请教F1000-AK125防火墙做的端口映射,在主口有数据,出口没数据,如何配置解决
- 0关注
- 1收藏,2644浏览
问题描述:
请教SecPath F1000-AK125防火墙做的端口映射,在主口可以抓到数据,到了出口抓不到数据了请教SecPath F1000-AK125防火墙做的端口映射,在外网入主口可以抓到数据,到了出口抓不到数据了,如何配置解决,监控平台使用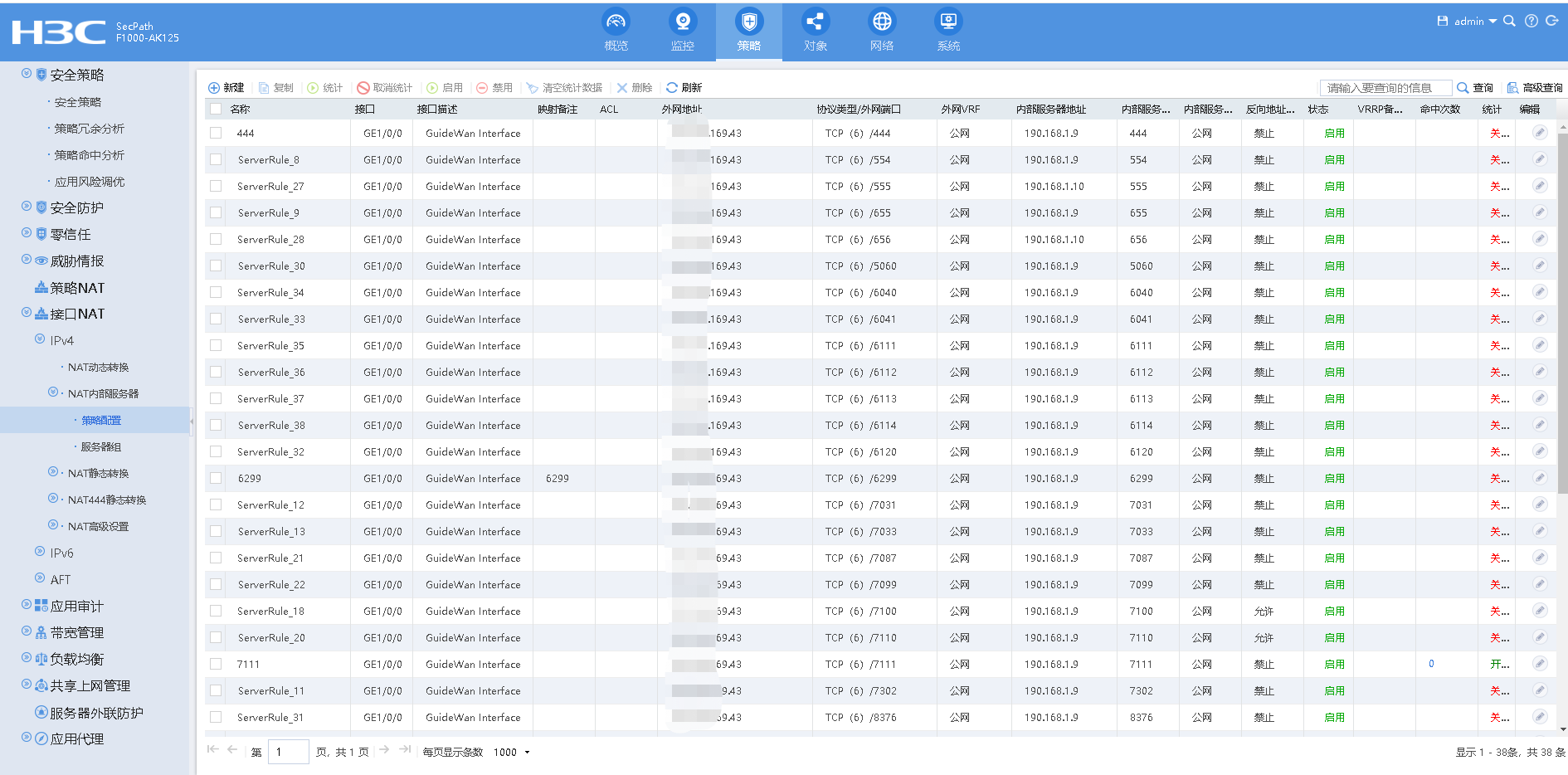
组网及组网描述:
#
version 7.1.064, Release xxxxxxx
#
sysname H3C
#
context Admin id 1
#
irf mac-address persistent timer
irf auto-update enable
undo irf link-delay
irf member 1 priority 1
#
dhcp enable
#
dns server 8.8.8.8
#
password-recovery enable
#
vlan 1
#
dhcp server ip-pool 22
gateway-list 192.168.1.1
network 192.168.1.0 mask 255.255.255.0
dns-list 192.168.1.1
expired unlimited
#
dhcp server ip-pool 111
gateway-list 190.168.1.1
network 190.168.1.0 mask 255.255.255.0
dns-list 218.201.96.130 211.137.191.26
expired unlimited
#
dhcp server ip-pool GuideSecDHCPPool
network 191.168.1.0 mask 255.255.255.0
#
controller Cellular1/0/0
#
controller Cellular1/0/1
#
interface NULL0
#
interface Vlan-interface1
#
interface GigabitEthernet1/0/0
port link-mode route
description GuideWan Interface
bandwidth 600000
combo enable copper
ip address xxx.xxx.169.43 255.255.255.0
dns server 211.137.191.26
dns server 218.201.96.130
ip last-hop hold
nat server protocol tcp global xxx.xxx.169.43 444 inside 190.168.1.9 444 rule 444
nat server protocol tcp global xxx.xxx.169.43 554 inside 190.168.1.9 554 rule ServerRule_8
nat server protocol tcp global xxx.xxx.169.43 555 inside 190.168.1.10 555 rule ServerRule_27
nat server protocol tcp global xxx.xxx.169.43 655 inside 190.168.1.9 655 rule ServerRule_9
nat server protocol tcp global xxx.xxx.169.43 656 inside 190.168.1.10 656 rule ServerRule_28
nat server protocol tcp global xxx.xxx.169.43 5060 inside 190.168.1.9 5060 rule ServerRule_30
nat server protocol tcp global xxx.xxx.169.43 6040 inside 190.168.1.9 6040 rule ServerRule_34
nat server protocol tcp global xxx.xxx.169.43 6041 inside 190.168.1.9 6041 rule ServerRule_33
nat server protocol tcp global xxx.xxx.169.43 6111 inside 190.168.1.9 6111 rule ServerRule_35
nat server protocol tcp global xxx.xxx.169.43 6112 inside 190.168.1.9 6112 rule ServerRule_36
nat server protocol tcp global xxx.xxx.169.43 6113 inside 190.168.1.9 6113 rule ServerRule_37
nat server protocol tcp global xxx.xxx.169.43 6114 inside 190.168.1.9 6114 rule ServerRule_38
nat server protocol tcp global xxx.xxx.169.43 6120 inside 190.168.1.9 6120 rule ServerRule_32
nat server protocol tcp global xxx.xxx.169.43 6299 inside 190.168.1.9 6299 rule 6299 description 6299
nat server protocol tcp global xxx.xxx.169.43 7031 inside 190.168.1.9 7031 rule ServerRule_12
nat server protocol tcp global xxx.xxx.169.43 7033 inside 190.168.1.9 7033 rule ServerRule_13
nat server protocol tcp global xxx.xxx.169.43 7087 inside 190.168.1.9 7087 rule ServerRule_21
nat server protocol tcp global xxx.xxx.169.43 7099 inside 190.168.1.9 7099 rule ServerRule_22
nat server protocol tcp global xxx.xxx.169.43 7100 inside 190.168.1.9 7100 reversible rule ServerRule_18
nat server protocol tcp global xxx.xxx.169.43 7110 inside 190.168.1.9 7110 reversible rule ServerRule_20
nat server protocol tcp global xxx.xxx.169.43 7111 inside 190.168.1.9 7111 rule 7111 counting
nat server protocol tcp global xxx.xxx.169.43 7302 inside 190.168.1.9 7302 rule ServerRule_11
nat server protocol tcp global xxx.xxx.169.43 8376 inside 190.168.1.9 8376 rule ServerRule_31
nat server protocol tcp global xxx.xxx.169.43 9308 inside 190.168.1.10 9308 rule ServerRule_17
nat server protocol tcp global xxx.xxx.169.43 9503 inside 190.168.1.9 9503 rule ServerRule_29
nat server protocol tcp global xxx.xxx.169.43 15000 16999 inside 190.168.1.9 15000 16999 rule ServerRule_15
nat server protocol tcp global xxx.xxx.169.43 17000 inside 190.168.1.9 17000 rule ServerRule_14
nat server protocol tcp global xxx.xxx.169.43 26100 26899 inside 190.168.1.9 26100 26899 rule ServerRule_23
nat server protocol tcp global xxx.xxx.169.43 55555 inside 192.168.1.9 55555 rule ServerRule_40 description 55555
nat server protocol tcp global xxx.xxx.169.43 55556 inside 190.168.1.10 55555 rule ServerRule_41 description 55556
nat server protocol udp global xxx.xxx.169.43 123 inside 190.168.1.9 123 rule ServerRule_25
nat server protocol udp global xxx.xxx.169.43 6304 inside 190.168.1.9 6304 rule ServerRule_7
nat server protocol udp global xxx.xxx.169.43 7100 inside 190.168.1.9 7100 reversible rule ServerRule_19
nat server protocol udp global xxx.xxx.169.43 7111 inside 190.168.1.9 7111 reversible rule 7111udp description 7111udp
nat server protocol udp global xxx.xxx.169.43 7660 inside 190.168.1.9 7660 rule ServerRule_10
nat server protocol udp global xxx.xxx.169.43 8374 inside 190.168.1.9 8374 rule ServerRule_39
nat server protocol udp global xxx.xxx.169.43 15000 16999 inside 190.168.1.9 15000 16999 rule ServerRule_16
nat server protocol udp global xxx.xxx.169.43 26100 26899 inside 190.168.1.9 26100 26899 rule ServerRule_24
nat static enable
manage http inbound
manage http outbound
manage https inbound
manage https outbound
manage ssh inbound
manage ssh outbound
manage telnet inbound
manage telnet outbound
gateway xxx.xxx.169.1
#
interface GigabitEthernet1/0/1
port link-mode route
combo enable copper
ip address dhcp-alloc
ip last-hop hold
#
interface GigabitEthernet1/0/2
port link-mode route
ip address 192.168.1.1 255.255.255.0
#
interface GigabitEthernet1/0/3
port link-mode route
#
interface GigabitEthernet1/0/4
port link-mode route
#
interface GigabitEthernet1/0/5
port link-mode route
#
interface GigabitEthernet1/0/6
port link-mode route
#
interface GigabitEthernet1/0/7
port link-mode route
#
interface GigabitEthernet1/0/8
port link-mode route
#
interface GigabitEthernet1/0/9
port link-mode route
#
interface GigabitEthernet1/0/10
port link-mode route
#
interface GigabitEthernet1/0/11
port link-mode route
ip address 190.168.1.1 255.255.255.0
nat static enable
manage http inbound
manage http outbound
manage https inbound
manage https outbound
manage ping inbound
manage ping outbound
manage ssh inbound
manage ssh outbound
manage telnet inbound
manage telnet outbound
gateway 190.168.1.1
#
security-zone name Local
#
security-zone name Trust
import interface GigabitEthernet1/0/1
import interface GigabitEthernet1/0/4
import interface GigabitEthernet1/0/10
import interface GigabitEthernet1/0/11
#
security-zone name DMZ
#
security-zone name Untrust
import interface GigabitEthernet1/0/0
#
security-zone name Management
import interface GigabitEthernet1/0/2
#
scheduler logfile size 16
#
line class aux
user-role network-operator
#
line class console
authentication-mode scheme
user-role network-admin
#
line class vty
user-role network-operator
#
line aux 0
user-role network-admin
#
line con 0
user-role network-admin
#
line vty 0 63
authentication-mode scheme
user-role network-admin
#
ip route-static 0.0.0.0 24 GigabitEthernet1/0/0 xxx.xxx.169.1
#
performance-management
#
ssh server enable
#
domain system
#
domain default enable system
#
role name level-0
description Predefined level-0 role
#
role name level-1
description Predefined level-1 role
#
role name level-2
description Predefined level-2 role
#
role name level-3
description Predefined level-3 role
#
role name level-4
description Predefined level-4 role
#
role name level-5
description Predefined level-5 role
#
role name level-6
description Predefined level-6 role
#
role name level-7
description Predefined level-7 role
#
role name level-8
description Predefined level-8 role
#
role name level-9
description Predefined level-9 role
#
role name level-10
description Predefined level-10 role
#
role name level-11
description Predefined level-11 role
#
role name level-12
description Predefined level-12 role
#
role name level-13
description Predefined level-13 role
#
role name level-14
description Predefined level-14 role
#
user-group system
#
local-user admin class manage
password hash $h$6$FbrX/jPSR4+BqQwf$BmfraLeo7tddZVt4b64gUPMjaEyBgEiJIzn5cYk8C5bZfY0Xy64dPGh0CN/srz0C7XH42fC6D0kxd2u08wzArw==
service-type ssh terminal https
authorization-attribute user-role level-3
authorization-attribute user-role network-admin
authorization-attribute user-role network-operator
#
ipsec logging negotiation enable
#
nat global-policy
rule name GlobalPolicyRule_4
description GuideNat
source-zone Trust
destination-zone Untrust
action snat easy-ip
#
apr signature auto-update
update schedule daily start-time 02:00:00 tingle 120
#
ike logging negotiation enable
#
ip https port 9090
ip https enable
#
url-filter signature auto-update
update schedule daily start-time 02:00:00 tingle 120
#
ips signature auto-update
update schedule daily start-time 02:00:00 tingle 120
#
inspect logging parameter-profile av_logging_default_parameter
#
inspect logging parameter-profile ips_logging_default_parameter
#
inspect email parameter-profile mailsetting_default_parameter
undo authentication enable
#
traffic-policy
rule 2 name GuideWANAccPolicy
action qos profile guidewanaccprofile
source-zone Trust
destination-zone DMZ
destination-zone Untrust
service ike
service ipsec-ah
service ipsec-esp
service l2tp
service nat-t-ipsec
rule 3 name GuideAVCPolicy
action qos profile guideavcprofile1
source-zone Trust
destination-zone DMZ
destination-zone Untrust
profile name guideavcprofile1
bandwidth downstream guaranteed 700000
bandwidth downstream maximum 700000
profile name guidewanaccprofile
bandwidth downstream guaranteed 300000
bandwidth downstream maximum 300000
#
packet-capture max-file-packets 1000
#
security-policy ip
rule 4 name GuideSecPolicy
action pass
source-zone Trust
destination-zone Untrust
destination-zone DMZ
rule 3 name Any_Any_3_IPv4
action pass
#
ips logging parameter-profile ips_logging_default_parameter
#
anti-virus signature auto-update
update schedule daily start-time 02:00:00 tingle 120
#
anti-virus logging parameter-profile av_logging_default_parameter
#
url-reputation signature auto-update
update schedule daily start-time 02:00:00 tingle 120
#
domain-reputation signature auto-update
update schedule daily start-time 02:00:00 tingle 120
#
ip-reputation signature auto-update
update schedule daily start-time 02:00:00 tingle 120
#
return
- 2023-06-07提问
- 举报
-
(0)

1.配置不全,安全策略问题无法确认
- 2023-06-07回答
- 评论(0)
- 举报
-
(0)
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明





暂无评论