问题描述:
总部一台H3C MSR2600路由,之前一直是单宽带拨号接入外网。
内网有一台WEB服务器还有一台文件共享服务器。 各分店通过外网访问WEB服务器,用的是该服务器带内网穿透的花生壳动态域名服务。 例外一个动态域名作为MSR2600 配置给各分店连入总部的 L2TP的外网连接地址(该VPN用于连接内网的文件服务器)
当前总部新添加一根外网专线,想实现内网两个网段,主要部门跟服务器(VLAN1)走专线网络,其他部门(VLAN2)走宽带网络。同时两个网段于内网还需要互通。
VPN 和 WEB服务仍然使用动态域名接入(因为买了三年的服务)
配置了策略路由,一切都很正常,总部的两个VLAN走了不同的路由出外网。各分店的VPN也能正常接入总部,但是分店接入VPN后无法再访问VLAN1(192.168.1.0/24) 网段了,只能访问192.168.1.1网关。。。。。 感觉像是没有回来到192.168.1.0/24 的路由了。 有高手能够指点一下吗??
组网及组网描述:
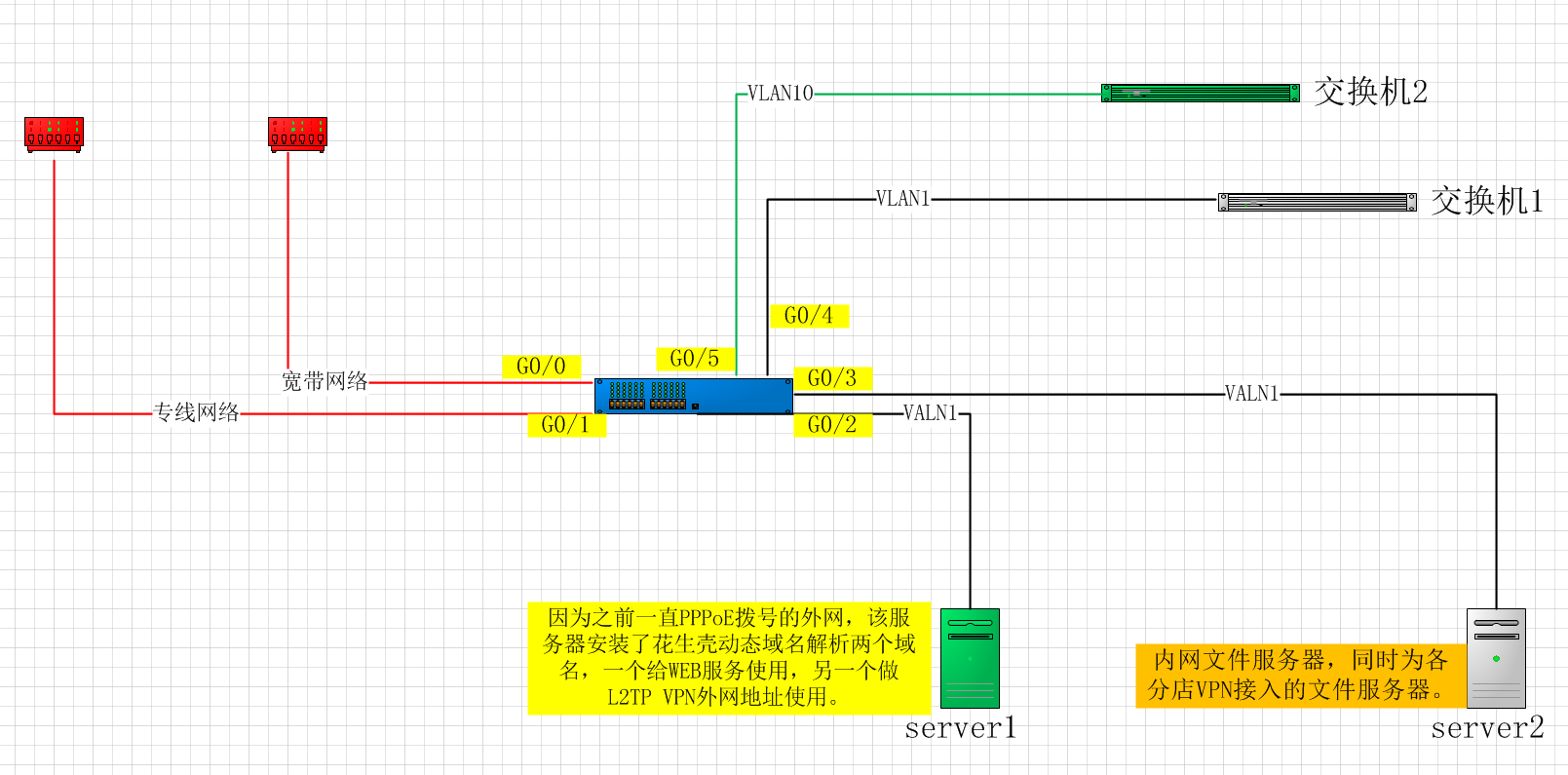
- 2021-07-05提问
- 举报
-
(0)

您好,以下参考
1、确认vpn地址没冲突
2、升级下版本吧
3、检查路由配置,是否缺少路由
参考策略路由配置
- 2021-07-05回答
- 评论(1)
- 举报
-
(0)
于当前的VPN地址没有冲突,分店VPN可以连接进来,但是只能访问到1段的网关,放问不到1段的其他IP。。。 晚些时候我把配置信息挂上。。。。先此谢谢

您好,请知:
策略路由不生效,以下是排查要点,请参考:
1、检查基础路由是否可达。
2、检查策略路由的匹配策略是否准确匹配上。
3、检查策略路由的执行动作是否生效,比如下一跳地址是否可达。
4、检查策略路由下发的位置是否准确。
5、看下路由器软件版本是否最新,可考虑升级到最新。
- 2021-07-05回答
- 评论(3)
- 举报
-
(0)
这个配置信息粘上去 好乱啊,我重发一个提问吧
当前一切的连接都很正常,包括内网两个网段的路由选路都正常,只是VPN连接后只能访问1段网关,访问不到1段其他IP。。。。 晚些时候挂上配置信息。。 谢谢
# version 5.20, Release 2516P15 # sysname H3C # l2tp enable # ip pool 3 10.3.3.1 10.3.3.50 # domain default enable system # dns resolve dns proxy enable # telnet server enable # dar p2p signature-file flash:/p2p_default.mtd # ndp enable # ntdp enable # cluster enable # port-security enable # password-recovery enable # acl number 3000 rule 0 permit ip source 192.168.1.0 0.0.0.255 acl number 3001 rule 0 permit ip source 192.168.1.0 0.0.0.255 destination 192.168.10.0 0.0.0.25 5 # vlan 1 # vlan 10 # domain newsystem authentication ppp local authorization ppp none accounting ppp local access-limit disable state active idle-cut disable self-service-url disable ip pool 3 10.3.3.1 10.3.3.50 domain system access-limit disable state active idle-cut disable self-service-url disable ip pool 2 10.9.9.100 10.9.9.199 # ike proposal 1 encryption-algorithm 3des-cbc dh group2 authentication-algorithm md5 # ike peer xsd-vpn exchange-mode aggressive proposal 1 pre-shared-key cipher $c$3$l1KjDGQDJjPLWp3yxtIyRBgGX5eqAOnYcw== id-type name remote-name b remote-address a dynamic local-name a nat traversal # ipsec transform-set lsd-vpn encapsulation-mode tunnel transform esp esp authentication-algorithm md5 esp encryption-algorithm 3des # ipsec policy-template 720896.1_t 1 connection-name lsd-vpn ike-peer lsd-vpn transform-set lsd-vpn sa duration traffic-based 1843200 sa duration time-based 3600 # ipsec policy 720896 1 isakmp template 720896.1_t # dhcp server ip-pool vlan1 extended network ip range 192.168.1.2 192.168.1.254 network mask 255.255.255.0 gateway-list 192.168.1.1 dns-list 192.168.1.1 # dhcp server ip-pool vlan10 extended network ip range 192.168.10.100 192.168.10.170 network mask 255.255.255.0 gateway-list 192.168.10.1 dns-list 221.228.255.1 # policy-based-route aaa permit node 10 if-match acl 3001 policy-based-route aaa permit node 20 if-match acl 3000 apply ip-address next-hop 67.160.90.201 # user-group system group-attribute allow-guest # local-user 777 password cipher $c$3$bxxCJKbOD67KI+Cn7TqtsFn28PKjIIx9AWqRQw== authorization-attribute level 2 service-type telnet local-user ALEX password cipher $c$3$61LfxPfIxuyvUJLtQMaWAXZhYvml9l7q9682WD8= authorization-attribute level 3 service-type ppp local-user CCYJ password cipher $c$3$abIx8ppthovc8JIQYlXas/qB3/7+H+CZrvmM0S0= authorization-attribute level 3 service-type ppp local-user SZ password cipher $c$3$1lCQrwT7T5WZQ3z29IYo5WfN49NowuczMW3DGw== authorization-attribute level 3 service-type ppp local-user Vuser3 password cipher $c$3$DfAcveTH7rZcJWbQwnWTQUvbFEfk9siH5l1w3/4= authorization-attribute level 3 service-type ppp local-user LSD-ZD password cipher $c$3$i69f4MvMAGDWAwzFyrkxfoBXXFSSKB6xYsG7vM/8MxTqjvc= authorization-attribute level 3 service-type ppp local-user admin password cipher $c$3$6WW92JYBZPfAZ9wVyEX1JGsH4ZyVxzURYnVE2Gc= authorization-attribute level 3 service-type telnet service-type web local-user tongwei password cipher $c$3$wJzVdBzWbWD059kURuDolnIYwQDAMncMlAGEhDI= authorization-attribute level 3 service-type telnet service-type web local-user wangyan password cipher $c$3$+61A8g5r11HxV3ejXUoLvhb1oRdr8PUx9Q4ywyGThkA= authorization-attribute level 3 service-type ppp local-user xiangsu password cipher $c$3$V/VpsOUKAS0c3tNSUZVVRJ7GCH4CAO629vXw2w== authorization-attribute level 3 service-type ppp # cwmp undo cwmp enable # l2tp-group 1 undo tunnel authentication allow l2tp virtual-template 0 # interface Aux0 async mode flow link-protocol ppp # interface Cellular0/0 async mode protocol link-protocol ppp tcp mss 1024 # interface Dialer10 nat outbound link-protocol ppp ppp chap user 051012705444 ppp chap password cipher $c$3$s+Lb7UDZ7oZQq1oVti80sq1hIWqOrIai1g== ppp pap local-user 051012705444 password cipher $c$3$m4tLiwxl0y3NGoZ5nhMItErfOs q3/jj6Sg== ppp ipcp dns admit-any ppp ipcp dns request mtu 1492 ip address ppp-negotiate tcp mss 1024 dialer user username dialer-group 10 dialer bundle 10 ipsec no-nat-process enable ipsec policy 720896 # interface Virtual-Template0 ppp authentication-mode pap domain system remote address pool 2 ip address 10.9.9.1 255.255.255.0 # interface Virtual-Ethernet0 # interface NULL0 # interface Vlan-interface1 ip address 192.168.1.1 255.255.255.0 tcp mss 1024 dhcp server apply ip-pool vlan1 ip policy-based-route aaa # interface Vlan-interface10 ip address 192.168.10.1 255.255.255.0 dhcp server apply ip-pool vlan10 # interface GigabitEthernet0/0 port link-mode route nat outbound nat server protocol tcp global 67.160.90.202 7777 inside 192.168.1.254 877 ip address 67.160.90.202 255.255.255.252 dns server 221.228.255.1 # interface GigabitEthernet0/1 port link-mode route nat outbound pppoe-client dial-bundle-number 10 # interface GigabitEthernet0/2 port link-mode bridge # interface GigabitEthernet0/3 port link-mode bridge # interface GigabitEthernet0/4 port link-mode bridge # interface GigabitEthernet0/5 port link-mode bridge # interface GigabitEthernet0/6 port link-mode bridge port access vlan 10 # interface GigabitEthernet0/7 port link-mode bridge port access vlan 10 # interface GigabitEthernet0/8 port link-mode bridge port access vlan 10 # interface GigabitEthernet0/9 port link-mode bridge port access vlan 10 # ip route-static 0.0.0.0 0.0.0.0 Dialer10 ip route-static 0.0.0.0 0.0.0.0 67.160.90.201 preference 70 # dhcp enable # dialer-rule 10 ip permit # nms primary monitor-interface GigabitEthernet0/0 # load xml-configuration # load tr069-configuration # user-interface tty 12 user-interface aux 0 user-interface vty 0 4 authentication-mode scheme # return <H3C>dis cu
这个配置信息粘上去 好乱啊,我重发一个提问吧
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明





于当前的VPN地址没有冲突,分店VPN可以连接进来,但是只能访问到1段的网关,放问不到1段的其他IP。。。 晚些时候我把配置信息挂上。。。。先此谢谢