MSR36-40 同一端口建立多个IPSEC隧道
- 0关注
- 0收藏,837浏览
问题描述:
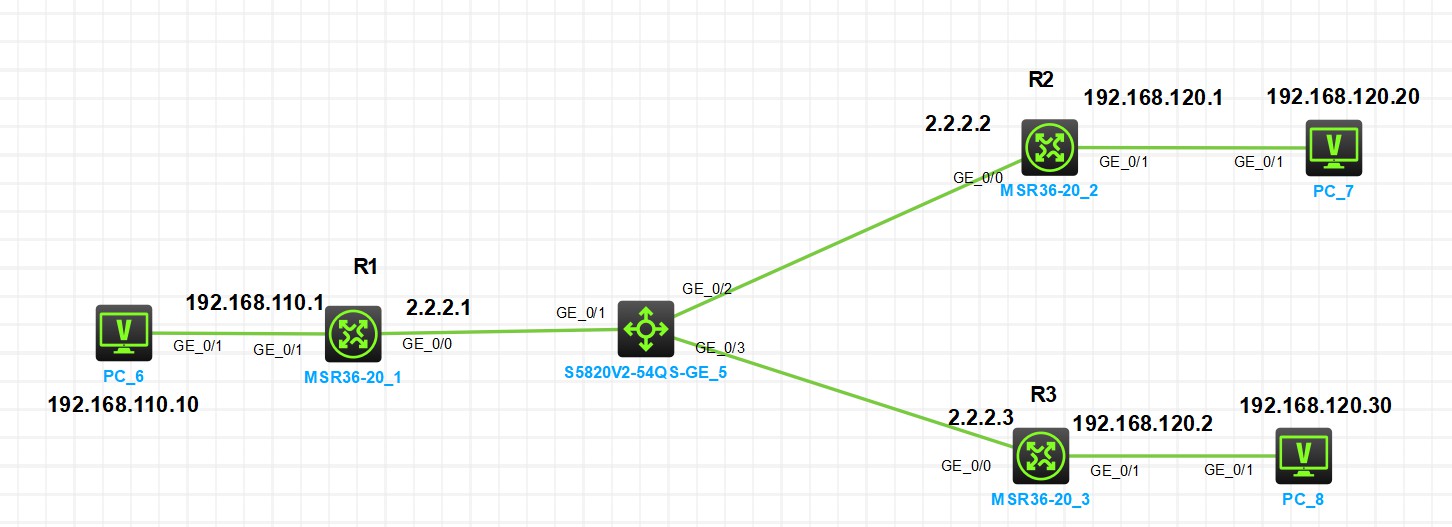
组网及组网描述:
要求在 R1 和 R2、R3....之间建立多个 IPsec 隧道,对 PC6所在的子网(192.168.110.0/24)与其他PC所在的子网(192.168.120.X/32)之间的数据流进行安全保护。
现在的思路是使用ipsec policy-template的方法。
进展是:R1和R2之间的IPSEC的SA协商没有通过。请帮忙看看,谢谢!
配置如下
R1
int gig 0/0ip addr 2.2.2.1 24quit
int gig 0/1ip addr 192.168.110.1 24quit
acl advanced 3101rule 0 permit ip source 192.168.110.0 0.0.0.255 destination 192.168.120.0 0.0.0.255quit
ipsec transform-set tran1encapsulation-mode tunnelprotocol espesp encryption-algorithm 3desesp authentication-algorithm sha1quit
ikev2 keychain keychain1peer ENBaddress 0.0.0.0 0.0.0.0identity fqdn branchpre-shared-key plaintext 123456quitquit
ikev2 profile profile1keychain keychain1match remote identity fqdn branchauthentication-method local pre-shareauthentication-method remote pre-sharequit
ipsec policy-template template1 1remote-address 2.2.2.2security acl 3101transform-set transform1ikev2-profile profile1quit
ipsec policy policy1 1 isakmp template template1ikev2 address-group template1 2.2.2.2 2.2.2.10 255.255.255.255
##int gig 0/0ipsec apply policy policy1quit
ip route-static 192.168.120.0 255.255.255.0 2.2.2.2-------------------------------------------------------R2
int gig 0/0ip addr 2.2.2.2 24quit
int gig 0/1ip addr 192.168.120.1 24quit
acl advanced 3101rule 0 permit ip source 192.168.120.0 0.0.0.255 destination 192.168.110.0 0.0.0.255quit
ipsec transform-set tran1encapsulation-mode tunnelprotocol espesp encryption-algorithm 3desesp authentication-algorithm sha1quit
ikev2 keychain keychain1peer ENBaddress 2.2.2.1 24identity address 2.2.2.1pre-shared-key plaintext 123456quitquit
ikev2 profile profile1identity local fqdn branchauthentication-method local pre-shareauthentication-method remote pre-sharekeychain keychain1match remote identity address 2.2.2.1 255.255.255.0quit
ipsec policy use1 10 isakmplocal-address 2.2.2.2remote-address 2.2.2.1security acl 3101transform-set tran1ikev2-profile profile1quit
int gig 0/0ipsec apply policy use1quit
ip route-static 192.168.110.0 255.255.255.0 2.2.2.1
- 2025-04-02提问
- 举报
-
(0)

keychain 里面的地址配置有问题吧,不要写子网掩码啊
- 2025-04-02回答
- 评论(8)
- 举报
-
(0)

(Tunnel ID 22): IKE SA deleted.
undo terminal debugging*Apr 3 03:00:35:467 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Received packet from 2.2.2.2 source port 500 destination port 500.
*Apr 3 03:00:35:467 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
I-SPI: 9d0d025d6c23ac37
R-SPI: 0000000000000000
Message ID: 0
Exchange type: SA_INIT
Flags: REQUEST, INITIATOR
Next payload: SA, Length: 400.
*Apr 3 03:00:35:467 2025 H3C IKEV2/7/FSM: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
(Tunnel ID 23): (R) Current State: IDLE.
*Apr 3 03:00:35:467 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Payload contents:
*Apr 3 03:00:35:467 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
SA Next payload: KE, Length: 80.
*Apr 3 03:00:35:467 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Last proposal: 0, Length: 76.
*Apr 3 03:00:35:467 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Proposal: 1, Protocol: IKE, SPI size: 0, Transform number: 8.
*Apr 3 03:00:35:467 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Last transform: 0x3, Length: 12.
*Apr 3 03:00:35:467 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Type: ENCR, Transform ID: AES-CBC.
*Apr 3 03:00:35:467 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Key length: 128.
*Apr 3 03:00:35:467 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Last transform: 0x3, Length: 8.
*Apr 3 03:00:35:467 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Type: ENCR, Transform ID: 3DES-CBC.
*Apr 3 03:00:35:467 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Last transform: 0x3, Length: 8.
*Apr 3 03:00:35:468 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Type: INTEG, Transform ID: AUTH-HMAC-SHA1-96.
*Apr 3 03:00:35:468 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Last transform: 0x3, Length: 8.
*Apr 3 03:00:35:468 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Type: INTEG, Transform ID: AUTH-HMAC-MD5-96.
*Apr 3 03:00:35:468 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Last transform: 0x3, Length: 8.
*Apr 3 03:00:35:468 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Type: PRF, Transform ID: PRF-HMAC-SHA1.
*Apr 3 03:00:35:468 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Last transform: 0x3, Length: 8.
*Apr 3 03:00:35:468 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Type: PRF, Transform ID: PRF-HMAC-MD5.
*Apr 3 03:00:35:468 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Last transform: 0x3, Length: 8.
*Apr 3 03:00:35:468 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Type: D-H, Transform ID: 1536-bit MODP/Group 5.
*Apr 3 03:00:35:468 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Last transform: 0, Length: 8.
*Apr 3 03:00:35:468 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Type: D-H, Transform ID: 1024-bit MODP/Group 2.
*Apr 3 03:00:35:468 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
KE Next payload: NONCE, Length: 200, DH: 1536-bit MODP/Group 5.
*Apr 3 03:00:35:468 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
NONCE Next payload: NOTIFY, Length: 36.
*Apr 3 03:00:35:468 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
NOTIFY Next payload: NOTIFY, Length: 28, Type: NAT_DETECTION_SOURCE_IP, Protocol: NO PROTOCOL, SPI size: 0.
*Apr 3 03:00:35:468 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
NOTIFY Next payload: NO_PAYLOAD, Length: 28, Type: NAT_DETECTION_DESTINATION_IP, Protocol: NO PROTOCOL, SPI size: 0.
*Apr 3 03:00:35:468 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Request has message id 0, expected from (0 ~ 0).
*Apr 3 03:00:35:468 2025 H3C IKEV2/7/FSM: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Search policy with vrf 0, local address 2.2.2.1.
*Apr 3 03:00:35:468 2025 H3C IKEV2/7/FSM: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Found default policy to use.
*Apr 3 03:00:35:468 2025 H3C IKEV2/7/FSM: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Process SA payload.
*Apr 3 03:00:35:468 2025 H3C IKEV2/7/FSM: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Process KE payload.
*Apr 3 03:00:35:468 2025 H3C IKEV2/7/FSM: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Process NAT discovery notify.
*Apr 3 03:00:35:468 2025 H3C IKEV2/7/FSM: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
No NAT found.
*Apr 3 03:00:35:468 2025 H3C IKEV2/7/FSM: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
(Tunnel ID 23): (R) Current State: PROC_INIT.
*Apr 3 03:00:35:468 2025 H3C IKEV2/7/FSM: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Search policy with vrf 0, local address 2.2.2.1.
*Apr 3 03:00:35:468 2025 H3C IKEV2/7/FSM: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Found default policy to use.
*Apr 3 03:00:35:468 2025 H3C IKEV2/7/FSM: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Construct SA payload.
*Apr 3 03:00:35:468 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Proposal 1.
*Apr 3 03:00:35:468 2025 H3C IKEV2/7/FSM: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Transform ENCR AES-CBC 128.
*Apr 3 03:00:35:468 2025 H3C IKEV2/7/FSM: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Transform INTEG AUTH-HMAC-SHA1-96.
*Apr 3 03:00:35:468 2025 H3C IKEV2/7/FSM: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Transform PRF PRF-HMAC-SHA1.
*Apr 3 03:00:35:468 2025 H3C IKEV2/7/FSM: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Transform D-H 1536-bit MODP/Group 5.
*Apr 3 03:00:35:487 2025 H3C IKEV2/7/FSM: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Compute DH public key, use 1536-bit MODP/Group 5.
*Apr 3 03:00:35:487 2025 H3C IKEV2/7/FSM: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Construct KE payload.
*Apr 3 03:00:35:487 2025 H3C IKEV2/7/FSM: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Construct NONCE payload.
*Apr 3 03:00:35:487 2025 H3C IKEV2/7/FSM: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Construct NOTIFY payload: NAT_DETECTION_SOURCE_IP.
*Apr 3 03:00:35:487 2025 H3C IKEV2/7/FSM: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Construct NOTIFY payload: NAT_DETECTION_DESTINATION_IP.
*Apr 3 03:00:35:487 2025 H3C IKEV2/7/FSM: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Construct CERTREQ payload.
*Apr 3 03:00:35:487 2025 H3C IKEV2/7/ERROR: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Construct CERTREQ payload failed.
*Apr 3 03:00:35:504 2025 H3C IKEV2/7/FSM: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Calculate SKEYSEED.
*Apr 3 03:00:35:505 2025 H3C IKEV2/7/TIMER: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Responder: start 30 secs wait auth timer.
*Apr 3 03:00:35:505 2025 H3C IKEV2/7/FSM: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
(Tunnel ID 23): (R) Current State: BUILD_INIT.
*Apr 3 03:00:35:505 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Payload contents:
*Apr 3 03:00:35:505 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
SA Next payload: KE, Length: 48.
*Apr 3 03:00:35:505 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Last proposal: 0, Length: 44.
*Apr 3 03:00:35:505 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Proposal: 1, Protocol: IKE, SPI size: 0, Transform number: 4.
*Apr 3 03:00:35:506 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Last transform: 0x3, Length: 12.
*Apr 3 03:00:35:506 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Type: ENCR, Transform ID: AES-CBC.
*Apr 3 03:00:35:506 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Key length: 128.
*Apr 3 03:00:35:506 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Last transform: 0x3, Length: 8.
*Apr 3 03:00:35:506 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Type: INTEG, Transform ID: AUTH-HMAC-SHA1-96.
*Apr 3 03:00:35:506 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Last transform: 0x3, Length: 8.
*Apr 3 03:00:35:506 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Type: PRF, Transform ID: PRF-HMAC-SHA1.
*Apr 3 03:00:35:506 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Last transform: 0, Length: 8.
*Apr 3 03:00:35:506 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Type: D-H, Transform ID: 1536-bit MODP/Group 5.
*Apr 3 03:00:35:506 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
KE Next payload: NONCE, Length: 200, DH: 1536-bit MODP/Group 5.
*Apr 3 03:00:35:506 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
NONCE Next payload: NOTIFY, Length: 36.
*Apr 3 03:00:35:506 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
NOTIFY Next payload: NOTIFY, Length: 28, Type: NAT_DETECTION_SOURCE_IP, Protocol: NO PROTOCOL, SPI size: 0.
*Apr 3 03:00:35:506 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
NOTIFY Next payload: NO_PAYLOAD, Length: 28, Type: NAT_DETECTION_DESTINATION_IP, Protocol: NO PROTOCOL, SPI size: 0.
*Apr 3 03:00:35:506 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Sending packet to 2.2.2.2 remote port 500, local port 500.
*Apr 3 03:00:35:506 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
I-SPI: 9d0d025d6c23ac37
R-SPI: c21376a2d67e8df7
Message ID: 0
Exchange type: SA_INIT
Flags: RESPONSE
Next payload: SA, Length: 368.
*Apr 3 03:00:35:506 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Sending an IPv4 packet.
*Apr 3 03:00:35:506 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Sent response with message id 0, requests can be accepted from (1 ~ 1).
*Apr 3 03:00:35:525 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Received packet from 2.2.2.2 source port 500 destination port 500.
*Apr 3 03:00:35:525 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
I-SPI: 9d0d025d6c23ac37
R-SPI: c21376a2d67e8df7
Message ID: 1
Exchange type: AUTH
Flags: REQUEST, INITIATOR
Next payload: ENCRYPTED, Length: 268.
*Apr 3 03:00:35:525 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Payload contents:
*Apr 3 03:00:35:525 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Parse the last payload (ENCRYPTED payload).
*Apr 3 03:00:35:526 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Integrity check passed.
*Apr 3 03:00:35:526 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
IDi Next payload: NOTIFY, Length: 14, Type: ID_FQDN.
*Apr 3 03:00:35:526 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
NOTIFY Next payload: AUTH, Length: 8, Type: INITIAL_CONTACT, Protocol: NO PROTOCOL, SPI size: 0.
*Apr 3 03:00:35:526 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
AUTH Next payload: NOTIFY, Length: 28, Method: Pre-shared key.
*Apr 3 03:00:35:526 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
NOTIFY Next payload: NOTIFY, Length: 8, Type: ESP_TFC_PADDING_NOT_SUPPORTED, Protocol: NO PROTOCOL, SPI size: 0.
*Apr 3 03:00:35:526 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
NOTIFY Next payload: NOTIFY, Length: 8, Type: NON_FIRST_FRAGMENTS_ALSO, Protocol: NO PROTOCOL, SPI size: 0.
*Apr 3 03:00:35:526 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
NOTIFY Next payload: SA, Length: 8, Type: IKEV2_MESSAGE_ID_SYNC_SUPPORTED, Protocol: NO PROTOCOL, SPI size: 0.
*Apr 3 03:00:35:526 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
SA Next payload: TSi, Length: 40.
*Apr 3 03:00:35:526 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Last proposal: 0, Length: 36.
*Apr 3 03:00:35:526 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Proposal: 1, Protocol: ESP, SPI size: 4, Transform number: 3.
*Apr 3 03:00:35:526 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Last transform: 0x3, Length: 8.
*Apr 3 03:00:35:526 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Type: INTEG, Transform ID: AUTH-HMAC-SHA1-96.
*Apr 3 03:00:35:527 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Last transform: 0x3, Length: 8.
*Apr 3 03:00:35:527 2025 H3C IKEV2/7/PACKET: vrf = 0, src = 2.2.2.1, dst = 2.2.2.2/500
Type: ENCR, Transform ID: 3DES-CBC.
- 2025-04-03回答
- 评论(0)
- 举报
-
(0)
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明


谢谢