SecPath F100-C-G2 联网配置失败
- 0关注
- 1收藏,2380浏览
问题描述:
我采购了 防火墙 F100-C-G2,是由参考官网文档配置 chm,但是配置失败,防火墙不能联网,不能dhcp。也致电过H3C售后,给我发了份 Word文档,都是配置失败,麻烦检查一下这文档中是否有缺漏的步骤,谢谢。
前几天发帖子,给我的回复的一些命令,我重置过防火墙,对着敲,还是没效果,而且那位技术给的命令缺少了dhcp。
要求不多,能上网就行
组网及组网描述:
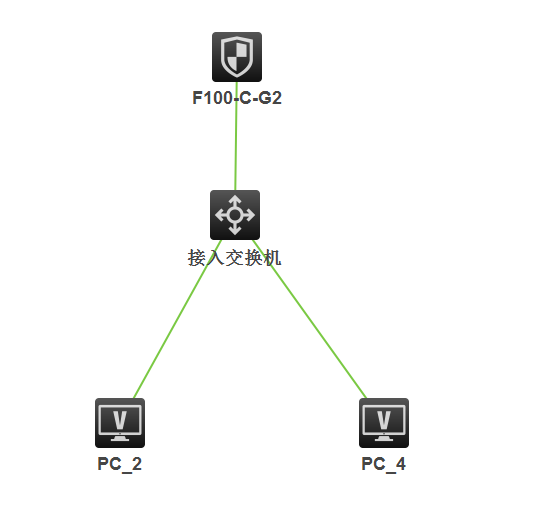
- 2018-06-25提问
- 举报
-
(0)
最佳答案

1.1 配置外网接口
将1/0/1设置为外网接口并设置IP地址。
[H3C]interface GigabitEthernet 1/0/1
[H3C-GigabitEthernet1/0/1]ip address 198.76.28.30 255.255.255.252
[H3C-GigabitEthernet1/0/1]quit
1.2 配置内网接口
配置内网接口为1/0/2接口并指定IP地址为192.168.10.1。
[H3C]interface GigabitEthernet 1/0/2
[H3C-GigabitEthernet1/0/2] ip address 192.168.10.1 255.255.255.0
[H3C-GigabitEthernet1/0/2] quit
1.3 配置NAT地址转换
进入1/0/1接口配置NAT动态地址转换。
[H3C]interface GigabitEthernet 1/0/1
[H3C-GigabitEthernet1/0/1]nat outbound
[H3C-GigabitEthernet1/0/1]quit
1.4 配置到外网网关的静态路由
配置默认路由到外网网关。
[H3C]ip route-static 0.0.0.0 0 198.76.28.29
1.5 配置外网接口加入Untrust安全区域
将1/0/1外网接口加入untrust区域。
[H3C]security-zone name untrust
[H3C-security-zone-Untrust]import interface GigabitEthernet 1/0/1
[H3C-security-zone-Untrust]quit
1.6 配置内网接口加入trust安全区域
将1/0/2内网接口加入trust区域。
[H3C]security-zone name trust
[H3C-security-zone-trust]import interface GigabitEthernet 1/0/2
[H3C-security-zone-trust]quit
1.7 配置安全策略将trust到Untrust域内网数据放通
创建高级访问控制列表匹配源地址为192.168.10.0网段。
[H3C]acl advanced 3000
[H3C-acl-ipv4-adv-3000]rule permit ip source 192.168.10.0 0.0.0.255
在域间策略中调用配置好的访问控制列表3000。
[H3C]zone-pair security source trust destination untrust
[H3C-zone-pair-security-Trust-Untrust]packet-filter 3000
[H3C-zone-pair-security-Trust-Untrust]quit
1.8 配置安全策略将trust到local域、local到trust域数据全放通策略
创建高级访问控制列表匹配所有数据
[H3C]acl advanced 3001
[H3C-acl-ipv4-adv-3001]rule permit ip source any
在源域为trust目的域为local的域间策略下调用访问控制列表3001。
[H3C]zone-pair security source trust destination local
[H3C-zone-pair-security-Trust-Local]packet-filter 3001
[H3C-zone-pair-security-Trust- Local]quit
在源域为local目的域为trust的域间策略下调用访问控制列表3001。
[H3C]zone-pair security source local destination trust
[H3C-zone-pair-security-Local -Trust]packet-filter 3001
[H3C-zone-pair-security-Local -Trust]quit
1.9 配置DHCP服务
开启DHCP服务并指定动态下发的地址以及网关等参数。
[H3C]dhcp enable
[H3C]dhcp server ip-pool 1
[H3C-dhcp-pool-1]network 192.168.10.0
[H3C-dhcp-pool-1]gateway-list 192.168.10.1
[H3C-dhcp-pool-1]dns-list 114.114.114.114 8.8.8.8
[H3C-dhcp-pool-1]quit
注:DNS服务器地址优先设置当地运营商提供的DNS服务器地址,如果没有提供可以设置114.114.114.114或8.8.8.8等DNS服务器地址。
1.10 保存配置
[H3C]quit
- 2018-06-25回答
- 评论(2)
- 举报
-
(0)

#
version 7.1.064, Release 9510P03
#
sysname H3C
#
context Admin id 1
#
ip vpn-instance management
route-distinguisher 1000000000:1
vpn-target 1000000000:1 import-extcommunity
vpn-target 1000000000:1 export-extcommunity
#
irf mac-address persistent timer
irf auto-update enable
undo irf link-delay
irf member 1 priority 1
#
dhcp enable
#
password-recovery enable
#
vlan 1
#
object-group ip address neiwang
0 network subnet 192.168.2.0 255.255.255.0
#
dhcp server ip-pool 1
gateway-list 192.168.2.1
network 192.168.2.0 mask 255.255.255.0
dns-list 114.114.114.114
#
interface NULL0
#
interface GigabitEthernet1/0/0
port link-mode route
combo enable fiber
ip binding vpn-instance management
ip address 192.168.0.1 255.255.255.0
#
interface GigabitEthernet1/0/1
port link-mode route
combo enable fiber
#
interface GigabitEthernet1/0/2
port link-mode route
ip binding vpn-instance management
ip address 172.18.8.210 255.255.255.0
nat outbound
#
interface GigabitEthernet1/0/3
port link-mode route
ip address 192.168.2.1 255.255.255.0
#
interface GigabitEthernet1/0/4
port link-mode route
#
interface GigabitEthernet1/0/5
port link-mode route
#
interface GigabitEthernet1/0/6
port link-mode route
#
interface GigabitEthernet1/0/7
port link-mode route
#
interface GigabitEthernet1/0/8
port link-mode route
#
interface GigabitEthernet1/0/9
port link-mode route
#
interface GigabitEthernet1/0/10
port link-mode route
ip address 192.168.4.1 255.255.255.0
#
interface GigabitEthernet1/0/11
port link-mode route
#
object-policy ip Trust-Untrust
rule 0 pass source-ip neiwang
#
security-zone name Local
#
security-zone name Trust
import interface GigabitEthernet1/0/3
import interface GigabitEthernet1/0/10
#
security-zone name DMZ
#
security-zone name Untrust
#
security-zone name Management
import interface GigabitEthernet1/0/0
import interface GigabitEthernet1/0/2
#
zone-pair security source Local destination Trust
packet-filter 3333
packet-filter 3001
#
zone-pair security source Trust destination Local
packet-filter 3333
packet-filter 3001
#
zone-pair security source Trust destination Untrust
object-policy apply ip Trust-Untrust
packet-filter 3000
#
scheduler logfile size 16
#
line class aux
user-role network-operator
#
line class console
user-role network-admin
#
line class vty
user-role network-operator
#
line aux 0
user-role network-admin
#
line con 0
authentication-mode scheme
user-role network-admin
#
line vty 0 63
authentication-mode scheme
user-role network-admin
#
ip route-static 0.0.0.0 0 172.18.8.1
#
ssh server enable
#
acl advanced 3000
rule 0 permit ip source 192.168.2.0 0.0.0.255
#
acl advanced 3001
rule 0 permit ip
#
acl advanced 3333
rule 0 permit ip
#
domain system
#
aaa session-limit ftp 16
aaa session-limit telnet 16
aaa session-limit ssh 16
domain default enable system
#
role name level-0
description Predefined level-0 role
#
role name level-1
description Predefined level-1 role
#
role name level-2
description Predefined level-2 role
#
role name level-3
description Predefined level-3 role
#
role name level-4
description Predefined level-4 role
#
role name level-5
description Predefined level-5 role
#
role name level-6
description Predefined level-6 role
#
role name level-7
description Predefined level-7 role
#
role name level-8
description Predefined level-8 role
#
role name level-9
description Predefined level-9 role
#
role name level-10
description Predefined level-10 role
#
role name level-11
description Predefined level-11 role
#
role name level-12
description Predefined level-12 role
#
role name level-13
description Predefined level-13 role
#
role name level-14
description Predefined level-14 role
#
user-group system
#
local-user admin class manage
password hash $h$6$UbIhNnPevyKUwfpm$LqR3+yg1IjNct39MkOR0H0iQXLkYB3jMqM4vbAeoXOhbabIIFnjJPEGR00YiYA1Sz4LiY3FmEdru2fOLMb1shQ==
service-type ssh terminal https
authorization-attribute user-role level-3
authorization-attribute user-role network-admin
authorization-attribute user-role network-operator
#
local-user root class manage
password hash $h$6$kJ1CaxuXcuqqahpX$9ePAGR/a2B/0shEZetBrVh3nPfaOTGlPVqnXteZZMzn+QJFWYysiMk93kEbRdhqCFmnjL7lT0pckDWkbWkmYow==
service-type telnet terminal http https
authorization-attribute user-role level-3
authorization-attribute user-role network-admin
authorization-attribute user-role network-operator
#
ip http enable
ip https enable
#
return
- 2018-06-25回答
- 评论(0)
- 举报
-
(0)
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明


上层路由器的分配的IP为 172.18.8.210/24 网关是 172.18.8.1 dns为 192.168.1.2