防火墙IPSEC VPN,两边均没有任何ike/ipsec sa
- 0关注
- 1收藏,1895浏览
问题描述:
REMOTE-FW(222.1.1.1)与FW1建立IPSEC VPN。
两端配置如下(感觉也不少配置啊!为什么IKE /IPSEC SA都没有,有什么思路,大佬能解惑嘛?)
IKE 阶段:
remote-FW:
ike profile 1
keychain 1
local-identity address 222.1.1.1
match remote identity address 58.242.252.251 255.255.255.255
match local address GigabitEthernet1/0/0
proposal 1
# ike proposal 1
encryption-algorithm 3des-cbc
dh group2 a
uthentication-algorithm md5
# ike keychain 1
pre-shared-key address 58.242.252.251 0.0.0.0 key simple 12345678
-------------------
FW1:
ike profile 1
keychain 1
local-identity address 58.242.252.251
match remote identity address 222.1.1.1 255.255.255.255
match local address GigabitEthernet1/0/0
proposal 1
# ike proposal 1
encryption-algorithm 3des-cbc
dh group2
authentication-algorithm md5
# ike keychain 1
pre-shared-key address 222.1.1.1 0.0.0.0 key simple 12345678
-----------------------------
IPSEC阶段:
remote-fw
acl advanced 3200
rule 0 permit ip source 10.5.255.1 0 destination 10.6.9.17 0 #
# 配置transform 加解密
ipsec transform-set 1
esp encryption-algorithm 3des-cbc esp
authentication-algorithm sha1
# 配置ipsec策略
# ipsec policy 1 isakmp
transform-set 1
security acl 3200
local-address 222.1.1.1
remote-address 58.242.252.251
ike-profile 1 #
接口下调用策略:
interface GigabitEthernet1/0/0
port link-mode route
combo enable copper
ip address 222.1.1.1 255.255.255.248
ospf 1 area 0.0.0.0
ip last-hop hold
ipsec apply policy 1
fw1:
# acl advanced 3200
rule 0 permit ip source 10.6.9.17 0 destination 10.5.255.1 0
# ipsec transform-set 1
esp encryption-algorithm 3des-cbc
esp authentication-algorithm sha1 #
ipsec policy 1 1 isakmp
transform-set 1
security acl 3200
local-address 58.242.252.251
remote-address 222.1.1.1
ike-profile 1 #
接口下调用策略:
interface GigabitEthernet1/0/0
port link-mode route
combo enable copper
ip address 58.242.252.251 255.255.255.248
ospf 1 area 0.0.0.0
ip last-hop hold
ipsec apply policy 1
两端公网IP都能互通,为什么10.5.255.1无法ping通10.6.9.17?(IPSEC无法建立)
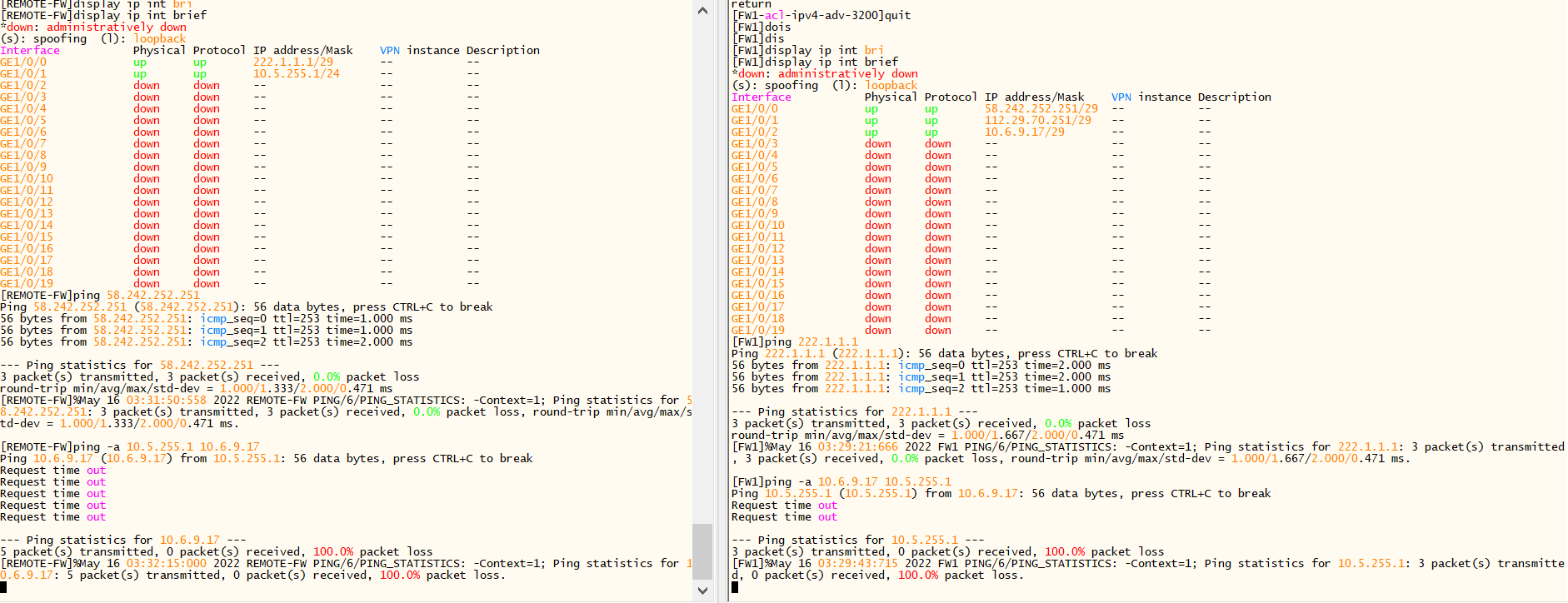
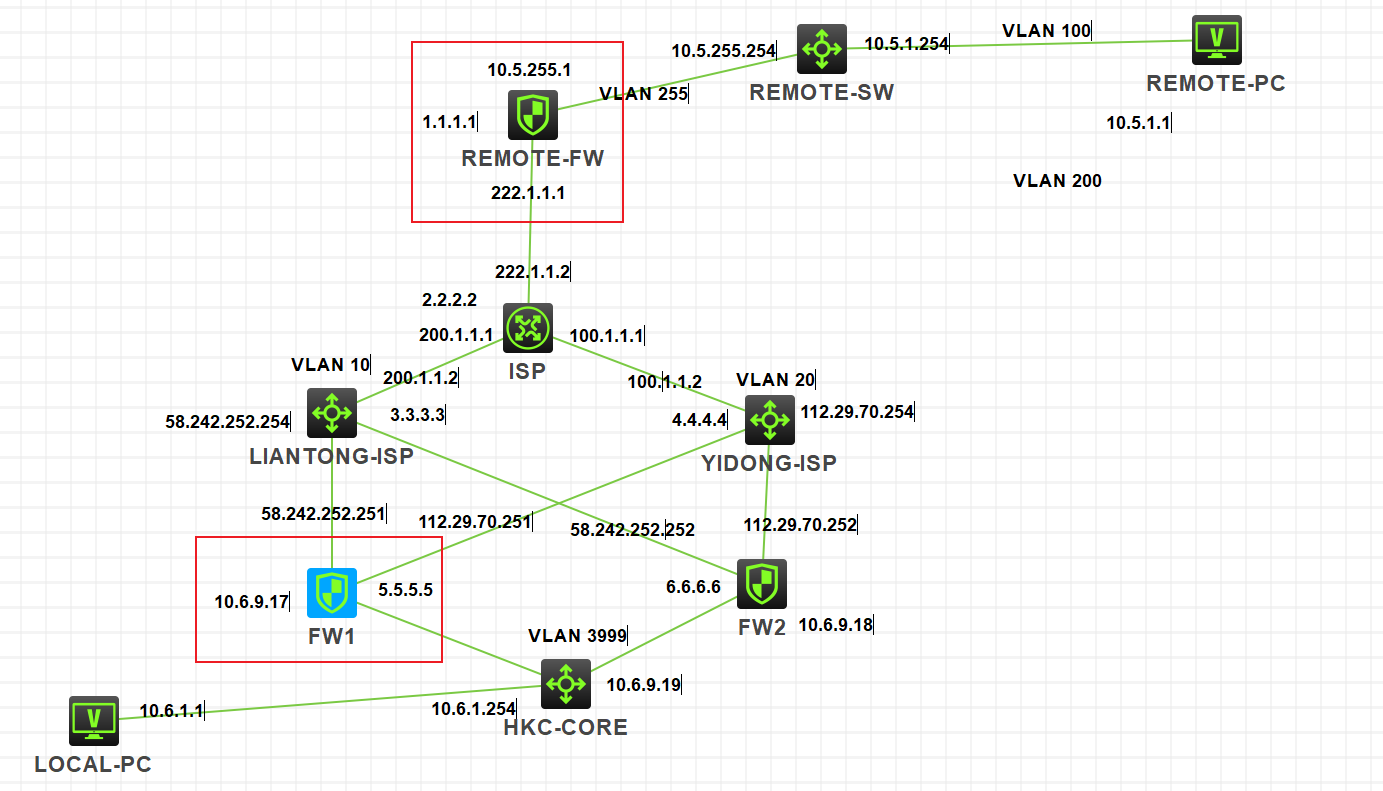
组网及组网描述:
- 2022-05-16提问
- 举报
-
(0)
最佳答案

所有配置如下:
remote-fw:
[REMOTE-FW]dis cu
#
version 7.1.064, Alpha 7164
#
sysname REMOTE-FW
#
context Admin id 1
#
telnet server enable
#
irf mac-address persistent timer
irf auto-update enable
undo irf link-delay
irf member 1 priority 1
#
ospf 1 router-id 1.1.1.1
area 0.0.0.0
#
ip unreachables enable
ip ttl-expires enable
#
lldp global enable
#
xbar load-single
password-recovery enable
lpu-type f-series
#
vlan 1
#
interface NULL0
#
interface LoopBack0
ip address 1.1.1.1 255.255.255.255
ospf 1 area 0.0.0.0
#
interface GigabitEthernet1/0/0
port link-mode route
combo enable copper
ip address 222.1.1.1 255.255.255.248
ospf 1 area 0.0.0.0
ip last-hop hold
ipsec apply policy 1
#
interface GigabitEthernet1/0/1
port link-mode route
combo enable copper
ip address 10.5.255.1 255.255.255.0
security-zone name Local
#
security-zone name Trust
import interface GigabitEthernet1/0/1
#
security-zone name DMZ
#
security-zone name Untrust
import interface GigabitEthernet1/0/0
#
security-zone name Management
#
zone-pair security source Any destination Any
packet-filter 3000
#
zone-pair security source Any destination Local
packet-filter 3000
#
zone-pair security source Local destination Any
packet-filter 3000
#
ip route-static 10.5.0.0 16 10.5.255.254
#
acl advanced 3000
rule 0 permit ip
#
acl advanced 3100
rule 5 deny ip source 10.5.0.0 0.0.255.255 destination 10.6.0.0 0.0.255.255
rule 10 permit ip
#
acl advanced 3200
rule 0 permit ip source 10.5.255.1 0 destination 10.6.9.17 0
#
domain system
#
aaa session-limit ftp 16
aaa session-limit telnet 16
aaa session-limit ssh 16
domain default enable system
#
ipsec transform-set 1
esp encryption-algorithm 3des-cbc
esp authentication-algorithm sha1
#
ipsec policy 1 1 isakmp
transform-set 1
security acl 3200
local-address 222.1.1.1
remote-address 58.242.252.251
ike-profile 1
#
ipsec policy 1 isakmp
transform-set 1
security acl 3200
local-address 222.1.1.1
remote-address 58.242.252.251
ike-profile 1
#
ike profile 1
keychain 1
local-identity address 222.1.1.1
match remote identity address 58.242.252.251 255.255.255.255
match local address GigabitEthernet1/0/0
proposal 1
#
ike proposal 1
encryption-algorithm 3des-cbc
dh group2
authentication-algorithm md5
#
ike keychain 1
pre-shared-key address 58.242.252.251 0.0.0.0 key cipher $c$3$gugYFDrkojjhRiPiEHDwQZ+EjPuyizzz1A==
#
ip http enable
ip https enable
#
return
----------------------
[FW1]dis cu
#
version 7.1.064, Alpha 7164
#
sysname FW1
#
context Admin id 1
#
telnet server enable
#
irf mac-address persistent timer
irf auto-update enable
undo irf link-delay
irf member 1 priority 1
#
ospf 1 router-id 5.5.5.5
area 0.0.0.0
#
ip unreachables enable
ip ttl-expires enable
#
lldp global enable
#
xbar load-single
password-recovery enable
lpu-type f-series
#
vlan 1
#
interface NULL0
#
interface LoopBack0
ip address 5.5.5.5 255.255.255.255
ospf 1 area 0.0.0.0
#
interface GigabitEthernet1/0/0
port link-mode route
combo enable copper
ip address 58.242.252.251 255.255.255.248
ospf 1 area 0.0.0.0
ip last-hop hold
ipsec apply policy 1
#
interface GigabitEthernet1/0/1
port link-mode route
combo enable copper
ip address 112.29.70.251 255.255.255.248
ospf cost 5
ospf 1 area 0.0.0.0
#
interface GigabitEthernet1/0/2
port link-mode route
combo enable copper
ip address 10.6.9.17 255.255.255.248
security-zone name Local
#
security-zone name Trust
import interface GigabitEthernet1/0/2
#
security-zone name DMZ
#
security-zone name Untrust
import interface GigabitEthernet1/0/0
import interface GigabitEthernet1/0/1
#
security-zone name Management
#
zone-pair security source Any destination Any
packet-filter 3000
#
zone-pair security source Any destination Local
packet-filter 3000
#
zone-pair security source Local destination Any
packet-filter 3000
#
ip route-static 10.6.0.0 16 10.6.9.19
#
acl advanced 3000
rule 0 permit ip
#
acl advanced 3100
rule 5 deny ip source 10.6.0.0 0.0.255.255 destination 10.5.0.0 0.0.255.255
rule 10 permit ip
#
acl advanced 3200
rule 0 permit ip source 10.6.9.17 0 destination 10.5.255.1 0
#
ipsec transform-set 1
esp encryption-algorithm 3des-cbc
esp authentication-algorithm sha1
#
ipsec policy 1 1 isakmp
transform-set 1
security acl 3200
local-address 58.242.252.251
remote-address 222.1.1.1
ike-profile 1
#
ike profile 1
keychain 1
local-identity address 58.242.252.251
match remote identity address 222.1.1.1 255.255.255.255
match local address GigabitEthernet1/0/0
proposal 1
#
ike proposal 1
encryption-algorithm 3des-cbc
dh group2
authentication-algorithm md5
#
ike keychain 1
pre-shared-key address 222.1.1.1 0.0.0.0 key cipher $c$3$LLHNrAeFN92nSdk8tSqL+Vx3uwKSuSBhiQ==
#
ip http enable
ip https enable
#
return
- 2022-05-16回答
- 评论(0)
- 举报
-
(0)

nat配置了吗?nat拒绝ipsec 兴趣流了?
ike ipsec加密算法一致?
- 2022-05-16回答
- 评论(3)
- 举报
-
(0)
还要配置静态路由。触发感兴趣流
nat还没配置呢,Ike ipsec加密算法检查了,都一致,就是建立不了任何sa
参考 https://zhiliao.h3c.com/Theme/details/45585
还要配置静态路由。触发感兴趣流
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明
