OSPF得问题
- 0关注
- 1收藏,2021浏览
问题描述:
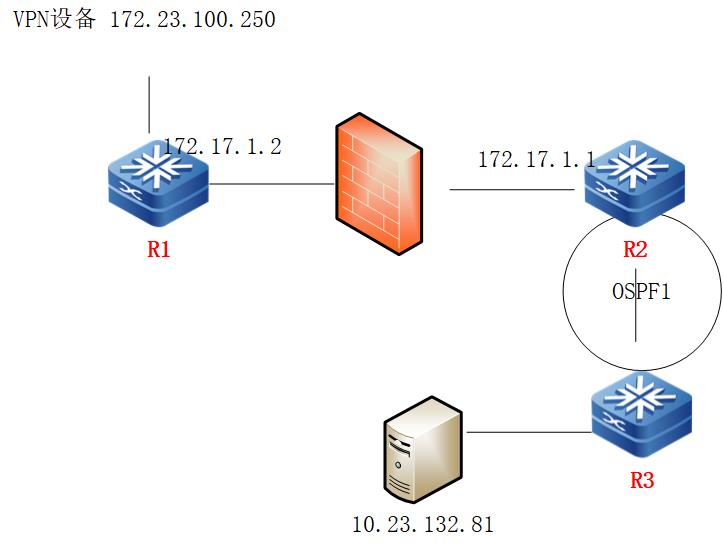
想VPN进来172.23.100.250 后访问 10.23.132.81 ,但是不通。
VPN进来后可以访问R2上 所有VLAN 但是访问不到 与他OSPF 1 中得 R3 上得数据 看路由还有啊
请问 是要做静态引入 路由重发布什么得么 有点蒙
组网及组网描述:
防火墙得配置 以上
<R1>
# interface Vlanif1000 ip address 172.17.1.2 255.255.255.252 #
# interface GigabitEthernet0/0/46
description to NeiWangHeXin-SW G1/4/0/27
port link-type access port default vlan 1000
port-mirroring to observe-port 1 inbound
ip route-static 0.0.0.0 0.0.0.0 172.17.1.10 preference 80
ip route-static 0.0.0.0 0.0.0.0 172.17.1.6 track nqa yd cmcc description link-detection
ip route-static 10.5.0.0 255.255.0.0 172.17.1.1
ip route-static 10.23.0.0 255.255.0.0 172.17.1.1 #
R2 配置
# acl number 2000 rule 0 permit source 10.23.10.108 0 rule 5 permit source 10.23.10.91 0 rule 10 permit source 10.23.10.95 0 rule 15 permit source 10.23.5.3 0 rule 20 permit source 10.23.0.102 0 rule 25 deny
# acl number 3000 rule 0 permit tcp destination-port eq www rule 1 permit tcp destination-port eq ftp rule 2 permit tcp destination-port eq ftp-data acl number 3001 rule 1 deny udp destination-port eq tftp rule 2 deny udp destination-port eq 135 rule 3 deny tcp destination-port eq 135 rule 4 deny udp destination-port eq netbios-ns rule 5 deny udp destination-port eq netbios-dgm rule 6 deny udp destination-port eq netbios-ssn rule 7 deny tcp destination-port eq 139 rule 8 deny udp destination-port eq 445 rule 9 deny tcp destination-port eq 445 rule 10 deny udp destination-port eq 593 rule 11 deny tcp destination-port eq 593 rule 12 deny tcp destination-port eq 1022 rule 13 deny tcp destination-port eq 1023 rule 14 deny tcp destination-port eq 1025 rule 15 deny tcp source-port eq 1034 destination-port eq www rule 16 deny tcp destination-port eq 1068 rule 17 permit tcp destination 10.1.7.0 0.0.0.255 destination-port eq 1433 rule 18 permit tcp destination 10.1.10.0 0.0.0.255 destination-port eq 1433 rule 19 deny tcp destination-port eq 1433 rule 20 deny udp destination-port eq 1434 rule 21 deny tcp destination-port eq 1871 rule 22 deny tcp destination-port eq 2745 rule 23 deny tcp destination-port eq 3127 rule 24 deny tcp destination-port eq 3208 rule 25 deny tcp destination-port eq 4331 rule 26 deny tcp destination-port eq 4334 rule 27 deny tcp destination-port eq 4444 rule 28 deny tcp destination-port eq 4510 rule 29 deny tcp destination-port eq 4557 rule 30 deny tcp destination-port eq 5554 rule 31 deny tcp destination-port eq 5800 rule 32 deny tcp destination-port eq 5900 rule 33 deny tcp destination-port eq 6129 rule 34 deny tcp destination-port eq 6667 rule 35 deny tcp destination-port eq 9995 rule 36 deny tcp destination-port eq 9996 rule 37 deny tcp destination-port eq 10080 rule 38 deny tcp source-port eq 4444 rule 39 permit tcp destination 10.23.2.40 0 destination-port eq 1433 rule 40 permit tcp destination 10.23.4.145 0 destination-port eq 8010
# interface Vlan-interface1000
description to HuLianWangHeXin-SW
ip address 172.17.1.1 255.255.255.252
# interface GigabitEthernet1/4/0/27 port link-mode bridge description to HuLianWangHeXin-SW G1/0/46 port access vlan 1000
# ospf 1
import-route direct
import-route static
area 0.0.0.23
network 10.23.0.0 0.0.0.127
network 10.23.0.128 0.0.0.127
network 10.23.1.0 0.0.0.127
network 10.23.1.128 0.0.0.127
network 10.23.2.0 0.0.0.127
network 10.23.2.128 0.0.0.127
network 10.23.3.0 0.0.0.31
network 10.23.3.32 0.0.0.31
network 10.23.3.64 0.0.0.31
network 10.23.3.128 0.0.0.31
network 10.23.3.160 0.0.0.31
network 10.23.3.192 0.0.0.31
network 10.23.3.224 0.0.0.31
network 10.23.4.0 0.0.0.31
network 10.23.4.32 0.0.0.31
network 10.23.4.64 0.0.0.31
network 10.23.4.96 0.0.0.31
network 10.23.4.128 0.0.0.31
network 10.23.4.160 0.0.0.31
network 10.23.4.192 0.0.0.31
network 10.23.4.224 0.0.0.31
network 10.23.5.0 0.0.0.31
network 10.23.5.32 0.0.0.31
network 10.23.5.64 0.0.0.31
network 10.23.5.96 0.0.0.31
network 10.23.5.192 0.0.0.31
network 10.23.5.224 0.0.0.31
network 10.23.6.0 0.0.0.127
network 10.23.7.0 0.0.0.255
network 10.23.8.0 0.0.0.127
network 10.23.254.20 0.0.0.3
network 10.23.254.44 0.0.0.3
network 10.23.254.48 0.0.0.3
network 10.23.254.56 0.0.0.7
network 10.23.254.64 0.0.0.3
network 10.23.254.8 0.0.0.3
network 10.23.10.0 0.0.0.127
network 10.23.15.0 0.0.0.127
network 10.23.254.4 0.0.0.3
network 10.23.254.68 0.0.0.3
network 10.23.254.36 0.0.0.3
network 10.23.254.32 0.0.0.3
network 10.23.12.0 0.0.0.255
network 172.17.1.0 0.0.0.3 # route-policy 1 permit node 1 if-match ip-prefix 1 # nqa entry 1 2 type icmp-echo destination ip 111.43.134.193 frequency 100 next-hop 10.23.0.101 reaction 1 checked-element probe-fail threshold-type consecutive 5 action-type trigger-only
# ip route-static 0.0.0.0 0.0.0.0 10.23.0.100 preference 100
ip route-static 0.0.0.0 0.0.0.0 10.23.0.101 track 1
ip route-static 0.0.0.0 0.0.0.0 172.17.1.2
ip route-static 10.23.13.0 255.255.255.240 10.23.241.68
ip route-static 10.23.13.16 255.255.255.240 10.23.254.37
ip route-static 10.23.13.32 255.255.255.240 10.23.254.37
ip route-static 10.23.13.48 255.255.255.240 10.23.254.37
ip route-static 10.23.13.64 255.255.255.240 10.23.254.37
ip route-static 10.23.13.80 255.255.255.240 10.23.254.37
ip route-static 10.23.13.96 255.255.255.240 10.23.254.37
ip route-static 10.23.13.112 255.255.255.240 10.23.254.37
ip route-static 10.23.13.128 255.255.255.240 10.23.254.37
ip route-static 10.23.13.144 255.255.255.240 10.23.254.37
ip route-static 10.23.13.160 255.255.255.240 10.23.254.37
ip route-static 10.23.13.192 255.255.255.224 10.23.254.37
ip route-static 10.23.15.0 255.255.255.128 10.23.12.100
ip route-static 10.23.37.64 255.255.255.192 10.23.254.37
ip route-static 10.23.54.128 255.255.255.224 10.23.254.37
ip route-static 10.23.56.0 255.255.255.224 10.23.251.194
ip route-static 10.23.70.64 255.255.255.192 10.23.254.37
ip route-static 10.23.115.0 255.255.255.0 172.17.1.2
ip route-static 10.23.119.128 255.255.255.192 10.23.254.45
ip route-static 10.23.135.0 255.255.255.192 10.23.254.45
ip route-static 10.23.135.64 255.255.255.192 10.23.254.45
ip route-static 10.23.147.144 255.255.255.240 10.23.254.37
ip route-static 10.23.150.0 255.255.255.0 10.23.254.45
ip route-static 10.23.150.0 255.255.255.224 10.23.254.45
ip route-static 10.23.150.32 255.255.255.224 10.23.254.45
ip route-static 10.23.150.128 255.255.255.224 10.23.254.37
ip route-static 10.23.150.224 255.255.255.224 10.23.254.37
ip route-static 10.23.178.0 255.255.255.192 10.23.254.45
ip route-static 10.23.254.32 255.255.255.252 10.23.254.34
ip route-static 10.88.0.0 255.255.0.0 10.23.254.21
ip route-static 10.111.0.64 255.255.255.252 10.23.254.21
ip route-static 18.23.132.81 255.255.255.255 10.23.254.5
ip route-static 172.17.1.6 255.255.255.255 172.17.1.2
ip route-static 172.17.1.10 255.255.255.255 172.17.1.2
ip route-static 172.17.221.0 255.255.255.0 172.17.1.2
ip route-static 172.18.0.0 255.255.0.0 10.23.254.59
ip route-static 172.23.3.0 255.255.255.0 172.17.1.2
ip route-static 172.23.4.0 255.255.255.0 172.17.1.2
ip route-static 172.23.5.0 255.255.255.0 172.17.1.2
ip route-static 172.23.7.0 255.255.255.0 172.17.1.2
ip route-static 172.23.8.0 255.255.255.0 172.17.1.2
ip route-static 172.23.9.0 255.255.255.0 172.17.1.2
ip route-static 172.23.10.0 255.255.255.0 172.17.1.2
ip route-static 172.23.100.0 255.255.255.0 172.17.1.2
ip route-static 172.172.172.0 255.255.255.0 10.23.254.37
ip route-static 192.168.0.0 255.255.255.0 10.23.252.21
ip route-static 192.168.0.0 255.255.255.240 10.23.254.21
ip route-static 192.168.0.0 255.255.255.252 10.23.254.21
ip route-static 218.203.13.171 255.255.255.255 172.17.1.2
ip route-static 218.203.13.172 255.255.255.255 172.17.1.2
ip route-static 218.203.59.116 255.255.255.255 172.17.1.2
ip route-static 221.181.72.153 255.255.255.255 172.17.1.2
ip route-static 221.181.72.244 255.255.255.255 172.17.1.2
R3 配置
| <hgt-xx-r2020-01>dis cu | |||||||||
| # | |||||||||
| version 5.20, Release 1205, Standard | |||||||||
| # | |||||||||
| sysname hgt-xx-r2020-01 | |||||||||
| # | |||||||||
| super password level 3 simple hljdzjxjdz | |||||||||
| # | |||||||||
| domain default enable system | |||||||||
| # | |||||||||
| router id 10.23.132.1 | |||||||||
| # | |||||||||
| telnet server enable | |||||||||
| # | |||||||||
| vlan 1 | |||||||||
| # | |||||||||
| radius scheme system | |||||||||
| server-type extended | |||||||||
| primary authentication 127.0.0.1 1645 | |||||||||
| primary accounting 127.0.0.1 1646 | |||||||||
| user-name-format without-domain | |||||||||
| # | |||||||||
| domain system | |||||||||
| access-limit disable | |||||||||
| state active | |||||||||
| idle-cut disable | |||||||||
| self-service-url disable | |||||||||
| # | |||||||||
| ike peer center | |||||||||
| pre-shared-key twzx | |||||||||
| remote-address 218.9.199.98 | |||||||||
| local-address 221.210.162.60 | |||||||||
| # | |||||||||
| ike peer center1 | |||||||||
| pre-shared-key hljtwzx | |||||||||
| remote-address 111.43.134.195 | |||||||||
| local-address 221.210.162.60 | |||||||||
| # | |||||||||
| ipsec proposal default | |||||||||
| # | |||||||||
| ipsec proposal hljdzj | |||||||||
| # | |||||||||
| ipsec policy center 1 isakmp | |||||||||
| security acl 3005 | |||||||||
| ike-peer center | |||||||||
| proposal hljdzj | |||||||||
| # | |||||||||
| ipsec policy center 2 isakmp | |||||||||
| security acl 3006 | |||||||||
| ike-peer center1 | |||||||||
| proposal default | |||||||||
| # | |||||||||
| acl number 2001 | |||||||||
| rule 0 permit source 10.23.132.0 0.0.0.255 | |||||||||
| # | |||||||||
| acl number 3000 | |||||||||
| rule 0 permit ip source 10.23.132.0 0.0.0.255 destination 10.23.0.0 0.0.0.255 | |||||||||
| rule 5 deny ip | |||||||||
| acl number 3005 | |||||||||
| rule 0 permit gre source 221.210.162.60 0 destination 218.9.199.98 0 | |||||||||
| acl number 3006 | |||||||||
| rule 0 permit gre source 221.210.162.60 0 destination 111.43.134.195 0 | |||||||||
| # | |||||||||
| interface Aux0 | |||||||||
| async mode flow | |||||||||
| link-protocol ppp | |||||||||
| # | |||||||||
| interface Ethernet0/0 | |||||||||
| port link-mode route | |||||||||
| ipsec policy center | |||||||||
| # | |||||||||
| interface Ethernet0/1 | |||||||||
| port link-mode route | |||||||||
| ip address 10.23.132.1 255.255.255.0 | |||||||||
| # | |||||||||
| interface Serial1/0 | |||||||||
| link-protocol ppp | |||||||||
| ip address 10.23.252.70 255.255.255.252 | |||||||||
| # | |||||||||
| interface NULL0 | |||||||||
| # | |||||||||
| interface Tunnel0 | |||||||||
| mtu 1500 | |||||||||
| ip address 10.23.253.70 255.255.255.252 | |||||||||
| source Ethernet0/0 | |||||||||
| destination 218.9.199.98 | |||||||||
| ospf cost 100 | |||||||||
| # | |||||||||
| interface Tunnel1 | |||||||||
| mtu 1500 | |||||||||
| ip address 10.23.251.70 255.255.255.252 | |||||||||
| source Ethernet0/0 | |||||||||
| destination 111.43.134.195 | |||||||||
| ospf cost 70 | |||||||||
| # | |||||||||
| ospf 1 | |||||||||
| area 0.0.0.23 | |||||||||
| network 10.23.132.0 0.0.0.255 | |||||||||
| network 10.23.253.68 0.0.0.3 | |||||||||
| network 10.23.252.68 0.0.0.3 | |||||||||
| network 10.23.251.68 0.0.0.3 | |||||||||
| # | |||||||||
| snmp-agent | |||||||||
| snmp-agent local-engineid 800063A203000FE257F883 | |||||||||
| snmp-agent community read dzj-105 | |||||||||
| snmp-agent sys-info version all |
- 2019-10-09提问
- 举报
-
(0)
最佳答案

VPN里面想访问公网里面的终端,肯定需要些静态路由
比如VPN 1里面想访问公网里的10.0.0.0/8
ip route-static vpn-instance 1 10.0.0.0 8 12.1.1.1 public
12.1.1.1是公网里面的下一跳,后面需要加public参数
公网里写去往VPN 1的路由
ip route-static 20.0.0.0 8 vpn-instance 1 22.1.1.1
22.1.1.1是VPN 1里面的下一跳
- 2019-10-09回答
- 评论(1)
- 举报
-
(0)
VPN 映射完了 没问题, 可以公网地址访问进来,只是到R2内网那面下得资源访问不了 ,


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明


VPN 映射完了 没问题, 可以公网地址访问进来,只是到R2内网那面下得资源访问不了 ,