防火墙出口策略路由不生效,请各位帮忙看看是什么地方不行
- 0关注
- 1收藏,2268浏览
问题描述:
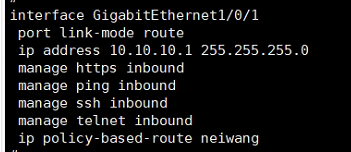
这是防火墙一口与核心相接的口 已经匹配了neiwang的路由策略
-----------------------
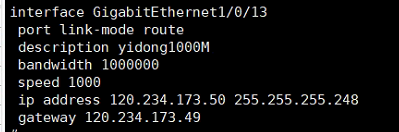
这是防火墙13口的专线
----------------------
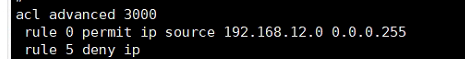
这是匹配我现在电脑网段的ACL
--------------------------
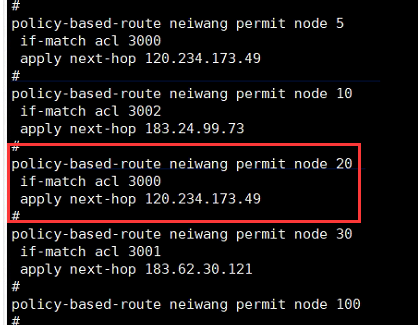
这是我做测试用的一个节点,其他节点我没配置ACL,就是配置了这一个,应该没关系吧。
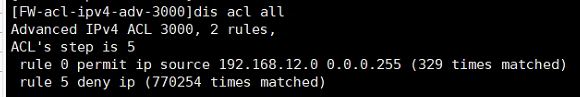
查看匹配这个段的流量是有的,但是没生效
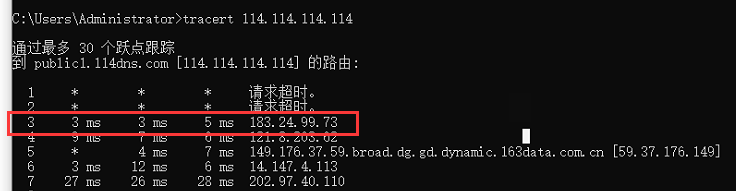
走的还是默认路由的专线
--------------------
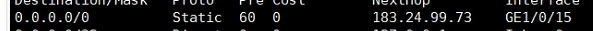
只有这一条默认路由,我现在就是不想走这条默认路由,走其他专线,但是失败了,请问我有哪里漏配或者是配置错了吗
组网及组网描述:
- 2022-06-17提问
- 举报
-
(0)

负载均衡优先
- 2022-06-17回答
- 评论(3)
- 举报
-
(0)
那我应该要如何把策略的优先级调高呢 或者把负载均衡关闭
只能把负载均衡禁用
ok了 谢谢

你的node5不是跟你这个一样的吗
- 2022-06-17回答
- 评论(2)
- 举报
-
(0)
你好 我把20删掉了 保留了5 还是一样走的默认路由专线

贴全配置吧
- 2022-06-17回答
- 评论(1)
- 举报
-
(0)
你好已经贴了 请帮忙看看
你好已经贴了 请帮忙看看

# |
|---|
- 2022-06-17回答
- 评论(0)
- 举报
-
(0)
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明



ok了 谢谢