msr36-10,ipsec连接上以后,发起端可以ping通对端,接收端无法ping通发起端。
- 0关注
- 1收藏,1922浏览
问题描述:
之前一直使用ipsec偶VPN连接,最近突然出现发起端可以ping通对端,接收端无法ping通发起端的情况,发起端所有的设备无变动,配置无变动。接收端配置信息如下。
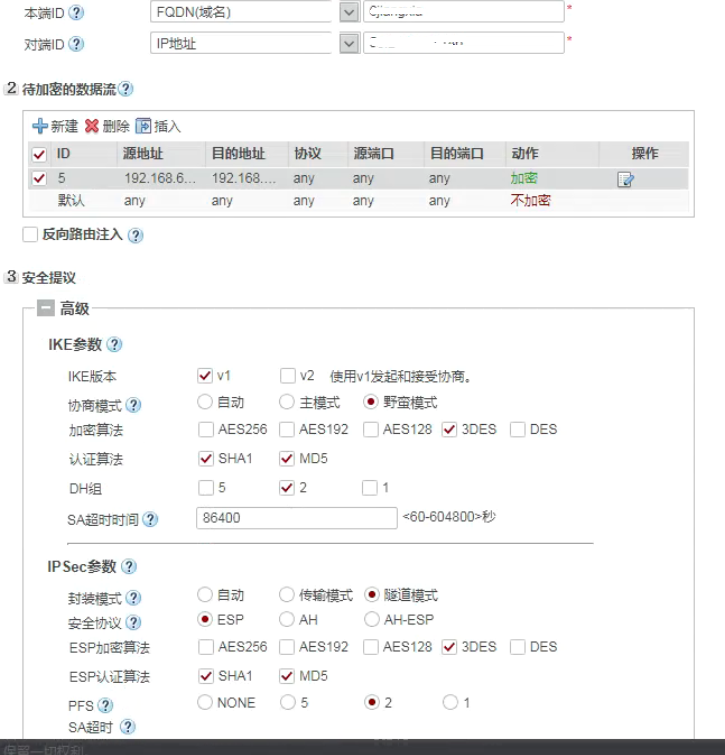
此图为发起端配置
组网及组网描述:
以下为接收端配置
- policy-based-route aaa permit node 1
- if-match acl 3100
- #
- policy-based-route aaa permit node 2
- if-match acl 3300
- apply next-hop 58.215.*.*
- #
- policy-based-route aaa permit node 5
- if-match acl 3200
- apply output-interface Dialer0
- #
- controller Cellular0/0
- #
- controller Cellular0/1
- #
- interface Aux0
- #
- interface Dialer0
- mtu 1400
- ppp chap password cipher $c$3$NVxVXgc1fmuCa/GIvCziVpTnNJxlBIQ5eg==
- ppp chap user 051012208068
- ppp ipcp dns admit-any
- ppp ipcp dns request
- ppp pap local-user 051012208068 password cipher $c$3$ZoUN06Tj2qrX2VqMlr0fFmxTWrdte18ZAA==
- dialer bundle enable
- dialer-group 1
- dialer timer idle 0
- dialer timer autodial 5
- ip address ppp-negotiate
- tcp mss 1024
- nat outbound
- #
- interface Virtual-Template0
- #
- interface NULL0
- #
- interface Vlan-interface1
- #
- interface GigabitEthernet0/0
- port link-mode route
- description Multiple_Line
- bandwidth 100000
- combo enable copper
- ip address 58.215.*.* 255.255.255.0
- dns server 221.228.255.1
- nat outbound
- nat outbound 3501
- nat server protocol tcp global 58.215.*.* 80 inside 192.168.100.223 80
- nat server protocol tcp global 58.215.*.* 81 inside 192.168.100.223 81
- nat server protocol tcp global 58.215.*.* 5222 inside 192.168.100.248 5222
- nat server protocol tcp global 58.215*.* 7070 inside 192.168.100.248 7070
- nat server protocol tcp global 58.215.*.* 8081 inside 192.168.100.251 8081
- nat server protocol tcp global 58.215.*.* 8082 inside 192.168.100.223 8082
- nat server protocol tcp global 58.215.*.* 8083 inside 192.168.100.236 8083
- nat server protocol tcp global 58.215.*.* 8089 inside 192.168.100.222 8089
- nat server protocol tcp global 58.215.*.* 8999 inside 192.168.100.248 8999
- nat server protocol tcp global 58.215.*.* 9000 inside 192.168.100.236 9000
- nat server protocol tcp global 58.215.*.* 33890 inside 192.168.100.222 33890
- nat static enable
- ipsec apply policy zb100
- #
- interface GigabitEthernet0/1
- port link-mode route
- description Multiple_Line
- duplex full
- speed 1000
- mtu 1200
- shutdown
- tcp mss 1024
- pppoe-client dial-bundle-number 0
- #
- interface GigabitEthernet0/2
- port link-mode route
- ip address 192.168.100.254 255.255.255.0
- tcp mss 1024
- nat server protocol tcp global 58.215.*.* 80 inside 192.168.100.223 80
- nat server protocol tcp global 58.215.*.* 89 inside 192.168.100.251 89
- nat server protocol tcp global 58.215.*.* 8081 inside 192.168.100.251 8081
- nat server protocol tcp global 58.215.*.* 8082 inside 192.168.100.223 8082
- nat hairpin enable
- ip policy-based-route aaa
- #
- security-zone name Local
- #
- security-zone name Trust
- #
- security-zone name DMZ
- #
- security-zone name Untrust
- #
- security-zone name Management
- #
- scheduler logfile size 16
- #
- line class aux
- user-role network-admin
- #
- line class tty
- user-role network-operator
- #
- line class vty
- user-role network-operator
- #
- line aux 0
- user-role network-admin
- #
- line vty 0 4
- authentication-mode scheme
- user-role level-15
- user-role network-admin
- user-role network-operator
- #
- line vty 5 63
- user-role network-operator
- #
- ip route-static 0.0.0.0 0 GigabitEthernet0/0 58.215.*.*.preference 30
- ip route-static 0.0.0.0 0 Dialer0
- #
- acl advanced 3100
- rule 0 permit ip destination 192.168.100.0 0.0.0.255
- #
- acl advanced 3200
- rule 0 permit ip source 192.168.100.64 0.0.0.63
- rule 1 permit ip source 192.168.100.0 0.0.0.63
- rule 2 permit ip source 192.168.128.0 0.0.0.63
- rule 20 permit ip source 192.168.100.192 0
- rule 25 permit ip source 192.168.100.193 0
- rule 26 permit ip source 192.168.100.194 0
- rule 27 permit ip source 192.168.100.195 0
- rule 28 permit ip source 192.168.100.196 0
- rule 29 permit ip source 192.168.100.197 0
- rule 30 permit ip source 192.168.100.198 0
- rule 31 permit ip source 192.168.100.199 0
- rule 32 permit ip source 192.168.100.200 0
- #
- acl advanced 3300
- rule 5 permit ip source 192.168.100.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
- rule 10 permit ip source 192.168.100.0 0.0.0.255 destination 192.168.5.0 0.0.0.255
- rule 15 permit ip source 192.168.100.0 0.0.0.255 destination 192.168.8.0 0.0.0.255
- rule 20 permit ip source 192.168.100.0 0.0.0.255 destination 192.168.11.0 0.0.0.255
- rule 25 permit ip source 192.168.100.0 0.0.0.255 destination 192.168.80.0 0.0.0.255
- rule 30 permit ip source 192.168.100.0 0.0.0.255 destination 192.168.0.0 0.0.0.255
- rule 35 permit ip source 192.168.100.0 0.0.0.255 destination 192.168.6.0 0.0.0.255
- rule 40 permit ip source 192.168.100.0 0.0.0.255 destination 192.168.3.0 0.0.0.255
- rule 45 permit ip source 192.168.100.0 0.0.0.255 destination 192.168.9.0 0.0.0.255
- rule 50 permit ip source 192.168.100.0 0.0.0.255 destination 192.168.18.0 0.0.0.255
- rule 55 permit ip source 192.168.100.0 0.0.0.255 destination 192.168.31.0 0.0.0.255
- #
- acl advanced 3501
- rule 0 deny ip source 192.168.100.0 0.0.0.255 destination 192.168.5.0 0.0.0.255
- rule 1 deny ip source 192.168.100.0 0.0.0.255 destination 192.168.18.0 0.0.0.255
- rule 2 deny ip source 192.168.100.0 0.0.0.255 destination 192.168.0.0 0.0.0.255
- rule 3 deny ip source 192.168.100.0 0.0.0.255 destination 192.168.6.0 0.0.0.255
- rule 4 deny ip source 192.168.100.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
- rule 5 deny ip source 192.168.100.0 0.0.0.255 destination 192.168.80.0 0.0.0.255
- rule 6 deny ip source 192.168.100.0 0.0.0.255 destination 192.168.11.0 0.0.0.255
- rule 7 deny ip source 192.168.100.0 0.0.0.255 destination 192.168.8.0 0.0.0.255
- rule 8 deny ip source 192.168.100.0 0.0.0.255 destination 192.168.3.0 0.0.0.255
- rule 9 deny ip source 192.168.100.0 0.0.0.255 destination 192.168.31.0 0.0.0.255
- rule 10 deny ip source 192.168.100.0 0.0.0.255 destination 192.168.9.0 0.0.0.255
- rule 31 permit ip
- #
- domain system
- #
- domain default enable system
- #
- role name level-0
- description Predefined level-0 role
- #
- role name level-1
- description Predefined level-1 role
- #
- role name level-2
- description Predefined level-2 role
- #
- role name level-3
- description Predefined level-3 role
- #
- role name level-4
- description Predefined level-4 role
- #
- role name level-5
- description Predefined level-5 role
- #
- role name level-6
- description Predefined level-6 role
- #
- role name level-7
- description Predefined level-7 role
- #
- role name level-8
- description Predefined level-8 role
- #
- role name level-9
- description Predefined level-9 role
- #
- role name level-10
- description Predefined level-10 role
- #
- role name level-11
- description Predefined level-11 role
- #
- role name level-12
- description Predefined level-12 role
- #
- role name level-13
- description Predefined level-13 role
- #
- role name level-14
- description Predefined level-14 role
- #
- user-group system
- #
- local-user admin class manage
- password hash $h$6$X5KlqjblPVQPGArx$LWJtAADuMwbOp7TD7cLPhGQHLxfnBdaq1agklTnAkAezs0Xuf1HgayJ5G501fcGsf2qACPEWp9sfwIqqB9IsRA==
- service-type ftp
- service-type ssh telnet terminal http https
- authorization-attribute user-role level-15
- authorization-attribute user-role network-admin
- authorization-attribute user-role network-operator
- #
- ipsec transform-set 1
- esp encryption-algorithm 3des-cbc
- esp authentication-algorithm md5
- pfs dh-group2
- #
- ipsec transform-set 31
- esp encryption-algorithm 3des-cbc
- esp authentication-algorithm md5
- #
- ipsec policy-template zb11wh 1
- transform-set 1
- ike-profile 11wuhan
- sa duration time-based 3600
- sa duration traffic-based 1843200
- #
- ipsec policy-template zb18mh 1
- transform-set 1
- ike-profile 18minhou
- sa duration time-based 3600
- sa duration traffic-based 1843200
- #
- ipsec policy-template zb31sz 1
- transform-set 31
- ike-profile 31suzhou
- sa duration time-based 3600
- sa duration traffic-based 1843200
- #
- ipsec policy-template zb3sz 1
- transform-set 1
- ike-profile 3suzhou
- sa duration time-based 3600
- sa duration traffic-based 1843200
- #
- ipsec policy-template zb80wh 1
- transform-set 1
- ike-profile 80wuhan
- sa duration time-based 3600
- sa duration traffic-based 1843200
- #
- ipsec policy-template zb8mh 1
- transform-set 1
- ike-profile 8minhou
- sa duration time-based 3600
- sa duration traffic-based 1843200
- #
- ipsec policy-template zb9dt 1
- transform-set 1
- ike-profile 9daotian
- sa duration time-based 3600
- sa duration traffic-based 1843200
- #
- ipsec policy-template zbfz 1
- transform-set 1
- ike-profile 5fuzhou
- sa duration time-based 3600
- sa duration traffic-based 1843200
- #
- ipsec policy-template zbjth 1
- transform-set 1
- ike-profile jintaihu
- sa duration time-based 3600
- sa duration traffic-based 1843200
- #
- ipsec policy-template zbjx 1
- transform-set 1
- ike-profile 6jiangxia
- sa duration time-based 3600
- sa duration traffic-based 1843200
- #
- ipsec policy-template zbjy 1
- transform-set 1
- ike-profile 2jiangyin
- sa duration time-based 3600
- sa duration traffic-based 1843200
- #
- ipsec policy zb100 1 isakmp template zbjth
- #
- ipsec policy zb100 2 isakmp template zbfz
- #
- ipsec policy zb100 3 isakmp template zbjx
- #
- ipsec policy zb100 4 isakmp template zbjy
- #
- ipsec policy zb100 5 isakmp template zb80wh
- #
- ipsec policy zb100 6 isakmp template zb11wh
- #
- ipsec policy zb100 7 isakmp template zb8mh
- #
- ipsec policy zb100 8 isakmp template zb3sz
- #
- ipsec policy zb100 9 isakmp template zb31sz
- #
- ipsec policy zb100 10 isakmp template zb9dt
- #
- ipsec policy zb100 11 isakmp template zb18mh
- #
- ike profile 11wuhan
- keychain test
- dpd interval 10 periodic
- exchange-mode aggressive
- local-identity address 58.215.*.*
- match remote identity fqdn 11wuhan
- proposal 2
- #
- ike profile 18minhou
- keychain test
- dpd interval 10 periodic
- exchange-mode aggressive
- local-identity fqdn zb100
- match remote identity fqdn 18minhou
- proposal 2
- #
- ike profile 2jiangyin
- keychain test
- dpd interval 10 periodic
- exchange-mode aggressive
- local-identity address 58.215.*.*
- match remote identity fqdn 2jiangyin
- proposal 2
- #
- ike profile 31suzhou
- keychain test
- dpd interval 10 periodic
- exchange-mode aggressive
- local-identity address 58.215.*.*
- match remote identity fqdn 31suzhou
- proposal 2
- #
- ike profile 3suzhou
- keychain test
- dpd interval 10 periodic
- exchange-mode aggressive
- local-identity address 58.215.*.*
- match remote identity fqdn 3suzhou
- proposal 2
- #
- ike profile 5fuzhou
- keychain test
- dpd interval 10 periodic
- exchange-mode aggressive
- local-identity address 58.215.*.*
- match remote identity fqdn 5fuzhou
- proposal 2
- #
- ike profile 6jiangxia
- keychain test
- dpd interval 10 periodic
- exchange-mode aggressive
- local-identity address 58.215.*.*
- match remote identity fqdn 6jiangxia
- proposal 2
- #
- ike profile 80wuhan
- keychain test
- dpd interval 10 periodic
- exchange-mode aggressive
- local-identity address 58.215.*.*
- match remote identity fqdn 80wuhan
- proposal 2
- #
- ike profile 8minhou
- keychain test
- dpd interval 10 periodic
- exchange-mode aggressive
- local-identity fqdn zb100
- match remote identity fqdn 8minhou
- proposal 2
- #
- ike profile 9daotian
- keychain test
- dpd interval 10 periodic
- exchange-mode aggressive
- local-identity address 58.215.*.*
- match remote identity fqdn 9daotian
- proposal 2
- #
- ike profile jintaihu
- keychain test
- dpd interval 10 periodic
- exchange-mode aggressive
- local-identity address 58.215.*.*.
- match remote identity fqdn 0jintaihu
- proposal 2
- #
- ike proposal 2
- encryption-algorithm 3des-cbc
- dh group2
- #
- ike keychain test
- pre-shared-key address 0.0.0.0 0.0.0.0 key cipher $c$3$Fpsouoa9Pf/HnFLN9K6cwsFHfCDyOX6pungY
- #
- ip http port 8989
- ip https port 18989
- ip http enable
- ip https enable
- #
- wlan global-configuration
- #
- wlan ap-group default-group
- #
- return
- 2019-10-21提问
- 举报
-
(0)
最佳答案

需要看一下故障时候dis ike sa和dis ipsec sa是否都有。另外要检查一下两端的路由对不对。
- 2019-10-21回答
- 评论(1)
- 举报
-
(0)
这个是我测试的摸一个网段,IKE sa 和ipsec sa 应该是都有 <H3C>dis ike sa Connection-ID Remote Flag DOI ------------------------------------------------------------------ 5 49.80.156.127 RD IPsec 2 110.83.16.88 RD IPsec 6 112.86.4.226 RD IPsec 3 180.113.172.24 RD IPsec 15 27.156.26.80 RD IPsec 7 27.155.238.36 RD IPsec 82 117.80.106.252 RD IPsec 20 111.175.84.83 RD IPsec 8 171.43.215.145 RD IPsec 88 27.156.26.140 Unknown IPsec 84 59.173.154.190 RD IPsec 67 59.173.154.190 RD|RL IPsec Flags: RD--READY RL--REPLACED FD-FADING RK-REKEY <H3C>dis ipsec sa ------------------------------- Interface: GigabitEthernet0/0 ----------------------------- IPsec policy: zb100 Sequence number: 3 Mode: Template ----------------------------- Tunnel id: 0 Encapsulation mode: tunnel Perfect Forward Secrecy: dh-group2 Inside VPN: Extended Sequence Numbers enable: N Traffic Flow Confidentiality enable: N Path MTU: 1444 Tunnel: local address: 58.215.215.146 remote address: 111.175.84.83 Flow: sour addr: 192.168.100.0/255.255.255.0 port: 0 protocol: ip dest addr: 192.168.6.0/255.255.255.0 port: 0 protocol: ip [Inbound ESP SAs] SPI: 3161781874 (0xbc74f672) Connection ID: 30064771074 Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5 SA duration (kilobytes/sec): 1843200/3600 SA remaining duration (kilobytes/sec): 1831672/2550 Max received sequence-number: 63663 Anti-replay check enable: Y Anti-replay window size: 64 UDP encapsulation used for NAT traversal: N Status: Active [Outbound ESP SAs] SPI: 453548495 (0x1b0899cf) Connection ID: 30064771075 Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5 SA duration (kilobytes/sec): 1843200/3600 SA remaining duration (kilobytes/sec): 1835358/2550 Max sent sequence-number: 61596 UDP encapsulation used for NAT traversal: N Status: Active

您好,请知:
当ipsec不同时,检查sa及ike是否还保留,另外确认路由是否还可达。
如果上述的信息还在,可重启ipsec的进程后再测试:
- 2019-10-21回答
- 评论(1)
- 举报
-
(1)
路由不可达,sa和ike有存在。 您给的命令会报错。 Unrecognized command found at '^' position. 虽然命令没有执行,不过我重启过设备。情况依旧、
路由不可达,sa和ike有存在。 您给的命令会报错。 Unrecognized command found at '^' position. 虽然命令没有执行,不过我重启过设备。情况依旧、
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明


这个是我测试的摸一个网段,IKE sa 和ipsec sa 应该是都有 <H3C>dis ike sa Connection-ID Remote Flag DOI ------------------------------------------------------------------ 5 49.80.156.127 RD IPsec 2 110.83.16.88 RD IPsec 6 112.86.4.226 RD IPsec 3 180.113.172.24 RD IPsec 15 27.156.26.80 RD IPsec 7 27.155.238.36 RD IPsec 82 117.80.106.252 RD IPsec 20 111.175.84.83 RD IPsec 8 171.43.215.145 RD IPsec 88 27.156.26.140 Unknown IPsec 84 59.173.154.190 RD IPsec 67 59.173.154.190 RD|RL IPsec Flags: RD--READY RL--REPLACED FD-FADING RK-REKEY <H3C>dis ipsec sa ------------------------------- Interface: GigabitEthernet0/0 ----------------------------- IPsec policy: zb100 Sequence number: 3 Mode: Template ----------------------------- Tunnel id: 0 Encapsulation mode: tunnel Perfect Forward Secrecy: dh-group2 Inside VPN: Extended Sequence Numbers enable: N Traffic Flow Confidentiality enable: N Path MTU: 1444 Tunnel: local address: 58.215.215.146 remote address: 111.175.84.83 Flow: sour addr: 192.168.100.0/255.255.255.0 port: 0 protocol: ip dest addr: 192.168.6.0/255.255.255.0 port: 0 protocol: ip [Inbound ESP SAs] SPI: 3161781874 (0xbc74f672) Connection ID: 30064771074 Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5 SA duration (kilobytes/sec): 1843200/3600 SA remaining duration (kilobytes/sec): 1831672/2550 Max received sequence-number: 63663 Anti-replay check enable: Y Anti-replay window size: 64 UDP encapsulation used for NAT traversal: N Status: Active [Outbound ESP SAs] SPI: 453548495 (0x1b0899cf) Connection ID: 30064771075 Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5 SA duration (kilobytes/sec): 1843200/3600 SA remaining duration (kilobytes/sec): 1835358/2550 Max sent sequence-number: 61596 UDP encapsulation used for NAT traversal: N Status: Active