LINUX系统漏洞
- 0关注
- 1收藏,2688浏览
问题描述:
| 服务器支持 TLS Client-initiated 重协商攻击(CVE-2011-1473)【原理扫描】 |
组网及组网描述:
| 服务器支持 TLS Client-initiated 重协商攻击(CVE-2011-1473)【原理扫描】 |
- 2018-12-06提问
- 举报
-
(0)
最佳答案

根据绿盟扫描的结果,和提示所给的解决方式,升级openssl都没有用,而且系统并没有安装,apache,nginx等中间件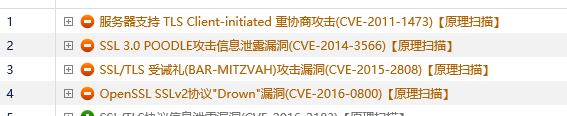
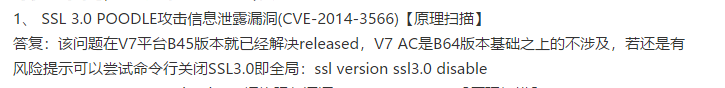 按照这个解决,但是ssl version ssl3.0 disable在redhad6.5上执行不了
按照这个解决,但是ssl version ssl3.0 disable在redhad6.5上执行不了
- 2018-12-06回答
- 评论(3)
- 举报
-
(0)
参考Redhat 官网:https://access.redhat.com/security/cve/cve-2011-1473 Statement This issue affects all of the versions of OpenSSL in Red Hat Enterprise Linux 5, 6, and 7. Red Hat Product Security has rated this issue as having Low security impact. We currently have no plans to fix this issue. For additional information,
使用的是什么型号的服务器,漏洞扫描时扫的网卡IP还是HDM IP
参考Redhat 官网:https://access.redhat.com/security/cve/cve-2011-1473 Statement This issue affects all of the versions of OpenSSL in Red Hat Enterprise Linux 5, 6, and 7. Red Hat Product Security has rated this issue as having Low security impact. We currently have no plans to fix this issue. For additional information,
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明



根据绿盟扫描的结果,和提示所给的解决方式,升级openssl都没有用,而且系统并没有安装,apache,nginx等中间件 按照这个解决,但是ssl version ssl3.0 disable在redhad6.5上执行不了