
问题描述:
S5120交换机的配置:1/0/24端口配置为TRUNK,允许VLAN2 VLAN4,1~12口划入VLAN2,13~23口划入VLAN4,交换机上无其它任何配置.
MSR2600路由器的配置如下,现在PC1连接S5120的GE1/0/1端口,获得192.168.2.X的地址等,可以正常上网,但一把,路由器的GE0/2(绑定的Dialer12)的网线断开,PC1就打不开网页了,在PC1上ping 202.96.64.68 -t(此地址为本地联通DNS,正常上网的终端都可以持续ping通)经常性丢包,通3断1,通1断1等
MSR2600的配置
#
version 5.20, Release 2516P17
#
sysname H3C
#
clock timezone UTC add 08:00:00
#
domain default enable system
#
dns proxy enable
#
telnet server enable
#
dar p2p signature-file flash:/p2p_default.mtd
#
ndp enable
#
ntdp enable
#
cluster enable
#
port-security enable
#
password-recovery enable
#
acl number 3002
rule 0 permit ip source 192.168.2.0 0.0.0.255
acl number 3004
rule 0 permit ip source 192.168.4.0 0.0.0.255
acl number 3008
rule 0 permit ip source 192.168.8.0 0.0.0.255
acl number 3016
rule 0 permit ip source 192.168.16.0 0.0.0.255
#
vlan 1
#
domain system
access-limit disable
state active
idle-cut disable
self-service-url disable
#
dhcp server ip-pool vlan1 extended
network ip range 192.168.1.2 192.168.1.254
network mask 255.255.255.0
forbidden-ip 192.168.1.23
gateway-list 192.168.1.1
dns-list 202.96.64.68 202.96.69.38
#
dhcp server ip-pool vlan16 extended
network ip range 192.168.16.2 192.168.16.200
network mask 255.255.255.0
gateway-list 192.168.16.1
dns-list 202.96.64.68
#
dhcp server ip-pool vlan2 extended
network ip range 192.168.2.2 192.168.2.200
network mask 255.255.255.0
gateway-list 192.168.2.1
dns-list 202.96.64.68 202.96.69.38
#
dhcp server ip-pool vlan4 extended
network ip range 192.168.4.2 192.168.4.200
network mask 255.255.255.0
gateway-list 192.168.4.1
dns-list 202.96.64.68 202.96.69.38
#
dhcp server ip-pool vlan8 extended
network ip range 192.168.8.2 192.168.8.200
network mask 255.255.255.0
gateway-list 192.168.8.1
dns-list 202.96.64.68 202.96.69.38
#
policy-based-route CNC permit node 1
if-match acl 3002
apply output-interface Dialer12
policy-based-route CNC permit node 2
if-match acl 3004
apply output-interface Dialer13
policy-based-route CNC permit node 3
if-match acl 3008
apply output-interface Dialer10
policy-based-route CNC permit node 4
if-match acl 3016
apply output-interface Dialer11
#
user-group system
group-attribute allow-guest
#
local-user admin
password cipher $c$3$Q58BrJ76zoVGiUYjcVsGhI3MCYwuXa8T5ljM
authorization-attribute level 3
service-type telnet
service-type web
local-user mars
password cipher $c$3$P0Xhf1w1RsVmdWCHuzKH/J4yWpZJTs3ms+5K
authorization-attribute level 3
service-type telnet terminal
service-type web
#
cwmp
undo cwmp enable
#
interface Aux0
async mode flow
link-protocol ppp
#
interface Cellular0/0
async mode protocol
link-protocol ppp
tcp mss 1024
#
interface Dialer10
nat outbound
link-protocol ppp
ppp chap user syl_06768035
ppp chap password cipher $c$3$NlCAvWpbfDmglf8j03pabnI2lAJUxvxXiw==
ppp pap local-user syl_06768035 password cipher $c$3$nSdTGqySqfD2E0jvz6frOAWhI55ratg5dg==
ppp ipcp dns admit-any
ppp ipcp dns request
mtu 1492
ip address ppp-negotiate
tcp mss 1024
dialer user username
dialer-group 10
dialer bundle 10
#
interface Dialer11
nat outbound
link-protocol ppp
ppp chap user syl_02410509361
ppp chap password cipher $c$3$GPrOJgGJv4pIIyFmolBjZ/ikLAoioA6QfA==
ppp pap local-user syl_02410509361 password cipher $c$3$hARSFmuvtkW7TSaRWqEBdc6GexkIABfHvg==
ppp ipcp dns admit-any
ppp ipcp dns request
mtu 1492
ip address ppp-negotiate
tcp mss 1024
dialer user username
dialer-group 11
dialer bundle 11
#
interface Dialer12
nat outbound
link-protocol ppp
ppp chap user syl_06761271
ppp chap password cipher $c$3$TjVs71oFIG1HhP0UNQ0SH8NY79kf+TSutg==
ppp pap local-user syl_06761271 password cipher $c$3$y82JE/MyLo2TS51dTez8c/rLSjT2qbdLTQ==
ppp ipcp dns admit-any
ppp ipcp dns request
mtu 1492
ip address ppp-negotiate
tcp mss 1024
dialer user username
dialer-group 12
dialer bundle 12
#
interface Dialer13
nat outbound
link-protocol ppp
ppp chap user syl_02410509357
ppp chap password cipher $c$3$xM07Y/IjPmqfTm8Mfu9h/SPLH1kl/wy+rw==
ppp pap local-user syl_02410509357 password cipher $c$3$IGDeupY1bBbIQvOd4JuMOqLGDoBTgkhOng==
ppp ipcp dns admit-any
ppp ipcp dns request
mtu 1492
ip address ppp-negotiate
tcp mss 1024
dialer user username
dialer-group 13
dialer bundle 13
#
interface NULL0
#
interface Vlan-interface1
ip address 192.168.1.1 255.255.255.0
tcp mss 1024
dhcp server apply ip-pool vlan1
#
interface GigabitEthernet0/0
port link-mode route
nat outbound
pppoe-client dial-bundle-number 10
#
interface GigabitEthernet0/1
port link-mode route
nat outbound
pppoe-client dial-bundle-number 11
#
interface GigabitEthernet0/2
port link-mode route
nat outbound
pppoe-client dial-bundle-number 12
#
interface GigabitEthernet0/3
port link-mode route
nat outbound
pppoe-client dial-bundle-number 13
#
interface GigabitEthernet0/4
port link-mode route
#
interface GigabitEthernet0/4.2
vlan-type dot1q vid 2
ip address 192.168.2.1 255.255.255.0
dhcp server apply ip-pool vlan2
ip policy-based-route CNC
#
interface GigabitEthernet0/4.4
vlan-type dot1q vid 4
ip address 192.168.4.1 255.255.255.0
dhcp server apply ip-pool vlan4
ip policy-based-route CNC
#
interface GigabitEthernet0/5
port link-mode route
#
interface GigabitEthernet0/5.8
vlan-type dot1q vid 8
ip address 192.168.8.1 255.255.255.0
dhcp server apply ip-pool vlan8
ip policy-based-route CNC
#
interface GigabitEthernet0/5.16
vlan-type dot1q vid 16
ip address 192.168.16.1 255.255.255.0
dhcp server apply ip-pool vlan16
ip policy-based-route CNC
#
interface GigabitEthernet0/6
port link-mode bridge
#
interface GigabitEthernet0/7
port link-mode bridge
#
interface GigabitEthernet0/8
port link-mode bridge
#
interface GigabitEthernet0/9
port link-mode bridge
#
ip route-static 0.0.0.0 0.0.0.0 Dialer10
ip route-static 0.0.0.0 0.0.0.0 Dialer11
ip route-static 0.0.0.0 0.0.0.0 Dialer12
ip route-static 0.0.0.0 0.0.0.0 Dialer13
#
dhcp enable
#
ntp-service unicast-server 202.112.29.82
#
dialer-rule 10 ip permit
dialer-rule 11 ip permit
dialer-rule 12 ip permit
dialer-rule 13 ip permit
#
nms primary monitor-interface Dialer11
#
load xml-configuration
#
load tr069-configuration
#
user-interface tty 12
user-interface aux 0
user-interface vty 0 4
authentication-mode scheme
#
return
自己又用MSR930 两条外网的情况下,一台PC做测试,MSR930与S5100-24交换机做同样的配置测试就没有问题,
不同之处只在于MSR2600连4条外网,S5120交换机每个VLAN下连接了10台FAT AP,和12台网络机顶盒(机顶盒通过WIFI与AP相连或网线连接面板型AP上的网口)
MSR930的配置 :
#
version 5.20, Release 2516P17
#
sysname H3C
#
domain default enable system
#
dns proxy enable
#
telnet server enable
#
dar p2p signature-file flash:/p2p_default.mtd
#
ndp enable
#
ntdp enable
#
cluster enable
#
port-security enable
#
password-recovery enable
#
acl number 3010
rule 0 permit ip source 192.168.10.0 0.0.0.255
acl number 3020
rule 0 permit ip source 192.168.20.0 0.0.0.255
#
vlan 1
#
domain system
access-limit disable
state active
idle-cut disable
self-service-url disable
#
dhcp server ip-pool vlan1 extended
network ip range 192.168.1.2 192.168.1.254
network mask 255.255.255.0
gateway-list 192.168.1.1
dns-list 192.168.1.1
#
dhcp server ip-pool vlan10 extended
network ip range 192.168.10.2 192.168.10.100
network mask 255.255.255.0
gateway-list 192.168.10.1
dns-list 202.96.64.68
#
dhcp server ip-pool vlan20 extended
network ip range 192.168.20.2 192.168.20.100
network mask 255.255.255.0
gateway-list 192.168.20.1
dns-list 202.96.64.68
#
policy-based-route cnc permit node 1
if-match acl 3010
apply ip-address next-hop 192.168.88.1
policy-based-route cnc permit node 2
if-match acl 3020
apply output-interface Dialer11
#
user-group system
group-attribute allow-guest
#
local-user admin
password cipher $c$3$40gC1cxf/wIJNa1ufFPJsjKAof+QP5aV
authorization-attribute level 3
service-type telnet
service-type web
#
cwmp
undo cwmp enable
#
interface Aux0
async mode flow
link-protocol ppp
#
interface Cellular0/0
async mode protocol
link-protocol ppp
tcp mss 1024
#
interface Dialer11
nat outbound
link-protocol ppp
ppp chap user sy_23967839
ppp chap password cipher $c$3$GcfQmTfbwClfK0rCzInyQSGmCRsC0oIodKM5
ppp pap local-user sy_23967839 password cipher $c$3$TZSy1CJ6QfJ6P+qrSQUhb3sys77HyhYHbd5S
ppp ipcp dns admit-any
ppp ipcp dns request
mtu 1492
ip address ppp-negotiate
tcp mss 1024
dialer user username
dialer-group 11
dialer bundle 11
#
interface NULL0
#
interface Vlan-interface1
ip address 192.168.1.1 255.255.255.0
tcp mss 1024
dhcp server apply ip-pool vlan1
#
interface GigabitEthernet0/0
port link-mode route
nat outbound
ip address 192.168.88.210 255.255.255.0
#
interface GigabitEthernet0/1
port link-mode route
nat outbound
pppoe-client dial-bundle-number 11
#
interface GigabitEthernet0/4
port link-mode route
#
interface GigabitEthernet0/4.10
vlan-type dot1q vid 10
ip address 192.168.10.1 255.255.255.0
dhcp server apply ip-pool vlan10
ip policy-based-route cnc
#
interface GigabitEthernet0/4.20
vlan-type dot1q vid 20
ip address 192.168.20.1 255.255.255.0
dhcp server apply ip-pool vlan20
ip policy-based-route cnc
#
interface GigabitEthernet0/2
port link-mode bridge
#
interface GigabitEthernet0/3
port link-mode bridge
#
ip route-static 0.0.0.0 0.0.0.0 Dialer11
ip route-static 0.0.0.0 0.0.0.0 GigabitEthernet0/0 192.168.88.1
#
dhcp enable
#
dialer-rule 11 ip permit
#
nms primary monitor-interface GigabitEthernet0/0
#
load xml-configuration
#
load tr069-configuration
#
user-interface tty 12
user-interface aux 0
user-interface vty 0 4
authentication-mode scheme
#
return
组网及组网描述:
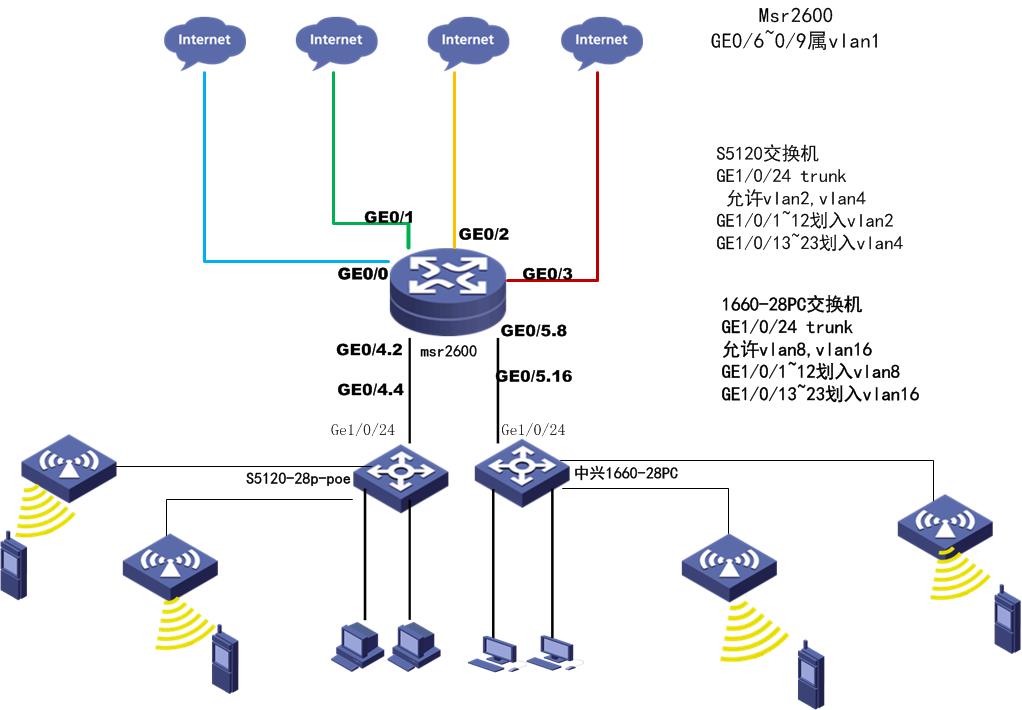
- 2018-09-18提问
- 举报
-
(0)


PC1连接S5120 1/0/1端口,IP自动获取,获得的是192.168.2.2的IP,子网255.255.255.0网关192.168.2.1,dns202.96.64.68
- 2018-09-18回答
- 评论(1)
- 举报
-
(0)
建议在交换机与路由器互联口抓包,看一下报文丢在哪里,配置没看出来什么异常
建议在交换机与路由器互联口抓包,看一下报文丢在哪里,配置没看出来什么异常
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明

