防火墙配置翻译问题
- 0关注
- 0收藏,1755浏览
问题描述:
原设备是思科的,现在换成华三了。麻烦大神给翻译翻译配置,感谢!
hostname SACI-BW
domain-name ***.***
enable password $sha512$5000$22xaCQZ+yChuLdgNpSxblg==$PcwUbzm4aC+H3u6A6Pp6LQ== pbkdf2
names
!
interface GigabitEthernet0/0
description out to internet
nameif outside
security-level 0
ip address 61.161.244.6 255.255.255.252
!
interface GigabitEthernet0/1
description Internal network
nameif inside
security-level 100
ip address 172.29.28.1 255.255.255.0
!
interface GigabitEthernet0/2
nameif OUTSIDE_20
security-level 0
ip address 218.61.160.62 255.255.255.0
!
interface GigabitEthernet0/3
nameif INSIDE_20
security-level 100
ip address 172.29.29.1 255.255.255.0
!
interface GigabitEthernet0/4
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/5
shutdown
no nameif
no security-level
no ip address
!
interface Management0/0
management-only
nameif management
security-level 100
ip address 192.168.1.1 255.255.255.0
!
boot system disk0:/asa982-smp-k8.bin
ftp mode passive
dns server-group DefaultDNS
domain-name ***.***
object network obj_172.29.28
subnet 172.29.28.0 255.255.255.0
object network ChatsMain
host 12.216.160.170
object network NewMain
subnet 172.29.34.0 255.255.254.0
description New main office
object network NewMain14
subnet 172.29.14.0 255.255.254.0
object network SAP
subnet 10.79.145.0 255.255.255.0
object network 172.29.29
subnet 172.29.29.0 255.255.255.0
object network 218.61.160.62
host 218.61.160.62
object network huake
subnet 172.29.14.0 255.255.254.0
object network huake1
subnet 10.79.145.0 255.255.255.0
object network huake2
subnet 172.29.34.0 255.255.254.0
object-group network Mainsite
network-object 172.29.12.0 255.255.255.0
network-object 172.29.13.0 255.255.255.0
object-group network DM_INLINE_NETWORK_1
network-object object NewMain
network-object object NewMain14
network-object object SAP
access-list outside_vpn extended permit ip object obj_172.29.28 object-group Mainsite
access-list outside_cryptomap extended permit ip object obj_172.29.28 object-group DM_INLINE_NETWORK_1
access-list outside_cryptomap extended permit ip object 172.29.29 object-group DM_INLINE_NETWORK_1
access-list huake extended permit ip 172.29.29.0 255.255.255.0 10.79.145.0 255.255.255.0
access-list huake extended permit ip 172.29.29.0 255.255.255.0 172.29.14.0 255.255.254.0
access-list huake extended permit ip 172.29.29.0 255.255.255.0 172.29.34.0 255.255.254.0
access-list outside_20_in extended permit ip host 103.39.231.116 any
access-list inside_20_in extended permit ip any any
pager lines 24
logging enable
logging console emergencies
logging buffered debugging
logging asdm informational
mtu outside 1500
mtu inside 1500
mtu OUTSIDE_20 1500
mtu INSIDE_20 1500
mtu management 1500
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-782.bin
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
arp rate-limit 8192
nat (INSIDE_20,OUTSIDE_20) source static 172.29.29 172.29.29 destination static huake huake
nat (INSIDE_20,OUTSIDE_20) source static 172.29.29 172.29.29 destination static huake1 huake1
nat (INSIDE_20,OUTSIDE_20) source static 172.29.29 172.29.29 destination static huake2 huake2
!
object network 172.29.29
nat (INSIDE_20,OUTSIDE_20) dynamic interface
access-group outside_20_in in interface OUTSIDE_20
access-group inside_20_in in interface INSIDE_20
route OUTSIDE_20 0.0.0.0 0.0.0.0 218.61.160.61 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
timeout conn-holddown 0:00:15
timeout igp stale-route 0:01:10
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
aaa authentication telnet console LOCAL
aaa authentication login-history
http server enable
http 192.168.1.0 255.255.255.0 management
http 172.29.0.0 255.255.0.0 inside
no snmp-server location
no snmp-server contact
crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set huake esp-des esp-md5-hmac
crypto ipsec ikev2 ipsec-proposal AES256
protocol esp encryption aes-256
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES192
protocol esp encryption aes-192
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES
protocol esp encryption aes
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal 3DES
protocol esp encryption 3des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal DES
protocol esp encryption des
protocol esp integrity sha-1 md5
crypto ipsec security-association pmtu-aging infinite
crypto map outside_map 1 match address outside_vpn
crypto map outside_map 1 set peer 12.216.160.170
crypto map outside_map 1 set ikev1 transform-set ESP-3DES-SHA
crypto map outside_map 2 match address outside_cryptomap
crypto map outside_map 2 set peer 98.152.163.18
crypto map outside_map 2 set ikev1 transform-set ESP-3DES-SHA
crypto map outside_map interface outside
crypto map huake 10 match address huake
crypto map huake 10 set peer 103.39.231.116
crypto map huake 10 set ikev1 transform-set huake
crypto map huake interface OUTSIDE_20
crypto ca trustpool policy
crypto ikev2 policy 1
encryption aes-256
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 10
encryption aes-192
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 20
encryption aes
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 30
encryption 3des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 40
encryption des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 enable outside
crypto ikev2 enable OUTSIDE_20
crypto ikev1 enable outside
crypto ikev1 enable OUTSIDE_20
crypto ikev1 policy 10
authentication pre-share
encryption des
hash md5
group 2
lifetime 86400
crypto ikev1 policy 20
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
telnet 172.29.29.0 255.255.255.0 INSIDE_20
telnet timeout 5
no ssh stricthostkeycheck
ssh 12.216.160.170 255.255.255.255 outside
ssh 98.152.163.18 255.255.255.255 outside
ssh 0.0.0.0 0.0.0.0 INSIDE_20
ssh timeout 5
ssh version 2
ssh key-exchange group dh-group1-sha1
console timeout 0
management-access inside
dhcpd address 172.29.28.150-172.29.28.181 inside
dhcpd dns 202.96.64.68 221.11.1.67 interface inside
dhcpd domain ***.*** interface inside
dhcpd enable inside
!
dhcpd address 172.29.29.120-172.29.29.150 INSIDE_20
dhcpd dns 202.96.64.68 interface INSIDE_20
dhcpd enable INSIDE_20
!
dhcpd address 192.168.1.2-192.168.1.254 management
dhcpd enable management
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
ssl cipher default custom "RC4-SHA:AES128-SHA:AES256-SHA:DES-CBC3-SHA"
ssl cipher tlsv1 custom "RC4-SHA:AES128-SHA:AES256-SHA:DES-CBC3-SHA"
ssl cipher tlsv1.1 low
ssl cipher tlsv1.2 low
ssl cipher dtlsv1 custom "RC4-SHA:AES128-SHA:AES256-SHA:DES-CBC3-SHA"
group-policy 12.216.160.170 internal
group-policy 12.216.160.170 attributes
vpn-idle-timeout none
group-policy GroupPolicy_98.152.163.18 internal
group-policy GroupPolicy_98.152.163.18 attributes
vpn-tunnel-protocol ikev1
dynamic-access-policy-record DfltAccessPolicy
username Saci password $sha512$5000$0dpIA9dWapIaNyAwfkGatw==$W6zLrO405QA2KyGHqkZupw== pbkdf2 privilege 15
username Align password $sha512$5000$epSdITezs1Tj5/Pm8IH6GQ==$hmI3kb3dCqjXBlO084CIDg== pbkdf2 privilege 15
tunnel-group 12.216.160.170 type ipsec-l2l
tunnel-group 12.216.160.170 general-attributes
default-group-policy 12.216.160.170
tunnel-group 12.216.160.170 ipsec-attributes
ikev1 pre-shared-key *****
tunnel-group 98.152.163.18 type ipsec-l2l
tunnel-group 98.152.163.18 general-attributes
default-group-policy GroupPolicy_98.152.163.18
tunnel-group 98.152.163.18 ipsec-attributes
ikev1 pre-shared-key *****
ikev2 remote-authentication pre-shared-key *****
ikev2 local-authentication pre-shared-key *****
tunnel-group 103.39.231.116 type ipsec-l2l
tunnel-group 103.39.231.116 ipsec-attributes
ikev1 pre-shared-key *****
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
tcp-inspection
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
inspect icmp
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
call-home
profile CiscoTAC-1
no active
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination address email callhome@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
Cryptochecksum:89f8e59ea8214d8ac33f0fd92c0c7c41
: end
组网及组网描述:
- 2022-10-24提问
- 举报
-
(0)

标杆神器转一下吧
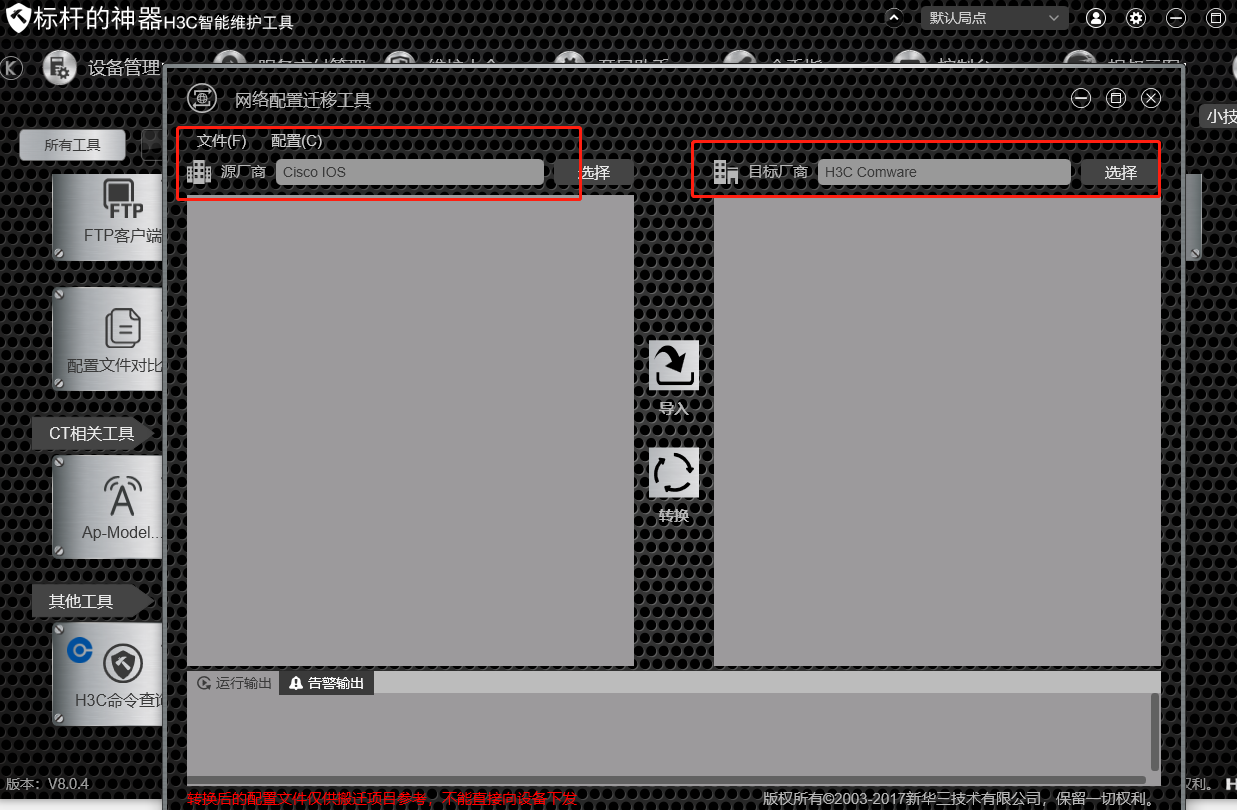
- 2022-10-24回答
- 评论(2)
- 举报
-
(0)
这个工具哪里下载?
https://www.h3c.com/cn/Service/Document_Software/Software_Download/Other_Product/H3C_Software/BG/BG/?CHID=190669&v=612
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明

https://www.h3c.com/cn/Service/Document_Software/Software_Download/Other_Product/H3C_Software/BG/BG/?CHID=190669&v=612