问题描述:
H3C SecPath F100-M-G
Comware Software, Version 5.20, Release 5139
防火墙上接了两条数字专线,是否可以实现主备,异常时自动切换
组网及组网描述:
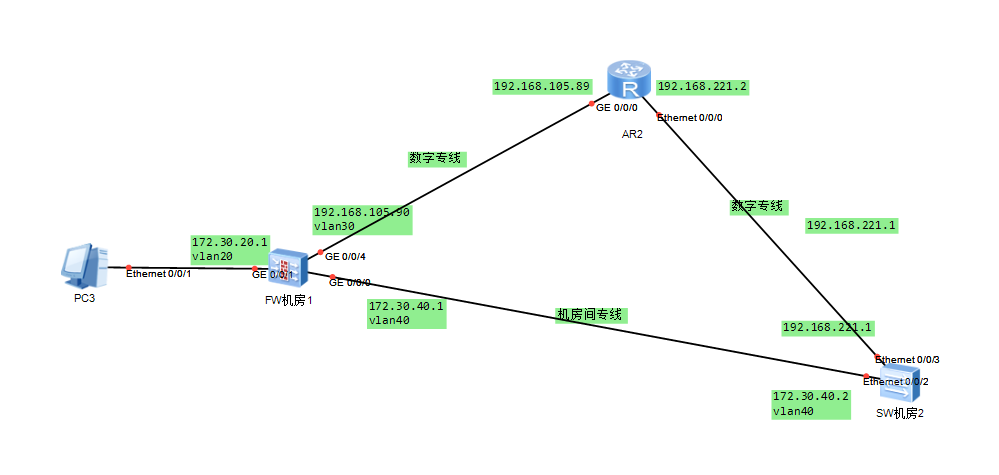
- 2021-09-16提问
- 举报
-
(0)
最佳答案

可以做下nqa track,
然后指定下源接口地址去探测对端。这样如果探测失败了就会进行切换。
可以参考下这个案例:
如下图所示,在防火墙1/0/4和1/0/5两个接口上配置nat outbound转换源地址,使用easy-ip方式直接转为接口地址。其中将1/0/4作为主接口, 使用默认优先级60并关联track联动探测下一跳1.1.1.2是否可达,在不可达的情况下切换到优先级为80的1/0/5备用出口。在路由器上配置回程路由,并创建Loopback:3.3.3.1作为目的地地址。

问题描述
目的是,当主接口1/0/4物理状态down时,切换到备接口1/0/5上,且配置的全局NAT能保证nat转换的源地址是本接口的地址(同理也可以配置不同的地址池,保转换后的源地址在不同运营商链路中是可以被识别的)。
过程分析
关键配置:
- 路由:通过优先级配置一主一备两条默认路由。
路由,优先级默认是60,越小越优先:
ip route-static 0.0.0.0 0 1.1.1.2 track 1
ip route-static 0.0.0.0 0 2.2.2.2 preference 80
2. 配置nqa探测,当探测连续失败5次时通知设备的其他模块。
nqa探测:
#
nqa entry admin test
type icmp-echo
destination ip 1.1.1.2
next-hop ip 1.1.1.2
reaction 1 checked-element probe-fail threshold-type consecutive 5 action-type trigger-only
#
track 1 nqa entry admin test reaction 1
3. 配置全局nat,这里的关键点在出接口的安全域,当目的安全域匹配电信出接口1/0/4时,源地址转换成1/0/4的接口地址(地址池同理);当目的安全域匹配移动出接口1/0/5时,源地址转换成1/0/5的接口地址(地址池同理)
全局nat配置:
#
nat global-policy
rule name test1
destination-zone dianxin
action snat easy-ip
rule name test2
destination-zone yidong
action snat easy-ip
4. 安全域:注意,一定要将两个出接口加入不同的安全域。
安全域
#
security-zone name dianxin
import interface GigabitEthernet1/0/4
#
security-zone name yidong
import interface GigabitEthernet1/0/5
解决方法
结论:
1. 查看会话确认达到目的:
| 断开前: <H3C>dis session table ipv4 source-ip 192.168.7.2 verbose Slot 1: Initiator: Source IP/port: 192.168.7.2/1 Destination IP/port: 3.3.3.1/2048 DS-Lite tunnel peer: - VPN instance/VLAN ID/Inline ID: -/-/- Protocol: ICMP(1) Inbound interface: GigabitEthernet1/0/1 Source security zone: pc Responder: Source IP/port: 3.3.3.1/4 Destination IP/port: 1.1.1.1/0 DS-Lite tunnel peer: - VPN instance/VLAN ID/Inline ID: -/-/- Protocol: ICMP(1) Inbound interface: GigabitEthernet1/0/4 Source security zone: dianxing State: ICMP_REPLY Application: ICMP Rule ID: 18 Rule name: all Start time: 2021-04-25 12:43:48 TTL: 14s Initiator->Responder: 0 packets 0 bytes Responder->Initiator: 0 packets 0 bytes 断开1/0/4口后: Initiator: Source IP/port: 192.168.7.2/1 Destination IP/port: 3.3.3.1/2048 DS-Lite tunnel peer: - VPN instance/VLAN ID/Inline ID: -/-/- Protocol: ICMP(1) Inbound interface: GigabitEthernet1/0/1 Source security zone: pc Responder: Source IP/port: 3.3.3.1/1 Destination IP/port: 2.2.2.1/0 DS-Lite tunnel peer: - VPN instance/VLAN ID/Inline ID: -/-/- Protocol: ICMP(1) Inbound interface: GigabitEthernet1/0/5 Source security zone: yidong State: ICMP_REPLY Application: ICMP Rule ID: 18 Rule name: all Start time: 2021-04-25 12:34:27 TTL: 24s Initiator->Responder: 0 packets 0 bytes Responder->Initiator: 0 packets 0 bytes |
|---|
2. debug nat packet 确认:
| 断开1/0/4口前: *Apr 25 12:45:53:352 2021 H3C NAT/7/COMMON: -COntext=1; PACKET: (GigabitEthernet1/0/4-in-session) Protocol: ICMP 3.3.3.1: 5 - 1.1.1.1: 0(VPN: 0) ------> 3.3.3.1: 1 - 192.168.7.2: 0(VPN: 0) *Apr 25 12:45:53:352 2021 H3C IPFW/7/IPFW_PACKET: -COntext=1; Sending, interface = GigabitEthernet1/0/1 version = 4, headlen = 20, tos = 0 pktlen = 60, pktid = 327, offset = 0, ttl = 254, protocol = 1 checksum = 60875, s = 3.3.3.1, d = 192.168.7.2 channelID = 0, vpn-InstanceIn = 0, vpn-InstanceOut = 0. prompt: Sending IP packet received from interface GigabitEthernet1/0/4 at interface GigabitEthernet1/0/1. Payload: ICMP type = 0, code = 0, checksum = 0x553b. 断开1/0/5口后: *Apr 25 12:46:29:190 2021 H3C NAT/7/COMMON: -COntext=1; PACKET: (GigabitEthernet1/0/5-in-session) Protocol: ICMP 3.3.3.1: 2 - 2.2.2.1: 0(VPN: 0) ------> 3.3.3.1: 1 - 192.168.7.2: 0(VPN: 0) *Apr 25 12:46:29:190 2021 H3C IPFW/7/IPFW_PACKET: -COntext=1; Sending, interface = GigabitEthernet1/0/1 version = 4, headlen = 20, tos = 0 pktlen = 60, pktid = 335, offset = 0, ttl = 254, protocol = 1 checksum = 60867, s = 3.3.3.1, d = 192.168.7.2 channelID = 0, vpn-InstanceIn = 0, vpn-InstanceOut = 0. prompt: Sending IP packet received from interface GigabitEthernet1/0/5 at interface GigabitEthernet1/0/1. Payload: ICMP type = 0, code = 0, checksum = 0x5537. |
|---|
综上,通过上述关键配置,可以实现,主用1/0/4口,且转换的源地址为1/0/4口的地址(或者地址池);当1/0/4口断开连接,物理状态为down时,流量走备用接口1/0/5口出,且此时转换的源地址为1/0/5口的地址(或者地址池)。
- 2021-09-16回答
- 评论(0)
- 举报
-
(0)
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明


暂无评论