MSR3600 v7查看wan口流量监控是需要额外license吗?
- 0关注
- 0收藏,663浏览
最佳答案

不需要license,可以看下web和命令行是不是混配了,导致web没办法正确识别wan口 所以无法读取流量
- 2025-08-07回答
- 评论(2)
- 举报
-
(0)
<MSR3600-xijie-26>dis cur # version 7.1.064, Release 6749P30 # sysname MSR3600-xijie-26 # clock timezone ShangHai add 08:00:00 clock protocol ntp # wlan global-configuration # telnet server enable telnet server acl 2422 telnet server ipv6 acl ipv6 2622 # undo resource-monitor output syslog snmp-notification netconf-event # track 1 nqa entry admin china_unicom_ping reaction 1 # ip pool 2 172.16.2.50 172.16.2.250 ip pool 3 172.16.3.50 172.16.3.250 # dhcp enable dhcp server forbidden-ip 10.3.0.0 10.3.0.50 dhcp server forbidden-ip 192.168.1.1 192.168.1.255 dhcp server forbidden-ip 192.168.11.0 192.168.11.50 dhcp server always-broadcast # dns proxy enable dns server 223.5.5.5 dns server 223.6.6.6 ip host ***.*** 10.3.0.31 ipv6 dns server 2400:3200::1 ipv6 dns server 2400:3200:BABA::1 # ipv6 dhcp prefix-pool 1 prefix FDFD::/64 assign-len 64 # system-working-mode standard password-recovery enable # vlan 1 # vlan 2 description PPPoE PAP # vlan 3 description PPPoE CHAP # vlan 13 description WiFi China-Telecom # vlan 14 description WiFi China-Unicom # vlan 15 description WiFi China-Mobile # vlan 16 description second session for China-Telecom # traffic behavior test # dhcp server ip-pool ap_and_router_pool gateway-list 10.3.0.11 network 10.3.0.0 mask 255.255.0.0 option 43 hex 80070000010a0d001f # dhcp server ip-pool china_mobile_user_pool gateway-list 10.15.0.11 network 10.15.0.0 mask 255.255.0.0 dns-list 223.5.5.5 223.6.6.6 # dhcp server ip-pool china_telecom_user_pool gateway-list 10.13.0.11 network 10.13.0.0 mask 255.255.0.0 dns-list 223.5.5.5 223.6.6.6 # dhcp server ip-pool china_unicom_user_pool gateway-list 10.14.0.11 network 10.14.0.0 mask 255.255.0.0 dns-list 223.5.5.5 223.6.6.6 # dhcp server ip-pool lan_pool gateway-list 192.168.11.11 network 192.168.0.0 mask 255.255.0.0 dns-list 192.168.11.11 static-bind ip-address 192.168.1.6 mask 255.255.0.0 client-identifier 085b-d6cf-31bd description windows10 static-bind ip-address 192.168.1.7 mask 255.255.0.0 client-identifier 0108-5bd6-cf31-bd description windows10 # ipv6 dhcp pool ipv6_lan_pool network FDFD::/64 dns-server 2400:3200::1 dns-server 2400:3200:BABA::1 prefix-pool 1 preferred-lifetime 86400 valid-lifetime 259200 gateway-list FDFD::1111 # policy-based-route rt_china_mobile permit node 15 apply default-output-interface Dialer15 # policy-based-route rt_china_telecom permit node 13 apply default-output-interface Dialer13 # policy-based-route rt_china_unicom permit node 14 apply default-output-interface Dialer14 # nqa entry admin china_mobile_ping type icmp-echo description China-Mobile offline destination ip 123.125.81.6 frequency 2000 history-record enable history-record keep-time 10 probe count 15 probe timeout 2000 reaction 1 checked-element probe-fail threshold-type accumulate 10 action-type trap-only source interface Vlan-interface15 # nqa entry admin china_unicom_ping type icmp-echo destination ip 223.5.5.5 frequency 2000 history-record enable history-record number 20 history-record keep-time 10 reaction 1 checked-element probe-fail threshold-type consecutive 10 action-type trigger-only source interface Vlan-interface14 # nqa entry admin keep_alive_ping type icmp-echo description 2 seconds * 15 count ping response average time > 300ms destination ip 202.96.128.86 frequency 2000 history-record enable history-record keep-time 10 probe count 15 probe timeout 2000 reaction 1 checked-element probe-duration threshold-type average threshold-value 300 0 action-type trap-only source interface Vlan-interface13 # nqa schedule admin keep_alive_ping start-time now lifetime forever # controller Cellular0/0 # interface Aux0 # interface Dialer13 mtu 1492 ppp chap password cipher $c$3$kYT/vziyH1U0YQ6OfLHRmoXqY0t7Qf+nhU7i ppp chap user 111111@163.gd ppp ipcp dns admit-any ppp ipcp dns request ppp pap local-user 111111@163.gd password cipher $c$3$kKrChAaZqyIedKqbXFE81NevpjGHdQcUdEYu dialer bundle enable dialer timer idle 0 dialer timer autodial 20 ip address ppp-negotiate tcp mss 1400 nat outbound 2413 nat66 source acl 2613 easy-ip ipv6 address auto # interface Dialer14 mtu 1492 ppp chap password cipher $c$3$aCLt1ixR2i7Q7RehspYQPSrd+1fLMu3Mfw== ppp chap user 111111@16900.gd ppp ipcp dns admit-any ppp ipcp dns request ppp pap local-user 111111@16900.gd password cipher $c$3$3yoZ++An9C4l0RnHGOcnwSXKCw59oM7MUg== dialer bundle enable dialer timer idle 0 dialer timer autodial 20 ip address ppp-negotiate tcp mss 1400 nat outbound 2413 nat66 source acl 2613 easy-ip # interface Dialer15 mtu 1492 ppp chap password cipher $c$3$UmFXD+IZ5FAMmdt5TrdIQfN8jfcff3uB+Q== ppp chap user 1111111@139.gd ppp ipcp dns admit-any ppp ipcp dns request ppp pap local-user 1111111@139.gd password cipher $c$3$BVMER0vZrE4tCVLvL2cMoTNYRea8ubJqOw== dialer bundle enable dialer timer idle 0 dialer timer autodial 20 ip address ppp-negotiate tcp mss 1400 nat outbound 2413 nat66 source acl 2613 easy-ip ipv6 address auto # interface Virtual-Template0 # interface Virtual-Template2 ppp authentication-mode pap domain chap_auth_domain ppp ipcp dns 172.16.2.11 remote address pool 2 ppp account-statistics enable ip address 172.16.2.11 255.255.255.0 # interface Virtual-Template3 ppp authentication-mode chap domain chap_auth_domain ppp ipcp dns 172.16.3.11 remote address pool 3 ppp account-statistics enable ip address 172.16.3.11 255.255.255.0 # interface NULL0 # interface Vlan-interface1 ip address 192.168.11.11 255.255.0.0 ipv6 dhcp select server ipv6 dhcp server allow-hint preference 255 rapid-commit ipv6 address FDFD::1111/64 ipv6 nd autoconfig managed-address-flag ipv6 nd autoconfig other-flag undo ipv6 nd ra halt # interface Vlan-interface2 description interface ip as PAP gateway to dhcp for user ip address 10.2.0.11 255.255.0.0 pppoe-server bind virtual-template 2 # interface Vlan-interface3 description interface ip as CHAP gateway to dhcp for user ip address 10.3.0.11 255.255.0.0 pppoe-server bind virtual-template 3 # interface Vlan-interface13 description WiFi China-Telecom ip address 10.13.0.11 255.255.0.0 ip policy-based-route rt_china_telecom # interface Vlan-interface14 description WiFi China-Unicom ip address 10.14.0.11 255.255.0.0 ip policy-based-route rt_china_unicom # interface Vlan-interface15 description WiFi China-Mobile ip address 10.15.0.11 255.255.0.0 ip policy-based-route rt_china_mobile # interface GigabitEthernet0/0 port link-mode route description China-Telecom WAN port pppoe-client dial-bundle-number 13 # interface GigabitEthernet0/1 port link-mode route description China-Unicom WAN port pppoe-client dial-bundle-number 14 # interface GigabitEthernet0/2 port link-mode route description China-Mobile WAN port pppoe-client dial-bundle-number 15 # interface GigabitEthernet0/3 port link-mode bridge description lan port #1 (don't change this!!!) port link-type trunk port trunk permit vlan all # interface GigabitEthernet0/4 port link-mode bridge description lan port #2 port link-type trunk port trunk permit vlan all # interface GigabitEthernet0/5 port link-mode bridge # interface GigabitEthernet0/6 port link-mode bridge # interface GigabitEthernet0/7 port link-mode bridge description lan port #5 port link-type trunk undo port trunk permit vlan 1 port trunk permit vlan 3 13 to 15 port trunk pvid vlan 3 # interface GigabitEthernet0/8 port link-mode bridge # interface GigabitEthernet0/9 port link-mode bridge # interface GigabitEthernet0/10 port link-mode bridge # interface GigabitEthernet0/11 port link-mode bridge # interface GigabitEthernet0/12 port link-mode bridge # interface GigabitEthernet0/13 port link-mode bridge # interface GigabitEthernet0/14 port link-mode bridge # interface GigabitEthernet0/15 port link-mode bridge port access vlan 16 # interface GigabitEthernet0/16 port link-mode bridge description 2nd session for China-Telecom (WAN port) port access vlan 16 shutdown # interface GigabitEthernet0/17 port link-mode bridge # interface GigabitEthernet0/18 port link-mode bridge # interface GigabitEthernet0/19 port link-mode bridge # interface GigabitEthernet0/20 port link-mode bridge # interface GigabitEthernet0/21 port link-mode bridge # interface GigabitEthernet0/22 port link-mode bridge # interface GigabitEthernet0/23 port link-mode bridge # interface GigabitEthernet0/24 port link-mode bridge # interface GigabitEthernet0/25 port link-mode bridge # interface GigabitEthernet0/26 port link-mode bridge # interface GigabitEthernet0/27 port link-mode bridge description optical fiber port (SFP) port access vlan 16 # scheduler logfile size 16 # scheduler job reconnect command 1 dialer disconnect interface Dialer 13 # scheduler job saveconfig command 1 save force # scheduler schedule reconnect user-role network-operator user-role network-admin job reconnect time repeating at 04:00 # scheduler schedule saveconfig user-role network-operator user-role network-admin job saveconfig time repeating at 23:00 # line class aux user-role network-admin # line class tty user-role network-operator # line class vty user-role network-operator # line aux 0 user-role network-admin # line vty 0 4 authentication-mode scheme user-role network-operator idle-timeout 1440 0 # line vty 5 63 authentication-mode scheme user-role network-operator # ip route-static 0.0.0.0 0 Dialer13 preference 30 description China-Telecom ip route-static 0.0.0.0 0 Dialer14 preference 20 description China-Unicom num smaller higher priority ip route-static 0.0.0.0 0 Dialer15 preference 10 description China-Mobile ipv6 route-static :: 0 Dialer13 preference 10 description prefer China-Telecom ipv6 route-static :: 0 Dialer15 preference 30 description China-Mobile # snmp-agent snmp-agent local-engineid 0123456789 snmp-agent sys-info version all undo snmp-agent trap enable bfd undo snmp-agent trap enable configuration undo snmp-agent trap enable fr undo snmp-agent trap enable ifmonitor undo snmp-agent trap enable mac-address undo snmp-agent trap enable standard undo snmp-agent trap enable system snmp-agent trap source Dialer13 # performance-management # ssh server enable sftp server enable ssh server acl 2422 ssh server ipv6 acl ipv6 2622 # ntp-service enable ntp-service unicast-server 203.107.6.88 # acl number 2011 description outbound ACL for nqa client rule 0 permit source 192.168.0.0 0.0.255.255 rule 13 permit source 10.13.0.0 0.0.255.255 rule 14 permit source 10.14.0.0 0.0.255.255 rule 15 permit source 10.15.0.0 0.0.255.255 rule 20 permit source 172.16.2.0 0.0.0.255 rule 30 permit source 172.16.3.0 0.0.0.255 rule 100 deny # acl number 2013 description allow any SSID source ip packet rule 13 permit source 10.13.0.0 0.0.255.255 # acl number 2014 description allow any SSID source ip packet rule 14 permit source 10.14.0.0 0.0.255.255 # acl number 2015 description allow any SSID source ip packet rule 15 permit source 10.15.0.0 0.0.255.255 # acl number 2413 description Allow WAN NAT (IPv4) rule 0 permit source 192.168.0.0 0.0.255.255 rule 13 permit source 10.13.0.0 0.0.255.255 rule 14 permit source 10.14.0.0 0.0.255.255 rule 15 permit source 10.15.0.0 0.0.255.255 rule 20 permit source 172.16.2.0 0.0.0.255 rule 30 permit source 172.16.3.0 0.0.0.255 rule 100 deny # acl number 2422 description Allow FTP, SSH, SFTP, TFTP, Telnet (IPv4) rule 0 permit source 192.168.0.0 0.0.255.255 rule 3 permit source 10.3.0.0 0.0.255.255 rule 13 permit source 10.13.0.0 0.0.255.255 rule 14 permit source 10.14.0.0 0.0.255.255 rule 15 permit source 10.15.0.0 0.0.255.255 rule 20 permit source 172.16.2.0 0.0.0.255 rule 30 permit source 172.16.3.0 0.0.0.255 rule 100 deny # acl ipv6 number 2613 description Allow WAN NAT (IPv6) rule 0 permit source FDFD::/64 rule 100 deny # acl ipv6 number 2622 description Allow FTP, SSH, Telnet (IPv6) rule 0 permit source FDFD::/64 rule 100 deny # acl ipv6 number 2623 description Allow WAN NAT66 rule 0 permit source FDFD::/64 rule 100 deny # tftp-server acl 2422 # tftp server enable # password-control enable undo password-control aging enable undo password-control history enable password-control length 6 password-control login-attempt 3 exceed lock-time 10 password-control update-interval 0 password-control login idle-time 0 # radius-server test-profile user_probe username user_probe@MSR3600-xijie-26 interval 1 # domain chap_auth_domain authentication ppp radius-scheme eap_and_mac_radius_server authorization ppp radius-scheme eap_and_mac_radius_server accounting ppp radius-scheme eap_and_mac_radius_server # domain system # domain default enable chap_auth_domain # role name level-0 description Predefined level-0 role # role name level-1 description Predefined level-1 role # role name level-2 description Predefined level-2 role # role name level-3 description Predefined level-3 role # role name level-4 description Predefined level-4 role # role name level-5 description Predefined level-5 role # role name level-6 description Predefined level-6 role # role name level-7 description Predefined level-7 role # role name level-8 description Predefined level-8 role # role name level-9 description Predefined level-9 role # role name level-10 description Predefined level-10 role # role name level-11 description Predefined level-11 role # role name level-12 description Predefined level-12 role # role name level-13 description Predefined level-13 role # role name level-14 description Predefined level-14 role # user-group system # local-user admin class manage service-type ftp service-type ssh telnet terminal http https authorization-attribute user-role network-admin authorization-attribute user-role network-operator # security-enhanced level 1 # ssl version gm-tls1.1 disable undo ssl renegotiation disable undo ssl version ssl3.0 disable undo ssl version tls1.0 disable undo ssl version tls1.1 disable undo ssl version tls1.2 disable undo ssl version tls1.3 disable # ftp server enable ftp server acl 2422 ftp server acl ipv6 2622 # ip http enable web idle-timeout 999 # wlan ap-group default-group vlan 1 radio 2.4g radio 5g # return 一直都是用命令行配置的,都没有用web配置过,这就很奇怪。有什么地方可以参考吗?
interface GigabitEthernet0/2 port link-mode route description Multiple_Line pppoe-client dial-bundle-number 15 通过web UI测试了下,description字段改成上面一样就可以了,神奇


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明


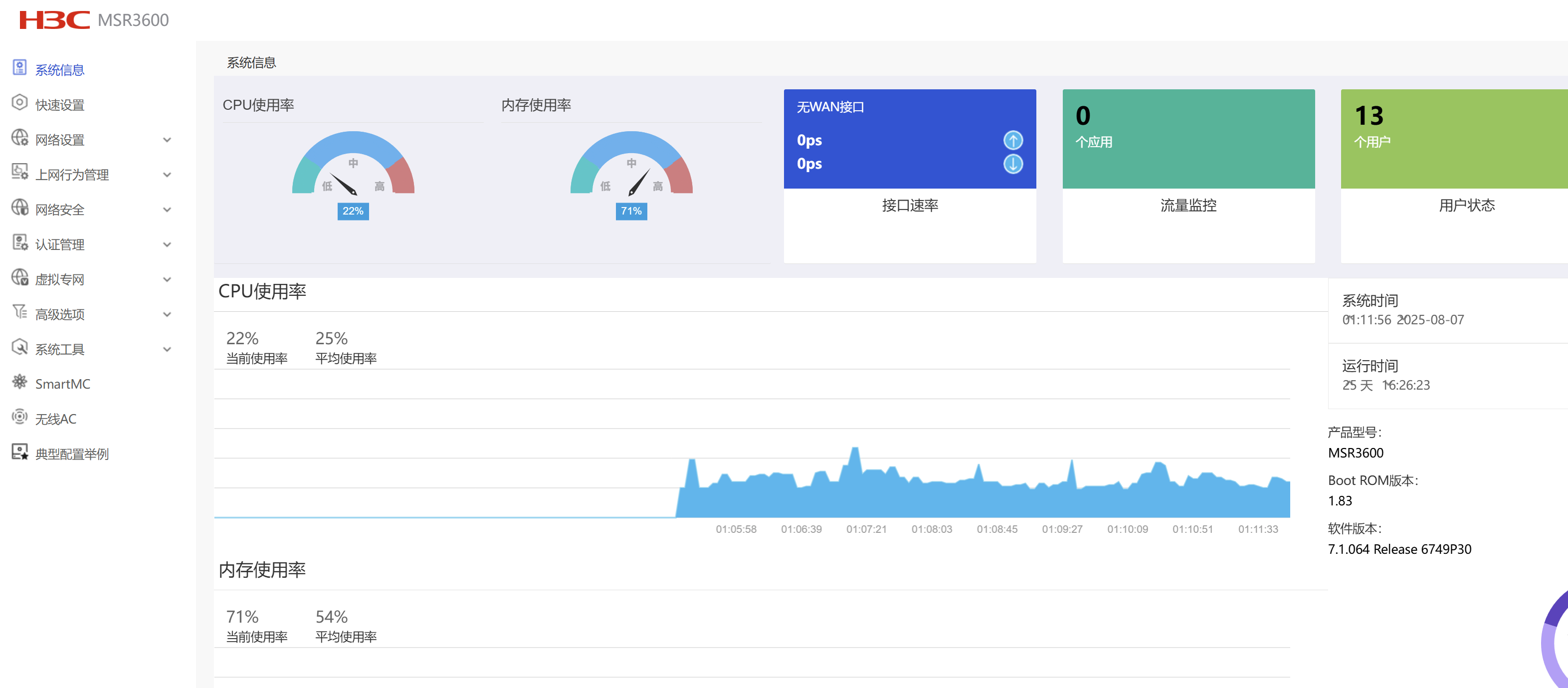
interface GigabitEthernet0/2 port link-mode route description Multiple_Line pppoe-client dial-bundle-number 15 通过web UI测试了下,description字段改成上面一样就可以了,神奇