问题描述:
总部与分支间gre ipsec传输数据 ,总部、分支用户均可正常访问外网,总部与分支ike\ipsec状态均正常
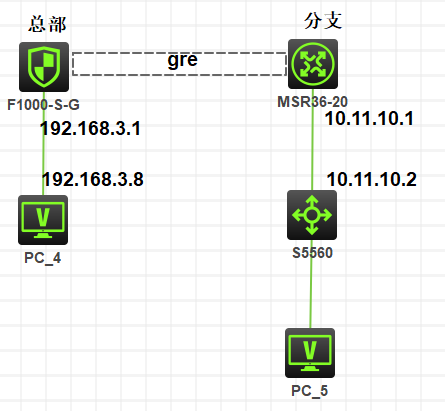
问题:用户192.168.3.0/24 可ping通10.11.10.1,但无法ping 10.11.10.2及设备5560下的VLAN用户
总部:
ersion 5.20, Release 3727
acl number 3036
rule 11 permit ip source 192.168.0.0 0.0.0.255 destination 172.16.20.0 0.0.0.255
rule 21 permit ip source 172.16.3.0 0.0.0.255 destination 172.16.20.0 0.0.0.255
rule 31 permit ip source 192.168.20.0 0.0.0.255 destination 172.16.20.0 0.0.0.255
acl number 3038
rule 10 permit ip source 118.114.24.10 0 destination 117.172.5.21 0
acl number 3100 name NAT
rule 67 deny ip source 192.168.0.0 0.0.0.255 destination 172.16.20.0 0.0.0.255
rule 68 deny ip source 192.168.20.0 0.0.0.255 destination 172.16.20.0 0.0.0.255
rule 69 deny ip source 172.16.3.0 0.0.0.255 destination 172.16.20.0 0.0.0.255
rule 100 permit ip source 172.16.0.0 0.0.255.255
rule 500 permit ip source 192.168.0.0 0.0.0.255
vlan 1
#
vlan 10 to 16
#
domain system
authentication ppp local
access-limit disable
state active
idle-cut disable
self-service-url disable
ip pool 1 10.0.10.2 10.0.10.254
#
pki entity en
common-name http-server
#
ike proposal 1
encryption-algorithm 3des-cbc
dh group2
authentication-algorithm md5
#
ike dpd dpd0001
time-out 30
#
ike peer shenxs0
pre-shared-key cipher $c$3$7mSaRMNXZHXzXHE/Vz5kxr6V0rBBEBYplR4s
remote-address 117.172.5.21
local-address 118.114.24.10
nat traversal
ipsec transform-set cdblzb
encapsulation-mode tunnel
transform esp
esp authentication-algorithm md5
esp encryption-algorithm 3des
#
ipsec policy 1048576 38 isakmp
security acl 3038
pfs dh-group2
ike-peer shenxs0
transform-set cdblzb
#
ssl server-policy access-policy
pki-domain default
#
interface Virtual-Template1
ppp authentication-mode chap domain system
remote address pool 1
ip address 10.10.0.1 255.255.255.0
#
interface Vlan-interface1
ip address 192.168.0.254 255.255.255.0
#
interface Vlan-interface16
ip address 192.168.3.1 255.255.255.0
#
interface GigabitEthernet0/0
port link-mode route
nat outbound 3100
ip address 118.114.24.10 255.255.255.0
tcp mss 1024
interface GigabitEthernet0/1
port link-mode bridge
port link-type trunk
port trunk permit vlan all
#
interface GigabitEthernet0/2
port link-mode bridge
port link-type trunk
port trunk permit vlan all
#
interface Tunnel2001
ip address 10.11.11.1 255.255.255.128
source 118.114.24.10
destination 117.172.5.21
keepalive 10 3
#
vd Root id 1
#
zone name Management id 0
priority 100
zone name Local id 1
priority 100
zone name Trust id 2
priority 50
import interface Vlan-interface1
import interface Vlan-interface10
import interface Vlan-interface11
import interface Vlan-interface12
import interface Vlan-interface13
import interface Vlan-interface14
import interface Vlan-interface15
import interface Vlan-interface16
import interface Virtual-Template1
zone name DMZ id 3
priority 45
import interface GigabitEthernet0/4
import interface GigabitEthernet0/5
import interface GigabitEthernet0/6
import interface GigabitEthernet0/7
import interface GigabitEthernet0/8
import interface GigabitEthernet0/9
zone name Untrust id 4
priority 5
import interface GigabitEthernet0/0
import interface Tunnel2001
#
connection-limit apply policy 0
#
mac-address blackhole 5ca7-21ad-bdf0 vlan 1
#
ssl-vpn server-policy access-policy port 2020
ssl-vpn enable
#
ip route-static 0.0.0.0 0.0.0.0 GigabitEthernet0/0 118.114.24.1
ip route-static 10.11.10.0 255.255.255.0 Tunnel2001
#
分支3620 :
version 7.1.064, Release 0821P13
#
#
interface GigabitEthernet0/0
port link-mode route
description Double_Line1
#
interface GigabitEthernet0/1
port link-mode route
description LAN-interface
combo enable copper
ip address 10.11.10.1 255.255.255.0
undo dhcp select server
#
interface GigabitEthernet0/2
port link-mode route
description Double_Line2
combo enable copper
ip address 117.172.5.21 255.255.255.0
dns server 183.221.253.100
tcp mss 1280
nat outbound
attack-defense apply policy AtkInterface4
ipsec apply policy shenxs0
#
#
interface Tunnel2001 mode gre
ip address 10.11.11.2 255.255.255.128
source 117.172.5.21
destination 118.114.24.10
keepalive 10 3
#
security-zone name Untrust
import interface GigabitEthernet0/0
import interface GigabitEthernet0/2
#
#
#
ip route-static 0.0.0.0 0 117.172.5.1 preference 100
ip route-static 10.0.0.0 24 10.11.10.2 preference 100
ip route-static 10.0.20.0 24 10.11.10.2 preference 100
ip route-static 172.16.20.0 24 10.11.10.2 preference 100
ip route-static 192.168.3.0 24 Tunnel2001
#
#
acl advanced 3020
rule 11 permit ip source 172.16.20.0 0.0.0.255 destination 192.168.0.0 0.0.0.255
rule 21 permit ip source 172.16.20.0 0.0.0.255 destination 192.168.20.0 0.0.0.255
#
acl advanced 3021
#
acl number 3030
rule 10 permit ip source 117.172.5.21 0 destination 118.114.24.10 0
#
acl number 3031
#
acl advanced 3100
rule 11 deny ip source 172.16.20.0 0.0.0.255 destination 192.168.0.0 0.0.0.255
rule 21 deny ip source 172.16.20.0 0.0.0.255 destination 192.168.20.0 0.0.0.255
rule 100 permit ip
#
#
#
#
ipsec transform-set shenxianshu
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
pfs dh-group2
#
#
ipsec policy shenxs0 65535 isakmp
transform-set shenxianshu
security acl 3030
local-address 117.172.5.21
remote-address 118.114.24.10
ike-profile shenxs0
#
#
ike profile shenxs0
keychain shenxs0
local-identity address 117.172.5.21
match remote identity address 118.114.24.10 255.255.255.255
proposal 65535
#
ike proposal 65535
encryption-algorithm 3des-cbc
dh group2
authentication-algorithm md5
#
#
ike keychain shenxs0
pre-shared-key address 118.114.24.10 255.255.255.255 key cipher $c$3$72b+gB2TDY/k1HSpvM76ucK0pAFpTghYgnWc
分支5560:
version 7.1.070, Release 6323P01
#
vlan 1
#
vlan 2001 to 2003
#
stp global enable
#
interface NULL0
#
interface Vlan-interface1
undo dhcp select server
dhcp client identifier ascii 98f181f44808-VLAN0001
#
interface Vlan-interface2001
ip address 172.16.20.1 255.255.255.0
undo dhcp select server
#
interface Vlan-interface2002
ip address 10.0.0.1 255.255.255.0
packet-filter 3020 inbound
undo dhcp select server
#
interface Vlan-interface2003
ip address 10.0.20.1 255.255.255.0
packet-filter 3021 inbound
undo dhcp select server
#
interface GigabitEthernet1/0/22
port link-mode route
combo enable auto
ip address 10.11.10.2 255.255.255.0
#
line vty 5 63
user-role network-operator
#
ip route-static 0.0.0.0 0 10.11.10.1 preference 100
ip route-static 192.168.3.0 24 10.11.10.1
#
#
acl number 3020
rule 9 permit ip source 10.0.0.2 0 destination 172.16.20.0 0.0.0.255
rule 10 permit ip source 10.0.0.3 0 destination 172.16.20.0 0.0.0.255
rule 11 deny ip source 10.0.0.0 0.0.0.255 destination 172.16.20.0 0.0.0.255
rule 21 deny ip source 10.0.0.0 0.0.0.255 destination 10.0.20.0 0.0.0.255
rule 100 permit ip
#
acl number 3021
rule 11 deny ip source 10.0.20.0 0.0.0.255 destination 10.0.0.0 0.0.0.255
rule 21 deny ip source 10.0.20.0 0.0.0.255 destination 172.16.20.0 0.0.0.255
rule 100 permit ip
#
#
组网及组网描述:
- 2021-09-04提问
- 举报
-
(0)
最佳答案

IPSEC VPN故障排查:
1、检查公网地址的连通性
2、检查ipsec acl是否配置正确(两端ACL以互为镜像的方式配置)
3、检查ike keychain/ike profile 协商参数配置是否正确(工作模式、keychain、identity、本端/对端隧道地址或隧道名称、NAT穿越功能v7自适应)
4、检查ipsec proposal(v5平台) /ipsec transform-set(v7平台)参数两端是否一致(封装模式、安全协议、验证算法、加密算法)
5、检查设备是否创建ipsec策略,并加载协商参数(acl、ike profile 、ipsec transform-set、对端隧道IP)
6、检查ipsec策略是否应用在正确的接口上
IPSEC排查命令:
1、disp ipsec policy
2、disp acl
3、dis cu conf ike-profile
4、dis cu conf ike-keychain
5、display ike proposal
6、display ipsec transform-set
7、disp ike sa (verbose)
8、disp ipsec sa
9、reset ipsec sa
10、reset ike sa
- 2021-09-06回答
- 评论(0)
- 举报
-
(0)


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明




暂无评论