问题描述:
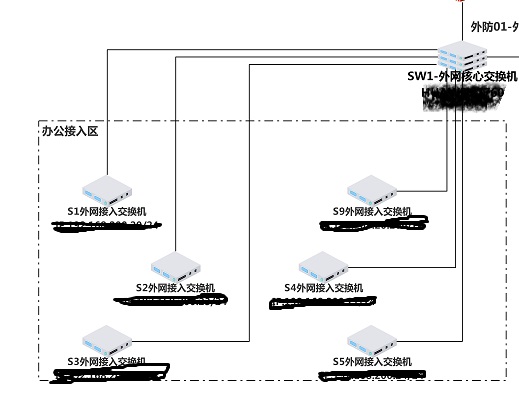
问题是这样的,我公司楼层交换机由H3C S3100组建而成,现在出现了一个奇怪的问题,本来S4交换机是为4楼PC分配地址进行交换任务的,S9交换机是为9楼PC端分配的,现在S4交换交换机11口的线插上,9楼的办公室可以上网,但是7楼这个办公室对应的S9交换机15口也必须插上,如果把S4交换机11口的线拔掉,9楼的这个办公室就不能上网了,把S9交换机的15口线拔掉,这个办公室也不能上网了,而且办公楼的所有PC端都是192.168.20段的地址,突然有一天,9楼的这个办公室就变成192.168.1段的地址了,请问大佬们谁知道这是怎么回事呢?怎么能处理一下且不影响上网呢?
组网及组网描述:
设置列表
- 有序列表
- 无序列表
- 2020-12-03提问
- 举报
-
(0)

被你说晕了,能看下配置吗,全网的
- 2020-12-03回答
- 评论(2)
- 举报
-
(0)
就是说S9交换机下端的pc,不知道怎么就和S4的某个口连上了,S4的这个口上链接pc的线一拔掉,S9的这个PC就上不了网了,当然S9链接这个PC的线被拔掉后,也是上不网的,而且PC段都在20段,就现在S9都在1段上了

您好,请知:
检查下现网的具体接入配置中是否存在有环路。
另外需反馈下配置情况。
- 2020-12-03回答
- 评论(1)
- 举报
-
(0)
你需要什么配置呢?
你需要什么配置呢?


[Internet-S4]dis cu
!Software Version V200R011C10SPC600
#
sysname Internet-S4
#
vlan batch 20 100 110
#
authentication-profile name default_authen_profile
authentication-profile name dot1x_authen_profile
dot1x-access-profile dot1x_access_profile
authentication-profile name mac_authen_profile
authentication-profile name portal_authen_profile
authentication-profile name dot1xmac_authen_profile
authentication-profile name multi_authen_profile
#
arp anti-attack packet-check sender-mac dst-mac
#
dhcp enable
#
radius-server template default
radius-server template default_mould
radius-server shared-key cipher %^%#&b#LTj^CJ@I=%w'>uh%;3g\e0_K#|LMSdE6+v8pV%^%#
radius-server authentication 192.168.10.2 1812 weight 80
#
pki realm default
certificate-check none
#
free-rule-template name default_free_rule
#
portal-access-profile name portal_access_profile
#
vlan 20
description This vlan Access Internet
vlan 110
description This vlan used to manage device
#
aaa
authentication-scheme default
authentication-scheme radius
authentication-mode radius
authentication-scheme default_radius
authentication-mode radius
authorization-scheme default
accounting-scheme default
local-aaa-user password policy administrator
password history record number 0
password expire 0
domain default
authentication-scheme default_radius
radius-server default_mould
domain default_admin
authentication-scheme default
local-user admin password irreversible-cipher $1a$NLSn&tSty>$Zb';=9h&o;W]OwCQx\*(lV""K`PC;TXRA|Q#1v0V$
local-user admin privilege level 15
local-user admin service-type terminal http
#
interface Vlanif20
ip address 192.168.20.204 255.255.255.0
#
interface Vlanif110
ip address 192.168.200.21 255.255.255.0
#
interface GigabitEthernet0/0/1
port link-type access
port default vlan 20
loopback-detect enable
#
interface GigabitEthernet0/0/2
port link-type access
port default vlan 20
loopback-detect enable
authentication-profile dot1x_authen_profile
#
interface GigabitEthernet0/0/3
port link-type access
port default vlan 20
loopback-detect enable
authentication-profile dot1x_authen_profile
#
interface GigabitEthernet0/0/4
port link-type access
port default vlan 20
loopback-detect enable
authentication-profile dot1x_authen_profile
#
interface GigabitEthernet0/0/5
port link-type access
port default vlan 20
loopback-detect enable
authentication-profile dot1x_authen_profile
#
interface GigabitEthernet0/0/6
port link-type access
port default vlan 20
loopback-detect enable
authentication-profile dot1x_authen_profile
#
interface GigabitEthernet0/0/7
port link-type access
port default vlan 20
loopback-detect enable
authentication-profile dot1x_authen_profile
#
interface GigabitEthernet0/0/8
port link-type access
port default vlan 20
loopback-detect enable
authentication-profile dot1x_authen_profile
#
interface GigabitEthernet0/0/9
port link-type access
port default vlan 20
loopback-detect enable
authentication-profile dot1x_authen_profile
#
interface GigabitEthernet0/0/10
port link-type access
port default vlan 20
loopback-detect enable
authentication-profile dot1x_authen_profile
#
interface GigabitEthernet0/0/11
port link-type access
port default vlan 20
loopback-detect enable
authentication-profile dot1x_authen_profile
#
interface GigabitEthernet0/0/12
port link-type access
port default vlan 20
loopback-detect enable
authentication-profile dot1x_authen_profile
#
interface GigabitEthernet0/0/13
port link-type access
port default vlan 20
loopback-detect enable
#
interface GigabitEthernet0/0/14
port link-type access
port default vlan 20
loopback-detect enable
authentication-profile dot1x_authen_profile
#
interface GigabitEthernet0/0/15
port link-type access
port default vlan 20
loopback-detect enable
authentication-profile dot1x_authen_profile
#
interface GigabitEthernet0/0/16
port link-type access
port default vlan 20
loopback-detect enable
authentication-profile dot1x_authen_profile
#
interface GigabitEthernet0/0/17
port link-type access
port default vlan 20
loopback-detect enable
authentication-profile dot1x_authen_profile
#
interface GigabitEthernet0/0/18
port link-type access
port default vlan 20
loopback-detect enable
authentication-profile dot1x_authen_profile
#
interface GigabitEthernet0/0/19
port link-type access
port default vlan 20
loopback-detect enable
authentication-profile dot1x_authen_profile
#
interface GigabitEthernet0/0/20
port link-type access
port default vlan 20
loopback-detect enable
authentication-profile dot1x_authen_profile
#
interface GigabitEthernet0/0/21
port link-type access
port default vlan 20
loopback-detect enable
authentication-profile dot1x_authen_profile
#
interface GigabitEthernet0/0/22
port link-type access
port default vlan 20
loopback-detect enable
authentication-profile dot1x_authen_profile
#
interface GigabitEthernet0/0/23
port link-type access
port default vlan 20
loopback-detect enable
#
interface GigabitEthernet0/0/24
port link-type trunk
undo port trunk allow-pass vlan 1
port trunk allow-pass vlan 20 110
#
interface GigabitEthernet0/0/25
loopback-detect enable
#
interface GigabitEthernet0/0/26
loopback-detect enable
#
interface GigabitEthernet0/0/27
port link-type trunk
undo port trunk allow-pass vlan 1
port trunk allow-pass vlan 20 110
loopback-detect enable
#
interface GigabitEthernet0/0/28
port link-type trunk
undo port trunk allow-pass vlan 1
port trunk allow-pass vlan 20 110
loopback-detect enable
#
interface NULL0
#
ip route-static 0.0.0.0 0.0.0.0 192.168.20.1
#
user-interface con 0
authentication-mode aaa
user-interface vty 0 4
user-interface vty 16 20
#
dot1x-access-profile name dot1x_access_profile
#
mac-access-profile name mac_access_profile
#
return
- 2020-12-03回答
- 评论(1)
- 举报
-
(0)
S9配置一样
S9配置一样
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明


你有没有PC充当了dhcp server ?