问
S6520X-30HF-EI DHCP出现大量conflict问题
2026-02-03提问
- 0关注
- 0收藏,327浏览
问题描述:
每天早上有大概一个小时的时间内,命令display dhcp server conflict出现大量表项,导致dhcp池被耗尽,有些电脑无法获取到可用ip,且查看问题发生当下的ARP表,以上ip皆只对应同一个或两个mac地址。起初将发生这些问题的mac地址对应的电脑设为dhcp池外的静态ip,但第二天仍会出现同样的问题,请问该如何解决。
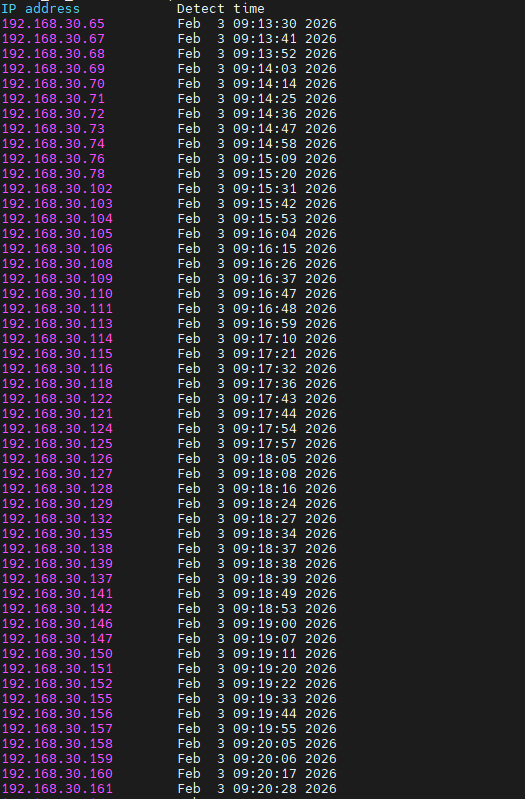
- 2026-02-03提问
- 举报
-
(0)

二、立即应急措施
1. 定位攻击源端口
# 查看ARP表,确认具体的攻击MAC地址
display arp | include 192.168.30
# 查看MAC地址表,找到该MAC对应的端口
display mac-address | include <攻击MAC>
# 例如:display mac-address | include 0011-2233-4455
# 如果看到多个端口出现同一个MAC,说明有环路或欺骗2. 隔离攻击端口
# 立即关闭攻击端口
interface GigabitEthernet x/x/x
shutdown
description "DHCP-Attack-Isolated-$(date)"
# 或使用端口安全功能隔离
port-security enable
port-security max-mac-num 1
port-security protect-action shutdown3. 清理DHCP冲突表
# 清除当前冲突记录
reset dhcp server conflict all
# 查看清理后状态
display dhcp server conflict三、华三S6520X详细解决方案
第一步:启用DHCP Snooping(关键防护)
# 进入系统视图
system-view
# 全局启用DHCP Snooping
dhcp snooping enable
# 在VLAN上启用(假设是VLAN 1)
vlan 1
dhcp snooping enable
quit
# 配置信任端口(连接合法DHCP服务器的端口)
interface GigabitEthernet x/x/x # DHCP服务器所在端口
dhcp snooping trust
quit
# 在用户接入端口限制DHCP请求速率
interface range GigabitEthernet 1/0/1 to GigabitEthernet 1/0/24
dhcp snooping max-learning-num 3 # 每个端口最多学习3个DHCP绑定
dhcp snooping check dhcp-rate enable
dhcp snooping check dhcp-rate 10 # 每秒最多10个DHCP请求
quit第二步:配置IP源防护(IPSG)
# 启用IP源防护
dhcp snooping binding record
user-bind enable
# 在接入端口启用IP源检查
interface range GigabitEthernet 1/0/1 to GigabitEthernet 1/0/24
ip source check user-bind enable
quit第三步:配置动态ARP检测(DAI)
# 在VLAN上启用ARP检测
vlan 1
arp detection enable
quit
# 配置信任端口(DHCP服务器和核心设备端口)
interface GigabitEthernet x/x/x
arp detection trust
quit第四步:DHCP服务器加固配置
# 查看当前DHCP配置
display dhcp server ip-in-use
display dhcp server free-ip
# 配置DHCP地址池保护
dhcp server ip-pool vlan1
gateway-list 192.168.30.1
network 192.168.30.0 mask 255.255.255.0
# 限制每个MAC的最大租约数
option 82
dhcp-server max-lease-per-mac 2
# 缩短租约时间(临时措施)
lease day 0 hour 1 minute 0
# 启用冲突检测
conflict auto-recycle interval 30
# 配置地址池保留(避免全部分配)
reserved-ip-address 192.168.30.201 192.168.30.254
quit第五步:启用环路检测
# 全局启用环路检测
loopback-detection enable
# 在所有接入端口启用
interface range GigabitEthernet 1/0/1 to GigabitEthernet 1/0/48
loopback-detection enable
loopback-detection action shutdown # 检测到环路时关闭端口
loopback-detection recovery-time 600 # 10分钟后自动恢复
quit第六步:STP加固配置
# 全局启用STP
stp global enable
stp mode rstp
# 配置边缘端口(所有接入端口)
interface range GigabitEthernet 1/0/1 to GigabitEthernet 1/0/48
stp edged-port enable
stp bpdu-protection # BPDU保护
quit
# 设置根桥优先级
stp priority 4096四、监控与诊断命令
1. 实时监控命令
# 查看DHCP Snooping状态
display dhcp snooping
# 查看绑定表
display dhcp snooping binding
# 查看违规统计
display dhcp snooping statistics
# 实时监控DHCP日志
terminal monitor
terminal logging
debugging dhcp server event
debugging dhcp snooping packet2. 抓包分析(问题再现时)
# 创建镜像会话
mirroring-group 1 local
mirroring-group 1 mirroring-port GigabitEthernet 1/0/1 inbound
mirroring-group 1 monitor-port GigabitEthernet 1/0/48
# 或使用packet-capture(如果交换机支持)
packet-capture interface GigabitEthernet 1/0/1 inbound3. 查看系统状态
# 检查CPU和内存使用率
display cpu-usage
display memory-usage
# 查看端口流量统计
display interface GigabitEthernet 1/0/1
display counters inbound interface GigabitEthernet 1/0/1五、高级排查步骤
1. 分析攻击模式
从时间戳看,攻击有精确的时间间隔:
09:13:30- 第一波开始- 每约10秒一个新IP冲突
- 持续约5分钟
这可能是自动化脚本攻击,特征:
- 定时触发(早上员工上班时)
- 固定间隔发送请求
- 使用MAC地址欺骗
2. 查找攻击源
# 查看日志缓冲
display logbuffer | include DHCP
display logbuffer | include 09:13
# 查看安全日志
display security-log3. 创建访问控制策略
# 创建ACL阻断异常DHCP流量
acl number 3000
rule 5 deny udp destination-port eq 67 # 阻止非法DHCP响应
rule 10 deny udp destination-port eq 68 time-range morning-attack
quit
# 创建时间范围
time-range morning-attack 09:00 to 10:00 working-day
# 应用ACL到接入端口
interface range GigabitEthernet 1/0/1 to GigabitEthernet 1/0/48
packet-filter 3000 inbound
quit六、长期防护建议
1. 网络分段
# 创建隔离VLAN
vlan 100
name DHCP-Isolation
quit
# 将疑似问题端口移到隔离VLAN
interface GigabitEthernet x/x/x
port access vlan 100
quit2. 部署网络准入控制
# 启用802.1X认证
dot1x
dot1x authentication-method eap
# 配置Radius服务器
radius scheme dhcp-protect
primary authentication 192.168.1.100
key authentication cipher xxxx
quit3. 定期审计
# 导出配置备份
display current-configuration > backup-config-$(date +%Y%m%d).txt
# 检查安全配置
display security-policy
display acl all七、如果问题依旧存在
如果按以上步骤操作后问题依然存在,请收集以下信息:
- 完整配置导出
display current-configuration - 详细诊断信息
display diagnostic-information - 特定时段抓包
# 在攻击发生前开始抓包 packet-capture interface GigabitEthernet 1/0/1 inbound size 2048 - 联系华三技术支持时提供:
- 交换机型号和软件版本:
display version - 故障时间点的日志:
display logbuffer - 网络拓扑图
- 已尝试的解决措施
八、特别提醒
- 时间敏感:攻击发生在早上9点左右,建议在8:30前完成防护配置部署
- 影响范围:先在一部分端口测试,确认无误后再全局部署
- 备份配置:每次修改前备份配置
- 监控效果:部署后持续监控至少3天
根本解决方案:结合
DHCP Snooping + IPSG + DAI三合一防护,基本可以防御此类攻击。如果仍有问题,可能需要检查网络中是否有无线网络、VPN设备或访客网络作为攻击入口。需要我提供任何具体命令的详细解释吗?
- 2026-02-03回答
- 评论(0)
- 举报
-
(0)
编辑答案
➤


✖
亲~登录后才可以操作哦!
确定
✖
✖
你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
✖
举报
×
侵犯我的权益
>
对根叔社区有害的内容
>
辱骂、歧视、挑衅等(不友善)
侵犯我的权益
×
侵犯了我企业的权益
>
抄袭了我的内容
>
诽谤我
>
辱骂、歧视、挑衅等(不友善)
骚扰我
侵犯了我企业的权益
×
您好,当您发现根叔知了上有关于您企业的造谣与诽谤、商业侵权等内容时,您可以向根叔知了进行举报。 请您把以下内容通过邮件发送到 pub.zhiliao@h3c.com 邮箱,我们会在审核后尽快给您答复。
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
我们认为知名企业应该坦然接受公众讨论,对于答案中不准确的部分,我们欢迎您以正式或非正式身份在根叔知了上进行澄清。
抄袭了我的内容
×
原文链接或出处
诽谤我
×
您好,当您发现根叔知了上有诽谤您的内容时,您可以向根叔知了进行举报。 请您把以下内容通过邮件发送到pub.zhiliao@h3c.com 邮箱,我们会尽快处理。
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
我们认为知名企业应该坦然接受公众讨论,对于答案中不准确的部分,我们欢迎您以正式或非正式身份在根叔知了上进行澄清。
对根叔社区有害的内容
×
垃圾广告信息
色情、暴力、血腥等违反法律法规的内容
政治敏感
不规范转载
>
辱骂、歧视、挑衅等(不友善)
骚扰我
诱导投票
不规范转载
×
举报说明




暂无评论