F1000-AK145防火墙配置前缀长度126位的ipv6上网
- 0关注
- 0收藏,1503浏览
问题描述:
运营商提供一前缀长度126位的ipv6地址:240e:xxxx:xxxx::2/126;
网关:240e:xxxx:xxxx::1;
DNS:240e:44:xxxx:xxxx::1;
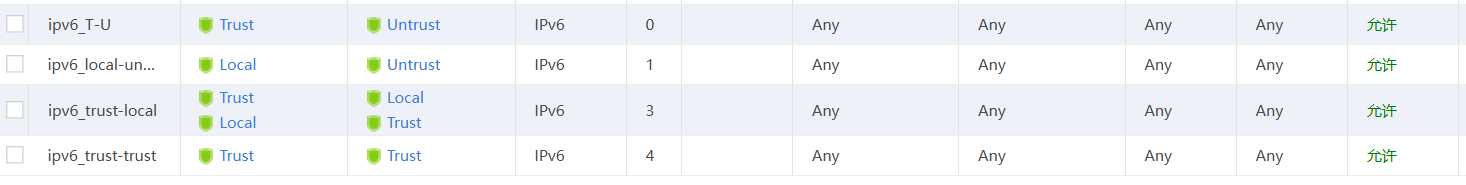
安全策略放通loca-untrust,trust-untrust所有ipv6
从运营商交换机连接防火墙GE1/0/11(untrust),写入ipv6地址240e:xxxx:xxxx::2/126,proxy-nd enable;
防火墙GE1/0/12(trust)启用dhcpv6服务器,内网地址为fd::1/64,引用ipv6 dhcp pool 1,给内网设备下发内网地址和DNS;
防火墙写入缺省静态路由ipv6 route-static :: 0 240e:xxxx:xxxx::1;
目前防火墙内可ping通纯ipv6网站,内网PC仅能ping通240e:xxxx:xxxx::2,显示ipv6无internet访问权限。怎样才能让内网设备正常访问ipv6?
组网及组网描述:
#
interface GigabitEthernet1/0/11
port link-mode route
nat66 prefix source FD:: 64 240E:xxxx:xxxx:: 126 pat //尝试nat66前缀转换,无变化
undo dhcp select server
ipv6 address 240E:xxxx:xxxx::2/126
proxy-nd enable
#
#
interface GigabitEthernet1/0/12
port link-mode route
ip address 192.168.10.1 255.255.255.0
ipv6 dhcp select server
ipv6 address FD::1/64
ipv6 nd autoconfig managed-address-flag
ipv6 nd autoconfig other-flag
undo ipv6 nd ra halt
#
#
ipv6 dhcp pool 1
network FD::/64 preferred-lifetime 172800 valid-lifetime 345600
dns-server 240E:44:xxxx:xxxx::1
gateway-list FD::1
#
[AK145]dis ipv6 routing-table
Destinations : 8 Routes : 8
Destination: ::/0 Protocol : Static
NextHop : 240E:xxxx:xxxx::1 Preference: 60
Interface : GE1/0/11 Cost : 0
Destination: ::1/128 Protocol : Direct
NextHop : ::1 Preference: 0
Interface : InLoop0 Cost : 0
Destination: FD::/64 Protocol : Direct
NextHop : :: Preference: 0
Interface : GE1/0/12 Cost : 0
Destination: FD::1/128 Protocol : Direct
NextHop : ::1 Preference: 0
Interface : InLoop0 Cost : 0
Destination: 240E:xxxx:xxxx::/126 Protocol : Direct
NextHop : :: Preference: 0
Interface : GE1/0/11 Cost : 0
Destination: 240E:xxxx:xxxx::2/128 Protocol : Direct
NextHop : ::1 Preference: 0
Interface : InLoop0 Cost : 0
- 2024-06-15提问
- 举报
-
(0)

安全策略全放开试试,排除下安全策略的问题
- 2024-06-15回答
- 评论(1)
- 举报
-
(0)
放通untrust-trust的ipv6,还是一样
放通untrust-trust的ipv6,还是一样
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明

