H3C 防火墙频繁报ARP-spoofing
- 0关注
- 1收藏,2701浏览
问题描述:
组网情况:所有设备共用一个C类网段,10.0.0.0/24,电脑网关配置为RT1的IP,配置后防火墙经常报arp攻击,基本每台电脑都会报,但是网关和电脑的MAC地址都是正确的。想请教一下是什么机制触发防火墙报arp欺骗。
atckType(1016)=(21)ARP-spoofing;rcvIfName(1023)=Ethernet1/1;srcIPAddr(1017)=10.0.0.214More Information;srcMacAddr(1021)=44-39-c4-90-29-02;destIPAddr(1019)=10.0.0.7.1More Information;destMacAddr(1022)=74-25-8a-71-cf-03;atckSpeed(1047)=0;atckTime_cn(1048)=20211231132440
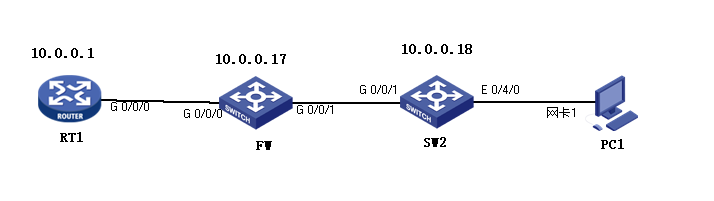
防火墙配置如下:
# firewall packet-filter enable firewall packet-filter default permit # insulate # undo connection-limit enable connection-limit default deny connection-limit default amount upper-limit 50 lower-limit 20 # firewall mode transparent firewall system-ip 10.0.0.17 255.255.255.0 # firewall statistic system enable # radius scheme system # domain system # # interface Aux0 async mode flow # interface Ethernet0/0 promiscuous # interface Ethernet0/1 promiscuous # interface Ethernet0/2 promiscuous # interface Ethernet0/3 promiscuous # interface Ethernet1/0 promiscuous # interface Ethernet1/1 promiscuous # interface Ethernet1/2 promiscuous # interface NULL0 # interface LoopBack0 ip address 10.0.0.17 255.255.255.0 # interface LoopBack1 # firewall zone local set priority 100 # firewall zone trust add interface Ethernet1/0 set priority 85 # firewall zone untrust add interface Ethernet1/1 set priority 5 # firewall zone DMZ set priority 50 # firewall interzone local trust # firewall interzone local untrust # firewall interzone local DMZ # firewall interzone trust untrust # firewall interzone trust DMZ # firewall interzone DMZ untrust # ip route-static 0.0.0.0 0.0.0.0 10.0.0.1 preference 60 ip route-static 10.0.0.0 255.255.255.128 10.0.0.18 preference 30 # firewall defend land firewall defend smurf firewall defend fraggle firewall defend winnuke firewall defend icmp-redirect firewall defend icmp-unreachable firewall defend source-route firewall defend route-record firewall defend tracert firewall defend ping-of-death firewall defend tcp-flag firewall defend ip-fragment firewall defend large-icmp firewall defend teardrop firewall defend ip-sweep firewall defend port-scan firewall defend arp-spoofing firewall defend arp-flood firewall defend frag-flood firewall defend syn-flood enable firewall defend udp-flood enable firewall defend icmp-flood enable # user-interface con 0 user-interface aux 0 user-interface vty 0 4 authentication-mode scheme user privilege level 3 protocol inbound ssh # return
组网及组网描述:
- 2022-01-04提问
- 举报
-
(0)
最佳答案

您好,参考
6.1.8 firewall defend arp-spoofing
【命令】
firewall defend arp-spoofing
undo firewall defend arp-spoofing
【视图】
系统视图
【参数】
无
【描述】
firewall defend arp-spoofing命令用来打开ARP欺骗攻击防范功能,undo firewall defend arp-spoofing命令用来关闭ARP欺骗攻击防范功能。
缺省情况下,关闭ARP欺骗攻击防范功能。
【举例】
# 打开ARP欺骗攻击防范功能。
[H3C] firewall defend arp-spoofing
这个命令产生的日志
- 2022-01-04回答
- 评论(1)
- 举报
-
(0)
我想了解是什么原因触发这类日志


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明


我想了解是什么原因触发这类日志