防火墙上配置好接口ip 静态路由 内网nat服务器转发等,阿里云dns解析同步添加一条移动ip的域名解析之后,
移动的用户无法正常打开业务地址,请教下大家是哪里的配置问题?
配置已贴下发,感谢
以下是防火墙配置:
#
version 7.1.064, Release 9560P48
#
memory-threshold slot 1 minor 102 severe 96 critical 88 normal 128
memory-threshold slot 2 minor 102 severe 96 critical 88 normal 128
#
sysname NCYT-DC-FW-1
#
clock timezone Beijing add 08:00:00
clock protocol none
#
irf mac-address persistent timer
irf auto-update enable
undo irf link-delay
irf member 1 priority 2
irf member 2 priority 1
#
track 1 interface GigabitEthernet1/0/6
#
track 2 interface GigabitEthernet1/0/7
#
track 3 interface GigabitEthernet2/0/6
#
track 4 interface GigabitEthernet2/0/7
#
nat address-group 1 name snat-pool
address 180.97.15.185 180.97.15.185
#
nat log enable
#
dns proxy enable
dns server 218.2.2.2
#
password-recovery enable
#
vlan 1
#
irf-port 1/2
port group interface GigabitEthernet1/0/8
port group interface GigabitEthernet1/0/9
#
irf-port 2/1
port group interface GigabitEthernet2/0/8
port group interface GigabitEthernet2/0/9
#
object-group ip address 2网段
security-zone Trust
0 network subnet 10.2.1.0 255.255.255.0
#
object-group ip address 3网段
security-zone Trust
0 network subnet 10.3.1.0 255.255.255.0
10 network subnet 10.30.105.0 255.255.255.0
#
object-group ip address 5和6网段
security-zone Trust
0 network subnet 10.5.1.0 255.255.255.0
10 network subnet 10.6.1.0 255.255.255.0
#
object-group ip address web-server
security-zone DMZ
0 network host address 180.97.15.184
10 network host address 180.97.15.186
20 network host address 180.97.15.185
#
object-group ip address 防火墙地址
0 network host address 10.20.201.1
10 network host address 180.97.15.184
#
controller Cellular1/0/0
#
controller Cellular1/0/1
#
controller Cellular2/0/0
#
controller Cellular2/0/1
#
interface Reth10
ip address 112.21.33.2 255.255.255.248
ip address 112.21.33.3 255.255.255.248 sub
member interface GigabitEthernet1/0/5 priority 100
member interface GigabitEthernet2/0/5 priority 80
ip last-hop hold
nat server protocol tcp global 112.21.33.2 80 inside 10.2.1.199 80 rule 移动_nginx_http counting description 移动智慧能源网https登录B端口
nat server protocol tcp global 112.21.33.2 443 inside 10.2.1.199 443 rule 移动_nginx_https counting description 移动智慧能源网https登录B端口
nat server protocol tcp global 112.21.33.3 80 inside 10.2.1.199 7080 rule 移动_nginx_api counting description 外部http服务api接口
nat server protocol tcp global 112.21.33.3 443 inside 10.2.1.199 8043 rule 移动_nginx_api_https counting description 外部https服务api接口
gateway 112.21.33.1
#
interface Reth11
ip address 180.97.15.184 255.255.255.192
ip address 180.97.15.185 255.255.255.192 sub
ip address 180.97.15.186 255.255.255.192 sub
ip address 180.97.15.187 255.255.255.192 sub
member interface GigabitEthernet1/0/6 priority 100
member interface GigabitEthernet2/0/6 priority 80
ip last-hop hold
nat server protocol tcp global 180.97.15.184 21 inside 10.3.1.50 21 rule ftp_meter_upgrade counting description E版本电表FTP升级端口***.***
nat server protocol tcp global 180.97.15.184 80 inside 10.2.1.199 80 rule nginx_http_b counting description 智慧能源网https登录B端口
nat server protocol tcp global 180.97.15.184 443 inside 10.2.1.199 443 rule nginx_https_B counting description 智慧能源网https登录B端口
nat server protocol tcp global 180.97.15.185 80 inside 10.2.1.199 7080 rule nginx_api_a counting description 外部http服务api接口
nat server protocol tcp global 180.97.15.185 443 inside 10.2.1.199 8043 rule nginx_api_https counting description 外部https服务api接口
#
interface Reth12
ip address 10.20.201.1 255.255.255.0
member interface GigabitEthernet1/0/7 priority 100
member interface GigabitEthernet2/0/7 priority 80
#
interface NULL0
#
interface GigabitEthernet1/0/0
port link-mode route
combo enable copper
#
interface GigabitEthernet1/0/1
port link-mode route
combo enable fiber
#
interface GigabitEthernet1/0/2
port link-mode route
ip address 192.168.1.1 255.255.255.0
#
interface GigabitEthernet1/0/3
port link-mode route
#
interface GigabitEthernet1/0/4
port link-mode route
#
interface GigabitEthernet1/0/5
port link-mode route
#
interface GigabitEthernet1/0/6
port link-mode route
#
interface GigabitEthernet1/0/7
port link-mode route
#
interface GigabitEthernet2/0/0
port link-mode route
combo enable fiber
#
interface GigabitEthernet2/0/1
port link-mode route
combo enable fiber
#
interface GigabitEthernet2/0/2
port link-mode route
ip address 192.168.3.3 255.255.255.0
#
interface GigabitEthernet2/0/3
port link-mode route
#
interface GigabitEthernet2/0/4
port link-mode route
#
interface GigabitEthernet2/0/5
port link-mode route
#
interface GigabitEthernet2/0/6
port link-mode route
#
interface GigabitEthernet2/0/7
port link-mode route
#
interface GigabitEthernet1/0/8
#
interface GigabitEthernet1/0/9
#
interface GigabitEthernet2/0/8
#
interface GigabitEthernet2/0/9
#
interface SSLVPN-AC1
ip address 10.10.1.240 255.255.255.0
#
security-zone name Local
#
security-zone name Trust
import interface Reth12
#
security-zone name DMZ
import interface Reth10
import interface Reth11
import interface SSLVPN-AC1
attack-defense apply policy policy-protect-1
#
security-zone name Untrust
#
security-zone name Management
import interface GigabitEthernet1/0/0
import interface GigabitEthernet1/0/2
import interface GigabitEthernet2/0/2
#
scheduler logfile size 16
#
line class aux
user-role network-operator
#
line class console
authentication-mode scheme
user-role network-admin
#
line class vty
user-role network-operator
#
line aux 0
user-role network-admin
#
line aux 1
user-role network-operator
#
line con 0 1
user-role network-admin
#
line vty 0 63
authentication-mode scheme
user-role network-admin
#
ip route-static 0.0.0.0 0 Reth11 180.97.15.129
ip route-static 0.0.0.0 0 Reth10 112.21.33.1
ip route-static 10.2.1.0 24 Reth12 10.20.201.2
ip route-static 10.3.1.0 24 Reth12 10.20.201.2
ip route-static 10.30.105.0 24 Reth12 10.20.201.2
ip route-static 10.60.1.0 24 Reth12 10.20.201.2
#
customlog format attack-defense
customlog format dpi ips
customlog format dpi anti-virus
customlog format dpi traffic-policy
#
performance-management
#
ssh server port 2020
#
redundancy group a
member interface Reth10
member interface Reth11
member interface Reth12
node 1
bind slot 1
priority 20
track 1 interface GigabitEthernet1/0/6
track 2 interface GigabitEthernet1/0/7
track 5 interface GigabitEthernet1/0/5
node 2
bind slot 2
priority 10
track 3 interface GigabitEthernet2/0/6
track 4 interface GigabitEthernet2/0/7
track 6 interface GigabitEthernet2/0/5
#
ntp-service enable
ntp-service authentication enable
ntp-service refclock-master
#
acl advanced 3000
rule 0 permit ip source 10.10.1.0 0.0.0.255 destination 10.3.1.0 0.0.0.255 counting
rule 5 permit ip source 10.10.1.0 0.0.0.255 destination 10.30.105.0 0.0.0.255 counting
#
#
password-control enable
undo password-control aging enable
undo password-control history enable
password-control length 8
password-control complexity same-character check
#
domain system
authentication ppp local
#
domain default enable system
#
role name level-0
description Predefined level-0 role
#
role name level-1
description Predefined level-1 role
#
role name level-2
description Predefined level-2 role
#
role name level-3
description Predefined level-3 role
#
role name level-4
description Predefined level-4 role
#
role name level-5
description Predefined level-5 role
#
role name level-6
description Predefined level-6 role
#
role name level-7
description Predefined level-7 role
#
role name level-8
description Predefined level-8 role
#
role name level-9
description Predefined level-9 role
#
role name level-10
description Predefined level-10 role
#
role name level-11
description Predefined level-11 role
#
role name level-12
description Predefined level-12 role
#
role name level-13
description Predefined level-13 role
#
role name level-14
description Predefined level-14 role
#
user-group system
authorization-attribute idle-cut 60
#
#
local-user admin class manage
service-type ftp
service-type ssh telnet terminal http https
authorization-attribute user-role level-3
authorization-attribute user-role network-admin
authorization-attribute user-role network-operator
#
local-user administrator class manage
service-type ftp
service-type ssh telnet terminal
authorization-attribute user-role network-operator
#
#
pki domain default
certificate request entity vpn
usage ike
usage ssl-client
usage ssl-server
#
#
session statistics enable
session top-statistics enable
session synchronization enable
#
ipsec logging negotiation enable
#
nat policy
rule name toInter
source-ip 2网段
source-ip 3网段
source-ip 防火墙地址
outbound-interface Reth11
action address-group 1
rule name toInter2
description 移动接口
source-ip 2网段
source-ip 3网段
source-ip 防火墙地址
outbound-interface Reth10
action address-group 1
#
ike logging negotiation enable
#
ip http port 8282
ip https port 1443
ip https enable
web idle-timeout 900
#
user-identity enable
user-identity online-user-name-match without-domain
#
packet-capture max-file-packets 1000
#
security-policy ip
rule 8 name 禁止外部UDP53端口
counting enable
source-zone DMZ
destination-zone Trust
destination-zone Local
service dns-udp
service ike
rule 7 name 拦截异常域名
logging enable
counting enable
source-zone Trust
source-zone Local
destination-zone DMZ
destination-ip 异常域名
rule 1 name untrust2trust
action pass
counting enable
profile 1_IPv4
source-zone Trust
destination-zone Local
destination-zone DMZ
rule 2 name trust2untrust
action pass
disable
rule 3 name DMZ2Trust
action pass
counting enable
profile 3_IPv4
source-zone DMZ
destination-zone Trust
destination-zone Local
destination-zone Management
rule 4 name MNG2Trust
action pass
disable
source-zone Management
destination-zone Trust
destination-zone DMZ
destination-zone Local
rule 5 name local2Trust
action pass
counting enable
profile 5_IPv4
source-zone Local
destination-zone Trust
destination-zone Management
rule 6 name Local2DMZ
action pass
counting enable
profile 6_IPv4
source-zone Local
destination-zone DMZ
#
return
(0)
最佳答案

您好,增加保持上一跳,参考
开启保持上一跳功能后,当该接口接收到正向流量的第一个IP报文,在高速缓存中会记录相应的流量特征以及上一跳信息,反向流量报文到达设备上进行转发时可以直接通过该上一跳信息指导报文进行转发。保证了从对端到本端的正向流量和本端到对端的反向流量走的是相同的路径,从而保证同一会话的流量能够进行相同的业务处理。
如图1-1所示,外网服务器向内网服务器发起业务请求,请求报文通过ISP1到达Device设备,访问内网服务器。用户希望相同会话或连接的正向流量与反向流量保持相同的转发路径,即回应报文到达Device设备后,通过接收请求报文的Interface A接口转发出去,经过ISP1到达外网服务器。未开启保持上一跳功能时,Device设备会选择最佳链路进行报文的转发,这样就无法保证正反向流量路径一致。这种情况下,用户可以在接收正向流量的Interface A接口上开启保持上一跳功能。
保持上一跳功能依赖于快速转发表项的建立,如果上一跳的MAC地址发生变化,对应的快速转发表项需要重建才能使保持上一跳功能正常工作。
(1) 进入系统视图。
system-view
(2) 进入接口视图
¡ 进入三层以太网接口视图。
interface interface-type interface-number
¡ 进入三层以太网子接口视图。
interface interface-type interface-number.subnumber
(3) 开启保持上一跳功能。
ip last-hop hold
缺省情况下,转发保持上一跳功能处于关闭状态。
(0)
你好,两个外网接口下都是有配置 ip last-hop hold 保持上一跳的

映射有问题是吧
配置下保持上一跳功能
(0)
两个外网接口下都是有配置 ip last-hop hold 保持上一跳的
两个外网接口下都是有配置 ip last-hop hold 保持上一跳的

你看你的nat 地址组 和全局的nat 策略 你都转换成了nat 地址组1 了,但是你nat 地址组了只是
180.97.15.185
检查一下这两个地方
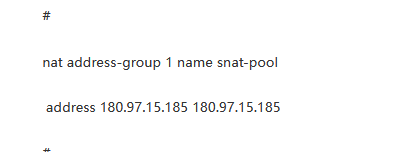
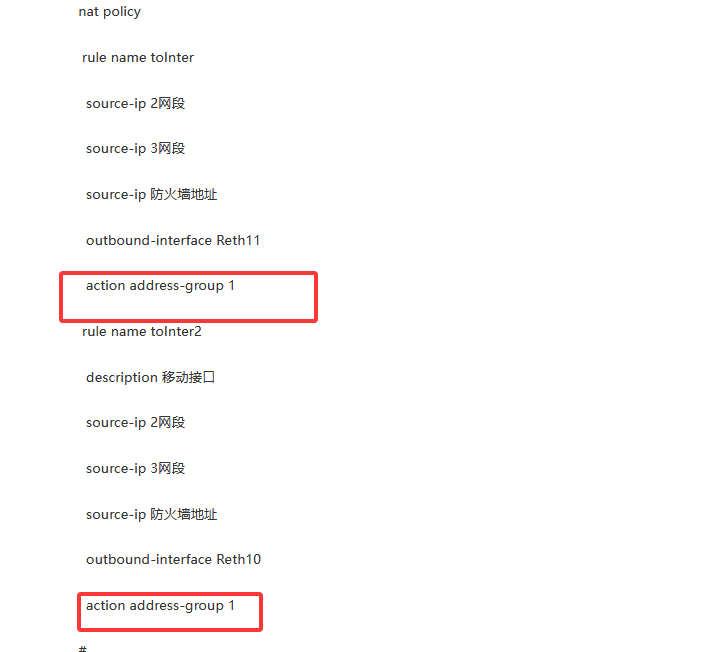
(0)
nat address-group 2 name snat-pool2 address 112.21.33.2 112.21.33.2 rule name toInter2 description 移动接口 source-ip 2网段 source-ip 3网段 source-ip 防火墙地址 outbound-interface Reth10 action address-group 2 大佬这样是否就对了吗?


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
抄袭了我的内容
×
原文链接或出处
诽谤我
×
对根叔社区有害的内容
×
不规范转载
×
举报说明
你好,两个外网接口下都是有配置 ip last-hop hold 保持上一跳的