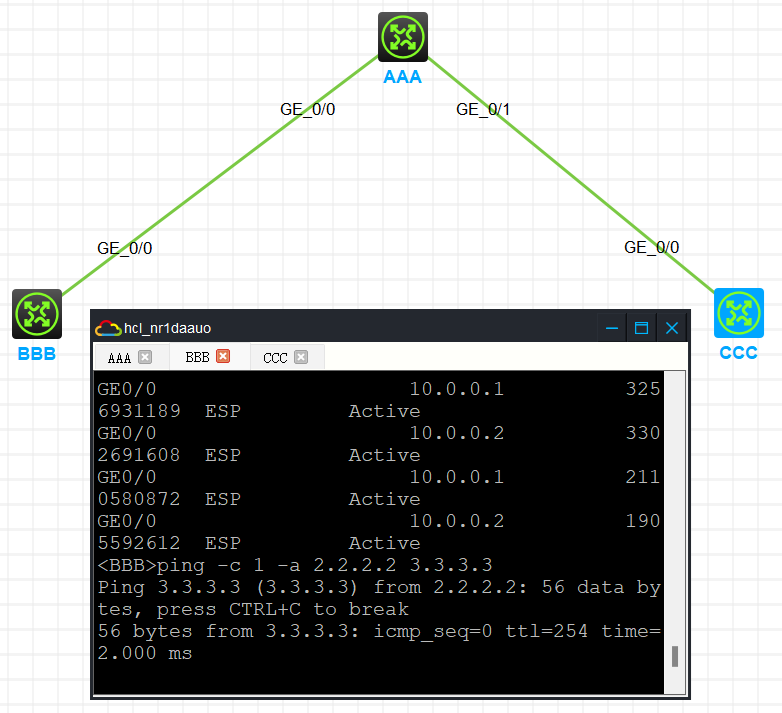
模拟器配置多分支ipsec不通
- 0关注
- 0收藏,824浏览
问题描述:
查看IKE sa和ipsec sa都没问题,就是ping不通
A设备配置
interface GigabitEthernet0/0
port link-mode route
combo enable copper
ip address 10.0.0.1 255.255.255.0
ipsec apply policy 22
#
interface GigabitEthernet0/1
port link-mode route
combo enable copper
ip address 10.0.1.1 255.255.255.0
ipsec apply policy 22
#
ipsec transform-set 1
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
#
ipsec policy-template 22 1
transform-set 1
security acl 3000
ike-profile B
#
ipsec policy-template 33 1
transform-set 1
security acl 3100
ike-profile C
#
ipsec policy 22 1 isakmp template 22
#
ipsec policy 22 2 isakmp template 33
#
ike identity fqdn AAA
#
ike profile B
keychain B
exchange-mode aggressive
local-identity fqdn AAA
match remote identity fqdn BBB
#
ike profile C
keychain C
exchange-mode aggressive
local-identity fqdn AAA
match remote identity fqdn CCC
#
ike keychain B
pre-shared-key hostname BBB key cipher $c$3$eh2VpqPO1Y/PwMlyYc3PKryT8KmTYqCkVQ==
#
ike keychain C
pre-shared-key hostname CCC key cipher $c$3$Ecg3VJka+w4NTWJeyJofHWAkZJCDMyIGcw==
#
acl advanced 3000
rule 0 permit ip source 1.1.1.1 0 destination 2.2.2.2 0
rule 5 permit ip source 3.3.3.3 0 destination 2.2.2.2 0
#
acl advanced 3100
rule 0 permit ip source 1.1.1.1 0 destination 3.3.3.3 0
rule 5 permit ip source 2.2.2.2 0 destination 3.3.3.3 0
B设备配置
interface LoopBack0
ip address 2.2.2.2 255.255.255.0
#
interface GigabitEthernet0/0
port link-mode route
combo enable copper
ip address 10.0.0.2 255.255.255.0
ipsec apply policy 1
#
ipsec transform-set 1
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
#
ipsec policy 1 1 isakmp
transform-set 1
security acl 3000
remote-address 10.0.0.1
ike-profile 1
#
ike identity fqdn BBB
#
ike profile 1
keychain 1
exchange-mode aggressive
local-identity fqdn BBB
match remote identity fqdn AAA
#
ike keychain 1
pre-shared-key address 10.0.0.1 255.255.255.255 key cipher $c$3$ju6mTxpNNK6XKQ2ZFwrNfkFSSUPj1uiGLw==
#
acl advanced 3000
rule 0 permit ip source 2.2.2.2 0 destination 1.1.1.1 0
rule 5 permit ip source 2.2.2.2 0 destination 3.3.3.3 0
#
C设备配置
interface LoopBack0
ip address 3.3.3.3 255.255.255.0
#
interface GigabitEthernet0/0
port link-mode route
combo enable copper
ip address 10.0.1.2 255.255.255.0
ipsec apply policy 1
#
ipsec transform-set 1
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
#
ipsec policy 1 1 isakmp
transform-set 1
security acl 3000
remote-address 10.0.1.1
ike-profile 1
#
ike identity fqdn CCC
#
ike profile 1
keychain 1
exchange-mode aggressive
local-identity fqdn CCC
match remote identity fqdn AAA
#
ike keychain 1
pre-shared-key address 10.0.1.1 255.255.255.255 key cipher $c$3$QjpJY4GnAog+Zp1m5RwtToXnw2HgqxCIQQ==
#
acl advanced 3000
rule 0 permit ip source 3.3.3.3 0 destination 1.1.1.1 0
rule 5 permit ip source 3.3.3.3 0 destination 2.2.2.2 0
组网及组网描述:
在A上查看的sa
<AAA>dis ike sa
Connection-ID Local Remote Flag DOI
-------------------------------------------------------------------------
1 10.0.0.1 10.0.0.2 RD IPsec
2 10.0.1.1 10.0.1.2 RD IPsec
Flags:
RD--READY RL--REPLACED FD-FADING RK-REKEY
<AAA>dis ipsec sa
-------------------------------
Interface: GigabitEthernet0/0
-------------------------------
-----------------------------
IPsec policy: 22
Sequence number: 1
Mode: Template
-----------------------------
Tunnel id: 2
Encapsulation mode: tunnel
Perfect Forward Secrecy:
Inside VPN:
Extended Sequence Numbers enable: N
Traffic Flow Confidentiality enable: N
Transmitting entity: Responder
Path MTU: 1444
Tunnel:
local address: 10.0.0.1
remote address: 10.0.0.2
Flow:
sour addr: 3.3.3.3/255.255.255.255 port: 0 protocol: ip
dest addr: 2.2.2.2/255.255.255.255 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 1471197854 (0x57b0b29e)
Connection ID: 12884901891
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843200/1574
Max received sequence-number: 0
Anti-replay check enable: Y
Anti-replay window size: 64
UDP encapsulation used for NAT traversal: N
Status: Active
[Outbound ESP SAs]
SPI: 1577153356 (0x5e01734c)
Connection ID: 12884901890
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843200/1574
Max sent sequence-number: 0
UDP encapsulation used for NAT traversal: N
Status: Active
-----------------------------
IPsec policy: 22
Sequence number: 1
Mode: Template
-----------------------------
Tunnel id: 0
Encapsulation mode: tunnel
Perfect Forward Secrecy:
Inside VPN:
Extended Sequence Numbers enable: N
Traffic Flow Confidentiality enable: N
Transmitting entity: Responder
Path MTU: 1444
Tunnel:
local address: 10.0.0.1
remote address: 10.0.0.2
Flow:
sour addr: 1.1.1.1/255.255.255.255 port: 0 protocol: ip
dest addr: 2.2.2.2/255.255.255.255 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 1970886898 (0x757958f2)
Connection ID: 12884901895
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843200/1559
Max received sequence-number: 0
Anti-replay check enable: Y
Anti-replay window size: 64
UDP encapsulation used for NAT traversal: N
Status: Active
[Outbound ESP SAs]
SPI: 2652031688 (0x9e12cac8)
Connection ID: 12884901894
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843200/1559
Max sent sequence-number: 0
UDP encapsulation used for NAT traversal: N
Status: Active
-------------------------------
Interface: GigabitEthernet0/1
-------------------------------
-----------------------------
IPsec policy: 22
Sequence number: 2
Mode: Template
-----------------------------
Tunnel id: 3
Encapsulation mode: tunnel
Perfect Forward Secrecy:
Inside VPN:
Extended Sequence Numbers enable: N
Traffic Flow Confidentiality enable: N
Transmitting entity: Responder
Path MTU: 1444
Tunnel:
local address: 10.0.1.1
remote address: 10.0.1.2
Flow:
sour addr: 2.2.2.2/255.255.255.255 port: 0 protocol: ip
dest addr: 3.3.3.3/255.255.255.255 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 2924452425 (0xae4f9a49)
Connection ID: 12884901889
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843200/1565
Max received sequence-number: 0
Anti-replay check enable: Y
Anti-replay window size: 64
UDP encapsulation used for NAT traversal: N
Status: Active
[Outbound ESP SAs]
SPI: 224059300 (0x0d5adfa4)
Connection ID: 12884901888
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843200/1565
Max sent sequence-number: 0
UDP encapsulation used for NAT traversal: N
Status: Active
-----------------------------
IPsec policy: 22
Sequence number: 2
Mode: Template
-----------------------------
Tunnel id: 1
Encapsulation mode: tunnel
Perfect Forward Secrecy:
Inside VPN:
Extended Sequence Numbers enable: N
Traffic Flow Confidentiality enable: N
Transmitting entity: Responder
Path MTU: 1444
Tunnel:
local address: 10.0.1.1
remote address: 10.0.1.2
Flow:
sour addr: 1.1.1.1/255.255.255.255 port: 0 protocol: ip
dest addr: 3.3.3.3/255.255.255.255 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 2618482348 (0x9c12deac)
Connection ID: 12884901893
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843200/1552
Max received sequence-number: 0
Anti-replay check enable: Y
Anti-replay window size: 64
UDP encapsulation used for NAT traversal: N
Status: Active
[Outbound ESP SAs]
SPI: 1224906267 (0x4902961b)
Connection ID: 12884901892
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843200/1552
Max sent sequence-number: 0
UDP encapsulation used for NAT traversal: N
Status: Active
- 2025-04-27提问
- 举报
-
(0)
最佳答案

首先排查路由问题,看情况,个人觉得重点查一下总部有没有到分支的路由
- 2025-04-27回答
- 评论(1)
- 举报
-
(0)
直连的还要什么路由啊?
直连的还要什么路由啊?


编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明