ipsec VPN对端的内网地址和本端的内网地址有冲突,这个要怎么处理呢?
- 0关注
- 0收藏,1442浏览
问题描述:
两端都是公网地址。对端是天融信,内网地址两边都有192.168.100.0
组网及组网描述:
- 2024-11-26提问
- 举报
-
(0)
最佳答案

江苏某公司两个局域网站点出口用MSR3620做ipsec VPN,两端地址重叠,导致ipsec建立成功后,两端不能互访,实验室组网拓扑简图如图一所示:
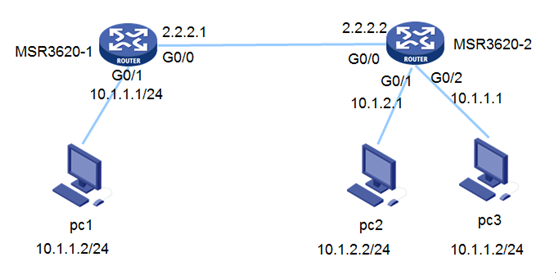
图一 组网拓扑
两端局域网出口设备建立ipsec之后,由PC1侧发起ping操作到PC2侧时,ping报文可以到达PC2,但当PC2回应报文时,由于在MSR3620-2侧直接查找本地路由到了PC3,无法到达设备出接口封装ipsec报文头,导致两端局域网终端无法互访。
在连接PC2的接口上配nat outbound和PBR,PC1发出的报文在该接口上先
匹配nat outbound,替换为该接口ip地址到达pc2,pc2回应的时候匹配PBR,下一跳为MSR3620-2的出接口ip地址,将该报文送到MSR3620-2的ipsec接口上,使PC1访问PC2的报文得到回应。
关键配置如下:
MSR3620-1:
#
interface GigabitEthernet0/0
port link-mode route
combo enable copper
ip address 2.2.2.1 255.255.255.0
ipsec apply policy map1
#
interface GigabitEthernet0/1
port link-mode route
combo enable copper
ip address 10.1.1.1 255.255.255.0
#
ip route-static 10.1.2.0 24 GigabitEthernet0/0 2.2.2.2
#
acl advanced 3101
rule 0 permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255
#
ipsec transform-set tran1
esp encryption-algorithm aes-cbc-128
esp authentication-algorithm sha1
#
ipsec policy map1 10 isakmp
transform-set tran1
security acl 3101
local-address 2.2.2.1
remote-address 2.2.2.2
ike-profile profile1
#
ike profile profile1
keychain keychain1
match remote identity address 2.2.2.2 255.255.255.0
#
ike keychain keychain1
pre-shared-key address 2.2.2.2 255.255.255.0 key cipher $c$3$0hpFFye6lOO9kcA9W2ZftyUCBV6c6A==
#
MSR3620-2:
policy-based-route aaa permit node 5
if-match acl 3000
apply next-hop 2.2.2.1
#
interface GigabitEthernet0/0
port link-mode route
combo enable copper
ip address 2.2.2.2 255.255.255.0
ipsec apply policy use1
#
interface GigabitEthernet0/1
port link-mode route
combo enable copper
ip address 10.1.2.1 255.255.255.0
nat outbound
ip policy-based-route aaa
#
interface GigabitEthernet0/2
port link-mode route
combo enable copper
ip address 10.1.1.1 255.255.255.0
#
ip route-static 10.1.1.0 24 GigabitEthernet0/0 2.2.2.1
#
acl advanced 3000
rule 0 permit ip source 10.1.2.2 0 destination 10.1.1.2 0
#
acl advanced 3101
rule 0 permit ip source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
#
ipsec transform-set tran1
esp encryption-algorithm aes-cbc-128
esp authentication-algorithm sha1
#
ipsec policy use1 10 isakmp
transform-set tran1
security acl 3101
local-address 2.2.2.2
remote-address 2.2.2.1
ike-profile profile1
#
ike profile profile1
keychain keychain1
match remote identity address 2.2.2.1 255.255.255.0
#
ike keychain keychain1
pre-shared-key address 2.2.2.1 255.255.255.0 key cipher $c$3$FmI8sXpm7iD4vhMvu4cbssfcsSqiIQ==
验证:
[PC1]ping 10.1.2.2
Ping 10.1.2.2 (10.1.2.2): 56 data bytes, press CTRL_C to break
Request time out
56 bytes from 10.1.2.2: icmp_seq=1 ttl=253 time=12.063 ms
56 bytes from 10.1.2.2: icmp_seq=2 ttl=253 time=16.215 ms
56 bytes from 10.1.2.2: icmp_seq=3 ttl=253 time=2.534 ms
56 bytes from 10.1.2.2: icmp_seq=4 ttl=253 time=2.178 ms
--- Ping statistics for 10.1.2.2 ---
5 packet(s) transmitted, 4 packet(s) received, 20.0% packet loss
round-trip min/avg/max/std-dev = 2.178/8.248/16.215/6.073 ms
[PC1]%Apr 6 22:16:22:794 2017 PC1 PING/6/PING_STATISTICS: Ping statistics for 10.1.2.2: 5 packet(s) transmitted, 4 packet(s) received, 20.0% packet loss, round-trip min/avg/max/std-dev = 2.178/8.248/16.215/6.073 ms.
ipsec网络,当两端局域网ip重叠,可以通过PBR+nat outbound方式解决两端局域网访问不通的问题。
- 2024-11-26回答
- 评论(0)
- 举报
-
(0)
暂无评论
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明








暂无评论