F100-C-G3 IPSEC VPN能够建立但是无法通信
- 0关注
- 1收藏,1836浏览
问题描述:
TP-LINK R473 和F100-C-G3建立ipsec vpn ,隧道可以建立 ,但是无法通信,(不是所有的不能通信),R473处于非POE拨号下可以通信,但是处于PPPOE模式下获得公网地址的,不能通信。
正常可以通信的状态(NAT穿越是打开的):
-----------------------------
IPsec policy: JSAS
Sequence number: 1
Mode: Template
-----------------------------
Tunnel id: 0
Encapsulation mode: tunnel
Perfect Forward Secrecy:
Inside VPN:
Extended Sequence Numbers enable: N
Traffic Flow Confidentiality enable: N
Path MTU: 1436
Tunnel:
local address: 218.95.47.205
remote address: 111.73.113.230
Flow:
sour addr: 10.106.0.0/255.255.0.0 port: 0 protocol: ip
dest addr: 10.27.218.0/255.255.255.0 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 3940029544 (0xead81468)
Connection ID: 4294967296
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/86400
SA remaining duration (kilobytes/sec): 1843200/85868
Max received sequence-number: 0
Anti-replay check enable: Y
Anti-replay window size: 1024
UDP encapsulation used for NAT traversal: Y
Status: Active
[Outbound ESP SAs]
SPI: 3255990874 (0xc2127a5a)
Connection ID: 12884901889
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/86400
SA remaining duration (kilobytes/sec): 1843200/85868
Max sent sequence-number: 0
UDP encapsulation used for NAT traversal: Y
Status: Active
无法通信的(NAT穿越是关闭的)
-----------------------------
IPsec policy: JSAS
Sequence number: 1
Mode: Template
-----------------------------
Tunnel id: 2
Encapsulation mode: tunnel
Perfect Forward Secrecy:
Inside VPN:
Extended Sequence Numbers enable: N
Traffic Flow Confidentiality enable: N
Path MTU: 1444
Tunnel:
local address: 218.95.47.205
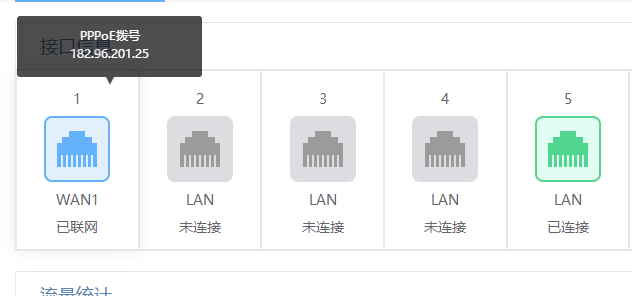
remote address: 182.96.201.25
Flow:
sour addr: 10.106.0.0/255.255.0.0 port: 0 protocol: ip
dest addr: 10.20.99.0/255.255.255.0 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 1450917191 (0x567b3d47)
Connection ID: 4294967300
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/86400
SA remaining duration (kilobytes/sec): 1843200/85868
Max received sequence-number: 0
Anti-replay check enable: Y
Anti-replay window size: 1024
UDP encapsulation used for NAT traversal: N
Status: Active
[Outbound ESP SAs]
SPI: 3373570391 (0xc9149957)
Connection ID: 4294967301
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/86400
SA remaining duration (kilobytes/sec): 1843200/85868
Max sent sequence-number: 0
UDP encapsulation used for NAT traversal: N
Status: Active
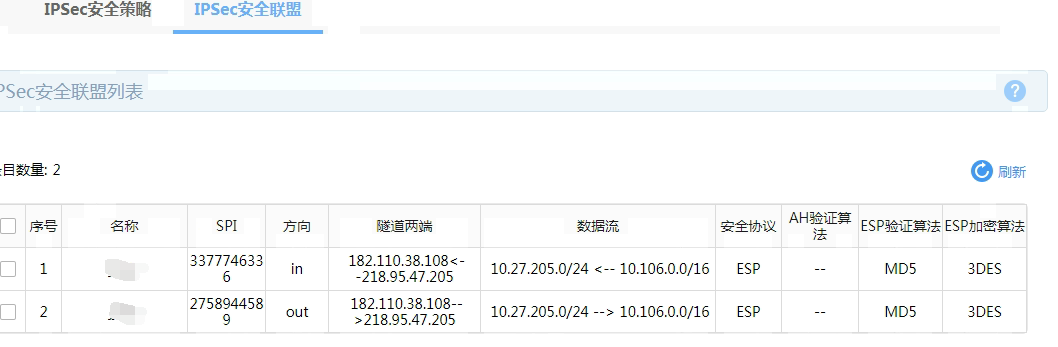
NAT全局 已经剔除感兴趣流量的NAT
nat global-policy
rule name ipsec
source-ip 总部
destination-ip 门店
source-zone Local
source-zone Trust
destination-zone Untrust
action snat no-nat
object-group ip address 门店
security-zone Untrust
0 network subnet 10.27.0.0 255.255.0.0
10 network subnet 10.20.99.0 255.255.255.0
#
object-group ip address 总部
security-zone Trust
0 network subnet 10.106.0.0 255.255.0.0
组网及组网描述:
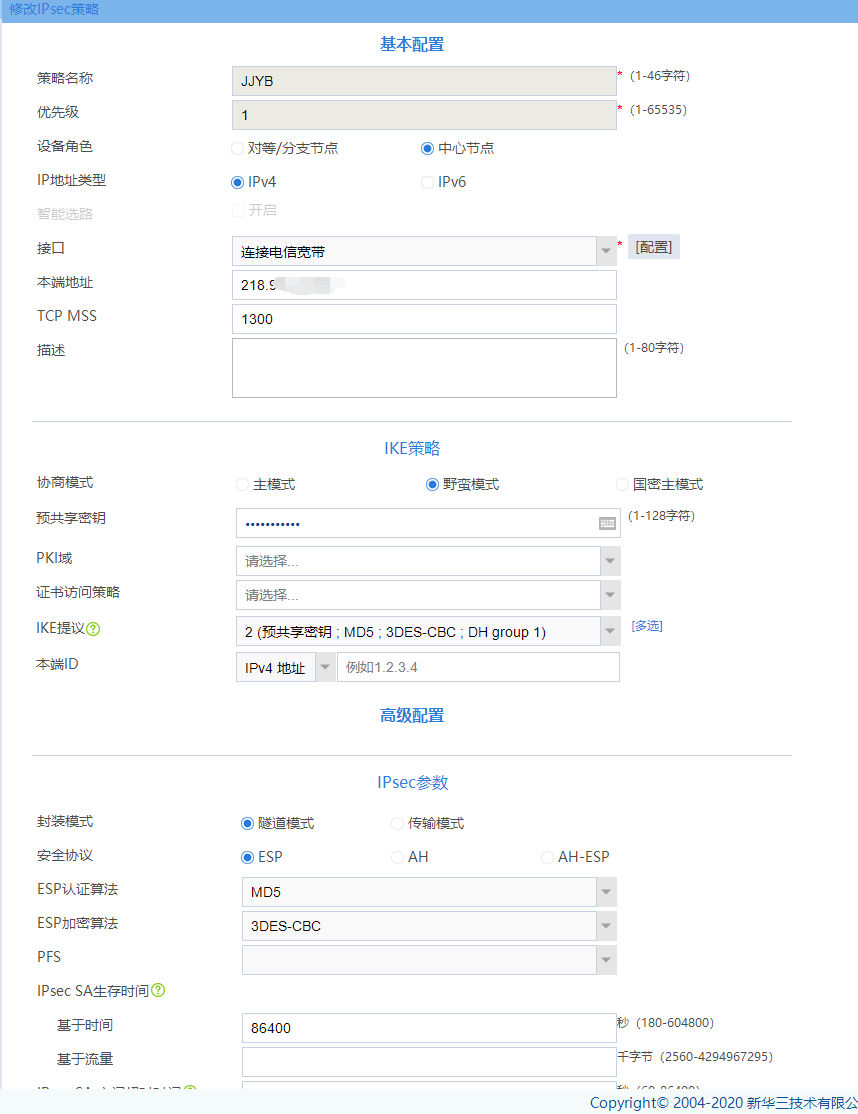
F100-C-G3 处于中心,采用 IPSEC 中心模式, R473处于门店 采用IPSEC 发起模式,无法单独选择谁开启NAT穿越 谁不开启。
- 2021-08-12提问
- 举报
-
(0)
最佳答案

IPSEC VPN故障排查:
1、检查公网地址的连通性
2、检查ipsec acl是否配置正确(两端ACL以互为镜像的方式配置)
3、检查ike keychain/ike profile 协商参数配置是否正确(工作模式、keychain、identity、本端/对端隧道地址或隧道名称、NAT穿越功能v7自适应)
4、检查ipsec proposal(v5平台) /ipsec transform-set(v7平台)参数两端是否一致(封装模式、安全协议、验证算法、加密算法)
5、检查设备是否创建ipsec策略,并加载协商参数(acl、ike profile 、ipsec transform-set、对端隧道IP)
6、检查ipsec策略是否应用在正确的接口上
IPSEC排查命令:
1、disp ipsec policy
2、disp acl
3、dis cu conf ike-profile
4、dis cu conf ike-keychain
5、display ike proposal
6、display ipsec transform-set
7、disp ike sa (verbose)
8、disp ipsec sa
9、reset ipsec sa
10、reset ike sa
- 2021-08-12回答
- 评论(0)
- 举报
-
(0)


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明


