F100的SSLvpn
- 0关注
- 1收藏,2446浏览
问题描述:
F100做网关直连外网,IP接入方式配置了SSLVPN,用户通过Inode访问内网服务器,以前是移动专线,现在要加一条电信专线,
让用户也可以通过电信的公网IP用Inode访问内网服务器,怎么做配置呢?
组网及组网描述:
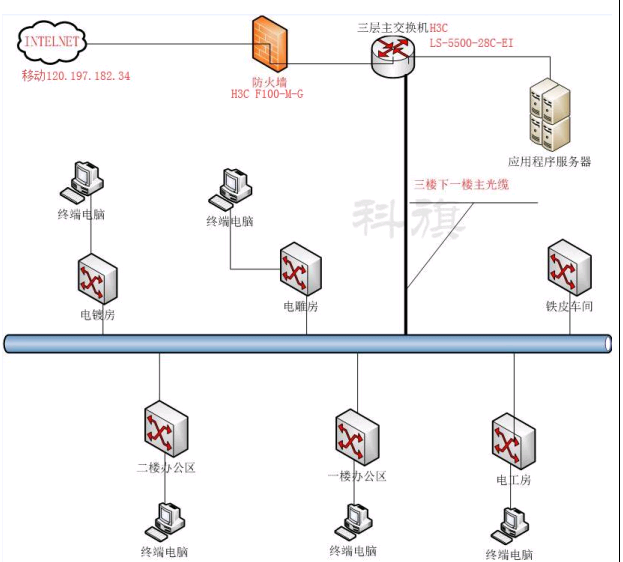
- 2018-09-12提问
- 举报
-
(0)
最佳答案

1. 组网需求
Device为SSL VPN网关设备,连接公网用户和企业私有网络VPN 1。用户通过Device可以通过IP接入方式安全地访问VPN 1内的Server。Device通过RADIUS server采用远程认证和授权方式对用户进行认证和授权。
2. 组网图
图1-27 IP接入配置组网图

3. 配置步骤
![]()
在开始下面的配置之前,假设已完成如下配置:
· Device上已创建VPN实例,设备各接口都已绑定对应的VPN实例且接口的地址都已配置完毕。
· Device已获取到CA证书ca.cer和服务器证书server.pfx。
· Device与SSL VPN客户端、Server之间路由可达。
· Server上存在到达网段10.1.1.0/24的路由。
· RADIUS server已经部署完成,能够对用户进行认证和授权。
# 配置PKI域sslvpn。
<Device> system-view
[Device] pki domain sslvpn
[Device-pki-domain-sslvpn] public-key rsa general name sslvpn
[Device-pki-domain-sslvpn] undo crl check enable
[Device-pki-domain-sslvpn] quit
# 导入CA证书ca.cer和服务器证书server.pfx。
[Device] pki import domain sslvpn der ca filename ca.cer
[Device] pki import domain sslvpn p12 local filename server.pfx
# 配置SSL服务器端策略ssl。
[Device] ssl server-policy ssl
[Device-ssl-server-policy-ssl] pki-domain sslvpn
[Device-ssl-server-policy-ssl] quit
# 创建IPv4高级ACL3000,允许所有IP报文通过。
[Device] acl advanced 3000
[Device-acl-ipv4-adv-3000] rule permit ip
[Device-acl-ipv4-adv-3000] quit
# 配置SSL VPN网关gw的IP地址为1.1.1.2,端口号为2000,并引用SSL服务器端策略ssl。
[Device] sslvpn gateway gw
[Device-sslvpn-gateway-gw] ip address 1.1.1.2 port 2000
[Device-sslvpn-gateway-gw] ssl server-policy ssl
# 开启SSL VPN网关gw。
[Device-sslvpn-gateway-gw] service enable
[Device-sslvpn-gateway-gw] quit
# 创建地址池ippool,指定IP地址范围为10.1.1.1~10.1.1.10。
[Device] sslvpn ip address-pool ippool 10.1.1.1 10.1.1.10
# 创建SSL VPN AC接口1,配置该接口绑定VPN实例VPN1,并配置接口的IP地址为10.1.1.100/24。
[Device] interface sslvpn-ac 1
[Device-SSLVPN-AC1] ip binding vpn-instance VPN1
[Device-SSLVPN-AC1] ip address 10.1.1.100 24
[Device-SSLVPN-AC1] quit
# 创建NAT地址组,配置出方向NAT地址转换。
[Device] nat address-group 1
[Device-nat-address-group-1] address 2.2.2.10 2.2.2.20
[Device-nat-address-group-1] quit
[Device] interface GigabitEthernet1/0/2
[Device-GigabitEthernet1/0/2] nat outbound 3000 address-group 1 vpn-instance vpn1
[Device-GigabitEthernet1/0/2] quit
# 配置SSL VPN访问实例ctx引用SSL VPN网关gw,并配置SSL VPN访问实例关联的VPN实例为VPN1。
[Device] sslvpn context ctx
[Device-sslvpn-context-ctx] gateway gw
[Device-sslvpn-context-ctx] vpn-instance VPN1
# 配置SSL VPN访问实例使用ISP域domain1进行AAA认证。
[Device-sslvpn-context-ctx] aaa domain domain1
# 创建路由列表rtlist,并添加路由表项20.2.2.0/24。
[Device-sslvpn-context-ctx] ip-route-list rtlist
[Device-sslvpn-context-ctx-route-list-rtlist] include 20.2.2.0 255.255.255.0
[Device-sslvpn-context-ctx-route-list-rtlist] quit
# 配置SSL VPN访问实例ctx引用SSL VPN AC接口1
[Device-sslvpn-context-ctx] ip-tunnel interface sslvpn-ac 1
# 配置SSL VPN访问实例ctx,并引用路由列表rtlist和地址池ippool。
[Device-sslvpn-context-ctx] ip-tunnel address-pool ippool mask 255.255.255.0
[Device-sslvpn-context-ctx] policy group pgroup
[Device-sslvpn-context-ctx-policy-group-pgroup] ip-tunnel access-route ip-route-list rtlist
[Device-sslvpn-context-ctx-policy-group-pgroup] filter ip-tunnel 3000
[Device-sslvpn-context-ctx-policy-group-pgroup] quit
# 开启SSL VPN访问实例ctx。
[Device-sslvpn-context-ctx] service enable
[Device-sslvpn-context-ctx] quit
# 配置RADIUS方案rscheme,指定认证和授权服务器地址均为3.3.3.2、认证和授权的共享密钥均为123456、发送给RADIUS服务器的用户名格式为不携带ISP域名。
[Device] radius scheme rscheme
[Device-radius-rscheme] primary authentication 3.3.3.2
[Device-radius-rscheme] primary accounting 3.3.3.2
[Device-radius-rscheme] accounting-on enable
[Device-radius-rscheme] key authentication simple 123456
[Device-radius-rscheme] key accounting simple 123456
[Device-radius-rscheme] user-name-format without-domain
[Device-radius-rscheme] quit
# 配置用户组group1,授权给该用户组的策略组为pgroup。
[Device] user-group group1
[Device-ugroup-group1] authorization-attribute sslvpn-policy-group pgroup
[Device-ugroup-group1] quit
# 配置ISP域domain1,指定用户授权属性为用户组group1,认证、授权和计费使用的RADIUS方案为rscheme。
[Device] domain domain1
[Device-isp-domain1] authorization-attribute user-group group1
[Device-isp-domain1] authentication sslvpn radius-scheme rscheme
[Device-isp-domain1] authorization sslvpn radius-scheme rscheme
[Device-isp-domain1] accounting sslvpn radius-scheme rscheme
[Device-isp-domain1] quit
4. 验证配置
# 在Device上查看SSL VPN网关状态,可见SSL VPN网关gw处于Up状态。
[Device] display sslvpn gateway
Gateway name: gw
Operation status: Up
IP: 1.1.1.2 port: 2000
SSL server-policy: ssl
Front VPN-instance not configured
# 在Device上查看SSL VPN访问实例状态,可见SSL VPN访问实例ctx处于Up状态。
[Device] display sslvpn context
Context name: ctx
Operation status: Up
AAA domain: domain1
Certificate authentication: Disabled
Dynamic password: Disabled
Verify code validation: Disabled
Default policy group not configured
Associated SSL VPN gateway: gw
Domain name and virtual host not configured
Maximum users allowed: 1048575
VPN-instance: VPN1
Idle timeout: 30 min
# 用户在PC上启动IP接入客户端软件,输入访问地址1.1.1.2、端口号2000、用户名h3c、密码123456,登录成功。
# 在Device上可以看到用户会话信息。
[Device] display sslvpn session context ctx
SSL VPN context: ctx
User: 1
Username User IP address Connections Idle Time Created
h3c 40.1.1.1 6 00:02:05 00:03:14
# 在PC上查看IPv4路由表,其中40.1.1.1/24为本地网卡地址,10.1.1.1/24为SSL VPN网关设备分配给用户的地址,20.2.2.0/24为到达内部服务器Server的路由。
>route -4 print
IPv4 Route Table
===========================================================================
Active Routes:
Network Destination Netmask Gateway Interface Metric
10.1.1.0 255.255.255.0 On-link 10.1.1.1 276
10.1.1.1 255.255.255.255 On-link 10.1.1.1 276
10.1.1.255 255.255.255.255 On-link 10.1.1.1 276
20.2.2.0 255.255.255.0 On-link 10.1.1.1 276
20.2.2.255 255.255.255.255 On-link 10.1.1.1 276
40.1.1.0 255.255.255.0 On-link 40.1.1.1 276
40.1.1.1 255.255.255.255 On-link 40.1.1.1 276
40.1.1.255 255.255.255.255 On-link 40.1.1.1 276
===========================================================================
# 在PC上可以Ping通服务器地址20.2.2.2。
>ping 20.2.2.2
Pinging 20.2.2.2 with 32 bytes of data:
Reply from 20.2.2.2: bytes=32 time=197ms TTL=254
Reply from 20.2.2.2: bytes=32 time=1ms TTL=254
Reply from 20.2.2.2: bytes=32 time=1ms TTL=254
Reply from 20.2.2.2: bytes=32 time=186ms TTL=254
Ping statistics for 20.2.2.2:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 1ms, Maximum = 197ms, Average = 96ms
- 2018-09-12回答
- 评论(0)
- 举报
-
(0)


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明

暂无评论