Ipsec 对接
- 0关注
- 0收藏,728浏览
问题描述:
总部与两个分支对接ipsec,总部与分支1已成功对接成功,总部与分支2对接不成功,但是总部与分支2查看ike 都已经成功,但是ipsec不成功。总部与两个分支对接,必须要使用策略模版吗?
- 2025-06-12提问
- 举报
-
(0)
最佳答案

不是的
1、组网
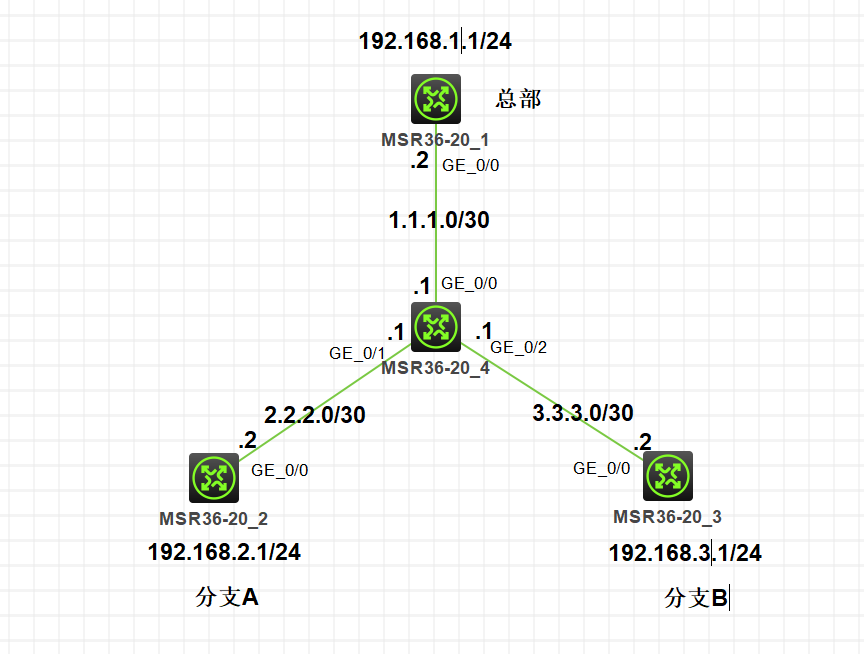
2、需求
配置步骤
3、关键配置
总部:
#
interface GigabitEthernet0/0
port link-mode route
combo enable copper
ip address 1.1.1.2 255.255.255.252
nat outbound 3002
ipsec apply policy test
#
ip route-static 0.0.0.0 0 1.1.1.1
#
acl advanced 3000
description toBranchA
rule 0 permit ip source 192.168.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
rule 5 permit ip source 192.168.3.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
#
acl advanced 3001
description toBranchB
rule 0 permit ip source 192.168.1.0 0.0.0.255 destination 192.168.3.0 0.0.0.255
rule 5 permit ip source 192.168.2.0 0.0.0.255 destination 192.168.3.0 0.0.0.255
#
acl advanced 3002
description outboundNATDenyFlow
rule 0 deny ip source 192.168.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
rule 5 deny ip source 192.168.3.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
rule 10 deny ip source 192.168.1.0 0.0.0.255 destination 192.168.3.0 0.0.0.255
rule 15 deny ip source 192.168.2.0 0.0.0.255 destination 192.168.3.0 0.0.0.255
rule 100 permit ip
#
ipsec transform-set 1
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
#
ipsec policy-template branchA 1
transform-set 1
security acl 3000
ike-profile branchA
#
ipsec policy-template branchB 1
transform-set 1
security acl 3001
ike-profile branchB
#
ipsec policy test 1 isakmp template branchA
#
ipsec policy test 2 isakmp template branchB
#
ike dpd interval 10 on-deman
#
ike profile branchA
keychain branchA
exchange-mode aggressive
local-identity fqdn headquarters
match remote identity fqdn branchA
#
ike profile branchB
keychain branchB
exchange-mode aggressive
local-identity fqdn headquarters
match remote identity fqdn branchB
#
ike proposal 1
encryption-algorithm 3des-cbc
authentication-algorithm md5
#
ike keychain branchA
match local address 1.1.1.2
pre-shared-key hostname branchA key cipher $c$3$nng95cm/zlG3ghvIRim5saZ3bMEhoJD+Ow==
#
ike keychain branchB
match local address 1.1.1.2
pre-shared-key hostname branchB key cipher $c$3$Rl2okdkTYNBEYWd32X25LOWYkYo5YCcrgw==
#
分支A
#
nqa entry admin test
type icmp-echo
destination ip 192.168.1.1
frequency 5000
history-record enable
history-record number 10
probe count 10
probe timeout 500
source ip 192.168.2.1
#
nqa entry admin test1
type icmp-echo
destination ip 192.168.3.1
frequency 5000
history-record enable
history-record number 10
probe count 10
probe timeout 500
source ip 192.168.2.1
#
nqa schedule admin test start-time now lifetime forever
nqa schedule admin test1 start-time now lifetime forever
#
interface GigabitEthernet0/0
port link-mode route
combo enable copper
ip address 2.2.2.2 255.255.255.252
nat outbound 3001
ipsec apply policy 1
#
ip route-static 0.0.0.0 0 2.2.2.1
#
acl advanced 3000
rule 0 permit ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
rule 5 permit ip source 192.168.2.0 0.0.0.255 destination 192.168.3.0 0.0.0.255
#
acl advanced 3001
rule 0 deny ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
rule 5 deny ip source 192.168.2.0 0.0.0.255 destination 192.168.3.0 0.0.0.255
rule 100 permit ip
#
ipsec transform-set 1
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
#
ipsec policy 1 1 isakmp
transform-set 1
security acl 3000
remote-address 1.1.1.2
ike-profile 1
#
ike dpd interval 10 on-demand
#
ike profile 1
keychain 1
exchange-mode aggressive
local-identity fqdn branchA
match remote identity fqdn headquarters
#
ike proposal 1
encryption-algorithm 3des-cbc
authentication-algorithm md5
#
ike keychain 1
pre-shared-key address 1.1.1.2 255.255.255.0 key cipher $c$3$5QlYyBFEZTju/oTPut9zgP5JNpmVleBIbA==
#
#
nqa entry admin test
type icmp-echo
destination ip 192.168.1.1
frequency 5000
history-record enable
history-record number 10
probe count 10
probe timeout 500
source ip 192.168.3.1
#
nqa entry admin test1
type icmp-echo
destination ip 192.168.2.1
frequency 5000
history-record enable
history-record number 10
probe count 10
probe timeout 500
source ip 192.168.3.1
#
nqa schedule admin test start-time now lifetime forever
nqa schedule admin test1 start-time now lifetime forever
#
interface GigabitEthernet0/0
port link-mode route
combo enable copper
ip address 3.3.3.2 255.255.255.252
nat outbound 3001
ipsec apply policy 1
#
ip route-static 0.0.0.0 0 3.3.3.1
#
acl advanced 3000
rule 0 permit ip source 192.168.3.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
rule 5 permit ip source 192.168.3.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
#
acl advanced 3001
rule 0 deny ip source 192.168.3.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
rule 5 deny ip source 192.168.3.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
rule 100 permit ip
#
ipsec transform-set 1
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
#
ipsec policy 1 1 isakmp
transform-set 1
security acl 3000
remote-address 1.1.1.2
ike-profile 1
#
ike dpd interval 10 on-demand
#
ike profile 1
keychain 1
exchange-mode aggressive
local-identity fqdn branchB
match remote identity fqdn headquarters
#
ike proposal 1
encryption-algorithm 3des-cbc
authentication-algorithm md5
#
ike keychain 1
pre-shared-key address 1.1.1.2 255.255.255.0 key cipher $c$3$5QlYyBFEZTju/oTPut9zgP5JNpmVleBIbA==
#
4、测试
- 2025-06-12回答
- 评论(0)
- 举报
-
(0)

在IPsec配置中,策略模版并非必须使用,但它提供了一种灵活的配置方式,特别是在多分支与中心总部的连接场景中。策略模版允许中心设备(如总部)使用一个模板来定义IPsec策略,而分支设备则可以基于这个模板自动建立连接,无需每个分支都单独配置策略。
对于您提到的情况,总部与分支1成功对接,而与分支2的IPsec不成功,尽管IKE阶段已经成功,这可能是因为IPsec策略配置不匹配或网络配置问题。以下是一些可能的检查点:
1. **IPsec策略匹配**:确保总部和分支2的IPsec策略(包括加密算法、认证算法、生命周期等)完全匹配。
2. **ACL配置**:检查ACL是否正确配置,确保它允许总部与分支2之间的流量。
3. **接口配置**:确认总部的接口上正确应用了IPsec策略。
4. **NAT穿越**:如果存在NAT,确保NAT穿越配置正确,尤其是在总部的防火墙上。
5. **安全域和策略**:如果总部是防火墙,检查相关接口是否已加入到正确的安全域,并且安全策略是否允许流量通过。
如果总部与两个分支的连接都使用策略模版,这将简化配置管理,但不是唯一的方法。您可以根据具体需求选择是否使用策略模版。如果遇到配置问题,检查上述提到的配置点,以确定问题所在。
- 2025-06-13回答
- 评论(0)
- 举报
-
(0)
暂无评论
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明


暂无评论