VRF
- 0关注
- 0收藏,1590浏览
问题描述:
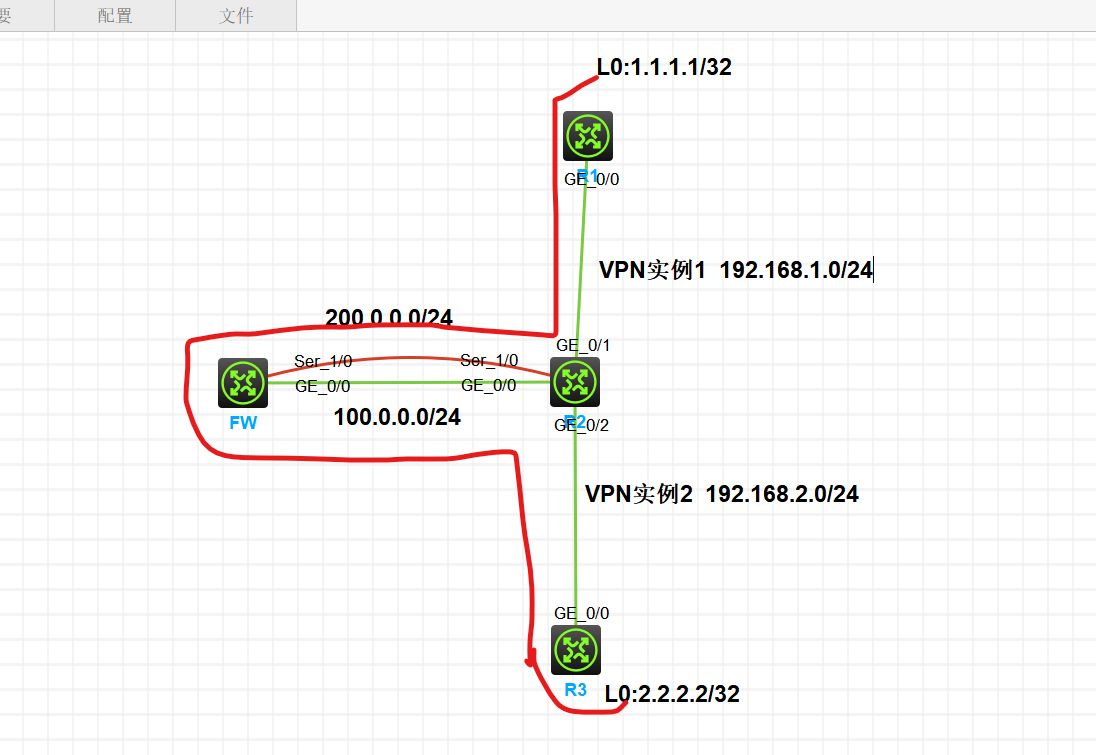
1.1.1.1网段和2.2.2.2分别属于两个vpn实例,要实现流量1.1.1.1访问2.2.2.2走红色路径,路由引入有相关案例吗
组网及组网描述:
- 2023-10-16提问
- 举报
-
(0)
最佳答案

2.2 三层直路部署SecBlade插卡(划分VRF)
2.2.1 组网需求
Host A、Host B和Host C通过接入交换机Switch、路由器Router与Internet通信。出于安全考虑,需要在路由器Router上部署SecBlade插卡Device起安全防护作用,应用需求如下:
· Switch将Host A、Host B和Host C分别划分在VLAN 10、VLAN 20和VLAN 30,透传Host与Internet之间的流量。
· Router与Host、Internet和Device三层对接,下行口和Route-Aggregation1.100划分在VPN host,上行口和Route-Aggregation1.200划分在VPN internet,查静态路由表转发Host与Internet之间的流量。
· Device与Router三层对接,查静态路由表转发Host与Internet之间的流量。
图2-2 三层直路部署SecBlade插卡(划分VRF)组网图
设备 | 接口 | IP地址 | 设备 | 接口 | IP地址 |
Host A | - | 192.168.10.15/24 | Device | RAGG1.100 | 10.1.1.2/30 |
Host B | - | 192.168.20.15/24 |
| RAGG1.200 | 10.1.1.5/30 |
Host C | - | 192.168.30.15/24 |
|
|
|
Router | GE1/0/1.10 | 192.168.10.1/24 |
|
|
|
| GE1/0/1.20 | 192.168.20.1/24 |
|
|
|
| GE1/0/1.30 | 192.168.30.1/24 |
|
|
|
| RAGG1.100 | 10.1.1.1/30 |
|
|
|
| RAGG1.200 | 10.1.1.6/30 |
|
|
|
2.2.2 配置步骤
1. 配置Switch
# 创建VLAN 10、VLAN 20和VLAN 30,将GigabitEthernet1/0/1、GigabitEthernet1/0/2和GigabitEthernet1/0/3分别加入VLAN 10、VLAN 20和VLAN 30。
<Switch> system-view
[Switch] vlan 10
[Switch-vlan10] port gigabitethernet 1/0/1
[Switch-vlan10] quit
[Switch] vlan 20
[Switch-vlan20] port gigabitethernet 1/0/2
[Switch-vlan20] quit
[Switch] vlan 30
[Switch-vlan30] port gigabitethernet 1/0/3
[Switch-vlan30] quit
# 将GigabitEthernet1/0/4的链路类型配置为Trunk,并允许VLAN 10、VLAN 20和VLAN 30的报文通过。
[Switch] interface gigabitethernet 1/0/4
[Switch-GigabitEthernet1/0/4] port link-type trunk
[Switch-GigabitEthernet1/0/4] port trunk permit vlan 10 20 30
[Switch-GigabitEthernet1/0/4] quit
2. 配置Router
# 创建VPN实例host与internet。
[Router] ip vpn-instance host
[Router-vpn-instance-host] quit
[Router] ip vpn-instance internet
[Router-vpn-instance-internet] quit
# 创建三层聚合接口1。
[Router] interface route-aggregation 1
[Router-Route-Aggregation1] quit
# 创建三层聚合子接口Route-Aggregation1.100和Route-Aggregation1.200,开启Dot1q终结功能,分别终结VLAN 100和VLAN 200,绑定VPN实例并配置接口IP。
[Router] interface route-aggregation 1.100
[Router-Route-Aggregation1.100] vlan-type dot1q vid 100
[Router-Route-Aggregation1.100] ip binding vpn-instance host
[Router-Route-Aggregation1.100] ip address 10.1.1.1 30
[Router-Route-Aggregation1.100] quit
[Router] interface route-aggregation 1.200
[Router-Route-Aggregation1.200] vlan-type dot1q vid 200
[Router-Route-Aggregation1.200] ip binding vpn-instance internet
[Router-Route-Aggregation1.200] ip address 10.1.1.6 30
[Router-Route-Aggregation1.200] quit
# 将FortyGigE2/0/1和FortyGigE2/0/2加入到聚合组1中。
[Router] interface range fortygige 2/0/1 fortygige 2/0/2
[Router-if-range] port link-aggregation group 1
[Router-if-range] quit
# 创建三层子接口GigabitEthernet1/0/1.10、GigabitEthernet1/0/1.20和GigabitEthernet1/0/1.30,开启Dot1q终结功能,分别终结VLAN 10、VLAN 20和VLAN 30,绑定VPN实例并配置接口IP。
[Router] interface gigabitethernet 1/0/1.10
[Router-GigabitEthernet1/0/1.10] vlan-type dot1q vid 10
[Router-GigabitEthernet1/0/1.10] ip binding vpn-instance host
[Router-GigabitEthernet1/0/1.10] ip address 192.168.10.1 24
[Router-GigabitEthernet1/0/1.10] quit
[Router] interface gigabitethernet 1/0/1.20
[Router-GigabitEthernet1/0/1.20] vlan-type dot1q vid 20
[Router-GigabitEthernet1/0/1.20] ip binding vpn-instance host
[Router-GigabitEthernet1/0/1.20] ip address 192.168.20.1 24
[Router-GigabitEthernet1/0/1.20] quit
[Router] interface gigabitethernet 1/0/1.30
[Router-GigabitEthernet1/0/1.30] vlan-type dot1q vid 30
[Router-GigabitEthernet1/0/1.30] ip binding vpn-instance host
[Router-GigabitEthernet1/0/1.30] ip address 192.168.30.1 24
[Router-GigabitEthernet1/0/1.30] quit
# 配置GigabitEthernet1/0/2接口IP,绑定VPN实例。
[Router] interface gigabitethernet 1/0/2
[Router-GigabitEthernet1/0/2] ip binding vpn-instance internet
[Router-GigabitEthernet1/0/2] ip address 20.1.1.1 24
[Router-GigabitEthernet1/0/2] quit
# 配置静态路由指导上下行流量转发。
[Router] ip route-static vpn-instance host 20.1.1.0 24 vpn-instance host 10.1.1.2
[Router] ip route-static vpn-instance internet 192.168.10.0 24 vpn-instance internet 10.1.1.5
[Router] ip route-static vpn-instance internet 192.168.20.0 24 vpn-instance internet 10.1.1.5
[Router] ip route-static vpn-instance internet 192.168.30.0 24 vpn-instance internet 10.1.1.5
3. 配置Device
# 创建三层聚合接口1。
<Device> system-view
[Device] interface route-aggregation 1
[Device-Route-Aggregation1] quit
# 创建三层聚合子接口Route-Aggregation1.100和Route-Aggregation1.200,开启Dot1q终结功能,分别终结VLAN 100和VLAN 200,并配置接口IP。
[Device] interface route-aggregation 1.100
[Device-Route-Aggregation1.100] vlan-type dot1q vid 100
[Device-Route-Aggregation1.100] ip address 10.1.1.2 30
[Device-Route-Aggregation1.100] quit
[Device] interface route-aggregation 1.200
[Device-Route-Aggregation1.200] vlan-type dot1q vid 200
[Device-Route-Aggregation1.200] ip address 10.1.1.5 30
[Device-Route-Aggregation1.200] quit
# 将FortyGigE1/0/1和FortyGigE1/0/2加入到聚合组1中。
[Device] interface range fortygige 1/0/1 fortygige 1/0/2
[Device-if-range] port link-aggregation group 1
[Device-if-range] quit
# 将Route-Aggregation1.100和Route-Aggregation1.200分别加入安全域Trust和Untrust中。
[Device] security-zone name trust
[Device-security-zone-Trust] import interface route-aggregation 1.100
[Device-security-zone-Trust] quit
[Device] security-zone name untrust
[Device-security-zone-Untrust] import interface route-aggregation 1.200
[Device-security-zone-Untrust] quit
# 配置安全策略允许域间报文通过。
[Device] security-policy ip
[Device-security-policy-ip] rule name trust-untrust
[Device-security-policy-ip-0-trust-untrust] action pass
[Device-security-policy-ip-0-trust-untrust] source-zone trust
[Device-security-policy-ip-0-trust-untrust] destination-zone untrust
[Device-security-policy-ip-0-trust-untrust] quit
[Device-security-policy-ip] rule name untrust-trust
[Device-security-policy-ip-1-untrust-trust] action pass
[Device-security-policy-ip-1-untrust-trust] source-zone untrust
[Device-security-policy-ip-1-untrust-trust] destination-zone trust
[Device-security-policy-ip-1-untrust-trust] quit
[Device-security-policy-ip] quit
# 配置静态路由指导上下行流量转发。
[Device] ip route-static 192.168.10.0 24 10.1.1.1
[Device] ip route-static 192.168.20.0 24 10.1.1.1
[Device] ip route-static 192.168.30.0 24 10.1.1.1
[Device] ip route-static 20.1.1.0 24 10.1.1.6
- 2023-10-16回答
- 评论(0)
- 举报
-
(0)


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明


暂无评论