F100-C如何配置ipv6全球聚合地址上网?
- 1关注
- 0收藏,479浏览
问题描述:
我有一台H3C F100-C安全网关,在WAN接口Gigabitethernet0/0下配置:ipv6 address auto>ipv6 address auto link-local>ipv6 dhcp client pd 1 rapid-commit option-group 1//ipv6 dhcp pool v6>option-group 1//在其他上网接口Gigabitethernet0/1下配置:ipv6 dhcp select server>ipv6 dhcp server apply pool v6>ipv6 address 1::1/64>undo ipv6 nd ra halt,但是经过以上配置之后 ,上网的电脑一直获取不到全球聚合地址和前缀。
组网及组网描述:
Gigabitethernet0/0接口连接的是运营商光猫的上网口(可以插上正常上网),Gigabitethernet0/1接口接着上网的电脑。
- 2025-12-22提问
- 举报
-
(0)
最佳答案

你好,可以参考这个 nat66配置全局nat实现内网前缀转换成单个公网ipv6地址 - 知了社区
防火墙作为出口设备,配置96前缀的ipv6地址,内网的1000::1/64和1001::1/64前缀的网段转换成公网的2000::3地址访问外网,内网的1003::1/64和1004::1/64前缀的网段转换成公网的2000::4地址访问外网。
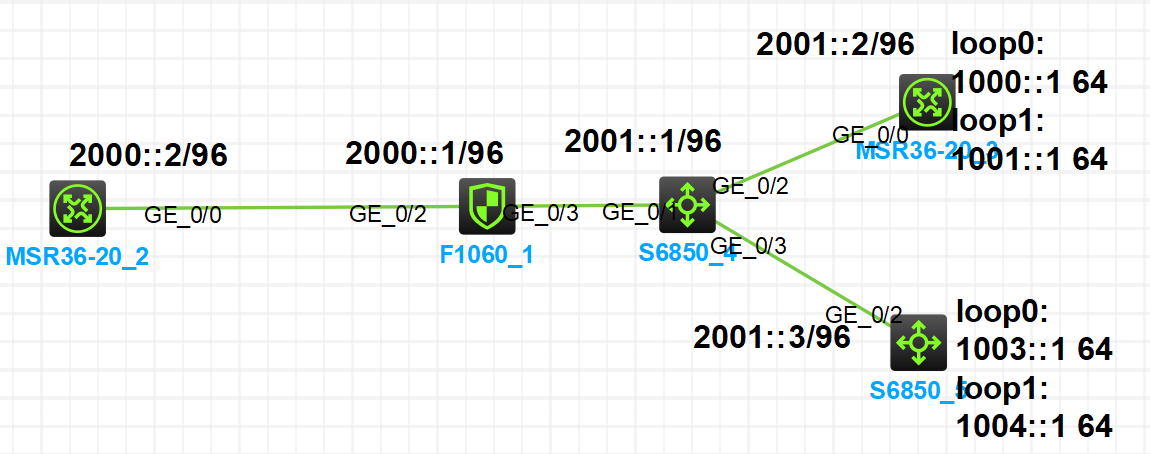
配置步骤
防火墙配置:
interface GigabitEthernet1/0/2 //外网口配置
port link-mode route
combo enable copper
ipv6 address 2000::1/96
proxy-nd enable //普通的arp代理这个是必须配置的
#
interface GigabitEthernet1/0/3 //内网口配置
port link-mode route
combo enable copper
ipv6 address 2001::1/96
安全域配置:
security-zone name Trust
import interface GigabitEthernet1/0/3
#
security-zone name Untrust
import interface GigabitEthernet1/0/2
安全策略配置:
security-policy ipv6
rule 1 name trust_untrust
action pass
source-zone trust
destination-zone untrust
指向内网网段的路由配置
ipv6 route-static 1000:: 64 2001::2
ipv6 route-static 1001:: 64 2001::2
ipv6 route-static 1003:: 64 2001::3
ipv6 route-static 1004:: 64 2001::3
创建nat地址对象组
object-group ipv6 address test
0 network host address 2000::3
#
object-group ipv6 address test1
0 network host address 2000::4
全局nat配置:
nat global-policy
rule name 1 type nat66
source-zone Trust
destination-zone Untrust
source-ip subnet 1000:: 64 //源地址是1000:: 64前缀的转换成test地址组中的地址
source-ip subnet 1001:: 64 //源地址是1001:: 64前缀的转换成test地址组中的地址
action snat object-group test
rule name 2 type nat66
source-zone Trust
destination-zone Untrust
source-ip subnet 1003:: 64 //源地址是1003:: 64前缀的转换成test1地址组中的地址
source-ip subnet 1004:: 64 //源地址是1004:: 64前缀的转换成test1地址组中的地址
action snat object-group test1
配置关键点
测试结果:
<H3C>ping ipv6 -a 1000::1 2000::2
Ping6(56 data bytes) 1000::1 --> 2000::2, press CTRL+C to break
56 bytes from 2000::2, icmp_seq=0 hlim=63 time=1.662 ms
56 bytes from 2000::2, icmp_seq=1 hlim=63 time=1.346 ms
56 bytes from 2000::2, icmp_seq=2 hlim=63 time=1.587 ms
56 bytes from 2000::2, icmp_seq=3 hlim=63 time=1.042 ms
56 bytes from 2000::2, icmp_seq=4 hlim=63 time=1.027 ms
<H3C>ping ipv6 -a 1001::1 2000::2
Ping6(56 data bytes) 1001::1 --> 2000::2, press CTRL+C to break
56 bytes from 2000::2, icmp_seq=0 hlim=63 time=4.393 ms
56 bytes from 2000::2, icmp_seq=1 hlim=63 time=1.954 ms
56 bytes from 2000::2, icmp_seq=2 hlim=63 time=1.121 ms
56 bytes from 2000::2, icmp_seq=3 hlim=63 time=1.125 ms
56 bytes from 2000::2, icmp_seq=4 hlim=63 time=1.175 ms
查看会话:
<H3C>dis nat66 session verbose
Slot 1:
Total sessions found: 0
<H3C>dis nat66 session verbose
Slot 1:
Initiator:
Source IP/port: 1001::1/11060
Destination IP/port: 2000::2/32768
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: IPV6-ICMP(58)
Inbound interface: GigabitEthernet1/0/3
Source security zone: Trust
Responder:
Source IP/port: 2000::2/6
Destination IP/port: 2000::3/33024
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: IPV6-ICMP(58)
Inbound interface: GigabitEthernet1/0/2
Source security zone: Untrust
State: ICMPV6_REPLY
Application: ICMP
Rule ID: 1
Rule name: trust_untrust
Start time: 2024-11-30 09:55:46 TTL: 25s
Initiator->Responder: 0 packets 0 bytes
Responder->Initiator: 0 packets 0 bytes
Initiator:
Source IP/port: 1000::1/11061
Destination IP/port: 2000::2/32768
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: IPV6-ICMP(58)
Inbound interface: GigabitEthernet1/0/3
Source security zone: Trust
Responder:
Source IP/port: 2000::2/7
Destination IP/port: 2000::3/33024
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: IPV6-ICMP(58)
Inbound interface: GigabitEthernet1/0/2
Source security zone: Untrust
State: ICMPV6_REPLY
Application: ICMP
Rule ID: 1
Rule name: trust_untrust
Start time: 2024-11-30 09:55:49 TTL: 27s
Initiator->Responder: 0 packets 0 bytes
Responder->Initiator: 0 packets 0 bytes
Total sessions found: 2
<H3C>ping ipv6 -a 1003::1 2000::2
Ping6(56 data bytes) 1003::1 --> 2000::2, press CTRL+C to break
56 bytes from 2000::2, icmp_seq=0 hlim=63 time=2.509 ms
56 bytes from 2000::2, icmp_seq=1 hlim=63 time=1.584 ms
56 bytes from 2000::2, icmp_seq=2 hlim=63 time=1.889 ms
56 bytes from 2000::2, icmp_seq=3 hlim=63 time=1.153 ms
56 bytes from 2000::2, icmp_seq=4 hlim=63 time=1.968 ms
<H3C>ping ipv6 -a 1004::1 2000::2
Ping6(56 data bytes) 1004::1 --> 2000::2, press CTRL+C to break
56 bytes from 2000::2, icmp_seq=0 hlim=63 time=2.129 ms
56 bytes from 2000::2, icmp_seq=1 hlim=63 time=1.758 ms
56 bytes from 2000::2, icmp_seq=2 hlim=63 time=2.058 ms
56 bytes from 2000::2, icmp_seq=3 hlim=63 time=1.387 ms
56 bytes from 2000::2, icmp_seq=4 hlim=63 time=1.041 ms
查看会话:
<H3C>dis nat66 session verbose
Slot 1:
Initiator:
Source IP/port: 1004::1/52749
Destination IP/port: 2000::2/32768
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: IPV6-ICMP(58)
Inbound interface: GigabitEthernet1/0/3
Source security zone: Trust
Responder:
Source IP/port: 2000::2/6
Destination IP/port: 2000::4/33024
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: IPV6-ICMP(58)
Inbound interface: GigabitEthernet1/0/2
Source security zone: Untrust
State: ICMPV6_REPLY
Application: ICMP
Rule ID: 1
Rule name: trust_untrust
Start time: 2024-11-30 09:56:44 TTL: 26s
Initiator->Responder: 0 packets 0 bytes
Responder->Initiator: 0 packets 0 bytes
Initiator:
Source IP/port: 1003::1/52748
Destination IP/port: 2000::2/32768
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: IPV6-ICMP(58)
Inbound interface: GigabitEthernet1/0/3
Source security zone: Trust
Responder:
Source IP/port: 2000::2/5
Destination IP/port: 2000::4/33024
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: IPV6-ICMP(58)
Inbound interface: GigabitEthernet1/0/2
Source security zone: Untrust
State: ICMPV6_REPLY
Application: ICMP
Rule ID: 1
Rule name: trust_untrust
Start time: 2024-11-30 09:56:39 TTL: 21s
Initiator->Responder: 0 packets 0 bytes
Responder->Initiator: 0 packets 0 bytes
Total sessions found: 2
- 2025-12-23回答
- 评论(0)
- 举报
-
(0)

除非运营商给了上ipv6外网的内外网地址,不然需要做nat66,除了外网口ipv6地址外还需要nat66转换前缀地址
- 2025-12-22回答
- 评论(1)
- 举报
-
(0)
现在的情况是运营商的路由器分配给直连电脑的都是64位前缀的全球聚合地址
现在的情况是运营商的路由器分配给直连电脑的都是64位前缀的全球聚合地址
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明

