问题描述:
如何在ospfv3中宣告网段,或者说如何将某接口加入到ospfv3的某个area里?
组网及组网描述:
- 2021-08-22提问
- 举报
-
(0)
最佳答案


[RouterA] interface gigabitethernet 1/0/1
[RouterA-GigabitEthernet1/0/1] ospfv3 1 area 1
[RouterA-GigabitEthernet1/0/1] quit
- 2021-08-22回答
- 评论(1)
- 举报
-
(0)
有类似ospf ipv4的方式在进程里宣告方式吗?

所有的路由器都运行OSPFv3,整个自治系统划分为3个区域。其中Router B和Router C作为ABR来转发区域之间的路由。
· 要求将Area 1配置为NSSA区域,同时将Router A配置为ASBR引入外部路由(静态路由),且路由信息可正确的在AS内传播。
2. 组网图
图1-2 OSPFv3 NSSA区域配置组网图

3. 配置步骤
(1) 配置各接口的IPv6地址(略)
(2) 配置OSPFv3基本功能(同前例1.13.1 )
(3) 配置Area 1为NSSA区域
# 配置Router A的NSSA区域。
[RouterA] ospfv3
[RouterA-ospfv3-1] area 1
[RouterA-ospfv3-1-area-0.0.0.1] nssa
[RouterA-ospfv3-1-area-0.0.0.1] quit
[RouterA-ospfv3-1] quit
# 配置Router B的NSSA区域。
[RouterB] ospfv3
[RouterB-ospfv3-1] area 1
[RouterB-ospfv3-1-area-0.0.0.1] nssa
[RouterB-ospfv3-1-area-0.0.0.1] quit
[RouterB-ospfv3-1] quit
# 查看Router A的OSPFv3路由表信息。
[RouterA] display ospfv3 1 routing
- 2021-08-22回答
- 评论(0)
- 举报
-
(0)

在接口中使能OSPFV3和区域就可以了。
以下是配置案例,请参考:
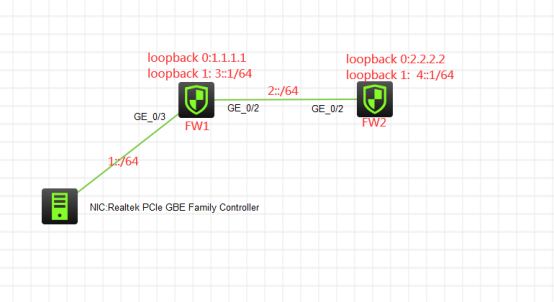
组网说明:
本案例采用H3C HCL模拟器的F1060防火墙来模拟IPV6之OSPFV3的典型组网配置,全网均采用IPV6子网,要求通过OSPFV3技术实现全网互通。
配置步骤
1、按照网络拓扑图正确配置IPV6地址。
2、全网运行OSPFV3路由协议
配置关键点
FW1:
<FW1>sys
System View: return to User View with Ctrl+Z.
[FW1]acl ipv6 basic 2001
[FW1-acl-ipv6-basic-2001]rule 0 permit source any
[FW1-acl-ipv6-basic-2001]quit
[FW1]
[FW1]zone-pair security source trust destination untrust
[FW1-zone-pair-security-Trust-Untrust]packet-filter ipv6 2001
[FW1-zone-pair-security-Trust-Untrust]quit
[FW1]
[FW1]zone-pair security source untrust destination trust
[FW1-zone-pair-security-Untrust-Trust]packet-filter ipv6 2001
[FW1-zone-pair-security-Untrust-Trust]quit
[FW1]
[FW1]zone-pair security source trust destination local
[FW1-zone-pair-security-Trust-Local]packet-filter ipv6 2001
[FW1-zone-pair-security-Trust-Local]quit
[FW1]
[FW1]zone-pair security source local destination trust
[FW1-zone-pair-security-Local-Trust]packet-filter ipv6 2001
[FW1-zone-pair-security-Local-Trust]quit
[FW1]
[FW1]zone-pair security source untrust destination local
[FW1-zone-pair-security-Untrust-Local]packet-filter ipv6 2001
[FW1-zone-pair-security-Untrust-Local]quit
[FW1]
[FW1]zone-pair security source local destination untrust
[FW1-zone-pair-security-Local-Untrust]packet-filter ipv6 2001
[FW1-zone-pair-security-Local-Untrust]quit
[FW1]
[FW1]zone-pair security source trust destination trust
[FW1-zone-pair-security-Trust-Trust]packet-filter ipv6 2001
[FW1-zone-pair-security-Trust-Trust]quit
[FW1]
[FW1]zone-pair security source untrust destination untrust
[FW1-zone-pair-security-Untrust-Untrust]packet-filter ipv6 2001
[FW1-zone-pair-security-Untrust-Untrust]quit
[FW1]ospfv3 1
[FW1-ospfv3-1]router-id 1.1.1.1
[FW1-ospfv3-1]import-route direct
[FW1-ospfv3-1]quit
[FW1]int loopback 0
[FW1-LoopBack0]ip address 1.1.1.1 32
[FW1-LoopBack0]quit
[FW1]int loopback 1
[FW1-LoopBack1]ipv6 address 3::1 63
[FW1-LoopBack1]ospfv3 1 area 0
[FW1-LoopBack1]quit
[FW1]int gi 1/0/3
[FW1-GigabitEthernet1/0/3]ipv6 address 1::1 64
[FW1-GigabitEthernet1/0/3]ospfv3 1 area 0
[FW1-GigabitEthernet1/0/3]quit
[FW1]int gi 1/0/2
[FW1-GigabitEthernet1/0/2]des <connect to FW2>
[FW1-GigabitEthernet1/0/2]ipv6 address 2::1 64
[FW1-GigabitEthernet1/0/2]ospfv3 1 area 0
[FW1-GigabitEthernet1/0/2]quit
[FW1]security-zone name Trust
[FW1-security-zone-Trust]import interface GigabitEthernet 1/0/3
[FW1-security-zone-Trust]quit
[FW1]security-zone name Untrust
[FW1-security-zone-Untrust]import interface LoopBack 0
[FW1-security-zone-Untrust]import interface LoopBack 1
[FW1-security-zone-Untrust]import interface GigabitEthernet 1/0/2
[FW1-security-zone-Untrust]quit
FW2:
<H3C>sys
System View: return to User View with Ctrl+Z.
[H3C]sysname FW2
[FW2]acl ipv6 basic 2001
[FW2-acl-ipv6-basic-2001]rule 0 permit source any
[FW2-acl-ipv6-basic-2001]quit
[FW2]
[FW2]zone-pair security source trust destination untrust
[FW2-zone-pair-security-Trust-Untrust]packet-filter ipv6 2001
[FW2-zone-pair-security-Trust-Untrust]quit
[FW2]
[FW2]zone-pair security source untrust destination trust
[FW2-zone-pair-security-Untrust-Trust]packet-filter ipv6 2001
[FW2-zone-pair-security-Untrust-Trust]quit
[FW2]
[FW2]zone-pair security source trust destination local
[FW2-zone-pair-security-Trust-Local]packet-filter ipv6 2001
[FW2-zone-pair-security-Trust-Local]quit
[FW2]
[FW2]zone-pair security source local destination trust
[FW2-zone-pair-security-Local-Trust]packet-filter ipv6 2001
[FW2-zone-pair-security-Local-Trust]quit
[FW2]
[FW2]zone-pair security source untrust destination local
[FW2-zone-pair-security-Untrust-Local]packet-filter ipv6 2001
[FW2-zone-pair-security-Untrust-Local]quit
[FW2]
[FW2]zone-pair security source local destination untrust
[FW2-zone-pair-security-Local-Untrust]packet-filter ipv6 2001
[FW2-zone-pair-security-Local-Untrust]quit
[FW2]
[FW2]zone-pair security source trust destination trust
[FW2-zone-pair-security-Trust-Trust]packet-filter ipv6 2001
[FW2-zone-pair-security-Trust-Trust]quit
[FW2]
[FW2]zone-pair security source untrust destination untrust
[FW2-zone-pair-security-Untrust-Untrust]packet-filter ipv6 2001
[FW2-zone-pair-security-Untrust-Untrust]quit
[FW2]ospfv3 1
[FW2-ospfv3-1]router-id 2.2.2.2
[FW2-ospfv3-1]import-route direct
[FW2-ospfv3-1]quit
[FW2]int loopback 0
[FW2-LoopBack0]ip address 2.2.2.2 32
[FW2-LoopBack0]quit
[FW2]int loopback 1
[FW2-LoopBack1]ipv6 address 4::1 64
[FW2-LoopBack1]ospfv3 1 area 0
[FW2-LoopBack1]quit
[FW2]int gi 1/0/2
[FW2-GigabitEthernet1/0/2]des <connect to FW1>
[FW2-GigabitEthernet1/0/2]ipv6 address 2::2 64
[FW2-GigabitEthernet1/0/2]ospfv3 1 area 0
[FW2-GigabitEthernet1/0/2]quit
[FW2]security-zone name Untrust
[FW2-security-zone-Untrust]import interface LoopBack 0
[FW2-security-zone-Untrust]import interface LoopBack 1
[FW2-security-zone-Untrust]import interface GigabitEthernet 1/0/2
[FW2-security-zone-Untrust]quit
PC填写IPV6地址:

PC可以PING通FW1、FW2的loopback 1:

FW1可以PING通PC及FW2的loopback1:
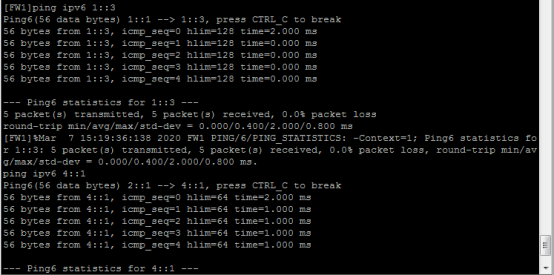
FW2可以PING通PC及FW1的loopback1:

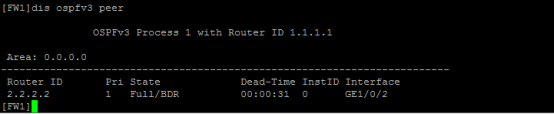
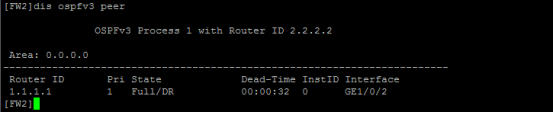
分别查看FW1、FW2的OSPFv3邻居信息:
- 2021-08-22回答
- 评论(0)
- 举报
-
(0)
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明



有类似ospf ipv4的方式在进程里宣告方式吗?