ipsec野蛮模式无法协商
- 0关注
- 0收藏,1821浏览
问题描述:
上海:固定ip 172.16.100.2
北京:动态(dhcp自动获取代替pppoe
现在是ike协商成功,为什么ipsec 无法起来呢?
上海
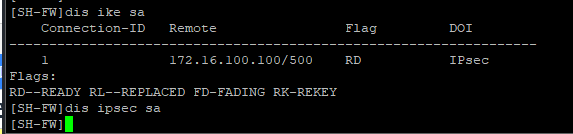
北京
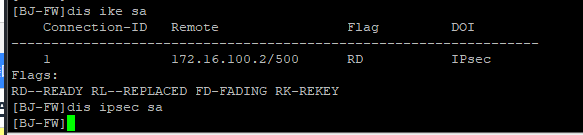
上海:

北京:

配置:
上海:
[SH-FW]acl advanced name ipsec-lan-to-lan-bj
[SH-FW-acl-ipv4-adv-ipsec-lan-to-lan-bj]rule 0 permit ip source 172.16.10.0 0.0.0.255 destination 172.17.10.0 0.0.0.255
[SH-FW-acl-ipv4-adv-ipsec-lan-to-lan-bj]rule 5 permit ip source 172.16.10.0 0.0.0.255 destination 172.17.20.0 0.0.0.255
[SH-FW-acl-ipv4-adv-ipsec-lan-to-lan-bj]rule 10 permit ip source 172.16.20.0 0.0.0.255 destination 172.17.10.0 0.0.0.255
[SH-FW-acl-ipv4-adv-ipsec-lan-to-lan-bj]rule 15 permit ip source 172.16.20.0 0.0.0.255 destination 172.17.20.0 0.0.0.255
[SH-FW]ike identity fqdn sh-fw
[SH-FW]ike proposal 1
[SH-FW-ike-proposal-1]authentication-algorithm md5
[SH-FW-ike-proposal-1]encryption-algorithm 3des-cbc
[SH-FW-ike-proposal-1]dh group2
[SH-FW-ike-proposal-1]quit
[SH-FW]ike keychain To-BJ-ike-keychain
[SH-FW-ike-keychain-To-BJ-ike-keychain]pre-shared-key hostname bj-fw key simple ***.***
[SH-FW-ike-keychain-To-BJ-ike-keychain]quit
[SH-FW]ike profile To-BJ-ike-profile
[SH-FW-ike-profile-To-BJ-ike-profile]keychain To-BJ-ike-keychain
[SH-FW-ike-profile-To-BJ-ike-profile]exchange-mode aggressive
[SH-FW-ike-profile-To-BJ-ike-profile]proposal 1
[SH-FW-ike-profile-To-BJ-ike-profile]local-identity address 172.16.100.2
[SH-FW-ike-profile-To-BJ-ike-profile]match remote identity fqdn bj-fw
[SH-FW-ike-profile-To-BJ-ike-profile]match local address GigabitEthernet 1/0/0
[SH-FW]ipsec transform-set To-BJ-ipsec-transform-set
[SH-FW-ipsec-transform-set-To-BJ-ipsec-transform-set]protocol esp
[SH-FW-ipsec-transform-set-To-BJ-ipsec-transform-set]encapsulation-mode tunnel
[SH-FW-ipsec-transform-set-To-BJ-ipsec-transform-set]esp encryption-algorithm 3des-cbc
[SH-FW-ipsec-transform-set-To-BJ-ipsec-transform-set]esp authentication-algorithm md5
[SH-FW-ipsec-transform-set-To-BJ-ipsec-transform-set]pfs dh-group2
[SH-FW-ipsec-transform-set-To-BJ-ipsec-transform-set]quit
[SH-FW]ipsec policy To-BJ-ipsec-policy 1 isakmp
[SH-FW-ipsec-policy-isakmp-To-BJ-ipsec-policy-1]transform-set To-BJ-ipsec-transform-set
[SH-FW-ipsec-policy-isakmp-To-BJ-ipsec-policy-1]security acl name ipsec-lan-to-lan-bj
[SH-FW-ipsec-policy-isakmp-To-BJ-ipsec-policy-1]local-address 172.16.100.2
[SH-FW-ipsec-policy-isakmp-To-BJ-ipsec-policy-1]remote-address bj-fw
[SH-FW-ipsec-policy-isakmp-To-BJ-ipsec-policy-1]ike-profile To-BJ-ike-profile
[SH-FW-ipsec-policy-isakmp-To-BJ-ipsec-policy-1]sa trigger-mode auto
[SH-FW-ipsec-policy-isakmp-To-BJ-ipsec-policy-1]quit
[SH-FW]interface GigabitEthernet 1/0/0
[SH-FW-GigabitEthernet1/0/0]ipsec apply policy To-BJ-ipsec-policy
[SH-FW-GigabitEthernet1/0/0]quit
北京:
[BJ-FW]acl advanced name ipsec-lan-to-lan-sh
[BJ-FW-acl-ipv4-adv-ipsec-lan-to-lan-sh]rule 0 permit ip source 172.17.10.0 0.0.0.255 destination 172.16.10.0 0.0.0.255
[BJ-FW-acl-ipv4-adv-ipsec-lan-to-lan-sh]rule 5 permit ip source 172.17.10.0 0.0.0.255 destination 172.16.20.0 0.0.0.255
[BJ-FW-acl-ipv4-adv-ipsec-lan-to-lan-sh]rule 10 permit ip source 172.17.20.0 0.0.0.255 destination 172.16.10.0 0.0.0.255
[BJ-FW-acl-ipv4-adv-ipsec-lan-to-lan-sh]rule 15 permit ip source 172.17.20.0 0.0.0.255 destination 172.16.20.0 0.0.0.255
[BJ-FW]ike identity fqdn bj-fw
[BJ-FW]ike keychain To-SH-ike-keychain
[BJ-FW-ike-keychain-To-SH-ike-keychain]pre-shared-key address 172.16.100.2 32 key simple ***.***
[BJ-FW-ike-keychain-To-SH-ike-keychain]quit
[BJ-FW]ike proposal 1
[BJ-FW-ike-proposal-1]authentication-algorithm md5
[BJ-FW-ike-proposal-1]encryption-algorithm 3des-cbc
[BJ-FW-ike-proposal-1]dh group2
[BJ-FW-ike-proposal-1]quit
[BJ-FW]ike profile To-SH-ike-profile
[BJ-FW-ike-profile-To-SH-ike-profile]keychain To-SH-ike-keychain
[BJ-FW-ike-profile-To-SH-ike-profile]exchange-mode aggressive
[BJ-FW-ike-profile-To-SH-ike-profile]proposal 1
[BJ-FW-ike-profile-To-SH-ike-profile]local-identity fqdn bj-fw
[BJ-FW-ike-profile-To-SH-ike-profile]match remote identity address 172.16.100.2
[BJ-FW-ike-profile-To-SH-ike-profile]match local address GigabitEthernet 1/0/0
[BJ-FW]ipsec transform-set To-SH-ipsec-transform-set
[BJ-FW-ipsec-transform-set-To-SH-ipsec-transform-set]protocol esp
[BJ-FW-ipsec-transform-set-To-SH-ipsec-transform-set]encapsulation-mode tunnel
[BJ-FW-ipsec-transform-set-To-SH-ipsec-transform-set]esp encryption-algorithm 3des-cbc
[BJ-FW-ipsec-transform-set-To-SH-ipsec-transform-set]esp authentication-algorithm md5
[BJ-FW-ipsec-transform-set-To-SH-ipsec-transform-set]pfs dh-group2
[BJ-FW-ipsec-transform-set-To-SH-ipsec-transform-set]quit
[BJ-FW]ipsec policy To-SH-ipsec-policy 1 isakmp
[BJ-FW-ipsec-policy-isakmp-To-SH-ipsec-policy-1]transform-set To-SH-ipsec-transform-set
[BJ-FW-ipsec-policy-isakmp-To-SH-ipsec-policy-1]security acl name ipsec-lan-to-lan-sh
[BJ-FW-ipsec-policy-isakmp-To-SH-ipsec-policy-1]remote-address 172.16.100.2
[BJ-FW-ipsec-policy-isakmp-To-SH-ipsec-policy-1]ike-profile To-SH-ike-profile
[BJ-FW-ipsec-policy-isakmp-To-SH-ipsec-policy-1]sa trigger-mode auto
[BJ-FW-ipsec-policy-isakmp-To-SH-ipsec-policy-1]quit
[BJ-FW]interface GigabitEthernet 1/0/0
[BJ-FW-GigabitEthernet1/0/0]ipsec apply policy To-SH-ipsec-policy
[BJ-FW-GigabitEthernet1/0/0]quit
组网及组网描述:

- 2024-03-06提问
- 举报
-
(0)
最佳答案

身份信息无效导致IPsec SA协商失败
1. 故障现象
(1) 通过display ike sa命令查看当前的IKE SA信息,发现IKE SA协商成功,其状态(Flags字段)为RD。但通过display ipsec sa命令查看当前的IPsec SA时,发现没有协商出相应的IPsec SA。
(2) 打开IKE调试信息开关可以看到以下调试信息:
Notification INVALID_ID_INFORMATION is received.
或者:
Failed to get IPsec policy when renegotiating IPsec SA. Delete IPsec SA.
Construct notification packet: INVALID_ID_INFORMATION.
2. 故障分析
响应方IPsec安全策略配置错误,导致在IKE第二阶段协商时找不到IPsec安全策略,原因可能为如下几点:
(1) 通过display ike sa verbose命令查看IKE一阶段协商中是否找到匹配的IKE profile。若没有找到IKE profile,则会查找全局的IKE参数,因此就要求这种情况下IPsec安全策略中不能引用任何IKE profile,否则协商失败。
通过如下显示信息可以看到,IKE SA在协商过程中没有找到匹配的IKE profile:
<Sysname> display ike sa verbose
-----------------------------------------------
Connection ID: 3
Outside VPN:
Inside VPN:
Profile:
Transmitting entity: Responder
Initiator COOKIE: 1bcf453f0a217259
Responder COOKIE: 5e32a74dfa66a0a4
-----------------------------------------------
Local IP/port: 192.168.222.5/500
Local ID type: IPV4_ADDR
Local ID: 192.168.222.5
Remote IP/port: 192.168.222.71/500
Remote ID type: IPV4_ADDR
Remote ID: 192.168.222.71
Authentication-method: PRE-SHARED-KEY
Authentication-algorithm: MD5
Encryption-algorithm: 3DES-CBC
Life duration(sec): 86400
Remaining key duration(sec): 85847
Exchange-mode: Main
Diffie-Hellman group: Group 1
NAT traversal: Not detected
Vendor ID index: 0xa1d
Vendor ID sequence number: 0x0
但在IPsec策略中引用了IKE profile profile1:
[Sysname] display ipsec policy
-------------------------------------------
IPsec Policy: policy1
Interface: GigabitEthernet1/0/1
-------------------------------------------
-----------------------------
Sequence number: 1
Mode: ISAKMP
-----------------------------
Description:
Security data flow: 3000
Selector mode: aggregation
Local address: 192.168.222.5
Remote address: 192.168.222.71
Transform set: transform1
IKE profile: profile1
smart-link policy:
SA trigger mode: Auto
SA duration(time based): 3600 seconds
SA duration(traffic based): 1843200 kilobytes
SA soft-duration buffer(time based): 1000 seconds
SA soft-duration buffer(traffic based): 43200 kilobytes
SA idle time: 100 seconds
(2) 查看IPsec安全策略中引用的ACL配置是否正确。
例如,如发起方ACL流范围为网段到网段:
[Sysname] display acl 3000
Advanced IPv4 ACL 3000, 1 rule,
ACL's step is 5
rule 0 permit ip source 192.168.222.0 0.0.0.255 destination 192.168.222.0 0.0.0.255
响应方ACL流范围为主机到主机:
[Sysname] display acl 3000
Advanced IPv4 ACL 3000, 1 rule,
ACL's step is 5
rule 0 permit ip source 192.168.222.71 0 destination 192.168.222.5 0
以上配置中,响应方ACL规则定义的流范围小于发起方ACL规则定义的流范围,这会导致IPsec SA协商失败。
(3) IPsec 安全策略配置不完整。具体包括:没有配置对端地址、没有配置IPsec提议、IPsec提议配置不完整。
例如,如下IPsec安全策略中没有配置隧道的对端IP地址,因此IPsec安全策略是不完整的:
[Sysname] display ipsec policy
-------------------------------------------
IPsec Policy: policy1
Interface: GigabitEthernet1/0/1
-------------------------------------------
-----------------------------
Sequence number: 1
Mode: ISAKMP
-----------------------------
Security data flow: 3000
Selector mode: aggregation
Local address: 192.168.222.5
Remote address:
Transform set: transform1
IKE profile: profile1
smart-link policy:
SA trigger mode: Auto
SA duration(time based): 3600 seconds
SA duration(traffic based): 1843200 kilobytes
SA soft-duration buffer(time based): 1000 seconds
SA soft-duration buffer(traffic based): 43200 kilobytes
SA idle time: 100 seconds
3. 处理过程
(1) 若在IKE第一阶段协商过程中没有找到IKE profile,建议在响应方IPsec安全策略中去掉对IKE profile的引用或者调整IKE profile的配置使之能够与发起端相匹配。
(2) 若响应方ACL规则定义的流范围小于发起方ACL规则定义的流范围,建议修改响应方ACL的流范围大于或等于发起方ACL的流范围。以故障分析(2)中的配置为例,可以将响应方ACL流范围修改为:
[Sysname] display acl 3000
Advanced IPv4 ACL 3000, 2 rules,
ACL's step is 5
rule 0 permit ip source 192.168.222.0 0.0.0.255 destination 192.168.222.0 0.0.0.255
(3) 将IPsec安全策略配置完整。以故障分析中的(3)中的配置为例,需要在IPsec安全策略中配置隧道的对端IP地址。
- 2024-03-06回答
- 评论(0)
- 举报
-
(0)

debug出现这些日志
*Mar 6 11:38:54:088 2024 SH-FW IPSEC/7/EVENT: -COntext=1;
Received DNS analyse invalid result or have no address result.
*Mar 6 11:38:54:088 2024 SH-FW IPSEC/7/EVENT: -COntext=1;
Update SP by dns request result.
*Mar 6 11:38:54:088 2024 SH-FW IPSEC/7/EVENT: -COntext=1;
Switch remote address no change, SP index is 0.
*Mar 6 11:38:57:819 2024 SH-FW IPSEC/7/EVENT: -COntext=1;
Send DNS analyse acquire.
*Mar 6 11:38:57:819 2024 SH-FW IPSEC/7/EVENT: -COntext=1;
Failed to get SP (SP ID=0): Remote address not exist (hostname=bj-fw).
*Mar 6 11:38:57:819 2024 SH-FW IPSEC/7/EVENT: -COntext=1;
Received DNS analyse invalid result or have no address result.
*Mar 6 11:38:57:819 2024 SH-FW IPSEC/7/EVENT: -COntext=1;
Update SP by dns request result.
*Mar 6 11:38:57:819 2024 SH-FW IPSEC/7/EVENT: -COntext=1;
Switch remote address no change, SP index is 0.
*Mar 6 11:38:57:834 2024 SH-FW IPSEC/7/EVENT: -COntext=1;
Send DNS analyse acquire.
*Mar 6 11:38:57:834 2024 SH-FW IPSEC/7/EVENT: -COntext=1;
Failed to get SP (SP ID=0): Remote address not exist (hostname=bj-fw).
*Mar 6 11:38:57:834 2024 SH-FW IPSEC/7/EVENT: -COntext=1;
Received DNS analyse invalid result or have no address result.
*Mar 6 11:38:57:834 2024 SH-FW IPSEC/7/EVENT: -COntext=1;
Update SP by dns request result.
*Mar 6 11:38:57:834 2024 SH-FW IPSEC/7/EVENT: -COntext=1;
Switch remote address no change, SP index is 0.
*Mar 6 11:38:57:849 2024 SH-FW IPSEC/7/EVENT: -COntext=1;
Send DNS analyse acquire.
*Mar 6 11:38:57:849 2024 SH-FW IPSEC/7/EVENT: -COntext=1;
Failed to get SP (SP ID=0): Remote address not exist (hostname=bj-fw).
*Mar 6 11:38:57:849 2024 SH-FW IPSEC/7/EVENT: -COntext=1;
Received DNS analyse invalid result or have no address result.
*Mar 6 11:38:57:849 2024 SH-FW IPSEC/7/EVENT: -COntext=1;
Update SP by dns request result.
*Mar 6 11:38:57:849 2024 SH-FW IPSEC/7/EVENT: -COntext=1;
Switch remote address no change, SP index is 0.
*Mar 6 11:38:57:864 2024 SH-FW IPSEC/7/EVENT: -COntext=1;
Send DNS analyse acquire.
*Mar 6 11:38:57:864 2024 SH-FW IPSEC/7/EVENT: -COntext=1;
Failed to get SP (SP ID=0): Remote address not exist (hostname=bj-fw).
*Mar 6 11:38:57:864 2024 SH-FW IPSEC/7/EVENT: -COntext=1;
Received DNS analyse invalid result or have no address result.
*Mar 6 11:38:57:865 2024 SH-FW IPSEC/7/EVENT: -COntext=1;
Update SP by dns request result.
*Mar 6 11:38:57:865 2024 SH-FW IPSEC/7/EVENT: -COntext=1;
Switch remote address no change, SP index is 0.
*Mar 6 11:38:59:087 2024 SH-FW IPSEC/7/EVENT: -COntext=1;
Auto negotiate starts.
*Mar 6 11:38:59:087 2024 SH-FW IPSEC/7/EVENT: -COntext=1;
Got SA time-based soft lifetime settings when filling Sp data.
Configured soft lifetime buffer : 0 seconds.
Configured global soft lifetime buffer : 0 s
- 2024-03-06回答
- 评论(0)
- 举报
-
(0)

野蛮模式的话,上海侧应该改用ipsec policy-template。
比如:
ipsec policy-template test 1
transform-set test
ike-profile test
quit
ipsec policy test 1 isakmp template test
具体参考配置手册:
HCL简易实验:

配置:
<R1>
sysname R1
interface LoopBack0
ip address 1.1.1.1 255.255.255.255
interface GigabitEthernet0/0
ip address 10.0.12.1 255.255.255.0
ipsec apply policy VPN
ip route-static 0.0.0.0 0 10.0.12.2
acl advanced 3000
rule 0 permit ip source 1.1.1.1 0 destination 3.3.3.3 0
ipsec transform-set VPN
esp encryption-algorithm des-cbc
esp authentication-algorithm md5
ipsec policy VPN 13 isakmp
transform-set VPN
security acl 3000
remote-address 10.0.23.3
ike-profile VPN
ike identity user-fqdn R1
ike profile VPN
keychain VPN
exchange-mode aggressive
match remote identity user-fqdn R3
ike keychain VPN
pre-shared-key address 10.0.23.3 255.255.255.255 key simple 123
<R2>
sysname R2
interface GigabitEthernet0/0
ip address 10.0.12.2 255.255.255.0
interface GigabitEthernet0/1
ip address 10.0.23.2 255.255.255.0
<R3>
sysname R3
interface LoopBack0
ip address 3.3.3.3 255.255.255.255
interface GigabitEthernet0/0
ip address 10.0.23.3 255.255.255.0
ipsec apply policy VPN
ip route-static 0.0.0.0 0 10.0.23.2
ipsec transform-set VPN
esp encryption-algorithm des-cbc
esp authentication-algorithm md5
ipsec policy-template VPN 13
transform-set VPN
ike-profile VPN
ipsec policy VPN 13 isakmp template VPN
ike identity user-fqdn R3
ike profile VPN
keychain VPN
match remote identity user-fqdn R1
ike keychain VPN
pre-shared-key hostname R1 key simple 123
- 2024-03-06回答
- 评论(7)
- 举报
-
(1)
感谢。
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明


