1.0 24 192.168.30.2
#
ssh server enable
#
acl basic 2000
rule 0 permit
#
acl advanced 3000
rule 0 permit ip
#
acl advanced 3100
rule 0 permit ip source 172.16.1.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
rule 5 permit ip source 172.16.1.0 0.0.0.255 destination 192.168.5.0 0.0.0.255
#
acl advanced 3200
rule 0 deny ip source 172.16.1.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
rule 5 deny ip source 172.16.1.0 0.0.0.255 destination 192.168.5.0 0.0.0.255
rule 10 permit ip
#
domain system
authentication ppp local
#
aaa session-limit ftp 16
aaa session-limit telnet 16
aaa session-limit ssh 16
domain default enable system
#
user-group system
#
local-user l2tpuser class network
password cipher $c$3$FSHePZak1wFpAG1+spqUSyTub0aMA7K6TqfKrjB2Zg==
service-type ppp
authorization-attribute user-role network-operator
#
l2tp-group 1 mode lns
allow l2tp virtual-template 1
undo tunnel authentication
tunnel name LNS
#
l2tp enable
#
ip http enable
ip https enable
#
return
- 2020-11-10回答
- 评论(0)
- 举报
-
(0)
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明



我知道怎么回事了, l2tp 命令没错,只是早上先配置了 IPsec ,中午再配置 l2tp,所以导致 l2tp 能拨号,但是与内网不通。我把 IPsec 删了,l2tp 就可以正常使用了