SECPATH F100-C-G2防火墙cpu始终90%以上
- 0关注
- 1收藏,4088浏览
问题描述:
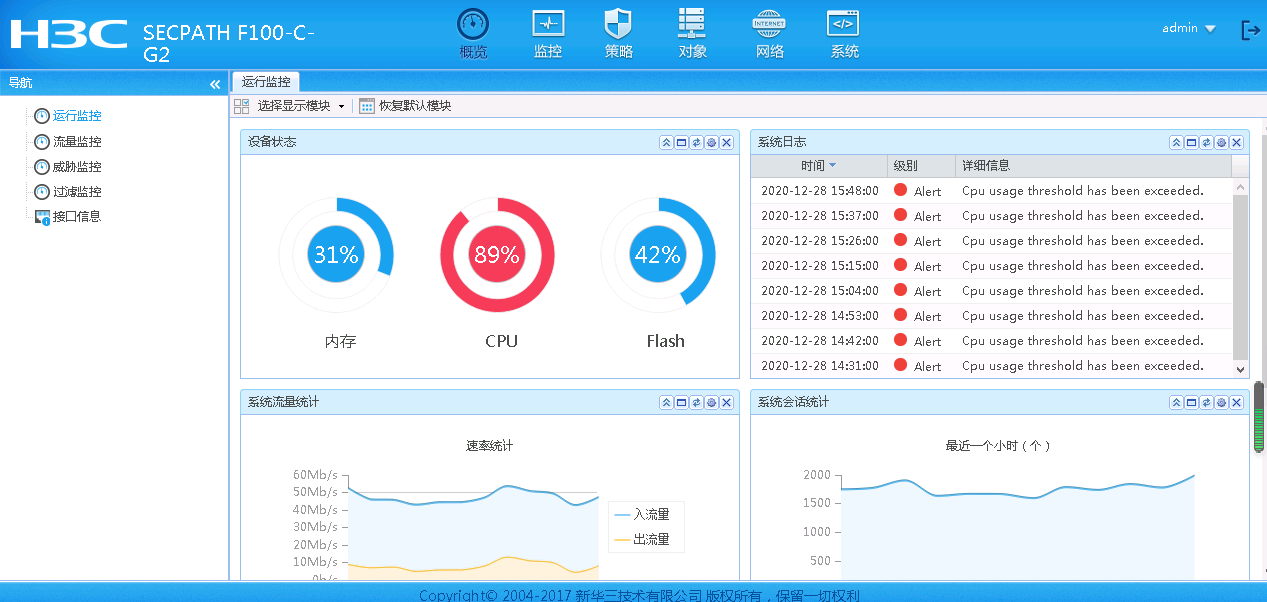
cpu始终90%左右
组网及组网描述:
设置列表
- 有序列表
- 无序列表
重启后cpu依旧,具体诊断信息见附件
- 2020-12-28提问
- 举报
-
(0)
最佳答案

[xlfirewall]dis process
JID PID %CPU %MEM STAT PRI TTY HH:MM:SS COMMAND
1 1 0.0 0.0 S 120 - 00:00:06 scmd
2 2 0.0 0.0 S 115 - 00:00:00 [kthreadd]
3 3 0.0 0.0 S 99 - 00:00:00 [migration/0]
4 4 0.0 0.0 S 115 - 00:00:00 [ksoftirqd/0]
5 5 0.0 0.0 S 99 - 00:00:00 [watchdog/0]
6 6 0.0 0.0 S 99 - 00:00:00 [migration/1]
7 7 0.0 0.0 S 115 - 00:00:00 [ksoftirqd/1]
8 8 0.0 0.0 S 99 - 00:00:00 [watchdog/1]
9 9 0.0 0.0 S 115 - 00:00:00 [events/0]
10 10 0.0 0.0 S 115 - 00:00:00 [events/1]
11 11 0.0 0.0 S 115 - 00:00:00 [khelper]
12 12 0.0 0.0 S 115 - 00:00:00 [kblockd/0]
13 13 0.0 0.0 S 115 - 00:00:00 [kblockd/1]
14 14 0.0 0.0 S 115 - 00:00:00 [ata/0]
15 15 0.0 0.0 S 115 - 00:00:00 [ata/1]
16 16 0.0 0.0 S 115 - 00:00:00 [ata_aux]
17 17 0.0 0.0 S 115 - 00:00:00 [khubd]
18 18 0.0 0.0 S 120 - 00:00:00 [vzmond]
19 19 0.0 0.0 S 120 - 00:00:00 [pdflush]
20 20 0.0 0.0 S 120 - 00:00:00 [pdflush]
21 21 0.0 0.0 S 115 - 00:00:00 [kswapd0]
22 22 0.0 0.0 S 115 - 00:00:00 [aio/0]
23 23 0.0 0.0 S 115 - 00:00:00 [aio/1]
24 24 0.0 0.0 S 115 - 00:00:00 [mtdblockd]
32 32 0.0 0.0 D 115 - 00:00:03 [octeon_spi]
33 33 0.0 0.0 S 115 - 00:00:00 [scsi_eh_0]
34 34 0.0 0.0 S 115 - 00:00:00 [scsi_eh_1]
39 39 0.0 0.0 S 105 - 00:00:00 [dGDB]
43 43 0.0 0.0 D 115 - 00:00:00 [kdrvcp0]
44 44 29.4 0.0 D 115 - 01:09:48 [kdrvdp1]
45 45 0.9 0.0 D 115 - 00:02:23 [kPhyLinkd]
48 48 0.0 0.0 D 100 - 00:00:00 [lipc_topology]
50 50 0.0 0.0 S 120 - 00:00:00 [LOAD]
51 51 0.0 0.0 S 120 - 00:00:00 [LOADProc]
52 52 0.0 0.0 S 100 - 00:00:00 [STM_Main]
53 53 0.0 0.0 D 105 - 00:00:00 [hellopkt]
54 54 0.0 0.0 S 115 - 00:00:00 [lipc_portevt]
55 55 0.0 0.0 S 120 - 00:00:00 [timesyncs]
56 56 0.0 0.0 S 105 - 00:00:00 [kevent]
57 57 0.0 0.0 S 115 - 00:00:00 [kfastlog]
58 58 0.0 0.0 S 115 - 00:00:00 [kuserlog]
59 59 0.0 0.0 S 125 - 00:00:00 [kifupdown]
60 60 0.0 0.0 S 120 - 00:00:00 [kmac/1]
61 61 0.0 0.0 S 120 - 00:00:00 [kipfs/1]
62 62 0.0 0.0 S 120 - 00:00:00 [kip6fs/1]
63 63 0.0 0.0 S 115 - 00:00:00 [ktcp_proxy/1/0]
64 64 0.0 0.0 S 115 - 00:00:00 [ktcp_proxy/1/2]
65 65 0.0 0.0 S 115 - 00:00:00 [ktcp_proxy/1/3]
66 66 0.0 0.0 S 115 - 00:00:00 [ktcp_proxy/1/4]
67 67 0.0 0.0 S 120 - 00:00:00 [mbuf_main]
68 68 0.0 0.0 S 105 - 00:00:01 [sock/1]
69 69 0.0 0.0 S 120 - 00:00:00 [ksibsyn]
70 70 0.0 0.0 S 115 - 00:00:00 [kips/1]
71 71 0.0 0.0 S 115 - 00:00:00 [UFLT_KTHREAD1]
72 72 0.0 0.0 S 115 - 00:00:01 [kntop_AVCntop/1]
73 73 0.0 0.0 S 115 - 00:00:00 [kntop_ntop/1]
74 74 0.0 0.0 S 115 - 00:00:00 [kntop_Auditntop]
76 76 0.0 0.0 S 110 - 00:00:00 cioctld
77 77 0.0 0.0 S 120 - 00:00:00 mdcagentd
78 78 0.0 0.0 S 120 - 00:00:00 fsd
80 80 0.0 0.0 S 120 - 00:00:00 licd --mode=3 --did=2
81 81 0.0 0.1 S 100 - 00:00:02 dbmd
83 83 0.9 0.0 S 120 - 00:02:18 diagd -dflash --memale
84 84 0.0 0.0 S 105 - 00:00:00 had
85 85 0.1 0.0 S 120 - 00:00:07 syslogd --logfile=1 --
86 86 0.0 0.0 S 120 - 00:00:07 devd
90 90 0.0 0.0 S 120 - 00:00:00 edev --FanDirection --
91 91 0.0 0.0 S 120 - 00:00:00 mdcd --support-mode=4
94 94 0.0 0.0 S 120 - 00:00:02 ifmgr --pigroupnum=1 -
102 102 0.0 0.0 S 120 - 00:00:00 appprofiled
103 103 0.0 0.0 S 120 - 00:00:01 aprd
104 104 0.0 0.3 S 120 - 00:00:10 comsh server
105 105 0.0 0.0 S 120 - 00:00:00 sysmand
106 106 0.0 0.0 S 120 - 00:00:01 lauthd
107 107 0.0 0.0 S 120 - 00:00:00 ttymgrd --MaxVTYNum=64
108 108 0.0 0.0 S 120 - 00:00:01 aaad
109 109 0.0 0.0 S 110 - 00:00:00 laggd
110 110 0.0 0.0 S 120 - 00:00:00 tranged
111 111 0.0 0.0 S 120 - 00:00:00 vland --VlanAlloc=3
112 112 0.0 0.0 S 120 - 00:00:00 cryptomgrd
119 119 0.0 0.0 S 120 - 00:00:05 aclmgrd
123 123 0.0 0.0 S 125 - 00:00:00 ipcimd
124 124 0.1 0.0 S 120 - 00:00:01 ethd --MACCFG=0x11 --R
125 125 0.0 0.0 S 125 - 00:00:00 coppd
135 135 0.0 0.0 S 120 - 00:00:00 qosd --LogicIfType=63
137 137 0.0 0.3 S 120 - 00:00:33 xmlcfgd
140 140 0.0 0.0 S 120 - 00:00:00 atkd --SecZone
141 141 0.0 0.0 S 120 - 00:00:00 avcd
142 142 0.0 0.0 S 125 - 00:00:04 dhcpd
143 143 0.0 0.0 S 120 - 00:00:00 dnsd
144 144 0.3 0.1 S 120 - 00:00:57 dpid
145 145 0.0 0.0 S 125 - 00:00:08 httpd -w 2 -c 1024
146 146 0.1 0.2 S 120 - 00:00:01 iked
147 147 0.0 0.0 S 120 - 00:00:00 ipsecd
148 148 0.0 0.0 S 125 - 00:00:01 ipstackd --ARPMaxStati
149 149 0.0 0.0 S 120 - 00:00:00 natd --Hotbackup
150 150 4.1 0.2 S 120 - 00:14:11 ntopd
151 151 0.0 0.0 S 120 - 00:00:00 objpd
152 152 0.0 0.0 S 120 - 00:00:00 pcapwared
153 153 0.0 0.0 S 120 - 00:00:00 routed --ipv4
154 154 0.0 0.0 S 120 - 00:00:00 seczoned --membertype=
155 155 0.7 0.1 S 120 - 00:00:10 sessiond --Hotbackup
156 156 0.0 0.0 S 120 - 00:00:01 sshd
157 157 0.0 0.0 S 119 - 00:00:00 telnetd -I
163 163 0.0 0.0 S 115 - 00:00:00 [kipsec/1]
169 169 0.0 0.0 S 120 - 00:00:00 staticrtd --ipv4
176 176 46.4 0.0 R 115 - 02:05:08 [karp/1]
185 185 0.0 0.0 S 115 - 00:00:00 [kwadj/1]
188 188 0.0 0.0 S 115 - 00:00:00 [kfib/1]
197 197 0.0 0.0 S 100 - 00:00:00 [loop0]
199 199 0.0 0.0 S 100 - 00:00:00 [loop1]
201 201 0.0 0.0 S 100 - 00:00:00 [loop2]
203 203 0.0 0.0 S 100 - 00:00:00 [loop3]
205 205 0.0 0.0 S 100 - 00:00:00 [loop4]
209 209 0.0 0.0 S 100 - 00:00:00 [loop5]
211 211 0.0 0.0 S 100 - 00:00:00 [loop6]
215 215 0.0 0.0 S 100 - 00:00:00 [loop7]
217 217 0.0 0.0 S 100 - 00:00:00 [loop8]
219 219 0.0 0.0 S 100 - 00:00:00 [loop9]
221 221 0.0 0.0 S 100 - 00:00:00 [loop10]
224 224 0.0 0.0 S 100 - 00:00:00 [loop11]
226 226 0.0 0.0 S 100 - 00:00:00 [loop12]
228 228 0.0 0.0 S 100 - 00:00:00 [loop13]
230 230 0.0 0.0 S 100 - 00:00:00 [loop14]
232 232 0.0 0.0 S 100 - 00:00:00 [loop15]
234 234 0.0 0.0 S 100 - 00:00:00 [loop16]
236 236 0.0 0.0 S 100 - 00:00:00 [loop17]
238 238 0.0 0.0 S 100 - 00:00:00 [loop18]
241 241 0.0 0.0 S 100 - 00:00:00 [loop19]
243 243 0.0 0.0 S 100 - 00:00:00 [loop20]
245 245 0.0 0.0 S 100 - 00:00:00 [loop21]
247 247 0.0 0.0 S 100 - 00:00:00 [loop22]
249 249 0.0 0.0 S 100 - 00:00:00 [loop23]
251 251 0.0 0.0 S 100 - 00:00:00 [loop24]
253 253 0.0 0.0 S 100 - 00:00:00 [loop25]
255 255 0.0 0.0 S 100 - 00:00:00 [loop26]
257 257 0.0 0.0 S 100 - 00:00:00 [loop27]
259 259 0.0 0.0 S 100 - 00:00:00 [loop28]
261 261 0.0 0.0 S 100 - 00:00:00 [loop29]
263 263 0.0 0.0 S 100 - 00:00:00 [loop30]
265 265 0.0 0.0 S 100 - 00:00:00 [loop31]
267 267 0.0 0.0 S 100 - 00:00:00 [loop32]
269 269 0.0 0.0 S 100 - 00:00:00 [loop33]
271 271 0.0 0.0 S 100 - 00:00:00 [loop34]
273 273 0.0 0.0 S 100 - 00:00:00 [loop35]
275 275 0.0 0.0 S 100 - 00:00:00 [loop36]
277 277 0.0 0.0 S 100 - 00:00:00 [loop37]
279 279 0.0 0.0 S 100 - 00:00:00 [loop38]
281 281 0.0 0.0 S 100 - 00:00:00 [loop39]
283 283 0.0 0.0 S 100 - 00:00:00 [loop40]
285 285 0.0 0.0 S 100 - 00:00:00 [loop41]
287 287 0.0 0.0 S 100 - 00:00:00 [loop42]
289 289 0.0 0.0 S 100 - 00:00:00 [loop43]
291 291 0.0 0.0 S 100 - 00:00:00 [loop44]
293 293 0.0 0.0 S 100 - 00:00:00 [loop45]
295 295 0.0 0.0 S 100 - 00:00:00 [loop46]
297 297 0.0 0.0 S 100 - 00:00:00 [loop47]
299 299 0.0 0.0 S 100 - 00:00:00 [loop48]
301 301 0.0 0.0 S 100 - 00:00:00 [loop49]
304 304 0.0 0.0 S 100 - 00:00:00 [loop50]
306 306 0.0 0.0 S 100 - 00:00:00 [loop51]
308 308 0.0 0.0 S 100 - 00:00:00 [loop52]
310 310 0.0 0.0 S 100 - 00:00:00 [loop53]
312 312 0.0 0.0 S 100 - 00:00:00 [loop54]
314 314 0.0 0.0 S 100 - 00:00:00 [loop55]
316 316 0.0 0.0 S 100 - 00:00:00 [loop56]
318 318 0.0 0.0 S 100 - 00:00:00 [loop57]
320 320 0.0 0.0 S 100 - 00:00:00 [loop58]
322 322 0.0 0.0 S 100 - 00:00:00 [loop59]
324 324 0.0 0.0 S 100 - 00:00:00 [loop60]
326 326 0.0 0.0 S 100 - 00:00:00 [loop61]
328 328 0.0 0.0 S 100 - 00:00:00 [loop62]
330 330 0.0 0.0 S 100 - 00:00:00 [loop63]
332 332 0.0 0.0 S 100 - 00:00:00 [loop64]
334 334 0.0 0.0 S 100 - 00:00:00 [loop65]
336 336 0.0 0.0 S 100 - 00:00:00 [loop66]
338 338 0.0 0.0 S 100 - 00:00:00 [loop67]
340 340 0.0 0.0 S 100 - 00:00:00 [loop68]
342 342 0.0 0.0 S 100 - 00:00:00 [loop69]
344 344 0.0 0.0 S 100 - 00:00:00 [loop70]
346 346 0.0 0.0 S 100 - 00:00:00 [loop71]
348 348 0.0 0.0 S 100 - 00:00:00 [loop72]
351 351 0.0 0.0 S 100 - 00:00:00 [loop73]
357 357 0.0 0.0 S 100 - 00:00:00 [loop74]
359 359 0.0 0.0 S 100 - 00:00:00 [loop75]
361 361 0.0 0.0 S 100 - 00:00:00 [loop76]
363 363 0.0 0.0 S 100 - 00:00:00 [loop77]
365 365 0.0 0.0 S 100 - 00:00:00 [loop78]
367 367 0.0 0.0 S 100 - 00:00:00 [loop79]
369 369 0.0 0.0 S 100 - 00:00:00 [loop80]
372 372 0.0 0.0 S 100 - 00:00:00 [loop81]
374 374 0.0 0.0 S 100 - 00:00:00 [loop82]
378 378 0.0 0.0 S 100 - 00:00:00 [loop83]
380 380 0.0 0.0 S 100 - 00:00:00 [loop84]
382 382 0.0 0.0 S 100 - 00:00:00 [loop85]
384 384 0.0 0.0 S 100 - 00:00:00 [loop86]
386 386 0.0 0.0 S 100 - 00:00:00 [loop87]
388 388 0.0 0.0 S 100 - 00:00:00 [loop88]
390 390 0.0 0.0 S 100 - 00:00:00 [loop89]
392 392 0.0 0.0 S 100 - 00:00:00 [loop90]
394 394 0.0 0.0 S 100 - 00:00:00 [loop91]
396 396 0.0 0.0 S 100 - 00:00:00 [loop92]
398 398 0.0 0.0 S 100 - 00:00:00 [loop93]
400 400 0.0 0.0 S 100 - 00:00:00 [loop94]
402 402 0.0 0.0 S 100 - 00:00:00 [loop95]
404 404 0.0 0.0 S 100 - 00:00:00 [loop96]
406 406 0.0 0.0 S 100 - 00:00:00 [loop97]
408 408 0.0 0.0 S 100 - 00:00:00 [loop98]
410 410 0.0 0.0 S 100 - 00:00:00 [loop99]
412 412 0.0 0.0 S 100 - 00:00:00 [loop100]
414 414 0.0 0.0 S 100 - 00:00:00 [loop101]
416 416 0.0 0.0 S 100 - 00:00:00 [loop102]
418 418 0.0 0.0 S 100 - 00:00:00 [loop103]
420 420 0.0 0.0 S 100 - 00:00:00 [loop104]
422 422 0.0 0.0 S 100 - 00:00:00 [loop105]
424 424 0.0 0.0 S 100 - 00:00:00 [loop106]
426 426 0.0 0.0 S 100 - 00:00:00 [loop107]
428 428 0.0 0.0 S 100 - 00:00:00 [loop108]
430 430 0.0 0.0 S 100 - 00:00:00 [loop109]
432 432 0.0 0.0 S 100 - 00:00:00 [loop110]
434 434 0.0 0.0 S 100 - 00:00:00 [loop111]
436 436 0.0 0.0 S 100 - 00:00:00 [loop112]
438 438 0.0 0.0 S 100 - 00:00:00 [loop113]
440 440 0.0 0.0 S 100 - 00:00:00 [loop114]
442 442 0.0 0.0 S 100 - 00:00:00 [loop115]
444 444 0.0 0.0 S 100 - 00:00:00 [loop116]
446 446 0.0 0.0 S 100 - 00:00:00 [loop117]
448 448 0.0 0.0 S 100 - 00:00:00 [loop118]
450 450 0.0 0.0 S 100 - 00:00:00 [loop119]
452 452 0.0 0.0 S 100 - 00:00:00 [loop120]
454 454 0.0 0.0 S 100 - 00:00:00 [loop121]
456 456 0.0 0.0 S 100 - 00:00:00 [loop122]
458 458 0.0 0.0 S 100 - 00:00:00 [loop123]
460 460 0.0 0.0 S 100 - 00:00:00 [loop124]
462 462 0.0 0.0 S 100 - 00:00:00 [loop125]
464 464 0.0 0.0 S 100 - 00:00:00 [loop126]
466 466 0.0 0.0 S 100 - 00:00:00 [loop127]
468 468 0.0 0.0 S 100 - 00:00:00 [loop128]
470 470 0.0 0.0 S 100 - 00:00:00 [loop129]
472 472 0.0 0.0 S 100 - 00:00:00 [loop130]
474 474 0.0 0.0 S 100 - 00:00:00 [loop131]
476 476 0.0 0.0 S 100 - 00:00:00 [loop132]
478 478 0.0 0.0 S 100 - 00:00:00 [loop133]
480 480 0.0 0.0 S 100 - 00:00:00 [loop134]
482 482 0.0 0.0 S 100 - 00:00:00 [loop135]
484 484 0.0 0.0 S 100 - 00:00:00 [loop136]
486 486 0.0 0.0 S 100 - 00:00:00 [loop137]
488 488 0.0 0.0 S 100 - 00:00:00 [loop138]
490 490 0.0 0.0 S 100 - 00:00:00 [loop139]
492 492 0.0 0.0 S 100 - 00:00:00 [loop140]
494 494 0.0 0.0 S 100 - 00:00:00 [loop141]
496 496 0.0 0.0 S 100 - 00:00:00 [loop142]
498 498 0.0 0.0 S 100 - 00:00:00 [loop143]
500 500 0.0 0.0 S 100 - 00:00:00 [loop144]
502 502 0.0 0.0 S 100 - 00:00:00 [loop145]
504 504 0.0 0.0 S 100 - 00:00:00 [loop146]
506 506 0.0 0.0 S 100 - 00:00:00 [loop147]
508 508 0.0 0.0 S 100 - 00:00:00 [loop148]
510 510 0.0 0.0 S 100 - 00:00:00 [loop149]
512 512 0.0 0.0 S 100 - 00:00:00 [loop150]
514 514 0.0 0.0 S 100 - 00:00:00 [loop151]
516 516 0.0 0.0 S 100 - 00:00:00 [loop152]
518 518 0.0 0.0 S 100 - 00:00:00 [loop153]
520 520 0.0 0.0 S 100 - 00:00:00 [loop154]
522 522 0.0 0.0 S 100 - 00:00:00 [loop155]
524 524 0.0 0.0 S 100 - 00:00:00 [loop156]
526 526 0.0 0.0 S 100 - 00:00:00 [loop157]
528 528 0.0 0.0 S 100 - 00:00:00 [loop158]
530 530 0.0 0.0 S 100 - 00:00:00 [loop159]
532 532 0.0 0.0 S 100 - 00:00:00 [loop160]
534 534 0.0 0.0 S 100 - 00:00:00 [loop161]
536 536 0.0 0.0 S 100 - 00:00:00 [loop162]
538 538 0.0 0.0 S 100 - 00:00:00 [loop163]
540 540 0.0 0.0 S 100 - 00:00:00 [loop164]
542 542 0.0 0.0 S 100 - 00:00:00 [loop165]
544 544 0.0 0.0 S 100 - 00:00:00 [loop166]
546 546 0.0 0.0 S 100 - 00:00:00 [loop167]
548 548 0.0 0.0 S 100 - 00:00:00 [loop168]
550 550 0.0 0.0 S 100 - 00:00:00 [loop169]
552 552 0.0 0.0 S 100 - 00:00:00 [loop170]
554 554 0.0 0.0 S 100 - 00:00:00 [loop171]
556 556 0.0 0.0 S 100 - 00:00:00 [loop172]
558 558 0.0 0.0 S 100 - 00:00:00 [loop173]
560 560 0.0 0.0 S 100 - 00:00:00 [loop174]
562 562 0.0 0.0 S 100 - 00:00:00 [loop175]
564 564 0.0 0.0 S 100 - 00:00:00 [loop176]
566 566 0.0 0.0 S 100 - 00:00:00 [loop177]
568 568 0.0 0.0 S 100 - 00:00:00 [loop178]
570 570 0.0 0.0 S 100 - 00:00:00 [loop179]
572 572 0.0 0.0 S 100 - 00:00:00 [loop180]
574 574 0.0 0.0 S 100 - 00:00:00 [loop181]
576 576 0.0 0.0 S 100 - 00:00:00 [loop182]
2042 2042 0.3 0.0 S 120 - 00:00:00 sshd
2044 2044 0.0 0.0 S 120 - 00:00:00 login -f --ipv4 172.17
2046 2046 0.0 0.0 S 120 - 00:00:00 comshc shell level 0
2047 2047 0.2 0.2 S 120 pts/0 00:00:00 comsh server
2050 2050 0.1 0.2 S 120 pts/0 00:00:00 comsh server
2051 2051 0.6 0.2 S 120 pts/0 00:00:00 comsh server
[xlfirewall]
主要是
44 44 29.4 0.0 D 115 - 01:09:48 [kdrvdp1]
176 176 46.4 0.0 R 115 - 02:05:08 [karp/1]
- 2020-12-28回答
- 评论(0)
- 举报
-
(0)


具体要看看配置了什么 有些命名好资源的
- 2020-12-28回答
- 评论(1)
- 举报
-
(0)
[xlfirewall]dis cur # version 7.1.064, Release 9510P06 # sysname xlfirewall # clock timezone Beijing add 08:00:00 clock protocol none # context Admin id 1 # irf mac-address persistent timer irf auto-update enable undo irf link-delay irf member 1 priority 1 # port-mapping application ftp port 821 # password-recovery enable # vlan 1 # object-group ip address 0 description 外网 0 network subnet 0.0.0.0 0.0.0.0 # object-group ip address 172 description 172网段 0 network subnet 172.172.0.0 255.255.252.0 # object-group ip address 172trust description 允许通过防火墙映射公网的172地址 0 network host address 172.172.0.160 10 network host address 172.172.0.167 20 network host address 172.172.1.142 30 network host address 172.172.2.22 40 network host address 172.172.2.91 50 network host address 172.172.3.51 60 network host address 172.172.3.52 70 network host address 172.172.3.54 80 network host address 172.172.2.80 90 network host address 172.172.3.8 100 network host address 172.172.3.7 110 network host address 172.172.3.33 120 network host address 172.172.3.34 130 network host address 172.172.3.56 140 network host address 172.172.1.141 150 network host address 172.172.3.67 160 network host address 172.172.1.150 # object-group ip address 172管理 description 能访问199网段的172段地址 # object-group ip address 199 # object-group ip address dmz-ip # object-group ip address dmz开放 # object-group ip address trust-ip 0 network host address 172.172.0.3 # object-group ip address untrust-ip 0 network host address 221.181.216.10 # object-group ip address 网段0 0 network range 172.172.0.10 172.172.0.254 # object-group ip address 网段1 0 network range 172.172.1.1 172.172.1.254 # object-group ip address 网段2 0 network range 172.172.2.1 172.172.2.254 # object-group ip address 网段3 0 network range 172.172.3.40 172.172.3.254 # interface NULL0 # interface GigabitEthernet1/0/0 port link-mode route combo enable copper ip address 192.168.0.1 255.255.255.0 undo dhcp select server # interface GigabitEthernet1/0/1 port link-mode route combo enable fiber undo dhcp select server # interface GigabitEthernet1/0/2 port link-mode route ip address 192.168.1.1 255.255.255.0 undo dhcp select server # interface GigabitEthernet1/0/3 port link-mode route ip address XX dns server XX dns server 112.4.0.55 nat outbound 3172 undo dhcp select server # interface GigabitEthernet1/0/4 port link-mode route ip address 172.172.0.3 255.255.252.0 nat outbound 3172 nat hairpin enable # interface GigabitEthernet1/0/5 port link-mode route undo dhcp select server # interface GigabitEthernet1/0/6 port link-mode route undo dhcp select server # interface GigabitEthernet1/0/7 port link-mode route undo dhcp select server # interface GigabitEthernet1/0/8 port link-mode route undo dhcp select server # interface GigabitEthernet1/0/9 port link-mode route undo dhcp select server # interface GigabitEthernet1/0/10 port link-mode route ip address 199.199.199.1 255.255.255.0 undo dhcp select server # interface GigabitEthernet1/0/11 port link-mode route undo dhcp select server # object-policy ip Any-Any rule 0 pass source-ip 0 destination-ip 172trust # object-policy ip DMZ-Local rule 0 pass source-ip 199 destination-ip dmz-ip # object-policy ip DMZ-Trust rule 0 pass source-ip 199 destination-ip 172 # object-policy ip DMZ-Untrust rule 0 pass source-ip 199 destination-ip 0 # object-policy ip Local-DMZ rule 0 pass source-ip dmz-ip destination-ip 199 # object-policy ip Local-Trust rule 0 pass source-ip trust-ip destination-ip 172 # object-policy ip Local-Untrust rule 0 pass source-ip untrust-ip destination-ip 0 # object-policy ip Trust-Any rule 0 pass source-ip 0 destination-ip 0 # object-policy ip Trust-DMZ rule 0 pass source-ip 172管理 destination-ip 199 # object-policy ip Trust-Local rule 0 pass source-ip 172 destination-ip trust-ip # object-policy ip Trust-Trust rule 0 pass source-ip 172 destination-ip 172 # object-policy ip Trust-Untrust rule 0 pass source-ip 172trust destination-ip 0 rule 1 pass source-ip 172 destination-ip 0 # object-policy ip Untrust-DMZ rule 0 pass source-ip 0 destination-ip dmz开放 # object-policy ip Untrust-Local rule 0 pass source-ip 0 destination-ip untrust-ip # object-policy ip Untrust-Trust rule 0 pass source-ip 0 destination-ip 172trust rule 1 pass source-ip 0 destination-ip 172 # security-zone name Local # security-zone name Trust import interface GigabitEthernet1/0/4 # security-zone name DMZ import interface GigabitEthernet1/0/10 # security-zone name Untrust import interface GigabitEthernet1/0/3 blacklist enable # security-zone name Management import interface GigabitEthernet1/0/0 import interface GigabitEthernet1/0/2 # zone-pair security source Any destination Any object-policy apply ip Any-Any # zone-pair security source DMZ destination Local object-policy apply ip DMZ-Local # zone-pair security source DMZ destination Trust object-policy apply ip DMZ-Trust # zone-pair security source DMZ destination Untrust object-policy apply ip DMZ-Untrust # zone-pair security source Local destination DMZ object-policy apply ip Local-DMZ # zone-pair security source Local destination Trust object-policy apply ip Local-Trust # zone-pair security source Local destination Untrust object-policy apply ip Local-Untrust # zone-pair security source Trust destination Any object-policy apply ip Trust-Any # zone-pair security source Trust destination DMZ object-policy apply ip Trust-DMZ # zone-pair security source Trust destination Local object-policy apply ip Trust-Local # zone-pair security source Trust destination Trust object-policy apply ip Trust-Trust # zone-pair security source Trust destination Untrust object-policy apply ip Trust-Untrust # zone-pair security source Untrust destination DMZ object-policy apply ip Untrust-DMZ # zone-pair security source Untrust destination Local object-policy apply ip Untrust-Local # zone-pair security source Untrust destination Trust object-policy apply ip Untrust-Trust # scheduler logfile size 16 # line class aux user-role network-operator # line class console user-role network-admin # line class vty user-role network-operator # line aux 0 user-role network-admin # line con 0 authentication-mode scheme user-role network-admin # line vty 0 4 authentication-mode scheme user-role network-admin protocol inbound ssh # line vty 5 63 authentication-mode scheme user-role network-admin # ip route-static 0.0.0.0 0 221.181.216.9 # ssh server enable # time-range 工作时间 08:15 to 17:45 working-day # acl basic 2000 rule 0 permit source 172.172.0.0 0.0.0.255 rule 5 permit source 172.172.1.0 0.0.0.255 rule 10 permit source 172.172.2.0 0.0.0.255 rule 15 permit source 172.172.3.0 0.0.0.255 # acl advanced 3172 rule 0 permit ip source 172.172.0.0 0.0.0.255 rule 5 permit tcp source 172.172.0.0 0.0.0.255 rule 10 permit ip source 172.172.1.0 0.0.0.255 rule 15 permit tcp source 172.172.1.0 0.0.0.255 rule 20 permit tcp source 172.172.2.0 0.0.0.255 rule 25 permit tcp source 172.172.3.0 0.0.0.255 rule 30 permit ip source 172.172.3.0 0.0.0.255 rule 35 permit ip source 172.172.2.0 0.0.0.255 # acl advanced 3333 rule 0 permit ip # domain system # aaa session-limit ftp 16 aaa session-limit telnet 16 aaa session-limit ssh 16 domain default enable system # role name level-0 description Predefined level-0 role # role name level-1 description Predefined level-1 role # role name level-2 description Predefined level-2 role # role name level-3 description Predefined level-3 role # role name level-4 description Predefined level-4 role # role name level-5 description Predefined level-5 role # role name level-6 description Predefined level-6 role # role name level-7 description Predefined level-7 role # role name level-8 description Predefined level-8 role # role name level-9 description Predefined level-9 role # role name level-10 description Predefined level-10 role # role name level-11 description Predefined level-11 role # role name level-12 description Predefined level-12 role # role name level-13 description Predefined level-13 role # role name level-14 description Predefined level-14 role # user-group system # local-user admin class manage password hash $h$6$wjtCJPmuhZDQdZp5$aQEG01EvYsdxqyEk+AQAwNXmdub2WW7eziMofD5oM63lAqsJqVAuZeZe4bL4pkquk2x8xsDuLyLAQ96q1LmhKg== service-type ssh terminal https authorization-attribute user-role level-3 authorization-attribute user-role network-admin authorization-attribute user-role network-operator # local-user xladmin class manage password hash $h$6$KcZd+O16oNaE7Mvv$Eex8rL0ByEMMafNePssk/AhODYbh2otnxaXy/S5M21nf7RGzhBzmeZ8O2RDcXtHEM3yDr9O3/2MNYBscJEPMEA== service-type ssh terminal https authorization-attribute user-role level-3 authorization-attribute user-role network-operator # session statistics enable session top-statistics enable # ip https enable # blacklist ip 167.99.37.148 blacklist ip 178.33.145.241 blacklist global enable # attack-defense policy 1 scan detect level low action drop logging syn-flood action logging ack-flood action logging syn-ack-flood action logging rst-flood action logging fin-flood action logging udp-flood action logging icmp-flood action logging icmpv6-flood action logging dns-flood action logging http-flood action logging signature detect fragment action logging signature detect impossible action logging signature detect teardrop action drop logging signature detect tiny-fragment action logging signature detect ip-option-abnormal action drop logging signature detect smurf action logging signature detect traceroute action logging signature detect ping-of-death action drop logging signature detect large-icmp action logging signature detect large-icmpv6 action logging signature detect tcp-invalid-flags action logging signature detect tcp-null-flag action logging signature detect tcp-all-flags action logging signature detect tcp-syn-fin action logging signature detect tcp-fin-only action logging signature detect land action logging signature detect winnuke action logging signature detect udp-bomb action logging signature detect snork action logging signature detect fraggle action logging # inspect block-source parameter-profile ips_block_default_parameter # inspect block-source parameter-profile url_block_default_parameter # inspect capture parameter-profile ips_capture_default_parameter # inspect logging parameter-profile ips_logging_default_parameter # inspect logging parameter-profile url_logging_default_parameter # inspect redirect parameter-profile av_redirect_default_parameter # inspect redirect parameter-profile ips_redirect_default_parameter # inspect redirect parameter-profile url_redirect_default_parameter # traffic-policy rule name 网段0 time-range 工作时间 action qos profile 带宽0 source-address address-set 网段0 destination-address address-set 0 source-zone Trust destination-zone Untrust rule name 网段1 time-range 工作时间 action qos profile 带宽1 source-address address-set 网段1 destination-address address-set 0 source-zone Trust destination-zone Untrust rule name 网段2 time-range 工作时间 action qos profile 带宽2 source-address address-set 网段2 destination-address address-set 0 source-zone Trust destination-zone Untrust rule name 网段3 time-range 工作时间 action qos profile 带宽3 source-address address-set 网段3 destination-address address-set 0 source-zone Trust destination-zone Untrust profile name 带宽0 bandwidth downstream guaranteed 100 bandwidth downstream maximum 15000 bandwidth upstream guaranteed 100 bandwidth upstream maximum 15000 connection-limit count per-ip 300 bandwidth upstream maximum per-ip 3000 bandwidth downstream maximum per-ip 4000 profile name 带宽1 bandwidth downstream guaranteed 100 bandwidth downstream maximum 15000 bandwidth upstream guaranteed 100 bandwidth upstream maximum 15000 connection-limit count per-ip 300 bandwidth upstream maximum per-ip 3000 bandwidth downstream maximum per-ip 4000 profile name 带宽2 bandwidth downstream guaranteed 100 bandwidth downstream maximum 15000 bandwidth upstream guaranteed 100 bandwidth upstream maximum 15000 connection-limit count per-ip 300 bandwidth upstream maximum per-ip 3000 bandwidth downstream maximum per-ip 4000 profile name 带宽3 bandwidth downstream guaranteed 100 bandwidth downstream maximum 15000 bandwidth upstream guaranteed 100 bandwidth upstream maximum 15000 connection-limit count per-ip 300 bandwidth upstream maximum per-ip 3000 bandwidth downstream maximum per-ip 4000 # ips block-source parameter-profile ips_block_default_parameter # return [xlfirewall] 主要配置
[xlfirewall]dis cur # version 7.1.064, Release 9510P06 # sysname xlfirewall # clock timezone Beijing add 08:00:00 clock protocol none # context Admin id 1 # irf mac-address persistent timer irf auto-update enable undo irf link-delay irf member 1 priority 1 # port-mapping application ftp port 821 # password-recovery enable # vlan 1 # object-group ip address 0 description 外网 0 network subnet 0.0.0.0 0.0.0.0 # object-group ip address 172 description 172网段 0 network subnet 172.172.0.0 255.255.252.0 # object-group ip address 172trust description 允许通过防火墙映射公网的172地址 0 network host address 172.172.0.160 10 network host address 172.172.0.167 20 network host address 172.172.1.142 30 network host address 172.172.2.22 40 network host address 172.172.2.91 50 network host address 172.172.3.51 60 network host address 172.172.3.52 70 network host address 172.172.3.54 80 network host address 172.172.2.80 90 network host address 172.172.3.8 100 network host address 172.172.3.7 110 network host address 172.172.3.33 120 network host address 172.172.3.34 130 network host address 172.172.3.56 140 network host address 172.172.1.141 150 network host address 172.172.3.67 160 network host address 172.172.1.150 # object-group ip address 172管理 description 能访问199网段的172段地址 # object-group ip address 199 # object-group ip address dmz-ip # object-group ip address dmz开放 # object-group ip address trust-ip 0 network host address 172.172.0.3 # object-group ip address untrust-ip 0 network host address 221.181.216.10 # object-group ip address 网段0 0 network range 172.172.0.10 172.172.0.254 # object-group ip address 网段1 0 network range 172.172.1.1 172.172.1.254 # object-group ip address 网段2 0 network range 172.172.2.1 172.172.2.254 # object-group ip address 网段3 0 network range 172.172.3.40 172.172.3.254 # interface NULL0 # interface GigabitEthernet1/0/0 port link-mode route combo enable copper ip address 192.168.0.1 255.255.255.0 undo dhcp select server # interface GigabitEthernet1/0/1 port link-mode route combo enable fiber undo dhcp select server # interface GigabitEthernet1/0/2 port link-mode route ip address 192.168.1.1 255.255.255.0 undo dhcp select server # interface GigabitEthernet1/0/3 port link-mode route ip address XX dns server XX dns server 112.4.0.55 nat outbound 3172 undo dhcp select server # interface GigabitEthernet1/0/4 port link-mode route ip address 172.172.0.3 255.255.252.0 nat outbound 3172 nat hairpin enable # interface GigabitEthernet1/0/5 port link-mode route undo dhcp select server # interface GigabitEthernet1/0/6 port link-mode route undo dhcp select server # interface GigabitEthernet1/0/7 port link-mode route undo dhcp select server # interface GigabitEthernet1/0/8 port link-mode route undo dhcp select server # interface GigabitEthernet1/0/9 port link-mode route undo dhcp select server # interface GigabitEthernet1/0/10 port link-mode route ip address 199.199.199.1 255.255.255.0 undo dhcp select server # interface GigabitEthernet1/0/11 port link-mode route undo dhcp select server # object-policy ip Any-Any rule 0 pass source-ip 0 destination-ip 172trust # object-policy ip DMZ-Local rule 0 pass source-ip 199 destination-ip dmz-ip # object-policy ip DMZ-Trust rule 0 pass source-ip 199 destination-ip 172 # object-policy ip DMZ-Untrust rule 0 pass source-ip 199 destination-ip 0 # object-policy ip Local-DMZ rule 0 pass source-ip dmz-ip destination-ip 199 # object-policy ip Local-Trust rule 0 pass source-ip trust-ip destination-ip 172 # object-policy ip Local-Untrust rule 0 pass source-ip untrust-ip destination-ip 0 # object-policy ip Trust-Any rule 0 pass source-ip 0 destination-ip 0 # object-policy ip Trust-DMZ rule 0 pass source-ip 172管理 destination-ip 199 # object-policy ip Trust-Local rule 0 pass source-ip 172 destination-ip trust-ip # object-policy ip Trust-Trust rule 0 pass source-ip 172 destination-ip 172 # object-policy ip Trust-Untrust rule 0 pass source-ip 172trust destination-ip 0 rule 1 pass source-ip 172 destination-ip 0 # object-policy ip Untrust-DMZ rule 0 pass source-ip 0 destination-ip dmz开放 # object-policy ip Untrust-Local rule 0 pass source-ip 0 destination-ip untrust-ip # object-policy ip Untrust-Trust rule 0 pass source-ip 0 destination-ip 172trust rule 1 pass source-ip 0 destination-ip 172 # security-zone name Local # security-zone name Trust import interface GigabitEthernet1/0/4 # security-zone name DMZ import interface GigabitEthernet1/0/10 # security-zone name Untrust import interface GigabitEthernet1/0/3 blacklist enable # security-zone name Management import interface GigabitEthernet1/0/0 import interface GigabitEthernet1/0/2 # zone-pair security source Any destination Any object-policy apply ip Any-Any # zone-pair security source DMZ destination Local object-policy apply ip DMZ-Local # zone-pair security source DMZ destination Trust object-policy apply ip DMZ-Trust # zone-pair security source DMZ destination Untrust object-policy apply ip DMZ-Untrust # zone-pair security source Local destination DMZ object-policy apply ip Local-DMZ # zone-pair security source Local destination Trust object-policy apply ip Local-Trust # zone-pair security source Local destination Untrust object-policy apply ip Local-Untrust # zone-pair security source Trust destination Any object-policy apply ip Trust-Any # zone-pair security source Trust destination DMZ object-policy apply ip Trust-DMZ # zone-pair security source Trust destination Local object-policy apply ip Trust-Local # zone-pair security source Trust destination Trust object-policy apply ip Trust-Trust # zone-pair security source Trust destination Untrust object-policy apply ip Trust-Untrust # zone-pair security source Untrust destination DMZ object-policy apply ip Untrust-DMZ # zone-pair security source Untrust destination Local object-policy apply ip Untrust-Local # zone-pair security source Untrust destination Trust object-policy apply ip Untrust-Trust # scheduler logfile size 16 # line class aux user-role network-operator # line class console user-role network-admin # line class vty user-role network-operator # line aux 0 user-role network-admin # line con 0 authentication-mode scheme user-role network-admin # line vty 0 4 authentication-mode scheme user-role network-admin protocol inbound ssh # line vty 5 63 authentication-mode scheme user-role network-admin # ip route-static 0.0.0.0 0 221.181.216.9 # ssh server enable # time-range 工作时间 08:15 to 17:45 working-day # acl basic 2000 rule 0 permit source 172.172.0.0 0.0.0.255 rule 5 permit source 172.172.1.0 0.0.0.255 rule 10 permit source 172.172.2.0 0.0.0.255 rule 15 permit source 172.172.3.0 0.0.0.255 # acl advanced 3172 rule 0 permit ip source 172.172.0.0 0.0.0.255 rule 5 permit tcp source 172.172.0.0 0.0.0.255 rule 10 permit ip source 172.172.1.0 0.0.0.255 rule 15 permit tcp source 172.172.1.0 0.0.0.255 rule 20 permit tcp source 172.172.2.0 0.0.0.255 rule 25 permit tcp source 172.172.3.0 0.0.0.255 rule 30 permit ip source 172.172.3.0 0.0.0.255 rule 35 permit ip source 172.172.2.0 0.0.0.255 # acl advanced 3333 rule 0 permit ip # domain system # aaa session-limit ftp 16 aaa session-limit telnet 16 aaa session-limit ssh 16 domain default enable system # role name level-0 description Predefined level-0 role # role name level-1 description Predefined level-1 role # role name level-2 description Predefined level-2 role # role name level-3 description Predefined level-3 role # role name level-4 description Predefined level-4 role # role name level-5 description Predefined level-5 role # role name level-6 description Predefined level-6 role # role name level-7 description Predefined level-7 role # role name level-8 description Predefined level-8 role # role name level-9 description Predefined level-9 role # role name level-10 description Predefined level-10 role # role name level-11 description Predefined level-11 role # role name level-12 description Predefined level-12 role # role name level-13 description Predefined level-13 role # role name level-14 description Predefined level-14 role # user-group system # local-user admin class manage password hash $h$6$wjtCJPmuhZDQdZp5$aQEG01EvYsdxqyEk+AQAwNXmdub2WW7eziMofD5oM63lAqsJqVAuZeZe4bL4pkquk2x8xsDuLyLAQ96q1LmhKg== service-type ssh terminal https authorization-attribute user-role level-3 authorization-attribute user-role network-admin authorization-attribute user-role network-operator # local-user xladmin class manage password hash $h$6$KcZd+O16oNaE7Mvv$Eex8rL0ByEMMafNePssk/AhODYbh2otnxaXy/S5M21nf7RGzhBzmeZ8O2RDcXtHEM3yDr9O3/2MNYBscJEPMEA== service-type ssh terminal https authorization-attribute user-role level-3 authorization-attribute user-role network-operator # session statistics enable session top-statistics enable # ip https enable # blacklist ip 167.99.37.148 blacklist ip 178.33.145.241 blacklist global enable # attack-defense policy 1 scan detect level low action drop logging syn-flood action logging ack-flood action logging syn-ack-flood action logging rst-flood action logging fin-flood action logging udp-flood action logging icmp-flood action logging icmpv6-flood action logging dns-flood action logging http-flood action logging signature detect fragment action logging signature detect impossible action logging signature detect teardrop action drop logging signature detect tiny-fragment action logging signature detect ip-option-abnormal action drop logging signature detect smurf action logging signature detect traceroute action logging signature detect ping-of-death action drop logging signature detect large-icmp action logging signature detect large-icmpv6 action logging signature detect tcp-invalid-flags action logging signature detect tcp-null-flag action logging signature detect tcp-all-flags action logging signature detect tcp-syn-fin action logging signature detect tcp-fin-only action logging signature detect land action logging signature detect winnuke action logging signature detect udp-bomb action logging signature detect snork action logging signature detect fraggle action logging # inspect block-source parameter-profile ips_block_default_parameter # inspect block-source parameter-profile url_block_default_parameter # inspect capture parameter-profile ips_capture_default_parameter # inspect logging parameter-profile ips_logging_default_parameter # inspect logging parameter-profile url_logging_default_parameter # inspect redirect parameter-profile av_redirect_default_parameter # inspect redirect parameter-profile ips_redirect_default_parameter # inspect redirect parameter-profile url_redirect_default_parameter # traffic-policy rule name 网段0 time-range 工作时间 action qos profile 带宽0 source-address address-set 网段0 destination-address address-set 0 source-zone Trust destination-zone Untrust rule name 网段1 time-range 工作时间 action qos profile 带宽1 source-address address-set 网段1 destination-address address-set 0 source-zone Trust destination-zone Untrust rule name 网段2 time-range 工作时间 action qos profile 带宽2 source-address address-set 网段2 destination-address address-set 0 source-zone Trust destination-zone Untrust rule name 网段3 time-range 工作时间 action qos profile 带宽3 source-address address-set 网段3 destination-address address-set 0 source-zone Trust destination-zone Untrust profile name 带宽0 bandwidth downstream guaranteed 100 bandwidth downstream maximum 15000 bandwidth upstream guaranteed 100 bandwidth upstream maximum 15000 connection-limit count per-ip 300 bandwidth upstream maximum per-ip 3000 bandwidth downstream maximum per-ip 4000 profile name 带宽1 bandwidth downstream guaranteed 100 bandwidth downstream maximum 15000 bandwidth upstream guaranteed 100 bandwidth upstream maximum 15000 connection-limit count per-ip 300 bandwidth upstream maximum per-ip 3000 bandwidth downstream maximum per-ip 4000 profile name 带宽2 bandwidth downstream guaranteed 100 bandwidth downstream maximum 15000 bandwidth upstream guaranteed 100 bandwidth upstream maximum 15000 connection-limit count per-ip 300 bandwidth upstream maximum per-ip 3000 bandwidth downstream maximum per-ip 4000 profile name 带宽3 bandwidth downstream guaranteed 100 bandwidth downstream maximum 15000 bandwidth upstream guaranteed 100 bandwidth upstream maximum 15000 connection-limit count per-ip 300 bandwidth upstream maximum per-ip 3000 bandwidth downstream maximum per-ip 4000 # ips block-source parameter-profile ips_block_default_parameter # return [xlfirewall] 主要配置
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明



