问
MSR3620 nat端口映射问题
2022-01-18提问
- 0关注
- 1收藏,1783浏览
问题描述:
对齐方式
- 靠左
- 居中
- 靠右
- nat不起作用,我想外网访问内部192.168.20.3:18082上的服务器,做了以下配置,没起效果
- #
- version 7.1.064, Release 0821P18
- #
- sysname H3CROUTE
- #
- clock timezone Beijing add 08:00:00
- clock protocol ntp
- #
- wlan global-configuration
- #
- telnet server enable
- #
- ip unreachables enable
- ip ttl-expires enable
- #
- nat static inbound 218.108.84.204 192.168.20.3
- nat static outbound 192.168.20.3 218.108.84.204
- #
- dhcp enable
- dhcp server always-broadcast
- #
- dns proxy enable
- #
- system-working-mode standard
- password-recovery enable
- #
- vlan 1
- #
- object-group ip address 1段
- 0 network range 192.168.1.11 192.168.1.250
- #
- object-group ip address vlan字段
- 0 network range 192.168.20.1 192.168.100.254
- 0 network exclude 192.168.20.1
- 0 network exclude 192.168.20.3
- 0 network exclude 192.168.30.1
- 0 network exclude 192.168.40.1
- 0 network exclude 192.168.50.1
- 0 network exclude 192.168.60.1
- 0 network exclude 192.168.70.1
- #
- dhcp server ip-pool GigabitEthernet0/0
- gateway-list 192.168.0.1
- network 192.168.0.0 mask 255.255.255.0
- address range 192.168.0.11 192.168.0.249
- dns-list 202.101.172.35 114.114.114.114
- #
- dhcp server ip-pool GigabitEthernet0/1
- gateway-list 192.168.1.1
- network 192.168.1.0 mask 255.255.255.0
- address range 192.168.1.11 192.168.1.249
- dns-list 202.101.172.35 114.114.114.114
- #
- controller Cellular0/0
- #
- interface Virtual-Template0
- #
- interface NULL0
- #
- interface Vlan-interface1
- #
- interface GigabitEthernet0/0
- port link-mode route
- combo enable copper
- ip address 192.168.0.1 255.255.255.0
- nat static enable
- #
- interface GigabitEthernet0/1
- port link-mode route
- combo enable copper
- ip address 192.168.1.1 255.255.255.0
- nat static enable
- attack-defense apply policy AtkInterface3
- #
- interface GigabitEthernet0/2
- port link-mode route
- combo enable copper
- nat static enable
- #
- interface GigabitEthernet0/3
- port link-mode route
- description Multiple_Line
- bandwidth 100000
- combo enable copper
- ip address 115.238.110.154 255.255.255.252
- dns server 114.114.114.114
- dns server 202.101.172.35
- packet-filter name WebHttpHttps5 inbound
- qos car inbound any cir 100000 cbs 6250000 ebs 0 green pass red discard yellow pass
- qos car outbound any cir 100000 cbs 6250000 ebs 0 green pass red discard yellow pass
- nat outbound
- nat server protocol tcp global current-interface 18082 inside 192.168.20.3 18082
- nat static enable
- attack-defense apply policy AtkInterface5
- #
- interface GigabitEthernet0/4
- port link-mode route
- nat static enable
- #
- interface GigabitEthernet0/5
- port link-mode route
- nat static enable
- #
- object-policy ip Any-Any
- rule 0 pass source-ip vlan字段 app-group limitspeed_120
- rule 1 inspect limitspeed source-ip vlan字段
- #
- security-zone name Local
- #
- security-zone name Trust
- #
- security-zone name DMZ
- #
- security-zone name Untrust
- #
- security-zone name Management
- #
- zone-pair security source Any destination Any
- object-policy apply ip Any-Any
- #
- scheduler logfile size 16
- #
- line class console
- user-role network-admin
- #
- line class tty
- user-role network-operator
- #
- line class usb
- user-role network-admin
- #
- line class vty
- user-role network-operator
- #
- line con 0
- user-role network-admin
- #
- line vty 0 63
- authentication-mode scheme
- user-role network-operator
- #
- ip route-static 0.0.0.0 0 GigabitEthernet0/3 115.238.110.153
- ip route-static 114.55.101.147 32 115.238.110.153 preference 10
- ip route-static 192.168.0.0 16 192.168.1.253
- #
- info-center loghost 127.0.0.1 port 3301
- info-center source CFGLOG loghost level informational
- #
- performance-management
- #
- ssh server enable
- #
- ntp-service enable
- ntp-service unicast-server 120.25.108.11
- ntp-service unicast-server 203.107.6.88
- #
- acl advanced name WebHttpHttps5
- rule 65533 permit tcp destination-port eq www
- rule 65534 permit tcp destination-port eq 443
- #
- password-control enable
- undo password-control aging enable
- undo password-control history enable
- password-control length 6
- password-control login-attempt 3 exceed lock-time 10
- password-control update-interval 0
- password-control login idle-time 0
- #
- domain system
- #
- domain default enable system
- #
- role name level-0
- description Predefined level-0 role
- #
- role name level-1
- description Predefined level-1 role
- #
- role name level-2
- description Predefined level-2 role
- #
- role name level-3
- description Predefined level-3 role
- #
- role name level-4
- description Predefined level-4 role
- #
- role name level-5
- description Predefined level-5 role
- #
- role name level-6
- description Predefined level-6 role
- #
- role name level-7
- description Predefined level-7 role
- #
- role name level-8
- description Predefined level-8 role
- #
- role name level-9
- description Predefined level-9 role
- #
- role name level-10
- description Predefined level-10 role
- #
- role name level-11
- description Predefined level-11 role
- #
- role name level-12
- description Predefined level-12 role
- #
- role name level-13
- description Predefined level-13 role
- #
- role name level-14
- description Predefined level-14 role
- #
- user-group system
- #
- local-user admin class manage
- service-type ftp
- service-type ssh telnet terminal http https
- authorization-attribute user-role network-admin
- #
- connection-limit policy 32
- #
- app-group limitspeed_120
- description "User-defined application group"
- include application AndroidMarket
- include application AnZhiMarket
- include application BaiduWenKu
- include application JiFengMarket
- include application OnlineDown
- include application WanDouJia
- #
- ip http enable
- #
- attack-defense policy AtkInterface3
- scan detect level high action logging block-source
- syn-flood detect non-specific
- syn-flood action drop
- udp-flood detect non-specific
- udp-flood action drop
- icmp-flood detect non-specific
- icmp-flood action drop
- signature detect smurf action drop
- signature detect large-icmp action drop
- signature detect large-icmpv6 action drop
- signature detect tcp-invalid-flags action drop
- signature detect tcp-null-flag action drop
- signature detect tcp-all-flags action drop
- signature detect tcp-syn-fin action drop
- signature detect tcp-fin-only action drop
- signature detect land action drop
- signature detect winnuke action drop
- signature detect fraggle action drop
- signature detect ip-option record-route action drop
- signature detect ip-option strict-source-routing action drop
- signature detect icmp-type destination-unreachable action drop
- signature detect icmp-type redirect action drop
- #
- attack-defense policy AtkInterface5
- syn-flood detect non-specific
- syn-flood action drop
- udp-flood detect non-specific
- udp-flood action drop
- icmp-flood detect non-specific
- icmp-flood action drop
- signature detect smurf action drop
- signature detect large-icmp action drop
- signature detect large-icmpv6 action drop
- signature detect tcp-invalid-flags action drop
- signature detect tcp-null-flag action drop
- signature detect tcp-all-flags action drop
- signature detect tcp-syn-fin action drop
- signature detect tcp-fin-only action drop
- signature detect land action drop
- signature detect winnuke action drop
- signature detect fraggle action drop
- signature detect ip-option record-route action drop
- signature detect ip-option strict-source-routing action drop
- signature detect icmp-type destination-unreachable action drop
- signature detect icmp-type redirect action drop
- #
- url-filter policy limitspeed
- default-action permit
- #
- app-profile limitspeed
- url-filter apply policy limitspeed
- #
- wlan ap-group default-group
- vlan 1
- #
- traffic-policy
- rule 1 name limitspeed_120
- action qos profile limitspeed_120
- source-address address-set vlan字段
- application app AndroidMarket
- application app AnZhiMarket
- application app BaiduWenKu
- application app JiFengMarket
- application app OnlineDown
- application app WanDouJia
- profile name limitspeed_120
- bandwidth downstream maximum 100
- bandwidth upstream maximum 100
- #
- return
组网及组网描述:
交换机上做了20/30/40/50/60的vlan,交换机地址192.168.1.253
- 2022-01-18提问
- 举报
-
(0)
最佳答案

nat static inbound 218.108.84.204 192.168.20.3
全局做了全端口映射,需要访问 218.108.84.204
- 2022-01-18回答
- 评论(5)
- 举报
-
(0)
NAT hairpin应该是这个功能没开启,这个功能好像在web端是看不到的
zhiliao_IIO49h
发表时间:2022-01-18
更多>>
我路由器地址是115.238.110.154,218.108.84.204这是一个未使用的公网地址,我原来在5200上都是这么配的,都可以使用
zhiliao_IIO49h
发表时间:2022-01-18
不要管之前怎么配置,你的目标服务器,匹配了全端口映射自然不会匹配接口的端口映射
漓离原上谱
发表时间:2022-01-18
我把那条删了,现在是我用手机能访问,但是,在局域网内访问不了
zhiliao_IIO49h
发表时间:2022-01-18
跟踪一下路径 nat static outbound 192.168.20.3 218.108.84.204 这条是回给公网的不是回给内网的
漓离原上谱
发表时间:2022-01-18
NAT hairpin应该是这个功能没开启,这个功能好像在web端是看不到的
zhiliao_IIO49h
发表时间:2022-01-18
编辑答案
➤


✖
亲~登录后才可以操作哦!
确定
✖
✖
你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
✖
举报
×
侵犯我的权益
>
对根叔社区有害的内容
>
辱骂、歧视、挑衅等(不友善)
侵犯我的权益
×
侵犯了我企业的权益
>
抄袭了我的内容
>
诽谤我
>
辱骂、歧视、挑衅等(不友善)
骚扰我
侵犯了我企业的权益
×
您好,当您发现根叔知了上有关于您企业的造谣与诽谤、商业侵权等内容时,您可以向根叔知了进行举报。 请您把以下内容通过邮件发送到 pub.zhiliao@h3c.com 邮箱,我们会在审核后尽快给您答复。
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
我们认为知名企业应该坦然接受公众讨论,对于答案中不准确的部分,我们欢迎您以正式或非正式身份在根叔知了上进行澄清。
抄袭了我的内容
×
原文链接或出处
诽谤我
×
您好,当您发现根叔知了上有诽谤您的内容时,您可以向根叔知了进行举报。 请您把以下内容通过邮件发送到pub.zhiliao@h3c.com 邮箱,我们会尽快处理。
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
我们认为知名企业应该坦然接受公众讨论,对于答案中不准确的部分,我们欢迎您以正式或非正式身份在根叔知了上进行澄清。
对根叔社区有害的内容
×
垃圾广告信息
色情、暴力、血腥等违反法律法规的内容
政治敏感
不规范转载
>
辱骂、歧视、挑衅等(不友善)
骚扰我
诱导投票
不规范转载
×
举报说明




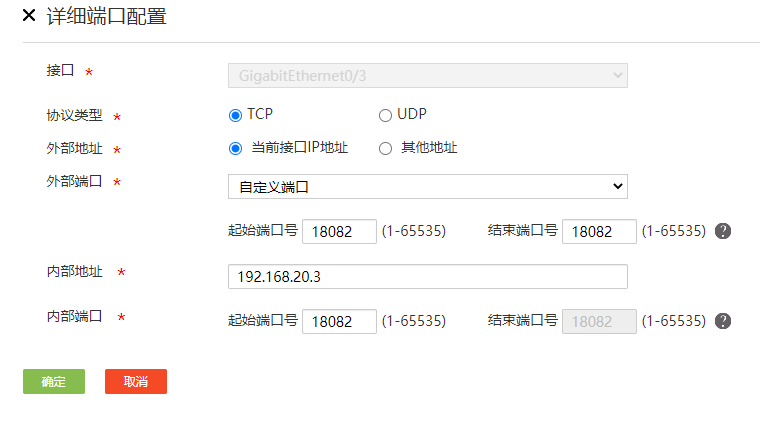
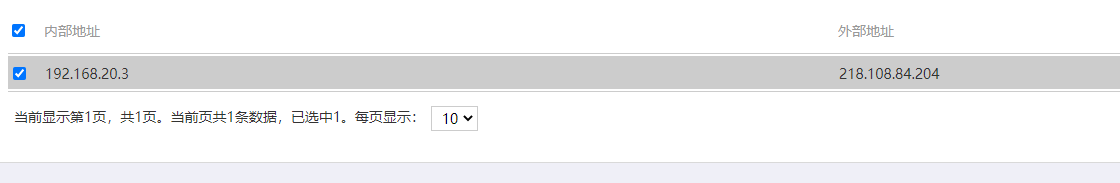 我做了2个映射,一个是端口映射,一个是公网地址的映射,都不成功
我做了2个映射,一个是端口映射,一个是公网地址的映射,都不成功