机房和公司做IPSec,但是公司侧加了NAT,不知为啥, 求大神帮忙
- 0关注
- 0收藏,1192浏览
问题描述:
做了个拓扑,是公司和机房的IPSec隧道连接,在加入NAT设备前都没问题,但是加了以后,去掉了公司防火墙的NAT,也在NAT设备上做了udp500和4500的端口映射,但是还是不能同,已经折腾了好长一段时间,麻烦各路大神帮忙指点一下,是我缺了什么配置,还是在哪里写错了,或者遗漏了什么,感激不尽!以下是配置信息(模拟运营商的节点我只在两个网口分别加了两个IP来模拟公网,其他配置没做,我就不往上放了):
+++++++++++++++++++公司防火墙配置+++++++++++++++++++++
#
version 7.1.064, Alpha 7164
#
sysname H3C
#
context Admin id 1
#
telnet server enable
#
irf mac-address persistent timer
irf auto-update enable
undo irf link-delay
irf member 1 priority 1
#
dhcp enable
#
xbar load-single
password-recovery enable
lpu-type f-series
#
vlan 1
#
vlan 100
#
dhcp server ip-pool pool
gateway-list 192.168.100.1
network 192.168.100.0 mask 255.255.255.0
dns-list 114.114.114.114
#
interface NULL0
#
interface Vlan-interface100
ip address 192.168.100.1 255.255.255.0
dhcp server apply ip-pool pool
#
interface GigabitEthernet1/0/0
port link-mode route
combo enable copper
ip address 172.16.0.249 255.255.255.0
nat outbound 3000 disable
ipsec apply policy gs-ipsec-policy
#
interface GigabitEthernet1/0/1
port link-mode route
combo enable copper
ip address 192.168.0.1 255.255.255.0
#
interface GigabitEthernet1/0/2
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/3
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/4
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/5
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/6
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/7
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/8
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/9
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/10
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/11
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/12
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/13
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/14
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/15
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/16
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/17
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/18
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/19
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/20
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/21
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/22
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/23
port link-mode bridge
port access vlan 100
combo enable copper
#
security-zone name Local
#
security-zone name Trust
import interface Vlan-interface100
import interface GigabitEthernet1/0/23 vlan 100
#
security-zone name DMZ
#
security-zone name Untrust
import interface GigabitEthernet1/0/0
#
security-zone name Management
#
scheduler logfile size 16
#
line class aux
user-role network-operator
#
line class console
user-role network-admin
#
line class tty
user-role network-operator
#
line class vty
user-role network-operator
#
line aux 0
user-role network-admin
#
line con 0
authentication-mode scheme
user-role network-admin
#
line vty 0 4
authentication-mode scheme
user-role network-admin
#
line vty 5 63
user-role network-operator
#
ip route-static 0.0.0.0 0 172.16.0.254
#
info-center loghost 127.0.0.1 port 3301 format default
info-center source CFGLOG loghost level informational
#
acl advanced 3000
rule 0 deny ip source 192.168.100.0 0.0.0.255 destination 172.16.100.0 0.0.0.255
rule 10 permit ip source 192.168.100.0 0.0.0.255
#
acl advanced 3001
rule 0 permit ip source 192.168.100.0 0.0.0.255 destination 172.16.100.0 0.0.0.255
#
domain system
#
aaa session-limit ftp 16
aaa session-limit telnet 16
aaa session-limit ssh 16
domain default enable system
#
role name level-0
description Predefined level-0 role
#
role name level-1
description Predefined level-1 role
#
role name level-2
description Predefined level-2 role
#
role name level-3
description Predefined level-3 role
#
role name level-4
description Predefined level-4 role
#
role name level-5
description Predefined level-5 role
#
role name level-6
description Predefined level-6 role
#
role name level-7
description Predefined level-7 role
#
role name level-8
description Predefined level-8 role
#
role name level-9
description Predefined level-9 role
#
role name level-10
description Predefined level-10 role
#
role name level-11
description Predefined level-11 role
#
role name level-12
description Predefined level-12 role
#
role name level-13
description Predefined level-13 role
#
role name level-14
description Predefined level-14 role
#
user-group system
#
local-user admin class manage
password hash $h$6$UbIhNnPevyKUwfpm$LqR3+yg1IjNct39MkOR0H0iQXLkYB3jMqM4vbAeoXOhbabIIFnjJPEGR00YiYA1Sz4LiY3FmEdru2fOLMb1shQ==
service-type telnet terminal http
authorization-attribute user-role level-3
authorization-attribute user-role network-admin
authorization-attribute user-role network-operator
#
ipsec transform-set gs-trans
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
#
ipsec policy gs-ipsec-policy 1 isakmp
transform-set gs-trans
security acl 3001
local-address 111.111.111.2
remote-address 222.222.222.2
ike-profile gs-ike-profile
#
ike profile gs-ike-profile
keychain gs-chain
local-identity address 111.111.111.2
match remote identity address 222.222.222.2 255.255.255.255
proposal 1
#
ike proposal 1
encryption-algorithm 3des-cbc
dh group2
authentication-algorithm md5
#
ike keychain gs-keychain
pre-shared-key address 222.222.222.2 255.255.255.255 key cipher $c$3$VA+TWneUBl36Re7j3B3GWRO0Z4F5YnWpsA==
#
ip http enable
ip https enable
#
security-policy ip
rule 0 name pass
action pass
#
return
++++++++++++++++++++++++公司防火墙配置结束+++++++++++++++++++++
++++++++++++++++++++++++NAT设备配置++++++++++++++++++++
#
version 7.1.075, ESS 8305
#
sysname H3C
#
system-working-mode standard
xbar load-single
password-recovery enable
lpu-type f-series
#
vlan 1
#
interface Serial0/0/3
#
interface Serial0/0/4
#
interface Serial0/0/5
#
interface Serial0/0/6
#
interface NULL0
#
interface GigabitEthernet0/0/0
port link-mode route
combo enable copper
ip address 111.111.111.2 255.255.255.0
nat outbound 3000
nat server protocol udp global 172.16.0.249 4500 inside 111.111.111.2 4500
nat server protocol udp global 172.16.0.249 500 inside 111.111.111.2 500
#
interface GigabitEthernet0/0/1
port link-mode route
combo enable copper
#
interface GigabitEthernet0/0/2
port link-mode route
combo enable copper
#
interface GigabitEthernet0/0/7
port link-mode route
combo enable copper
#
interface GigabitEthernet0/0/8
port link-mode route
combo enable copper
#
interface GigabitEthernet0/0/9
port link-mode route
combo enable copper
#
interface GigabitEthernet0/0/10
port link-mode route
combo enable copper
ip address 172.16.0.254 255.255.255.0
#
scheduler logfile size 16
#
line class aux
user-role network-operator
#
line class console
user-role network-admin
#
line class tty
user-role network-operator
#
line class vty
user-role network-operator
#
line aux 0
user-role network-operator
#
line con 0
user-role network-admin
#
line vty 0 63
user-role network-operator
#
ip route-static 0.0.0.0 0 111.111.111.1
#
acl advanced 3000
rule 10 permit ip
#
domain name system
#
domain default enable system
#
role name level-0
description Predefined level-0 role
#
role name level-1
description Predefined level-1 role
#
role name level-10
description Predefined level-10 role
#
role name level-11
description Predefined level-11 role
#
role name level-12
description Predefined level-12 role
#
role name level-13
description Predefined level-13 role
#
role name level-14
description Predefined level-14 role
#
role name level-2
description Predefined level-2 role
#
role name level-3
description Predefined level-3 role
#
role name level-4
description Predefined level-4 role
#
role name level-5
description Predefined level-5 role
#
role name level-6
description Predefined level-6 role
#
role name level-7
description Predefined level-7 role
#
role name level-8
description Predefined level-8 role
#
role name level-9
description Predefined level-9 role
#
user-group system
#
return
+++++++++++++++++++++NAT设备配置结束+++++++++++++++++++++
++++++++++++++++++++机房防火墙配置+++++++++++++++++++++++
#
version 7.1.064, Alpha 7164
#
sysname H3C
#
context Admin id 1
#
telnet server enable
#
irf mac-address persistent timer
irf auto-update enable
undo irf link-delay
irf member 1 priority 1
#
dhcp enable
#
xbar load-single
password-recovery enable
lpu-type f-series
#
vlan 1
#
vlan 100
#
dhcp server ip-pool pool
gateway-list 172.16.100.1
network 172.16.100.0 mask 255.255.255.0
dns-list 114.114.114.114
#
interface NULL0
#
interface Vlan-interface100
ip address 172.16.100.1 255.255.255.0
dhcp server apply ip-pool pool
#
interface GigabitEthernet1/0/0
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/1
port link-mode route
combo enable copper
ip address 222.222.222.2 255.255.255.0
nat outbound 3000
ipsec apply policy jf-ipsec-policy
#
interface GigabitEthernet1/0/2
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/3
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/4
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/5
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/6
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/7
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/8
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/9
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/10
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/11
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/12
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/13
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/14
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/15
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/16
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/17
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/18
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/19
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/20
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/21
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/22
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/23
port link-mode bridge
port access vlan 100
combo enable copper
#
security-zone name Local
#
security-zone name Trust
import interface Vlan-interface100
import interface GigabitEthernet1/0/23 vlan 100
#
security-zone name DMZ
#
security-zone name Untrust
import interface GigabitEthernet1/0/1
#
security-zone name Management
#
scheduler logfile size 16
#
line class aux
user-role network-operator
#
line class console
user-role network-admin
#
line class tty
user-role network-operator
#
line class vty
user-role network-operator
#
line aux 0
user-role network-admin
#
line con 0
authentication-mode scheme
user-role network-admin
#
line vty 0 4
authentication-mode scheme
user-role network-admin
#
line vty 5 63
user-role network-operator
#
ip route-static 0.0.0.0 0 222.222.222.1
#
info-center loghost 127.0.0.1 port 3301 format default
info-center source CFGLOG loghost level informational
#
acl advanced 3000
rule 0 deny ip source 172.16.100.0 0.0.0.255 destination 192.168.100.0 0.0.0.255
rule 10 permit ip source 172.16.100.0 0.0.0.255
#
acl advanced 3001
rule 0 permit ip source 172.16.100.0 0.0.0.255 destination 192.168.100.0 0.0.0.255
#
domain system
#
aaa session-limit ftp 16
aaa session-limit telnet 16
aaa session-limit ssh 16
domain default enable system
#
role name level-0
description Predefined level-0 role
#
role name level-1
description Predefined level-1 role
#
role name level-2
description Predefined level-2 role
#
role name level-3
description Predefined level-3 role
#
role name level-4
description Predefined level-4 role
#
role name level-5
description Predefined level-5 role
#
role name level-6
description Predefined level-6 role
#
role name level-7
description Predefined level-7 role
#
role name level-8
description Predefined level-8 role
#
role name level-9
description Predefined level-9 role
#
role name level-10
description Predefined level-10 role
#
role name level-11
description Predefined level-11 role
#
role name level-12
description Predefined level-12 role
#
role name level-13
description Predefined level-13 role
#
role name level-14
description Predefined level-14 role
#
user-group system
#
local-user admin class manage
password hash $h$6$UbIhNnPevyKUwfpm$LqR3+yg1IjNct39MkOR0H0iQXLkYB3jMqM4vbAeoXOhbabIIFnjJPEGR00YiYA1Sz4LiY3FmEdru2fOLMb1shQ==
service-type telnet terminal http
authorization-attribute user-role level-3
authorization-attribute user-role network-admin
authorization-attribute user-role network-operator
#
ipsec transform-set jf-trans
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
#
ipsec policy jf-ipsec-policy 1 isakmp
transform-set jf-trans
security acl 3001
local-address 222.222.222.2
remote-address 111.111.111.2
ike-profile jf-ike-profile
#
ike profile jf-ike-profile
keychain jf-chain
local-identity address 222.222.222.2
match remote identity address 111.111.111.2 255.255.255.255
proposal 1
#
ike proposal 1
encryption-algorithm 3des-cbc
dh group2
authentication-algorithm md5
#
ike keychain jf-chain
pre-shared-key address 111.111.111.2 255.255.255.255 key cipher $c$3$G/nV+XgkXPghQ/qGuyEnZ/6SY5TJaHuwJA==
#
ip http enable
ip https enable
#
security-policy ip
rule 0 name pass
action pass
#
return
+++++++++++++++++++++机房防火墙配置++++++++++++++++++
组网及组网描述:
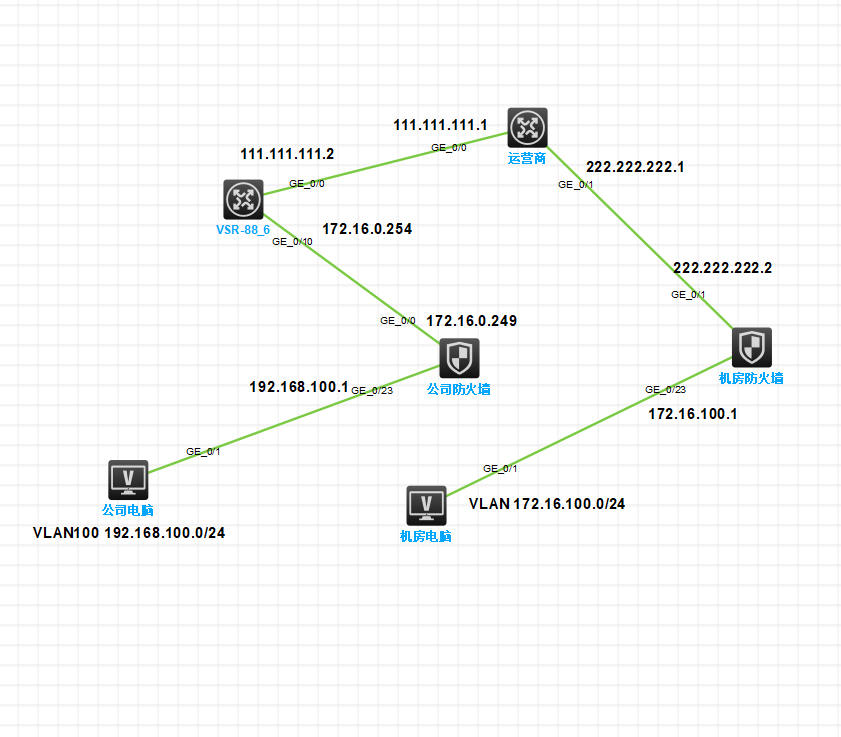
- 2023-12-15提问
- 举报
-
(0)
最佳答案


根据您的描述和图片,您的问题是关于在加入NAT设备后,公司和机房的IPSec隧道连接失败。您的公司防火墙配置了IPSec策略和NAT规则,但是没有配置NAT穿越功能。
NAT穿越功能是一种允许IPSec隧道在NAT设备之间建立的技术,它可以解决NAT设备对IPSec报文的源地址和端口的修改导致IPSec协商失败的问题。您需要在公司防火墙和机房防火墙上都启用NAT穿越功能,才能实现IPSec隧道的正常建立和通信。
您可以参考以下步骤来配置NAT穿越功能:
1. 在公司防火墙上,进入IPSec策略的视图,执行命令 nat traversal,启用NAT穿越功能。
2. 在机房防火墙上,进入IPSec策略的视图,执行命令 nat traversal,启用NAT穿越功能。
3. 在NAT设备上,配置UDP 500和4500端口的端口映射,将这两个端口的流量转发到公司防火墙和机房防火墙的外部接口。
- 2023-12-15回答
- 评论(0)
- 举报
-
(0)

您好,ipsec和nat在出方向上,先匹配nat,然后才匹配ipsec,一般来讲,走IPsec的流量都是私网的,不需要走nat,所以,在配置的时候,需要在nat的acl中deny掉ipsec的感兴趣流量
- 2023-12-15回答
- 评论(0)
- 举报
-
(0)
暂无评论
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明

暂无评论