华三与思科使用DDNS建立L2LVPN问题
- 0关注
- 1收藏,1740浏览
问题描述:
一台华三MSR360与一台思科2911都没有固定的外网IP,使用的是3322动态域名,配置完成后不能建立VPN,思科内网地址段: 192.168.10.0/24 192.168.15.0/24 192.168.100.0/24,注册的动态域名:***.***,华三内网地址段:192.168.0.0/24 注册的域名:***.***
诊断信息
<H3C>*Oct 12 14:26:06:236 2019 H3C IKE/7/EVENT: Received packet successfully.
*Oct 12 14:26:06:237 2019 H3C IKE/7/PACKET: vrf = 0, src = 221.225.97.8, dst = 49.73.165.9/500 Received packet from 49.73.165.9 source port 500 destination port 500.
*Oct 12 14:26:06:237 2019 H3C IKE/7/PACKET: vrf = 0, src = 221.225.97.8, dst = 49.73.165.9/500
I-COOKIE: fb79da73bb443e8e
R-COOKIE: 0000000000000000
next payload: SA version: ISAKMP
Version 1.0 exchange mode: Main
flags: message ID: 0 length: 164
*Oct 12 14:26:06:237 2019 H3C IKE/7/EVENT: IKE thread 1097119024 processes a job.
*Oct 12 14:26:06:237 2019 H3C IKE/7/EVENT: Phase1 process started.
*Oct 12 14:26:06:237 2019 H3C IKE/7/PACKET: vrf = 0, src = 221.225.97.8, dst = 49.73.165.9/500 Begin a new phase 1 negotiation as responder.
*Oct 12 14:26:06:237 2019 H3C IKE/7/EVENT: vrf = 0, src = 221.225.97.8, dst = 49.73.165.9/500 Responder created an SA for peer 49.73.165.9, local port 500, remote port 500.
*Oct 12 14:26:06:237 2019 H3C IKE/7/EVENT: vrf = 0, src = 221.225.97.8, dst = 49.73.165.9/500 Set IKE SA state to IKE_P1_STATE_INIT.
*Oct 12 14:26:06:237 2019 H3C IKE/7/PACKET: vrf = 0, src = 221.225.97.8, dst = 49.73.165.9/500 Received ISAKMP Security Association Payload.
*Oct 12 14:26:06:237 2019 H3C IKE/7/PACKET: vrf = 0, src = 221.225.97.8, dst = 49.73.165.9/500 Received ISAKMP Vendor ID Payload.
*Oct 12 14:26:06:237 2019 H3C IKE/7/PACKET: vrf = 0, src = 221.225.97.8, dst = 49.73.165.9/500 Received ISAKMP Vendor ID Payload.
*Oct 12 14:26:06:238 2019 H3C IKE/7/PACKET: vrf = 0, src = 221.225.97.8, dst = 49.73.165.9/500 Received ISAKMP Vendor ID Payload.
*Oct 12 14:26:06:238 2019 H3C IKE/7/PACKET: vrf = 0, src = 221.225.97.8, dst = 49.73.165.9/500 Received ISAKMP Vendor ID Payload. *Oct 12 14:26:06:238 2019 H3C IKE/7/PACKET: vrf = 0, src = 221.225.97.8, dst = 49.73.165.9/500 Process vendor ID payload.
*Oct 12 14:26:06:238 2019 H3C IKE/7/EVENT: Vendor ID NAT-T rfc3947 is matched.
*Oct 12 14:26:06:238 2019 H3C IKE/7/PACKET: vrf = 0, src = 221.225.97.8, dst = 49.73.165.9/500 Process SA payload.
*Oct 12 14:26:06:238 2019 H3C IKE/7/PACKET: vrf = 0, src = 221.225.97.8, dst = 49.73.165.9/500 Check ISAKMP transform 1.
*Oct 12 14:26:06:238 2019 H3C IKE/7/PACKET: vrf = 0, src = 221.225.97.8, dst = 49.73.165.9/500 Encryption algorithm is 3DES-CBC.
*Oct 12 14:26:06:238 2019 H3C IKE/7/PACKET: vrf = 0, src = 221.225.97.8, dst = 49.73.165.9/500 HASH algorithm is HMAC-MD5.
*Oct 12 14:26:06:238 2019 H3C IKE/7/PACKET: vrf = 0, src = 221.225.97.8, dst = 49.73.165.9/500 DH group is 2.
*Oct 12 14:26:06:238 2019 H3C IKE/7/PACKET: vrf = 0, src = 221.225.97.8, dst = 49.73.165.9/500 Authentication method is Pre-shared key.
*Oct 12 14:26:06:238 2019 H3C IKE/7/PACKET: vrf = 0, src = 221.225.97.8, dst = 49.73.165.9/500 Lifetime type is 1.
*Oct 12 14:26:06:238 2019 H3C IKE/7/PACKET: vrf = 0, src = 221.225.97.8, dst = 49.73.165.9/500 Life duration is 86400.
*Oct 12 14:26:06:238 2019 H3C IKE/7/EVENT: vrf = 0, src = 221.225.97.8, dst = 49.73.165.9/500 Pre-shared key matching address 49.73.165.9 not found.
*Oct 12 14:26:06:239 2019 H3C IKE/7/ERROR: vrf = 0, src = 221.225.97.8, dst = 49.73.165.9/500 No acceptable transform.
*Oct 12 14:26:06:239 2019 H3C IKE/7/ERROR: vrf = 0, src = 221.225.97.8, dst = 49.73.165.9/500 Failed to parse the IKE SA payload.
*Oct 12 14:26:06:239 2019 H3C IKE/7/PACKET: vrf = 0, src = 221.225.97.8, dst = 49.73.165.9/500 Construct notification packet: NO_PROPOSAL_CHOSEN.
*Oct 12 14:26:06:239 2019 H3C IKE/7/PACKET: vrf = 0, src = 221.225.97.8, dst = 49.73.165.9/500 Sending packet to 49.73.165.9 remote port 500, local port 500. *Oct 12 14:26:06:239 2019 H3C IKE/7/PACKET: vrf = 0, src = 221.225.97.8, dst = 49.73.165.9/500
I-COOKIE: fb79da73bb443e8e
R-COOKIE: 0000000000000000 next payload: NOTIFY
version: ISAKMP Version 1.0
exchange mode: Info
flags: message ID: 0 length: 56
*Oct 12 14:26:06:239 2019 H3C IKE/7/PACKET: vrf = 0, src = 221.225.97.8, dst = 49.73.165.9/500 Sending an IPv4 packet.
*Oct 12 14:26:06:240 2019 H3C IKE/7/EVENT: vrf = 0, src = 221.225.97.8, dst = 49.73.165.9/500 Sent data to socket successfully.
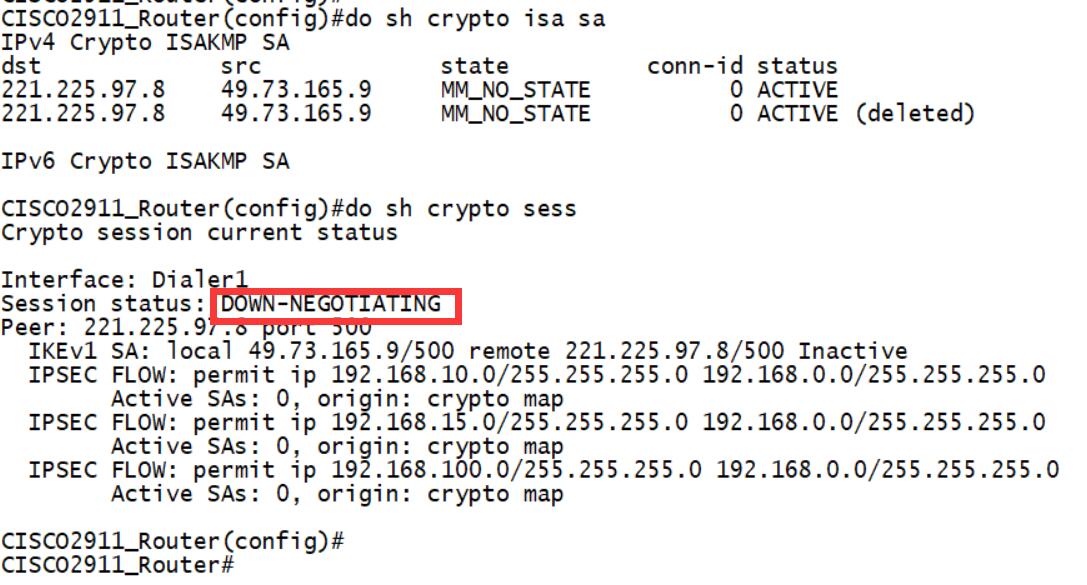
*Oct 12 14:26:06:240 2019 H3C IKE/7/ERROR: vrf = 0, src = 221.225.97.8, dst = 49.73.165.9/500 Failed to negotiate IKE SA. <H3C> <H3C>un de ike all <H3C> <H3C> <H3C> <H3C>un t d
++++++++++++++++++++++++++++++++++++
组网及组网描述:
华三配置:
ipsec transform-set MSR360
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
# ipsec policy-template 1 1
transform-set MSR360
security acl 3000
ike-profile MSR360
# ipsec policy L2LVPN 1 isakmp template 1
# ike identity fqdn MSR360
# ike profile MSR360
keychain MSR360
local-identity fqdn MSR360
match remote identity fqdn CISCO2911_Router
# ike proposal 1
encryption-algorithm 3des-cbc
dh group2
authentication-algorithm md5
# ike keychain MSR360
pre-shared-key hostname ***.*** key cipher simple 123456
++++++++++++++++++++++++++++++++++++++++++++++++++
思科:
ip access-list extended L2LVPN
permit ip 192.168.10.0 0.0.0.255 192.168.0.0 0.0.0.255
permit ip 192.168.15.0 0.0.0.255 192.168.0.0 0.0.0.255
permit ip 192.168.100.0 0.0.0.255 192.168.0.0 0.0.0.255
crypto isakmp policy
10 encr 3des
hash md5
authentication pre-share
group 2
crypto isakmp key 0 123456 hostname ***.***
crypto ipsec transform-set MSR360 esp-3des esp-md5-hmac
mode tunnel crypto map L2LVPN 1 ipsec-isakmp
set peer ***.*** dynamic
set transform-set MSR360
match address L2LVPN
int dia 1
crypto map L2LVPN
- 2019-10-12提问
- 举报
-
(0)
最佳答案


Failed to negotiate IKE SA.
应该是两边的配置问题
看配置,我们这边都是fqdn,对面思科的配置看不太明白
- 2019-10-12回答
- 评论(0)
- 举报
-
(0)


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明


暂无评论