固定ip宽带和动态adsl宽带野蛮模式ipsec配置
- 0关注
- 0收藏,1168浏览
问题描述:
1:上海固定IP 172.16.100.2 (假如这个是公网固定IP)
2:北京动态宽带
ipsec配置了野蛮模式哪里配置错了呢?为什么无法起来呢?
上海:
[SH-FW]acl advanced name Lan-To-Wan-ACL
[SH-FW-acl-ipv4-adv-Lan-To-Wan-ACL]rule 5 deny ip source 172.16.10.0 0.0.0.255 destination 172.17.10.0 0.0.0.255
[SH-FW-acl-ipv4-adv-Lan-To-Wan-ACL]rule 10 deny ip source 172.16.10.0 0.0.0.255 destination 172.17.20.0 0.0.0.255
[SH-FW-acl-ipv4-adv-Lan-To-Wan-ACL]rule 15 deny ip source 172.16.20.0 0.0.0.255 destination 172.17.10.0 0.0.0.255
[SH-FW-acl-ipv4-adv-Lan-To-Wan-ACL]rule 20 deny ip source 172.16.20.0 0.0.0.255 destination 172.17.20.0 0.0.0.255
[SH-FW-acl-ipv4-adv-Lan-To-Wan-ACL]rule 1000 rule 1000 permit ip
[SH-FW]acl advanced name ipsec-lan-to-lan-bj
[SH-FW-acl-ipv4-adv-ipsec-lan-to-lan-bj]rule 0 permit ip source 172.16.10.0 0.0.0.255 destination 172.17.10.0 0.0.0.255
[SH-FW-acl-ipv4-adv-ipsec-lan-to-lan-bj]rule 5 permit ip source 172.16.10.0 0.0.0.255 destination 172.17.20.0 0.0.0.255
[SH-FW-acl-ipv4-adv-ipsec-lan-to-lan-bj]rule 10 permit ip source 172.16.20.0 0.0.0.255 destination 172.17.10.0 0.0.0.255
[SH-FW-acl-ipv4-adv-ipsec-lan-to-lan-bj]rule 15 permit ip source 172.16.20.0 0.0.0.255 destination 172.17.20.0 0.0.0.255
SH-FW]ike identity fqdn sh-fw
[SH-FW]ike proposal 1
[SH-FW-ike-proposal-1]authentication-algorithm md5
[SH-FW-ike-proposal-1]encryption-algorithm 3des-cbc
[SH-FW-ike-proposal-1]dh group2
[SH-FW-ike-proposal-1]quit
[SH-FW]ike keychain To-BJ-ike-keychain
[SH-FW-ike-keychain-To-BJ-ike-keychain]pre-shared-key hostname sh-fw key simple ***.***
[SH-FW-ike-keychain-To-BJ-ike-keychain]quit
[SH-FW]ike profile To-BJ-ike-profile
[SH-FW-ike-profile-To-BJ-ike-profile]keychain To-BJ-ike-keychain
[SH-FW-ike-profile-To-BJ-ike-profile]exchange-mode aggressive
[SH-FW-ike-profile-To-BJ-ike-profile]proposal 1
[SH-FW-ike-profile-To-BJ-ike-profile]local-identity fqdn sh-fw
[SH-FW-ike-profile-To-BJ-ike-profile]match remote identity fqdn bj-fw
[SH-FW-ike-profile-To-BJ-ike-profile]match local address GigabitEthernet 1/0/0
[SH-FW]ipsec transform-set To-BJ-ipsec-transform-set
[SH-FW-ipsec-transform-set-To-BJ-ipsec-transform-set]esp encryption-algorithm 3des-cbc
[SH-FW-ipsec-transform-set-To-BJ-ipsec-transform-set]esp authentication-algorithm md5
[SH-FW-ipsec-transform-set-To-BJ-ipsec-transform-set]pfs dh-group2
[SH-FW-ipsec-transform-set-To-BJ-ipsec-transform-set]quit
[SH-FW]ipsec policy To-BJ-ipsec-policy 1 isakmp
[SH-FW-ipsec-policy-isakmp-To-BJ-ipsec-policy-1]transform-set To-BJ-ipsec-transform-set
[SH-FW-ipsec-policy-isakmp-To-BJ-ipsec-policy-1]security acl name ipsec-lan-to-lan-bj
[SH-FW-ipsec-policy-isakmp-To-BJ-ipsec-policy-1]ike-profile To-BJ-ike-profile
[SH-FW-ipsec-policy-isakmp-To-BJ-ipsec-policy-1]sa trigger-mode auto
[SH-FW-ipsec-policy-isakmp-To-BJ-ipsec-policy-1]quit
[SH-FW]interface GigabitEthernet 1/0/0
[SH-FW-GigabitEthernet1/0/0]ipsec apply policy To-BJ-ipsec-policy
[SH-FW-GigabitEthernet1/0/0]quit
北京:
[BJ-FW]acl advanced name ipsec-lan-to-lan-sh
[BJ-FW-acl-ipv4-adv-ipsec-lan-to-lan-sh]rule 0 permit ip source 172.17.10.0 0.0.0.255 destination 172.16.10.0 0.0.0.255
[BJ-FW-acl-ipv4-adv-ipsec-lan-to-lan-sh]rule 5 permit ip source 172.17.10.0 0.0.0.255 destination 172.16.20.0 0.0.0.255
[BJ-FW-acl-ipv4-adv-ipsec-lan-to-lan-sh]rule 10 permit ip source 172.17.20.0 0.0.0.255 destination 172.16.10.0 0.0.0.255
[BJ-FW-acl-ipv4-adv-ipsec-lan-to-lan-sh]rule 15 permit ip source 172.17.20.0 0.0.0.255 destination 172.16.20.0 0.0.0.255
[BJ-FW]ike identity fqdn bj-fw
[BJ-FW]ike keychain To-SH-ike-keychain
[BJ-FW-ike-keychain-To-SH-ike-keychain]pre-shared-key address 172.16.100.2 32 key simple ***.***
[BJ-FW-ike-keychain-To-SH-ike-keychain]quit
[BJ-FW]ike proposal 1
[BJ-FW-ike-proposal-1]authentication-algorithm md5
[BJ-FW-ike-proposal-1]encryption-algorithm 3des-cbc
[BJ-FW-ike-proposal-1]dh group2
[BJ-FW-ike-proposal-1]quit
[BJ-FW]ike profile To-SH-ike-profile
[BJ-FW-ike-profile-To-SH-ike-profile]keychain To-SH-ike-keychain
[BJ-FW-ike-profile-To-SH-ike-profile]exchange-mode aggressive
[BJ-FW-ike-profile-To-SH-ike-profile]proposal 1
[BJ-FW-ike-profile-To-SH-ike-profile]local-identity fqdn bj-fw
[BJ-FW-ike-profile-To-SH-ike-profile]match remote identity address 172.16.100.2
[BJ-FW-ike-profile-To-SH-ike-profile]match local address GigabitEthernet 1/0/0
[BJ-FW]ipsec transform-set To-SH-ipsec-transform-set
[BJ-FW-ipsec-transform-set-To-SH-ipsec-transform-set]esp encryption-algorithm 3des-cbc
[BJ-FW-ipsec-transform-set-To-SH-ipsec-transform-set]esp authentication-algorithm md5
[BJ-FW-ipsec-transform-set-To-SH-ipsec-transform-set]pfs dh-group2
[BJ-FW-ipsec-transform-set-To-SH-ipsec-transform-set]quit
[BJ-FW]ipsec policy To-SH-ipsec-policy 1 isakmp
[BJ-FW-ipsec-policy-isakmp-To-SH-ipsec-policy-1]transform-set To-SH-ipsec-transform-set
[BJ-FW-ipsec-policy-isakmp-To-SH-ipsec-policy-1]security acl name ipsec-lan-to-lan-sh
[BJ-FW-ipsec-policy-isakmp-To-SH-ipsec-policy-1]ike-profile To-SH-ike-profile
[BJ-FW-ipsec-policy-isakmp-To-SH-ipsec-policy-1]sa trigger-mode auto
[BJ-FW-ipsec-policy-isakmp-To-SH-ipsec-policy-1]quit
[BJ-FW]interface GigabitEthernet 1/0/0
[BJ-FW-GigabitEthernet1/0/0]ipsec apply policy To-SH-ipsec-policy
[BJ-FW-GigabitEthernet1/0/0]quit
组网及组网描述:
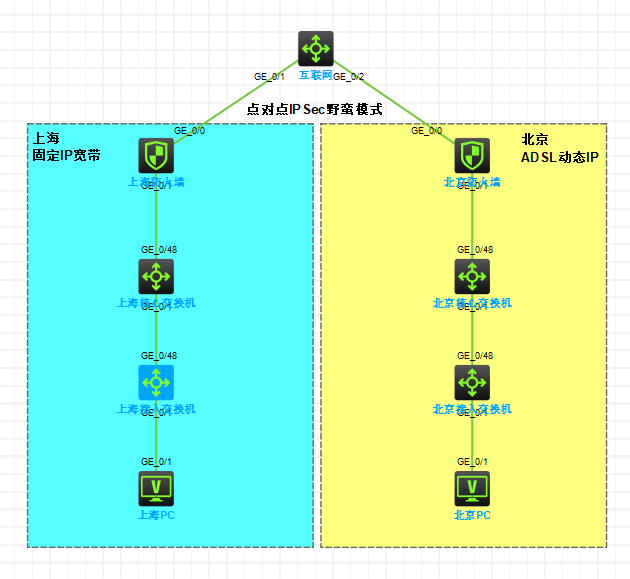
- 2024-03-05提问
- 举报
-
(0)

把这个也改成fqdn
BJ-FW-ike-profile-To-SH-ike-profile]match remote identity address 172.16.100.2
把两端的这条删掉
[SH-FW-ike-profile-To-BJ-ike-profile]match local address GigabitEthernet 1/0/0
然后两边reset ike sa测试一下
- 2024-03-05回答
- 评论(3)
- 举报
-
(0)
<SH-FW>debugging ike all <SH-FW>debugging ipsec all 两边都开启后也没看到什么日志产生
还是起不来
可以debug看看
<SH-FW>debugging ike all <SH-FW>debugging ipsec all 两边都开启后也没看到什么日志产生

问题找到了。
[BJ-FW-ipsec-policy-isakmp-To-SH-ipsec-policy-1]remote-address 172.16.100.2
需要加这一条后起来的。
现在ike起来了。
ipsec没起来。
- 2024-03-05回答
- 评论(0)
- 举报
-
(0)

2端都是fqdn还咋起来
如果要模拟野蛮模式的话,单侧fqdn或配合域名解析来做吧
另外在仔细确认下组网需求和配置吧
如果拓扑没错的话,上海节点配置就不对了呀。
参考思路
上海节点ip标识,北京节点fqdn标识。然后配置完成后北京节点触发ipsec
如果还是异常,请debug进一步定位
如果无法定位或情况复杂建议联系400热线或采购渠道H3C认证代理商由专业工程师处理。
- 2024-03-05回答
- 评论(4)
- 举报
-
(0)
上海: [SH-FW]ike profile To-BJ-ike-profile [SH-FW-ike-profile-To-BJ-ike-profile]keychain To-BJ-ike-keychain [SH-FW-ike-profile-To-BJ-ike-profile]exchange-mode aggressive [SH-FW-ike-profile-To-BJ-ike-profile]proposal 1 [SH-FW-ike-profile-To-BJ-ike-profile]local-identity address 172.16.100.2 [SH-FW-ike-profile-To-BJ-ike-profile]match remote identity fqdn bj-fw [SH-FW-ike-profile-To-BJ-ike-profile]match local address GigabitEthernet 1/0/0 北京: [BJ-FW]ike profile To-SH-ike-profile [BJ-FW-ike-profile-To-SH-ike-profile]keychain To-SH-ike-keychain [BJ-FW-ike-profile-To-SH-ike-profile]exchange-mode aggressive [BJ-FW-ike-profile-To-SH-ike-profile]proposal 1 [BJ-FW-ike-profile-To-SH-ike-profile]local-identity fqdn bj-fw [BJ-FW-ike-profile-To-SH-ike-profile]match remote identity address 172.16.100.2 [BJ-FW-ike-profile-To-SH-ike-profile]match local address GigabitEthernet 1/0/0
上海节点是哪里错了呢?
缺少了 [BJ-FW-ipsec-policy-isakmp-To-SH-ipsec-policy-1]remote-address 172.16.100.2 这一条ike没起来。现在是ipsec没起来。
上海: [SH-FW]ike profile To-BJ-ike-profile [SH-FW-ike-profile-To-BJ-ike-profile]keychain To-BJ-ike-keychain [SH-FW-ike-profile-To-BJ-ike-profile]exchange-mode aggressive [SH-FW-ike-profile-To-BJ-ike-profile]proposal 1 [SH-FW-ike-profile-To-BJ-ike-profile]local-identity address 172.16.100.2 [SH-FW-ike-profile-To-BJ-ike-profile]match remote identity fqdn bj-fw [SH-FW-ike-profile-To-BJ-ike-profile]match local address GigabitEthernet 1/0/0 北京: [BJ-FW]ike profile To-SH-ike-profile [BJ-FW-ike-profile-To-SH-ike-profile]keychain To-SH-ike-keychain [BJ-FW-ike-profile-To-SH-ike-profile]exchange-mode aggressive [BJ-FW-ike-profile-To-SH-ike-profile]proposal 1 [BJ-FW-ike-profile-To-SH-ike-profile]local-identity fqdn bj-fw [BJ-FW-ike-profile-To-SH-ike-profile]match remote identity address 172.16.100.2 [BJ-FW-ike-profile-To-SH-ike-profile]match local address GigabitEthernet 1/0/0
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明


