IPSECnat穿越 总部和分支都指向对方的ip地址但建立不起来,关键报错信息含义是什么意思
- 0关注
- 0收藏,706浏览
问题描述:
从分支向总部发起,建立不起来,在R1总部端查看debugging ike all关键报错信息含义是什么
*Aug 9 11:23:44:715 2025 H3C IKE/7/EVENT: No pre-shared key found based on address 20.1.1.2.
*Aug 9 11:23:44:715 2025 H3C IKE/7/EVENT: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Pre-shared key matching address 221.201.3.1 not found.
*Aug 9 11:23:44:715 2025 H3C IKE/7/ERROR: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
No acceptable transform.
*Aug 9 11:23:44:715 2025 H3C IKE/7/ERROR: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Failed to parse the IKE SA payload.
*Aug 9 11:23:44:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Construct notification packet: NO_PROPOSAL_CHOSEN.
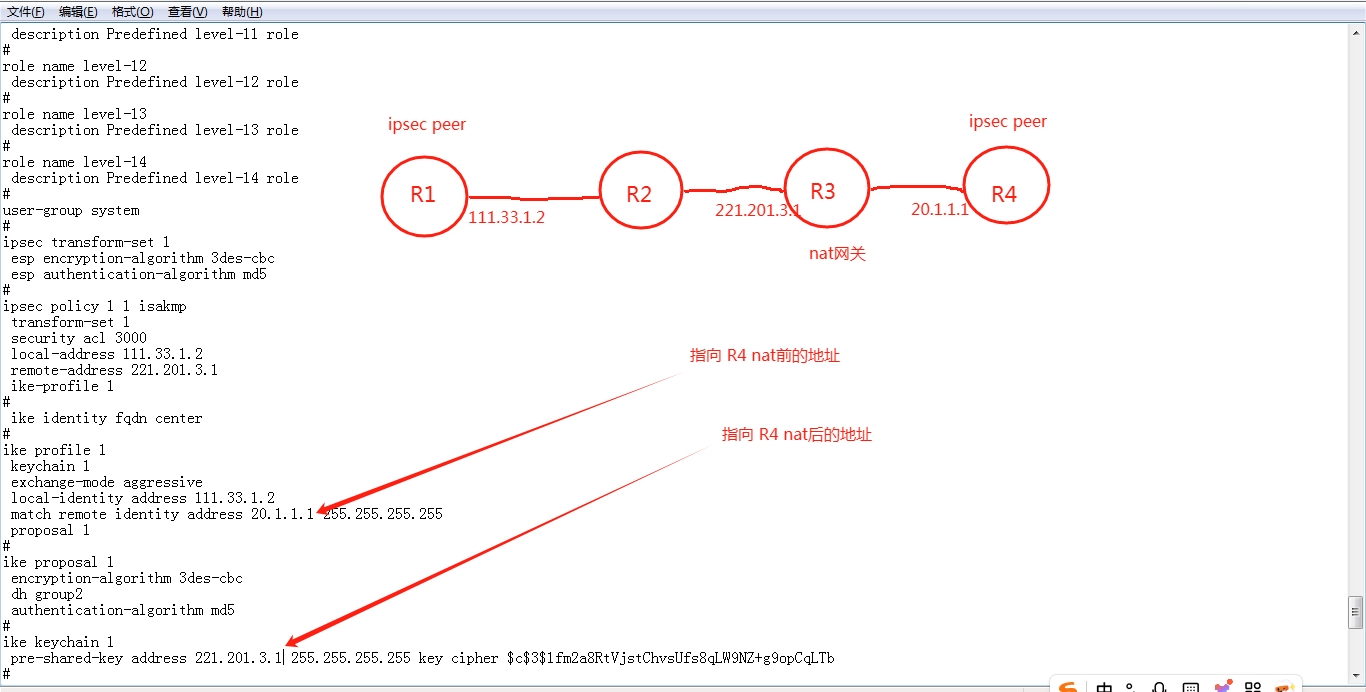
组网及组网描述:
分部访问总部时在总部debugging ike all 的信息
完整的debugging信息
<H3C>terminal monitor
The current terminal is enabled to display logs.
<H3C>*Aug 9 11:22:53:528 2025 H3C IKE/7/EVENT: Received packet successfully.
*Aug 9 11:22:53:528 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received packet from 221.201.3.1 source port 2 destination port 500.
*Aug 9 11:22:53:528 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
I-COOKIE: 17cb312c607bac1b
R-COOKIE: 0000000000000000
next payload: SA
version: ISAKMP Version 1.0
exchange mode: Aggressive
flags:
message ID: 0
length: 412
*Aug 9 11:22:53:528 2025 H3C IKE/7/EVENT: IKE thread 3062963152 processes a job.
*Aug 9 11:22:53:528 2025 H3C IKE/7/EVENT: Phase1 process started.
*Aug 9 11:22:53:528 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Begin a new phase 1 negotiation as responder.
*Aug 9 11:22:53:528 2025 H3C IKE/7/EVENT: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Responder created an SA for peer 221.201.3.1, local port 500, remote port 2.
*Aug 9 11:22:53:528 2025 H3C IKE/7/EVENT: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Set IKE SA state to IKE_P1_STATE_INIT.
*Aug 9 11:22:53:528 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Security Association Payload.
*Aug 9 11:22:53:528 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Key Exchange Payload.
*Aug 9 11:22:53:528 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Nonce Payload.
*Aug 9 11:22:53:528 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Identification Payload.
*Aug 9 11:22:53:528 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Vendor ID Payload.
*Aug 9 11:22:53:528 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Vendor ID Payload.
*Aug 9 11:22:53:528 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Vendor ID Payload.
*Aug 9 11:22:53:528 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Vendor ID Payload.
*Aug 9 11:22:53:528 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Vendor ID Payload.
*Aug 9 11:22:53:528 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Process ID payload.
*Aug 9 11:22:53:528 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Peer ID type: IPV4_ADDR (1).
*Aug 9 11:22:53:528 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Peer ID value: address 20.1.1.2.
*Aug 9 11:22:53:528 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
The profile 1 is matched.
*Aug 9 11:22:53:528 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Process SA payload.
*Aug 9 11:22:53:528 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Check ISAKMP transform 1.
*Aug 9 11:22:53:528 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Encryption algorithm is 3DES-CBC.
*Aug 9 11:22:53:528 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
HASH algorithm is HMAC-MD5.
*Aug 9 11:22:53:528 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
DH group is 5.
*Aug 9 11:22:53:528 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Authentication method is Pre-shared key.
*Aug 9 11:22:53:528 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Lifetime type is 1.
*Aug 9 11:22:53:528 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Life duration is 86400.
*Aug 9 11:22:53:528 2025 H3C IKE/7/EVENT: No pre-shared key found based on address 20.1.1.2.
*Aug 9 11:22:53:528 2025 H3C IKE/7/EVENT: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Pre-shared key matching address 221.201.3.1 not found.
*Aug 9 11:22:53:528 2025 H3C IKE/7/ERROR: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
No acceptable transform.
*Aug 9 11:22:53:528 2025 H3C IKE/7/ERROR: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Failed to parse the IKE SA payload.
*Aug 9 11:22:53:528 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Construct notification packet: NO_PROPOSAL_CHOSEN.
*Aug 9 11:22:53:528 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Sending packet to 221.201.3.1 remote port 2, local port 500.
*Aug 9 11:22:53:528 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
I-COOKIE: 17cb312c607bac1b
R-COOKIE: 0000000000000000
next payload: NOTIFY
version: ISAKMP Version 1.0
exchange mode: Info
flags:
message ID: 0
length: 56
*Aug 9 11:22:53:528 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Sending an IPv4 packet.
*Aug 9 11:22:53:529 2025 H3C IKE/7/EVENT: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Sent data to socket successfully.
*Aug 9 11:22:53:529 2025 H3C IKE/7/ERROR: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Failed to negotiate IKE SA.
*Aug 9 11:22:58:714 2025 H3C IKE/7/EVENT: Received packet successfully.
*Aug 9 11:22:58:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received packet from 221.201.3.1 source port 2 destination port 500.
*Aug 9 11:22:58:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
I-COOKIE: 17cb312c607bac1b
R-COOKIE: 0000000000000000
next payload: SA
version: ISAKMP Version 1.0
exchange mode: Aggressive
flags:
message ID: 0
length: 412
*Aug 9 11:22:58:715 2025 H3C IKE/7/EVENT: IKE thread 3062963152 processes a job.
*Aug 9 11:22:58:715 2025 H3C IKE/7/EVENT: Phase1 process started.
*Aug 9 11:22:58:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Begin a new phase 1 negotiation as responder.
*Aug 9 11:22:58:715 2025 H3C IKE/7/EVENT: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Responder created an SA for peer 221.201.3.1, local port 500, remote port 2.
*Aug 9 11:22:58:715 2025 H3C IKE/7/EVENT: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Set IKE SA state to IKE_P1_STATE_INIT.
*Aug 9 11:22:58:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Security Association Payload.
*Aug 9 11:22:58:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Key Exchange Payload.
*Aug 9 11:22:58:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Nonce Payload.
*Aug 9 11:22:58:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Identification Payload.
*Aug 9 11:22:58:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Vendor ID Payload.
*Aug 9 11:22:58:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Vendor ID Payload.
*Aug 9 11:22:58:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Vendor ID Payload.
*Aug 9 11:22:58:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Vendor ID Payload.
*Aug 9 11:22:58:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Vendor ID Payload.
*Aug 9 11:22:58:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Process ID payload.
*Aug 9 11:22:58:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Peer ID type: IPV4_ADDR (1).
*Aug 9 11:22:58:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Peer ID value: address 20.1.1.2.
*Aug 9 11:22:58:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
The profile 1 is matched.
*Aug 9 11:22:58:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Process SA payload.
*Aug 9 11:22:58:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Check ISAKMP transform 1.
*Aug 9 11:22:58:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Encryption algorithm is 3DES-CBC.
*Aug 9 11:22:58:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
HASH algorithm is HMAC-MD5.
*Aug 9 11:22:58:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
DH group is 5.
*Aug 9 11:22:58:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Authentication method is Pre-shared key.
*Aug 9 11:22:58:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Lifetime type is 1.
*Aug 9 11:22:58:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Life duration is 86400.
*Aug 9 11:22:58:715 2025 H3C IKE/7/EVENT: No pre-shared key found based on address 20.1.1.2.
*Aug 9 11:22:58:715 2025 H3C IKE/7/EVENT: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Pre-shared key matching address 221.201.3.1 not found.
*Aug 9 11:22:58:715 2025 H3C IKE/7/ERROR: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
No acceptable transform.
*Aug 9 11:22:58:715 2025 H3C IKE/7/ERROR: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Failed to parse the IKE SA payload.
*Aug 9 11:22:58:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Construct notification packet: NO_PROPOSAL_CHOSEN.
*Aug 9 11:22:58:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Sending packet to 221.201.3.1 remote port 2, local port 500.
*Aug 9 11:22:58:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
I-COOKIE: 17cb312c607bac1b
R-COOKIE: 0000000000000000
next payload: NOTIFY
version: ISAKMP Version 1.0
exchange mode: Info
flags:
message ID: 0
length: 56
*Aug 9 11:22:58:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Sending an IPv4 packet.
*Aug 9 11:22:58:715 2025 H3C IKE/7/EVENT: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Sent data to socket successfully.
*Aug 9 11:22:58:715 2025 H3C IKE/7/ERROR: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Failed to negotiate IKE SA.
<H3C>*Aug 9 11:23:14:710 2025 H3C IKE/7/EVENT: Received packet successfully.
*Aug 9 11:23:14:710 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received packet from 221.201.3.1 source port 2 destination port 500.
*Aug 9 11:23:14:710 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
I-COOKIE: 17cb312c607bac1b
R-COOKIE: 0000000000000000
next payload: SA
version: ISAKMP Version 1.0
exchange mode: Aggressive
flags:
message ID: 0
length: 412
*Aug 9 11:23:14:710 2025 H3C IKE/7/EVENT: IKE thread 3062963152 processes a job.
*Aug 9 11:23:14:710 2025 H3C IKE/7/EVENT: Phase1 process started.
*Aug 9 11:23:14:710 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Begin a new phase 1 negotiation as responder.
*Aug 9 11:23:14:710 2025 H3C IKE/7/EVENT: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Responder created an SA for peer 221.201.3.1, local port 500, remote port 2.
*Aug 9 11:23:14:710 2025 H3C IKE/7/EVENT: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Set IKE SA state to IKE_P1_STATE_INIT.
*Aug 9 11:23:14:710 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Security Association Payload.
*Aug 9 11:23:14:710 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Key Exchange Payload.
*Aug 9 11:23:14:710 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Nonce Payload.
*Aug 9 11:23:14:710 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Identification Payload.
*Aug 9 11:23:14:710 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Vendor ID Payload.
*Aug 9 11:23:14:710 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Vendor ID Payload.
*Aug 9 11:23:14:710 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Vendor ID Payload.
*Aug 9 11:23:14:710 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Vendor ID Payload.
*Aug 9 11:23:14:710 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Vendor ID Payload.
*Aug 9 11:23:14:710 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Process ID payload.
*Aug 9 11:23:14:710 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Peer ID type: IPV4_ADDR (1).
*Aug 9 11:23:14:710 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Peer ID value: address 20.1.1.2.
*Aug 9 11:23:14:710 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
The profile 1 is matched.
*Aug 9 11:23:14:710 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Process SA payload.
*Aug 9 11:23:14:710 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Check ISAKMP transform 1.
*Aug 9 11:23:14:710 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Encryption algorithm is 3DES-CBC.
*Aug 9 11:23:14:711 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
HASH algorithm is HMAC-MD5.
*Aug 9 11:23:14:711 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
DH group is 5.
*Aug 9 11:23:14:711 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Authentication method is Pre-shared key.
*Aug 9 11:23:14:711 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Lifetime type is 1.
*Aug 9 11:23:14:711 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Life duration is 86400.
*Aug 9 11:23:14:711 2025 H3C IKE/7/EVENT: No pre-shared key found based on address 20.1.1.2.
*Aug 9 11:23:14:711 2025 H3C IKE/7/EVENT: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Pre-shared key matching address 221.201.3.1 not found.
*Aug 9 11:23:14:711 2025 H3C IKE/7/ERROR: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
No acceptable transform.
*Aug 9 11:23:14:711 2025 H3C IKE/7/ERROR: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Failed to parse the IKE SA payload.
*Aug 9 11:23:14:711 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Construct notification packet: NO_PROPOSAL_CHOSEN.
*Aug 9 11:23:14:711 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Sending packet to 221.201.3.1 remote port 2, local port 500.
*Aug 9 11:23:14:711 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
I-COOKIE: 17cb312c607bac1b
R-COOKIE: 0000000000000000
next payload: NOTIFY
version: ISAKMP Version 1.0
exchange mode: Info
flags:
message ID: 0
length: 56
*Aug 9 11:23:14:711 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Sending an IPv4 packet.
*Aug 9 11:23:14:711 2025 H3C IKE/7/EVENT: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Sent data to socket successfully.
*Aug 9 11:23:14:711 2025 H3C IKE/7/ERROR: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Failed to negotiate IKE SA.
<H3C>
<H3C>
<H3C>
<H3C>*Aug 9 11:23:26:709 2025 H3C IKE/7/EVENT: Received packet successfully.
*Aug 9 11:23:26:709 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received packet from 221.201.3.1 source port 2 destination port 500.
*Aug 9 11:23:26:709 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
I-COOKIE: 17cb312c607bac1b
R-COOKIE: 0000000000000000
next payload: SA
version: ISAKMP Version 1.0
exchange mode: Aggressive
flags:
message ID: 0
length: 412
*Aug 9 11:23:26:709 2025 H3C IKE/7/EVENT: IKE thread 3062963152 processes a job.
*Aug 9 11:23:26:709 2025 H3C IKE/7/EVENT: Phase1 process started.
*Aug 9 11:23:26:709 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Begin a new phase 1 negotiation as responder.
*Aug 9 11:23:26:709 2025 H3C IKE/7/EVENT: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Responder created an SA for peer 221.201.3.1, local port 500, remote port 2.
*Aug 9 11:23:26:709 2025 H3C IKE/7/EVENT: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Set IKE SA state to IKE_P1_STATE_INIT.
*Aug 9 11:23:26:709 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Security Association Payload.
*Aug 9 11:23:26:709 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Key Exchange Payload.
*Aug 9 11:23:26:709 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Nonce Payload.
*Aug 9 11:23:26:709 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Identification Payload.
*Aug 9 11:23:26:709 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Vendor ID Payload.
*Aug 9 11:23:26:709 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Vendor ID Payload.
*Aug 9 11:23:26:709 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Vendor ID Payload.
*Aug 9 11:23:26:709 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Vendor ID Payload.
*Aug 9 11:23:26:709 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Vendor ID Payload.
*Aug 9 11:23:26:709 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Process ID payload.
*Aug 9 11:23:26:709 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Peer ID type: IPV4_ADDR (1).
*Aug 9 11:23:26:709 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Peer ID value: address 20.1.1.2.
*Aug 9 11:23:26:709 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
The profile 1 is matched.
*Aug 9 11:23:26:709 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Process SA payload.
*Aug 9 11:23:26:709 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Check ISAKMP transform 1.
*Aug 9 11:23:26:709 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Encryption algorithm is 3DES-CBC.
*Aug 9 11:23:26:709 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
HASH algorithm is HMAC-MD5.
*Aug 9 11:23:26:709 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
DH group is 5.
*Aug 9 11:23:26:709 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Authentication method is Pre-shared key.
*Aug 9 11:23:26:709 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Lifetime type is 1.
*Aug 9 11:23:26:710 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Life duration is 86400.
*Aug 9 11:23:26:710 2025 H3C IKE/7/EVENT: No pre-shared key found based on address 20.1.1.2.
*Aug 9 11:23:26:710 2025 H3C IKE/7/EVENT: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Pre-shared key matching address 221.201.3.1 not found.
*Aug 9 11:23:26:710 2025 H3C IKE/7/ERROR: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
No acceptable transform.
*Aug 9 11:23:26:710 2025 H3C IKE/7/ERROR: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Failed to parse the IKE SA payload.
*Aug 9 11:23:26:710 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Construct notification packet: NO_PROPOSAL_CHOSEN.
*Aug 9 11:23:26:710 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Sending packet to 221.201.3.1 remote port 2, local port 500.
*Aug 9 11:23:26:710 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
I-COOKIE: 17cb312c607bac1b
R-COOKIE: 0000000000000000
next payload: NOTIFY
version: ISAKMP Version 1.0
exchange mode: Info
flags:
message ID: 0
length: 56
*Aug 9 11:23:26:710 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Sending an IPv4 packet.
*Aug 9 11:23:26:710 2025 H3C IKE/7/EVENT: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Sent data to socket successfully.
*Aug 9 11:23:26:710 2025 H3C IKE/7/ERROR: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Failed to negotiate IKE SA.
<H3C>
<H3C>
<H3C>
<H3C>
<H3C>dis ike sa
Connection-ID Local Remote Flag DOI
-------------------------------------------------------------------------
<H3C>*Aug 9 11:23:44:714 2025 H3C IKE/7/EVENT: Received packet successfully.
*Aug 9 11:23:44:714 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received packet from 221.201.3.1 source port 2 destination port 500.
*Aug 9 11:23:44:714 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
I-COOKIE: 17cb312c607bac1b
R-COOKIE: 0000000000000000
next payload: SA
version: ISAKMP Version 1.0
exchange mode: Aggressive
flags:
message ID: 0
length: 412
*Aug 9 11:23:44:714 2025 H3C IKE/7/EVENT: IKE thread 3062963152 processes a job.
*Aug 9 11:23:44:714 2025 H3C IKE/7/EVENT: Phase1 process started.
*Aug 9 11:23:44:714 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Begin a new phase 1 negotiation as responder.
*Aug 9 11:23:44:714 2025 H3C IKE/7/EVENT: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Responder created an SA for peer 221.201.3.1, local port 500, remote port 2.
*Aug 9 11:23:44:714 2025 H3C IKE/7/EVENT: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Set IKE SA state to IKE_P1_STATE_INIT.
*Aug 9 11:23:44:714 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Security Association Payload.
*Aug 9 11:23:44:714 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Key Exchange Payload.
*Aug 9 11:23:44:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Nonce Payload.
*Aug 9 11:23:44:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Identification Payload.
*Aug 9 11:23:44:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Vendor ID Payload.
*Aug 9 11:23:44:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Vendor ID Payload.
*Aug 9 11:23:44:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Vendor ID Payload.
*Aug 9 11:23:44:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Vendor ID Payload.
*Aug 9 11:23:44:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Received ISAKMP Vendor ID Payload.
*Aug 9 11:23:44:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Process ID payload.
*Aug 9 11:23:44:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Peer ID type: IPV4_ADDR (1).
*Aug 9 11:23:44:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Peer ID value: address 20.1.1.2.
*Aug 9 11:23:44:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
The profile 1 is matched.
*Aug 9 11:23:44:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Process SA payload.
*Aug 9 11:23:44:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Check ISAKMP transform 1.
*Aug 9 11:23:44:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Encryption algorithm is 3DES-CBC.
*Aug 9 11:23:44:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
HASH algorithm is HMAC-MD5.
*Aug 9 11:23:44:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
DH group is 5.
*Aug 9 11:23:44:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Authentication method is Pre-shared key.
*Aug 9 11:23:44:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Lifetime type is 1.
*Aug 9 11:23:44:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Life duration is 86400.
*Aug 9 11:23:44:715 2025 H3C IKE/7/EVENT: No pre-shared key found based on address 20.1.1.2.
*Aug 9 11:23:44:715 2025 H3C IKE/7/EVENT: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Pre-shared key matching address 221.201.3.1 not found.
*Aug 9 11:23:44:715 2025 H3C IKE/7/ERROR: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
No acceptable transform.
*Aug 9 11:23:44:715 2025 H3C IKE/7/ERROR: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Failed to parse the IKE SA payload.
*Aug 9 11:23:44:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Construct notification packet: NO_PROPOSAL_CHOSEN.
*Aug 9 11:23:44:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Sending packet to 221.201.3.1 remote port 2, local port 500.
*Aug 9 11:23:44:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
I-COOKIE: 17cb312c607bac1b
R-COOKIE: 0000000000000000
next payload: NOTIFY
version: ISAKMP Version 1.0
exchange mode: Info
flags:
message ID: 0
length: 56
*Aug 9 11:23:44:715 2025 H3C IKE/7/PACKET: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Sending an IPv4 packet.
*Aug 9 11:23:44:715 2025 H3C IKE/7/EVENT: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Sent data to socket successfully.
*Aug 9 11:23:44:715 2025 H3C IKE/7/ERROR: vrf = 0, local = 111.33.1.2, remote = 221.201.3.1/2
Failed to negotiate IKE SA.
<H3C>
<H3C>u tm
The recycle-bin is empty.
<H3C>u t m
The current terminal is disabled to display logs.
<H3C>
- 2025-08-09提问
- 举报
-
(0)
最佳答案
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明




暂无评论