VPN连接MSR3600无法访问互联网
- 0关注
- 1收藏,2096浏览
问题描述:
单位内部有两台服务器是做软件开发使用,原来开发组在单位局域网内部,因此一直通过内网访问服务器做软件开发,现在由于种种原因开发组搬到局域网外,想要通过VPN连接到单位的局域网方便软件开发。经过大神指点,VPN已经创建成功并且通过公网可以连接,但是通过VPN连接之后无法访问互联网。路由器配置贴在下面,还望各位大神不吝赐教,不胜感激。
组网及组网描述:
#
version 7.1.064, Release 0809P28
#
sysname Internet-Roter
#
clock timezone Beijing add 08:00:00
clock protocol ntp
#
telnet server enable
#
security-zone intra-zone default permit
#
track 1 nqa entry admin pppoe0591 reaction 1
#
track 2 nqa entry admin pppoe0309 reaction 1
#
track 3 nqa entry admin zx reaction 1
#
ospf 10 router-id 10.255.255.1
default-route-advertise always
import-route direct
area 0.0.0.0
network 172.255.255.1 0.0.0.0
#
ip pool l2tp1 192.168.50.100 192.168.50.200
#
dialer-group 10 rule ip permit
#
ip unreachables enable
ip ttl-expires enable
#
dhcp enable
dhcp server always-broadcast
#
dns proxy enable
#
lldp global enable
#
password-recovery enable
#
vlan 1
#
object-group service FW
0 service tcp destination eq 12306
#
policy-based-route pbr permit node 10
if-match acl 3010
apply next-hop 192.168.2.1 track 1
#
policy-based-route pbr permit node 20
if-match acl 3020
apply next-hop 192.168.1.1 track 2
#
nqa entry admin pppoe0309
type icmp-echo
description ip 192.168.1.1
frequency 100
reaction 1 checked-element probe-fail threshold-type consecutive 5 action-type trigger-only
source ip 192.168.1.2
#
nqa entry admin pppoe0591
type icmp-echo
destination ip 192.168.2.1
frequency 100
reaction 1 checked-element probe-fail threshold-type consecutive 5 action-type trigger-only
source ip 192.168.2.2
#
nqa entry admin zx
type icmp-echo
destination ip 113.200.75.1
frequency 100
reaction 1 checked-element probe-fail threshold-type consecutive 5 action-type trigger-only
source ip 113.200.75.79
#
nqa schedule admin pppoe0591 start-time now lifetime forever
nqa schedule admin zx start-time now lifetime forever
#
controller Cellular0/0
#
interface Aux0
#
interface Virtual-Template0
#
interface Virtual-Template1
ppp authentication-mode chap
remote address pool l2tp1
ip address 192.168.50.1 255.255.255.0
#
interface NULL0
#
interface Vlan-interface1
description LAN-interface
ip address 192.168.142.1 255.255.255.0
tcp mss 1280
undo dhcp select server
#
interface GigabitEthernet0/0
port link-mode route
description PPPOE-02989630591
ip address 192.168.2.2 255.255.255.0
nat outbound 3000
#
interface GigabitEthernet0/1
port link-mode route
description DianXin-ZhuanXin
ip address 113.200.75.79 255.255.255.128
nat outbound 3000
nat server protocol tcp global current-interface 22 inside 192.168.142.250 22
nat server protocol tcp global current-interface 23 inside 192.168.142.251 22
nat server protocol tcp global current-interface 24 inside 192.168.142.252 22
nat server protocol tcp global current-interface 25 inside 192.168.142.253 22
nat server protocol tcp global current-interface 26 inside 192.168.142.254 22
nat server protocol tcp global current-interface 8087 8090 inside 192.168.142.251 8087 8090
nat server protocol tcp global current-interface 8091 inside 192.168.142.252 8089
nat server protocol tcp global current-interface 9000 inside 192.168.142.253 9000
nat server protocol tcp global current-interface 15672 inside 192.168.142.251 15672
#
interface GigabitEthernet0/2
port link-mode route
description PPPOE-02989630309
ip address 192.168.1.2 255.255.255.0
nat outbound 3000
#
interface GigabitEthernet0/3
port link-mode route
ip address 172.255.255.1 255.255.255.252
ospf network-type p2p
ip policy-based-route pbr
#
interface GigabitEthernet0/27
port link-mode route
#
interface GigabitEthernet0/4
port link-mode bridge
#
interface GigabitEthernet0/5
port link-mode bridge
#
interface GigabitEthernet0/6
port link-mode bridge
#
interface GigabitEthernet0/7
port link-mode bridge
#
interface GigabitEthernet0/8
port link-mode bridge
#
interface GigabitEthernet0/9
port link-mode bridge
#
interface GigabitEthernet0/10
port link-mode bridge
#
interface GigabitEthernet0/11
port link-mode bridge
#
interface GigabitEthernet0/12
port link-mode bridge
#
interface GigabitEthernet0/13
port link-mode bridge
#
interface GigabitEthernet0/14
port link-mode bridge
#
interface GigabitEthernet0/15
port link-mode bridge
#
interface GigabitEthernet0/16
port link-mode bridge
#
interface GigabitEthernet0/17
port link-mode bridge
#
interface GigabitEthernet0/18
port link-mode bridge
#
interface GigabitEthernet0/19
port link-mode bridge
#
interface GigabitEthernet0/20
port link-mode bridge
#
interface GigabitEthernet0/21
port link-mode bridge
#
interface GigabitEthernet0/22
port link-mode bridge
#
interface GigabitEthernet0/23
port link-mode bridge
#
interface GigabitEthernet0/24
port link-mode bridge
#
interface GigabitEthernet0/25
port link-mode bridge
#
interface GigabitEthernet0/26
port link-mode bridge
#
object-policy ip Local-Local
rule 0 pass counting
#
object-policy ip Local-Trust
rule 0 pass logging counting
#
object-policy ip Local-Untrust
rule 0 pass logging counting
#
object-policy ip Trust-Local
rule 0 pass logging counting
#
object-policy ip Trust-Trust
rule 0 pass logging counting
#
object-policy ip Trust-Untrust
rule 0 pass logging counting
#
object-policy ip Untrust-Local
rule 1 pass service FW counting
#
security-zone name Local
#
security-zone name Trust
import interface GigabitEthernet0/0
import interface GigabitEthernet0/1
import interface GigabitEthernet0/2
import interface GigabitEthernet0/3
import interface Vlan-interface1
#
security-zone name DMZ
#
security-zone name Untrust
#
security-zone name Management
#
zone-pair security source Local destination Local
object-policy apply ip Local-Local
#
zone-pair security source Local destination Trust
object-policy apply ip Local-Trust
#
zone-pair security source Local destination Untrust
object-policy apply ip Local-Untrust
#
zone-pair security source Trust destination Local
object-policy apply ip Trust-Local
#
zone-pair security source Trust destination Trust
object-policy apply ip Trust-Trust
#
zone-pair security source Trust destination Untrust
object-policy apply ip Trust-Untrust
#
scheduler logfile size 16
#
line class aux
user-role network-admin
#
line class tty
user-role network-operator
#
line class vty
user-role network-operator
#
line aux 0
user-role network-admin
#
line vty 0 63
authentication-mode scheme
user-role network-admin
user-role network-operator
#
ip route-static 0.0.0.0 0 192.168.2.1 preference 100
ip route-static 0.0.0.0 0 192.168.1.1 preference 150
ip route-static 0.0.0.0 0 113.200.75.1 track 3
#
ssh server enable
ssh server acl 2000
ssh server port 12306
#
ntp-service enable
ntp-service unicast-server 114.118.7.161
#
acl advanced 3000
rule 0 permit ip
#
acl advanced 3010
description PPPOE-02989630591
rule 0 permit ip source 172.16.10.0 0.0.1.255
rule 5 permit ip source 172.16.20.0 0.0.1.255
rule 10 permit ip source 172.16.30.0 0.0.1.255
#
acl advanced 3020
description PPPOE-02989630309
rule 0 permit ip source 172.16.15.0 0.0.0.255
rule 5 permit ip source 172.16.25.0 0.0.0.255
rule 10 permit ip source 172.16.40.0 0.0.0.255
#
password-control enable
undo password-control aging enable
undo password-control length enable
undo password-control composition enable
undo password-control history enable
password-control length 6
password-control login-attempt 3 exceed lock-time 2
password-control update-interval 0
password-control login idle-time 0
undo password-control complexity user-name check
undo password-control change-password first-login enable
#
domain system
#
domain default enable system
#
role name level-0
description Predefined level-0 role
#
role name level-1
description Predefined level-1 role
#
role name level-2
description Predefined level-2 role
#
role name level-3
description Predefined level-3 role
#
role name level-4
description Predefined level-4 role
#
role name level-5
description Predefined level-5 role
#
role name level-6
description Predefined level-6 role
#
role name level-7
description Predefined level-7 role
#
role name level-8
description Predefined level-8 role
#
role name level-9
description Predefined level-9 role
#
role name level-10
description Predefined level-10 role
#
role name level-11
description Predefined level-11 role
#
role name level-12
description Predefined level-12 role
#
role name level-13
description Predefined level-13 role
#
role name level-14
description Predefined level-14 role
#
user-group system
#
local-user admin class manage
service-type ftp
service-type ssh telnet terminal http https
authorization-attribute user-role level-15
authorization-attribute user-role network-admin
authorization-attribute user-role network-operator
#
local-user administrator class manage
service-type ssh telnet terminal http https
authorization-attribute user-role level-15
authorization-attribute user-role network-admin
authorization-attribute user-role network-operator
#
local-user bdxsj class network
password cipher $c$3$q+cRoZ
access-limit 50
service-type ppp
authorization-attribute user-role network-operator
#
l2tp-group 1 mode lns
allow l2tp virtual-template 1
undo tunnel authentication
tunnel name VPN
#
l2tp enable
#
ip http enable
ip https enable
#
wlan global-configuration
#
wlan ap-group default-group
vlan 1
#
return
- 2022-03-01提问
- 举报
-
(0)
最佳答案

inode客户端连进来的吗?
在inode客户端软件里把路由设置改一下,添加路由,这样就只有去目的网段的时候会走vpn了。默认是所有流量(包括正常上网)都会走vpn。
还有一种办法是vpn下发dns,让他们上网时先通过vpn连进来再通过你们的宽带连出去。这种配起来会麻烦一些。
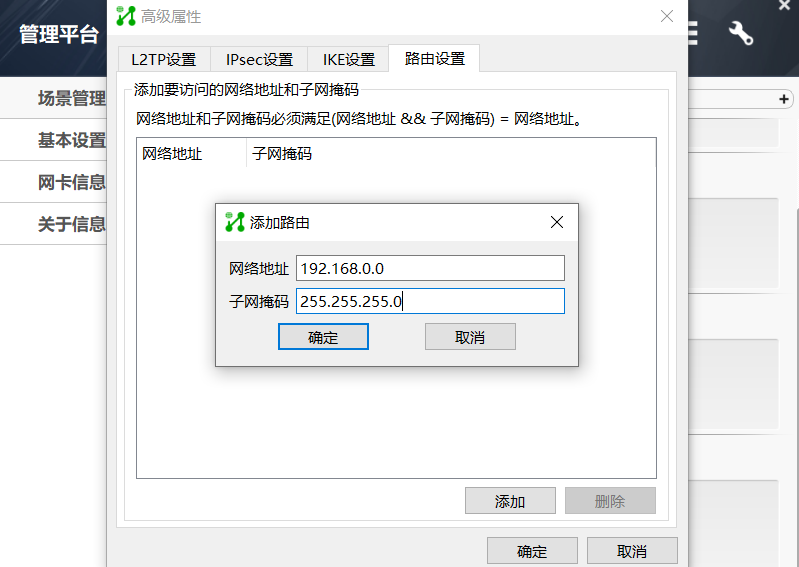
- 2022-03-01回答
- 评论(4)
- 举报
-
(0)


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明





谢谢了。前几天我下载了另一个VPN软件已经把这个问题解决了。