关于H3C 模拟器 ACL 的问题, 模拟器版本 HCL v2.1.1
- 1关注
- 1收藏,3230浏览
问题描述:
关于H3C 模拟器 ACL 的问题, 模拟器版本 HCL v2.1.1
想用ACL 实现局域网内 6段可以访问全网, 3,4,5网段之间不能互访, 请求大神给个思路, 能贴出配置命令最好(就acl那几条就行 谢谢啊)
我把交换机2 的配置 ,导出来了 ,以文档的形式放在附件里,求大神帮忙 改正一下
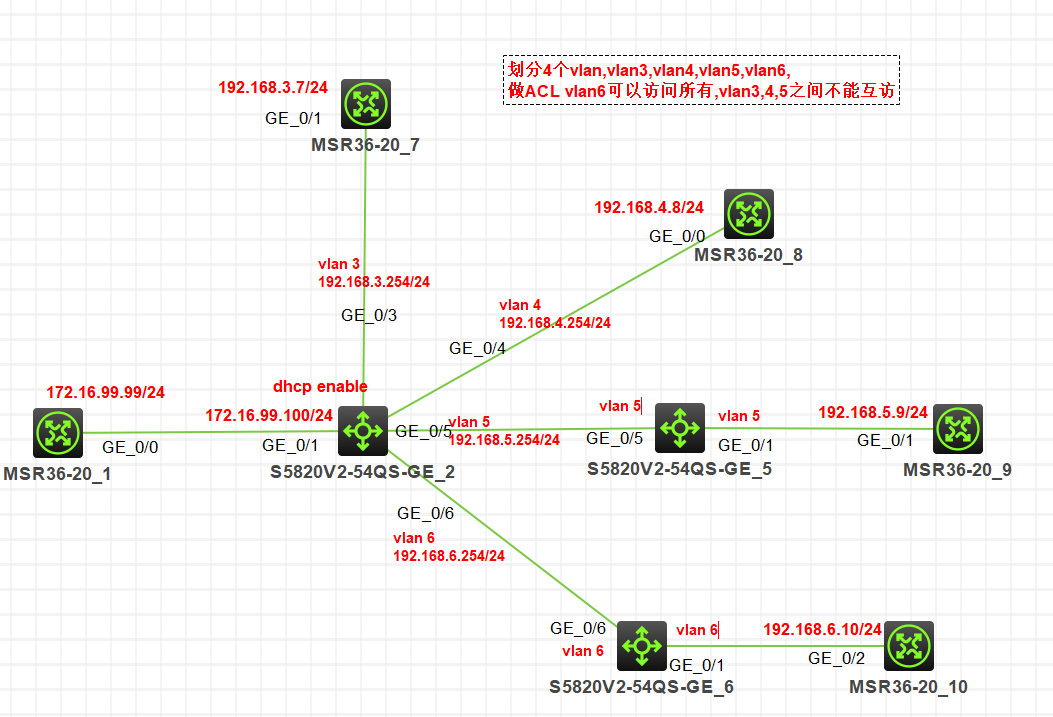
组网及组网描述:
关于H3C 模拟器 ACL 的问题, 模拟器版本 HCL v2.1.1
想用ACL 实现局域网内 6段可以访问全网, 3,4,5网段之间不能互访, 请求大神给个思路, 能贴出配置最好
我把交换机2 的配置 ,导出来了 ,以文档的形式放在附件里,求大神帮忙 改正一下,
有人说模拟器下 不能做acl, 做了也不成功. 我想求证一下
我还复制了一份
[R2]dis cu # version 7.1.075, Alpha 7571 # sysname R2 # irf mac-address persistent timer irf auto-update enable undo irf link-delay irf member 1 priority 1 # packet-filter default deny # dhcp enable dhcp server forbidden-ip 192.168.3.241 192.169.3.253 dhcp server forbidden-ip 192.168.4.241 192.169.4.253 dhcp server forbidden-ip 192.168.5.241 192.168.5.253 dhcp server forbidden-ip 192.168.6.241 192.168.6.253 # lldp global enable # system-working-mode standard xbar load-single password-recovery enable lpu-type f-series # vlan 1 # vlan 3 to 6 # vlan 100 # stp global enable # dhcp server ip-pool vlan3 gateway-list 192.168.3.254 network 192.168.3.0 mask 255.255.255.0 dns-list 222.172.200.68 114.114.114.114 # dhcp server ip-pool vlan4 gateway-list 192.168.4.254 network 192.168.4.0 mask 255.255.255.0 dns-list 222.172.200.68 114.114.114.114 # dhcp server ip-pool vlan5 gateway-list 192.168.5.254 network 192.168.5.0 mask 255.255.255.0 dns-list 222.172.200.68 114.114.114.114 # dhcp server ip-pool vlan6 gateway-list 222.172.200.68 114.114.114.114 192.168.6.254 network 192.168.6.0 mask 255.255.255.0 dns-list 222.172.200.68 114.114.114.114 # interface NULL0 # interface Vlan-interface3 ip address 192.168.3.254 255.255.255.0 packet-filter 3000 inbound packet-filter 3000 outbound # interface Vlan-interface4 ip address 192.168.4.254 255.255.255.0 packet-filter 3000 inbound packet-filter 3000 outbound # interface Vlan-interface5 ip address 192.168.5.254 255.255.255.0 packet-filter 3000 inbound packet-filter 3000 outbound # interface Vlan-interface6 ip address 192.168.6.254 255.255.255.0 packet-filter 3000 inbound packet-filter 3000 outbound # interface Vlan-interface100 ip address 172.16.99.100 255.255.255.0 # interface FortyGigE1/0/53 port link-mode bridge # interface FortyGigE1/0/54 port link-mode bridge # interface GigabitEthernet1/0/1 port link-mode bridge port access vlan 100 combo enable fiber # interface GigabitEthernet1/0/2 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/3 port link-mode bridge port access vlan 3 combo enable fiber packet-filter 3000 inbound # interface GigabitEthernet1/0/4 port link-mode bridge port access vlan 4 combo enable fiber packet-filter 3000 inbound # interface GigabitEthernet1/0/5 port link-mode bridge port access vlan 5 combo enable fiber packet-filter 3000 inbound # interface GigabitEthernet1/0/6 port link-mode bridge port access vlan 6 combo enable fiber packet-filter 3000 inbound # interface GigabitEthernet1/0/7 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/8 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/9 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/10 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/11 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/12 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/13 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/14 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/15 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/16 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/17 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/18 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/19 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/20 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/21 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/22 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/23 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/24 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/25 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/26 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/27 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/28 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/29 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/30 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/31 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/32 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/33 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/34 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/35 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/36 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/37 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/38 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/39 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/40 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/41 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/42 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/43 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/44 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/45 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/46 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/47 port link-mode bridge combo enable fiber # interface GigabitEthernet1/0/48 port link-mode bridge combo enable fiber # interface M-GigabitEthernet0/0/0 # interface Ten-GigabitEthernet1/0/49 port link-mode bridge combo enable fiber # interface Ten-GigabitEthernet1/0/50 port link-mode bridge combo enable fiber # interface Ten-GigabitEthernet1/0/51 port link-mode bridge combo enable fiber # interface Ten-GigabitEthernet1/0/52 port link-mode bridge combo enable fiber # scheduler logfile size 16 # line class aux user-role network-operator # line class console user-role network-admin # line class tty user-role network-operator # line class vty user-role network-operator # line aux 0 user-role network-operator # line con 0 user-role network-admin # line vty 0 63 user-role network-operator # acl basic 2000 # acl advanced 3000 rule 0 permit ip source 192.168.6.0 0.0.0.255 destination 192.168.0.0 0.0.255.255 rule 1 permit ip source 192.168.0.0 0.0.255.255 destination 192.168.6.0 0.0.0.255 rule 2 deny ip source 192.168.0.0 0.0.255.255 destination 0.0.0.0 255.255.0.0 rule 3 permit ip source 192.168.0.0 0.0.255.255 # radius scheme system user-name-format without-domain # domain name system # domain default enable system # role name level-0 description Predefined level-0 role # role name level-1 description Predefined level-1 role # role name level-2 description Predefined level-2 role # role name level-3 description Predefined level-3 role # role name level-4 description Predefined level-4 role # role name level-5 description Predefined level-5 role # role name level-6 description Predefined level-6 role # role name level-7 description Predefined level-7 role # role name level-8 description Predefined level-8 role # role name level-9 description Predefined level-9 role # role name level-10 description Predefined level-10 role # role name level-11 description Predefined level-11 role # role name level-12 description Predefined level-12 role # role name level-13 description Predefined level-13 role # role name level-14 description Predefined level-14 role # user-group system # return
最佳答案

可以配置包过滤,配置见下方,把允许改成拒绝就可以了,模拟器很长时间不用了,不知道是不是和真机不一样。
V7交换机允许指定范围内的主机互相访问配置方法(命令行版)
目录
V7交换机允许指定范围内的主机互相访问配置方法(命令行版) 1
1 配置需求或说明
1.1 适用产品系列
本案例适用于如S5130S-28S-SI、S5500V2-24P-WiNet等的V7交换机,V5、V7交换机具体分类及型号可以参考“1.1 Comware V5、V7平台交换机分类说明”。
1.2配置注意事项
在ACL规则中,设备通过通配符掩码(如0.0.0.255)来确定要匹配的IP地址范围。例如要匹配源地址为1.1.0.0/16网段,规则中应输入source 1.1.0.0 0.0.255.255。
在配置时要特别注意ACL规则的配置顺序,如果先配置了拒绝所有IP报文通过的规则,则指定网段之间的IP报文也将被过滤,无法实现组网需求。
1.3配置需求及实现的效果
交换机的GigabitEthernet1/0/1端口下连接了两个网段的主机,要求通过配置ACL,仅允许10.1.2.0/24网段访问100.1.1.0/24网段的报文通过,而拒绝其它报文通过。
2 组网图

3 配置步骤
3.1配置acl,接口下下发过滤策略,调用acl
# 创建IPv4高级ACL 3000,配置两条规则,分别为允许源地址为10.1.2.0/24网段,目的地址为100.1.1.0/24网段的IP报文通过,以及拒绝其它IP报文通过。
<H3C> system-view
[H3C] acl number 3000
[H3C-acl-ipv4-adv-3000] rule permit ip source 10.1.2.0 0.0.0.255 destination 100.1.1.0 0.0.0.255
[H3C-acl-ipv4-adv-3000] rule deny ip
[H3C-acl-ipv4-adv-3000] quit
说明:如果acl number 3000无法写上去的话可能是由于交换机的软件版本不同导致,此时修改为acl advanced 3000的写法就可以了。
# 配置包过滤功能,应用IPv4高级ACL 3000对端口GigabitEthernet1/0/1收到的IP报文进行过滤。
[H3C] interface gigabitethernet 1/0/1
[H3C-GigabitEthernet1/0/1] packet-filter 3000 inbound
3.2检查配置效果
# 执行display packet-filter命令查看包过滤功能的应用状态。
[H3C] display packet-filter interface GigabitEthernet 1/0/1
Interface: GigabitEthernet1/0/1
In-bound Policy:
acl 3000, Successful
上述信息显示GigabitEthernet1/0/1端口上已经正确应用了包过滤功能。
在10.1.2.0/24网段的主机上以100.1.1.0/24网段内的服务器为目的进行ping操作,返回正常应答信息;在其它网段的主机上执行此操作返回请求超时信息。
4保存配置信息
[H3C]save force
- 2019-09-08回答
- 评论(1)
- 举报
-
(0)
谢谢啊 找到问题了, 我是新手 把通配符掩码 写错了, 逻辑是对的 3Q


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明


谢谢啊 找到问题了, 我是新手 把通配符掩码 写错了, 逻辑是对的 3Q